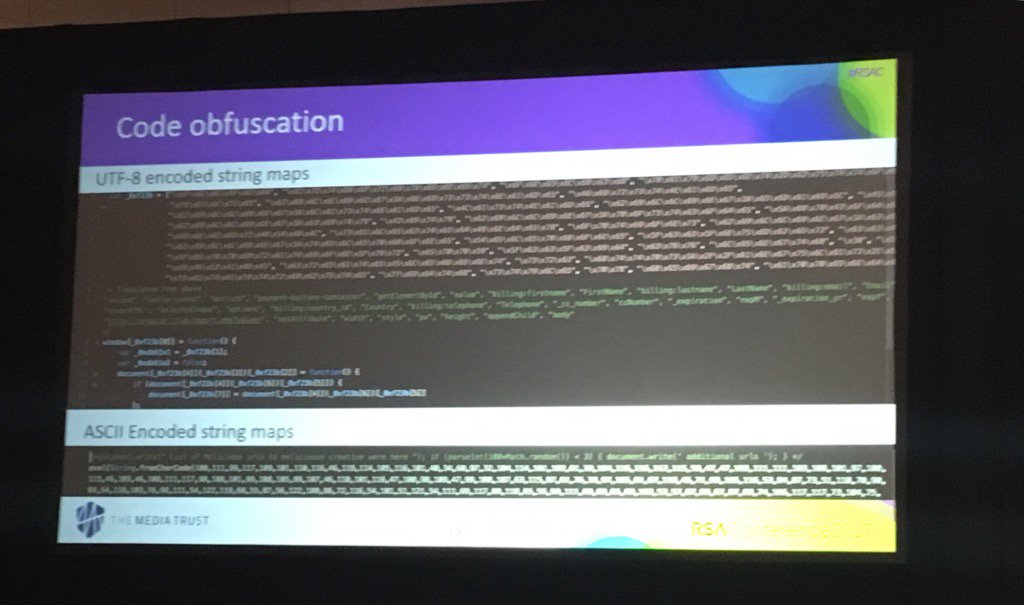
#codeobfuscation search results
Thank u @jasvir for sending me your "Surreptitious Software" book, which coined "chenxification". Finally got the book and love the special program on the inside cover! #codeobfuscation #softwaresecurity

💡Learn in-depth about state-of-the-art of 💻#codeobfuscation & deobfuscation techniques to find out how it complicates #reverseengineering from this hands-on training by Tim @mr_phrazer 🛡️Register to Upskill➡️bit.ly/3WsTmno #NullconDE2023 #infosec #Cybersecurity

Breaking state-of-the-art binary code obfuscation goo.gl/vao3Mv #Reversing #CodeObfuscation #ExploitDev #Infosec
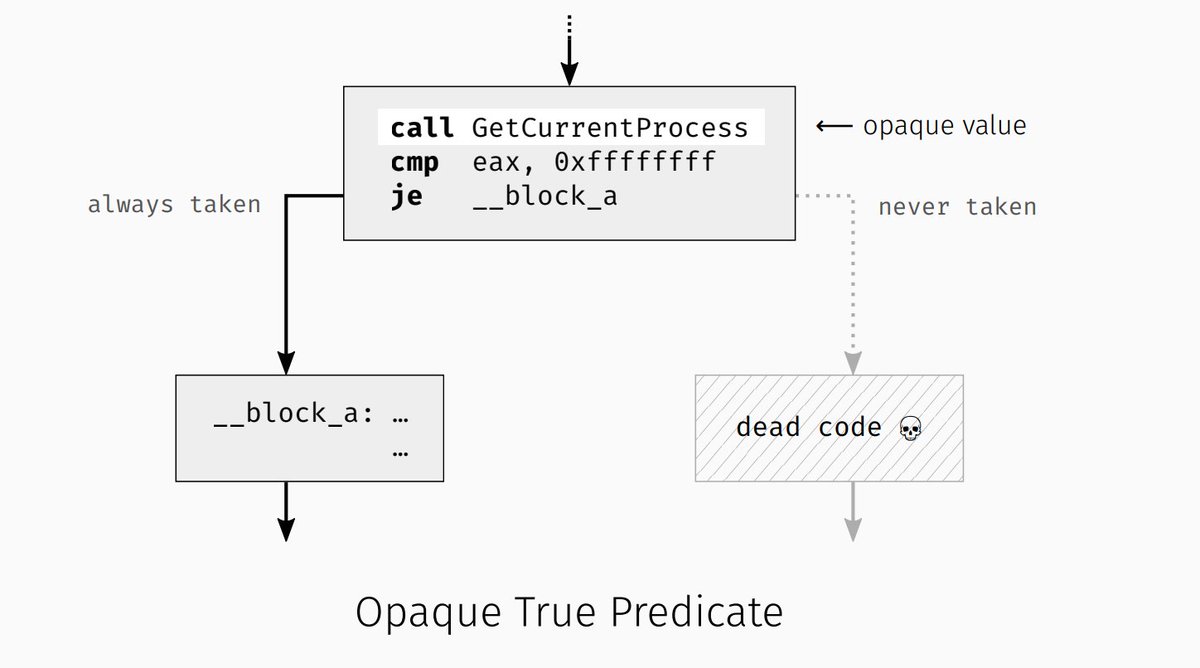
🔓Learn about👨💻#codeobfuscation & deobfuscation techniques to find out how it complicates RE 💡Apply all techniques to break obfuscation schemes from this training by @mr_phrazer ⚠️Grab early bird offer before New Year's eve👉bit.ly/3WsTmno #NullconDE2023 #infosec

👨💻Learn in-depth about state-of-the-art of #codeobfuscation & deobfuscation techniques & break these obfuscation schemes 💻A complete hands-on #training by Tim @mr_phrazer is here! ✅Register to Upskill now ➡️bit.ly/3WsTmno #NullconDE2023 #Infosec #Cybersecurity

2/6 🧵 Code Obfuscation: Make your source code hard to interpret by transforming it with obscure variable names and code flow tweaks. 🔑 While it remains functionally the same, it becomes challenging to reverse-engineer. #ReverseEngineering #Cybersecurity #CodeObfuscation…

Do iOS apps need obfuscation? Short Answer - Yes, they need it. Obfuscation will protect the machine code from being copied and altered without permission. and make it extremely difficult for hackers to identify vulnerabilities in your code. #codeobfuscation #iosapps

#Codeobfuscation is one of the best ways to harden mobile apps #security. bit.ly/2Tw6gF7 #reverseengineering #opensource #programming #coding #javascript #android #cyber #applicationsecurity #ITsecurity #networksecurity #tech #informationsecurity #safegaurding #ios

📱 Secure, quality mobile apps are no longer a luxury—they're a necessity! Learn how to protect your apps with #CodeObfuscation, monitor & react to threats in real-time, & automate testing. Watch now: bit.ly/3V31Cv7 Download the eBook: bit.ly/4fXp8St
(1/2) Ever wonder how #apps stay secure? #Codeobfuscation is the answer! Imagine your app #code as a treasure map. Code Obfuscation scrambles it into a crazy puzzle, leaving pirates scratching their heads! #CyberSecurity #mobilesecurity #Android #iOS #DataSecurity #viralpost

HTML Source Code Encryption: Cara Menyembunyikan dan Melindungi Script HTML #CodeObfuscation, #CSS, #Encryption, #FrontEndDevelopment, #HTML, #JavaScript, #Script, #Security, #WebDevelopment, tools online lupakerja.com/2023/03/html-s…

Have an Android app that needs code obfuscation + hardening to protect it from hacker attacks? Sign up for a free 30-day trial of Verimatrix App Shield verimatrix.com/products/app-s… #codeobfuscation #verimatrix #freetrial
Excited to announce my latest @pluralsight course is now live! Learn how to identify and defeat #codeobfuscation in #malware, both native and interpreted code is covered. pluralsight.com/courses/malwar…
pluralsight.com
Malware Analysis: Identifying and Defeating Code Obfuscation
Malware Analysis: Identifying and Defeating Code Obfuscation
Protect your apps with Verimatrix's award-winning #codeobfuscation. A cyber criminal’s first step of an attack is to analyze code and gain an understanding of your app logic with code obfuscation, #hackers can’t get started. #appsecurity Learn more: bit.ly/3pM3uYv
🔐 Elevate Your Web Security! 🔐 Discover the HTML CSS Obfuscate Code Project, your key to stronger HTML & CSS security. Simple, yet formidable against threats. #WebSecurity #CodeObfuscation

#6/10 🕵️♂️🔍🚨 Attackers are always looking for weaknesses in smart contracts. Developers should consider using techniques such as code obfuscation and white-box cryptography to make it more difficult for attackers to exploit vulnerabilities. #CodeObfuscation #WhiteBoxCryptography
A #softwaredevelopmentcompany had been ordered by a judge to share its product's source code with a competitor. Unenthusiastic developers replaced all identifiers with 0's and O's and obediently shared the code. It compiled but otherwise was useless. #codeobfuscation #programming
Think your app code is safe? Think again. Read our detailed blog "Code Obfuscation: A Comprehensive Guide" Stay one step ahead of attackers. 🔗 Read the detailed blog here - lnkd.in/dth3gd2g #MobileAppSecurity #CodeObfuscation #AppProtection #ReverseEngineering




@00soon_svm #SOONISTHEREDPILL soon_svm’s smart contract code obfuscation for privacy without sacrificing functionality. #soon_svm #CodeObfuscation
@00soon_svm #SOONISTHEREDPILL soon_svm’s smart contract code obfuscation for privacy without sacrificing functionality. #soon_svm #CodeObfuscation
@00soon_svm #SOONISTHEREDPILL soon_svm’s smart contract code obfuscation for privacy without sacrificing functionality. #soon_svm #CodeObfuscation
#Daily_Share Welcome to read and share the newly published paper "Code Obfuscation: A Comprehensive Approach to Detection, Classification, and Ethical Challenges". Read via: mdpi.com/1999-4893/18/2… #codeobfuscation #cybersecurity #classificationofobfuscation #obfuscationtools
Sunday Read: Code Obfuscation & Why It Matters? Read all about it in our latest Glossary ➡️ xygeni.io/sscs-glossary/… #SundayReading #CyberSecurity #CodeObfuscation #AppSec #Xygeni
In this article, we're going to take a look at obfuscation in the JavaScript, creating ways to hide algorithms and make it harder to study code. - hackernoon.com/how-to-brew-ob… #codeobfuscation #reverseengineering
📱 Secure, quality mobile apps are no longer a luxury—they're a necessity! Learn how to protect your apps with #CodeObfuscation, monitor & react to threats in real-time, & automate testing. Watch now: bit.ly/3V31Cv7 Download the eBook: bit.ly/4fXp8St
Day 7: Exploring #codeobfuscation today! 🔒 how simple #encryptiontechniques can make #detection harder, giving insight into how malware hides from #AVs. #ethicalhacking isn’t just about finding #threats, it’s also about understanding how they evolve 😉 theblackgem.net/2024/11/CodeOb…
theblackgem.net
10-Day Plan for Learning Malware Development in C: Day 7 – Code Obfuscation and Detection Avoidance
We got to day 7! and this time we’ll explore code obfuscation , a technique used to make code harder to detect and analyze. Obfuscat...
Code in Pic #1 an example of #CodeObfuscation. No techie in their right mind would code that way. Even after heavy beverage consumption. That's the hint: it's too obviously silly. It could be a wink and a nod, to see if this passed muster (a code review at the coffee machine) 🔽
2/6 🧵 Code Obfuscation: Make your source code hard to interpret by transforming it with obscure variable names and code flow tweaks. 🔑 While it remains functionally the same, it becomes challenging to reverse-engineer. #ReverseEngineering #Cybersecurity #CodeObfuscation…

🔐 Elevate Your Web Security! 🔐 Discover the HTML CSS Obfuscate Code Project, your key to stronger HTML & CSS security. Simple, yet formidable against threats. #WebSecurity #CodeObfuscation

Uncover the myriad ways to obfuscate a simple JavaScript line like 'var a=1' with WangLiwen. Protect your code but use with caution! #JavaScript #CodeObfuscation #Cybersecurity ift.tt/hX8NcZE
(1/2) Ever wonder how #apps stay secure? #Codeobfuscation is the answer! Imagine your app #code as a treasure map. Code Obfuscation scrambles it into a crazy puzzle, leaving pirates scratching their heads! #CyberSecurity #mobilesecurity #Android #iOS #DataSecurity #viralpost

🔐 Just dropped a project that takes your ASM code to the next level! Check it out now: github.com/c4ln/ASM-Obfus… 💡👾 #Assembly #CodeObfuscation #Security
*** Differences in #codeobfuscation and #malware detection
Breaking state-of-the-art binary code obfuscation goo.gl/vao3Mv #Reversing #CodeObfuscation #ExploitDev #Infosec

💡Learn in-depth about state-of-the-art of 💻#codeobfuscation & deobfuscation techniques to find out how it complicates #reverseengineering from this hands-on training by Tim @mr_phrazer 🛡️Register to Upskill➡️bit.ly/3WsTmno #NullconDE2023 #infosec #Cybersecurity

🔓Learn about👨💻#codeobfuscation & deobfuscation techniques to find out how it complicates RE 💡Apply all techniques to break obfuscation schemes from this training by @mr_phrazer ⚠️Grab early bird offer before New Year's eve👉bit.ly/3WsTmno #NullconDE2023 #infosec

👨💻Learn in-depth about state-of-the-art of #codeobfuscation & deobfuscation techniques & break these obfuscation schemes 💻A complete hands-on #training by Tim @mr_phrazer is here! ✅Register to Upskill now ➡️bit.ly/3WsTmno #NullconDE2023 #Infosec #Cybersecurity

Thank u @jasvir for sending me your "Surreptitious Software" book, which coined "chenxification". Finally got the book and love the special program on the inside cover! #codeobfuscation #softwaresecurity

#Codeobfuscation is one of the best ways to harden mobile apps #security. bit.ly/2Tw6gF7 #reverseengineering #opensource #programming #coding #javascript #android #cyber #applicationsecurity #ITsecurity #networksecurity #tech #informationsecurity #safegaurding #ios

2/6 🧵 Code Obfuscation: Make your source code hard to interpret by transforming it with obscure variable names and code flow tweaks. 🔑 While it remains functionally the same, it becomes challenging to reverse-engineer. #ReverseEngineering #Cybersecurity #CodeObfuscation…

HTML Source Code Encryption: Cara Menyembunyikan dan Melindungi Script HTML #CodeObfuscation, #CSS, #Encryption, #FrontEndDevelopment, #HTML, #JavaScript, #Script, #Security, #WebDevelopment, tools online lupakerja.com/2023/03/html-s…

(1/2) Ever wonder how #apps stay secure? #Codeobfuscation is the answer! Imagine your app #code as a treasure map. Code Obfuscation scrambles it into a crazy puzzle, leaving pirates scratching their heads! #CyberSecurity #mobilesecurity #Android #iOS #DataSecurity #viralpost

Protect your apps with Verimatrix's award-winning #codeobfuscation. A cyber criminal’s first step of an attack is to analyze code and gain an understanding of your app logic with code obfuscation, #hackers can’t get started. #appsecurity Learn more: bit.ly/3pM3uYv

Have an Android app that needs code obfuscation + hardening to protect it from hacker attacks? Sign up for a free 30-day trial of Verimatrix App Shield verimatrix.com/products/app-s… #codeobfuscation #verimatrix #freetrial

Do iOS apps need obfuscation? Short Answer - Yes, they need it. Obfuscation will protect the machine code from being copied and altered without permission. and make it extremely difficult for hackers to identify vulnerabilities in your code. #codeobfuscation #iosapps

Implement a range of obfuscation methods thanks to our code obfuscation solutions 🌀 🔺 Control Flow Obfuscation 🔺 Symbol Obfuscation 🔺 String Obfuscation 🔺 Arithmetic Obfuscation Learn more: hubs.ly/Q01dV8ww0 #codeobfuscation #vmxproduct #cybersecurity

🔐 Elevate Your Web Security! 🔐 Discover the HTML CSS Obfuscate Code Project, your key to stronger HTML & CSS security. Simple, yet formidable against threats. #WebSecurity #CodeObfuscation

Code Obfuscation As A Method Of Software Protection buff.ly/3hFIzkQ #CodeObfuscation #SoftwareDevelopment #SoftwareProtection #BestPractices #ReverseEngenieering #ObfuscationTools #Data #workflow #Experts #technology

Think your app code is safe? Think again. Read our detailed blog "Code Obfuscation: A Comprehensive Guide" Stay one step ahead of attackers. 🔗 Read the detailed blog here - lnkd.in/dth3gd2g #MobileAppSecurity #CodeObfuscation #AppProtection #ReverseEngineering




Something went wrong.
Something went wrong.
United States Trends
- 1. Gibbs 17.8K posts
- 2. #WWERaw 28.7K posts
- 3. Mike Evans 8,832 posts
- 4. Tez Johnson 2,495 posts
- 5. Lions 67.2K posts
- 6. Bucs 15.7K posts
- 7. Baker 24.8K posts
- 8. White House 227K posts
- 9. Dragon Lee 5,179 posts
- 10. #OnePride 5,770 posts
- 11. Josh Naylor 2,974 posts
- 12. Goff 7,434 posts
- 13. #TBvsDET 3,995 posts
- 14. Ben Solo 11.3K posts
- 15. Bron 19.7K posts
- 16. East Wing 44.6K posts
- 17. #RawOnNetflix N/A
- 18. Bieber 17.1K posts
- 19. AJ Lee 7,989 posts
- 20. Julio Rodriguez 1,992 posts