#webappsecurity search results
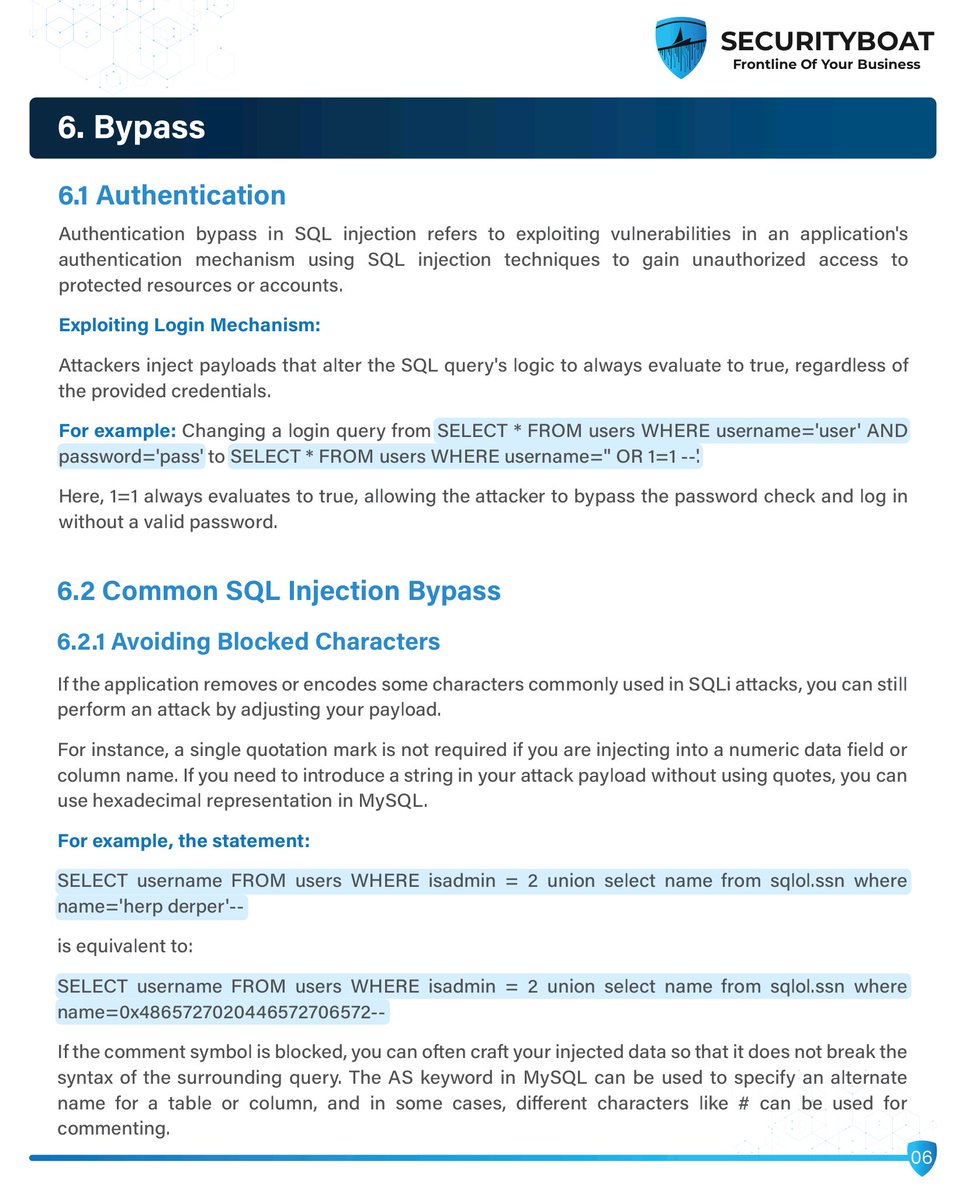
📚 SQL Injection Handbook: Understand, Exploit & Defend Your Web Apps 🔐💻 #SQLInjection #WebAppSecurity #CyberSecurityTraining #EthicalHacking #InfoSec #BugBounty #PenetrationTesting #EducationOnly #SecureCoding #OWASPTop10 #SQLMap


Just wrapped up talking about web app security for 4 hours and still not tired! The energy is real when you're passionate about what you do. 🔐💻 #WebAppSecurity #Cybersecurity

OWASP Web Application Security Risk #webappdevelopment #webapp #webappsecurity #webapplicationdevelopment #webapplicationsecurity #websecurity #infosec #informationsecurity

Network or Web App Pentesting: where should we focus? With apps handling critical data daily, web app security has never been more vital. But network pentesting remains crucial for overall security. What’s your take? #Cybersecurity #Pentesting #WebAppSecurity
📋 Web Application Exploit Checklist: Lab-Based Testing for Common Vulnerabilities 💻🛠️ #WebAppSecurity #PenTestingChecklist #EthicalHacking #OWASPTop10 #CyberSecurityTraining #InfoSec #WebSecurity #EducationOnly #BugBounty #RedTeamReady


Most people ask how can backend developers enhance their server security...one of the method is jsonwebtokens.🔒 We use JSON Web Tokens (JWT) to protect user data and ensure a robust authentication system. A Thread..k #WebAppSecurity
Attackers are often seen to be utilizing unprotected CORS policies when stealing sensitive data. Always validate Access-Control-Allow-Origin, and especially avoid wildcards in production. Secure your APIs before they secure your breach. 🔐💥 #CyberSecurity #WebAppSecurity #trend

Had the most awesome time previous weekend with @TheLaluka during his OffenSkill level 30 training. It is the best offensive web application security training ever and he is a great mentor with fantastic methodology. offenskill.com #webappsecurity #bugbounty

🔒💻 How secure are your web apps? Ben and Jacob break down the sandboxing concept and download dangers on Big App Energy. Don't miss the full episode on making smarter app choices! 🎧👉🏻 podcasters.spotify.com/pod/show/big-a… #WebAppSecurity #BigAppEnergy #TechTips #CyberSafety
🚨 Hands-on Learning Lab. Zero filler. Real-world defense. Join Sofia Visciglia, CTO @ 911CYBER, in person on October 18th at the LAIC Summit for a deep dive: “Web Application Security: From Cloud to Code” RSVP now: laicsummit.com #WebAppSecurity #LAICSummit2025 #

A penetration test revealed serious vulnerabilities in a web app. Instead of fixing them, the team chose to encrypt HTTP requests, which failed to provide true security. Lesson: encryption is not remediation! 🔒💻 #WebAppSecurity #EncryptionFails link: ift.tt/uM1SBvQ

Eric’s cybersecurity journey started with hands-on training at Milima Cyber Academy. Want to gain real-world skills too? April 2025 Cohort starts 7th April! Apply now: mca.ac.ug #CybersecurityTraining #WebAppSecurity

😱Shocking but true😨 A staggering 98% of web applications are sitting ducks for cyber attacks! From malware to malicious redirects, the risks are real. Are you safeguarding your digital presence? #CyberSecurity #WebAppSecurity #StayProtected #InstaSafe #ZeroTrust #malware

Modern web apps shouldn’t make you choose between speed and security ⚡ Join us on Sept 18 for a live webinar where we’ll discuss how to secure web apps without sacrificing agility. Register now: bit.ly/3HSdLQc #DevSecOps #WebAppSecurity
#eWPT Certification: Hands-on exam covering: - Manual exploitation (XSS, SQLi, RCE) - Session & authentication attacks - File inclusion vulnerabilities - Web service testing Real-world engagements. Professional validation. bit.ly/4mPk1H2 #WebAppSecurity

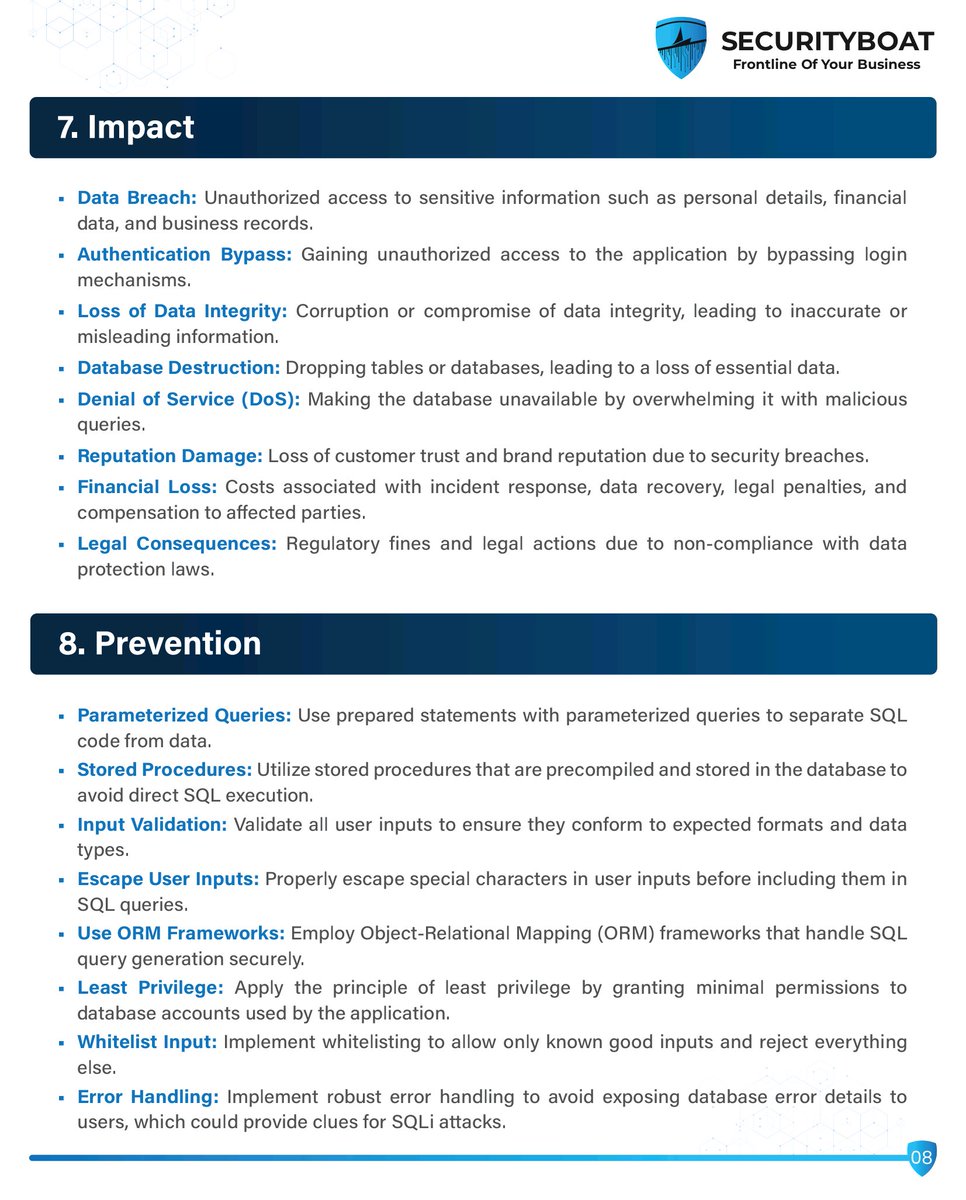
Our Chris Tams with a reminder on why security needs to feature high in the Software Development Life Cycle. Responses still contain too much information which simply doesn't need to be there - Information disclosure through insecure design pentestpartners.com/security-blog/… #webappsecurity

New video on my YouTube channel "Bike (HTB SP T1 walkthrough)"! youtu.be/45CcCjO0cNk?fe… #hackthebox #webappsecurity #cybersecuritytraining

Harnessing the power of machine learning algorithms, we automatically discover APIs by monitoring application traffic. Innovo seamlessly integrates out-of-the-box policies, creating a positive security model based on your organization’s schema specification. #WebAppSecurity

eWPTX: Our most advanced web app penetration testing certification 100% hands-on exam covering: API pentesting (25%) SQL/NoSQL injection Authentication attacks WAF bypass techniques Server-side attacks bit.ly/47PlSYx #eWPTX #WebAppSecurity #PenetrationTesting

#WooCommerce — Checkout Hijack via Parameter Tampering 🚨 Why it matters: Attackers replace checkout endpoints with fraudulent URLs → instant customer trust collapse 🛡️ Action: Block tampered HTTP requests with Quttera WAF. quttera.com/web-applicatio… #CVE #WebAppSecurity…

Is your web app ready for 2025? Don’t leave it vulnerable. Make sure it has: ✔ Two-Factor Authentication ✔ End-to-End Encryption ✔ Regular Security Audits Protect your users and your business. #WebSecurity #CyberSecurity #webappsecurity #TechTrends
#Joomla — Remote File Inclusions 🚨 Why it matters: RFI attacks upload shells and take full control 🛡️ Action: Block payloads with Web Application Firewall for full-perimeter defense quttera.com/web-applicatio… #CyberSecurity #WebAppSecurity #FullPerimeterSecurity

Why rely on generic scans? Our certified analysts manually probe every path, exploit weak apps, and validate fixes in real time—so you go live with confidence. 👉 Explore the full service → infosightinc.com/web-applicatio… #WebAppSecurity #PenTesting #ExpertLed #InfoSight…
Authentication & Sessions Test authenticated areas using cookies: sqlmap -u "site.com/dashboard" --cookie="session=abc123" Or use Burp Suite export: sqlmap -r request.txt #WebAppSecurity #BugBounty
🚨JS Overlay Credential Theft Why it matters: Overlaid login forms capture user and admin credentials 🛡️ Action: Use WAF to block overlay-based attacks at the script level quttera.com/web-applicatio… #InfoSec #Malware #WebAppSecurity

🚨Parameter Pollution Attacks Why it matters: Attackers manipulate URL parameters to bypass validation 🛡️ Action: Use Quttera WAF to block polluted multi-parameter payloads quttera.com/web-applicatio… #CyberSecurity #WebAppSecurity #Quttera

Clickjacking 🚨 Why it matters: Invisible overlays hijack user clicks on your site 🛡️ Action: Use WAF to block frame-based clickjacking attacks. quttera.com/web-applicatio… #Clickjacking #WebAppSecurity #Quttera

Unsafe Deserialization ⚠️Why it matters: Unsanitized data can be executed as code by attackers. Action: Validate all serialized inputs and block exploits with WAF. quttera.com #Deserialization #CyberThreats #WebAppSecurity

Path Traversal Attack ⚠️Why it matters: Hackers exploit directory paths to access private files. Action: Sanitize input and use WAF to block unauthorized file access. quttera.com #PathTraversal #CyberSecurity #WebAppSecurity

Remote File Inclusion (RFI) ⚠️Why it matters: Hackers exploit upload features to add malicious files remotely. Action: Validate file uploads and use WAF to block RFI attempts. quttera.com #RFI #CyberSecurity #WebAppSecurity

📚 SQL Injection Handbook: Understand, Exploit & Defend Your Web Apps 🔐💻 #SQLInjection #WebAppSecurity #CyberSecurityTraining #EthicalHacking #InfoSec #BugBounty #PenetrationTesting #EducationOnly #SecureCoding #OWASPTop10 #SQLMap




Felt it in one of my recent pentest engagements. The team had an API, which wasn't kinda production-ready but was still used in prod. This heavily leaked PII #pentest #webappsecurity #apisecurity

Just wrapped up talking about web app security for 4 hours and still not tired! The energy is real when you're passionate about what you do. 🔐💻 #WebAppSecurity #Cybersecurity

Expect security layers to fail: There are really useful tools to keep web applications safe. Take Web Application Firewalls (WAFs). They inspect web traffic and discard requests to your server if they look malicious. They're a huge benefit to security. #WebAppSecurity 1/2

Using numeric IDs for database records can be a security risk! A problem so common that attackers seeing a numeric ID WILL try to abuse it. They'll change the ID and try to access other people's data. Use GUIDs instead, e.g. ac037242-6e11-475c-a429-92ed1d2abc1c #WebAppSecurity

🍊🔐 Check out my OWASP Juice Shop Lab Walkthrough! 🚀 Dive into the world of web app security with me as we explore vulnerabilities, challenges, and best practices.💻 #OWASP #JuiceShop #WebAppSecurity youtu.be/6n1pI9dJpW4

API Security Google Dorks: hego.gitbook.io #BugBounty #WebAppSecurity #PenTesting #HackerMindset #EthicalHacking #OWASPTop10 #XSS #SQLInjection #CSRF #SecurityTesting #InfoSec #AppSec #VulnerabilityDiscovery #BugbountyTips #BurpSuite #PentestTools #API #APISecurity

🔍 Unleashing the Power of Google Dorks: Your Ultimate Arsenal for Bug Bounties, Web Security, and Pentesting! 🛡️💻 | Discovering Vulnerabilities, One Query at a Time | #BugBounty #WebAppSecurity #Pentesting #GoogleDorks Credit - @TakSec

📋 Web Application Exploit Checklist: Lab-Based Testing for Common Vulnerabilities 💻🛠️ #WebAppSecurity #PenTestingChecklist #EthicalHacking #OWASPTop10 #CyberSecurityTraining #InfoSec #WebSecurity #EducationOnly #BugBounty #RedTeamReady


eWPTX: Our most advanced web app penetration testing certification 100% hands-on exam covering: API pentesting (25%) SQL/NoSQL injection Authentication attacks WAF bypass techniques Server-side attacks bit.ly/47PlSYx #eWPTX #WebAppSecurity #PenetrationTesting

😱Shocking but true😨 A staggering 98% of web applications are sitting ducks for cyber attacks! From malware to malicious redirects, the risks are real. Are you safeguarding your digital presence? #CyberSecurity #WebAppSecurity #StayProtected #InstaSafe #ZeroTrust #malware

Most people ask how can backend developers enhance their server security...one of the method is jsonwebtokens.🔒 We use JSON Web Tokens (JWT) to protect user data and ensure a robust authentication system. A Thread..k #WebAppSecurity

A penetration test revealed serious vulnerabilities in a web app. Instead of fixing them, the team chose to encrypt HTTP requests, which failed to provide true security. Lesson: encryption is not remediation! 🔒💻 #WebAppSecurity #EncryptionFails link: ift.tt/uM1SBvQ

Attackers are often seen to be utilizing unprotected CORS policies when stealing sensitive data. Always validate Access-Control-Allow-Origin, and especially avoid wildcards in production. Secure your APIs before they secure your breach. 🔐💥 #CyberSecurity #WebAppSecurity #trend

Our Chris Tams with a reminder on why security needs to feature high in the Software Development Life Cycle. Responses still contain too much information which simply doesn't need to be there - Information disclosure through insecure design pentestpartners.com/security-blog/… #webappsecurity

Had the most awesome time previous weekend with @TheLaluka during his OffenSkill level 30 training. It is the best offensive web application security training ever and he is a great mentor with fantastic methodology. offenskill.com #webappsecurity #bugbounty

SAML Raider 2.0.0 is here! Upgraded to the Montoya API, now with a smoother build and better user experience. Perfect for your pentesting toolkit. Check it out and read our blog post! ✨#BurpSuite #SAML #WebAppSecurity blog.compass-security.com/2024/07/saml-r…

#eWPT Certification: Hands-on exam covering: - Manual exploitation (XSS, SQLi, RCE) - Session & authentication attacks - File inclusion vulnerabilities - Web service testing Real-world engagements. Professional validation. bit.ly/4mPk1H2 #WebAppSecurity

👉 Try #virtualpatching and start fixing your #vulnerabilities in a day! Understand how: (link in thread) @tumblr #webappsecurity #databreaches #vulnerabilitymanagement #vulnerabilityassessment #waf #apptrana #indusface

Something went wrong.
Something went wrong.
United States Trends
- 1. Thanksgiving 395K posts
- 2. Golesh 2,607 posts
- 3. Camp Haven 7,315 posts
- 4. Fani Willis 16.5K posts
- 5. Trumplican 3,343 posts
- 6. #WipersDayGiveaway N/A
- 7. Khabib 8,315 posts
- 8. Hong Kong 16.8K posts
- 9. NextNRG 1,143 posts
- 10. Tom Hardy 1,732 posts
- 11. Denzel 3,293 posts
- 12. Mendy 4,857 posts
- 13. Wine 39.5K posts
- 14. Stranger Things 167K posts
- 15. Africans 27.1K posts
- 16. Idris 7,822 posts
- 17. #PuebloEnBatallaYVictoria 4,759 posts
- 18. Riker N/A
- 19. Breyers 2,451 posts
- 20. #TejRan 4,172 posts






























