#networksecurity search results
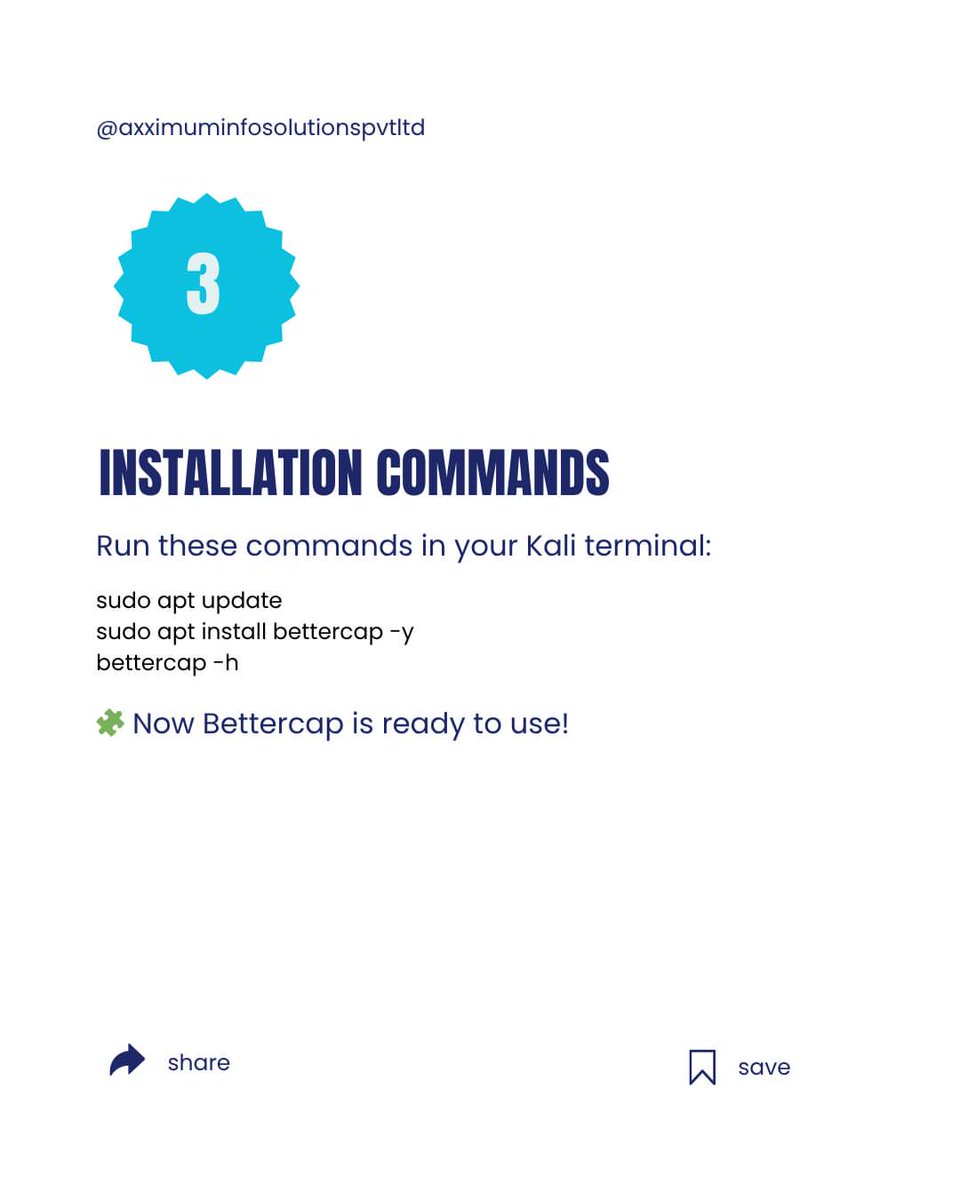
🛠️ Bettercap — Network Recon & MITM Framework Powerful toolkit for network monitoring, protocol inspection, and authorized MITM-style testing — ideal for defenders to validate detections and for learning how attackers operate. #Bettercap #NetworkSecurity #MITMDetection



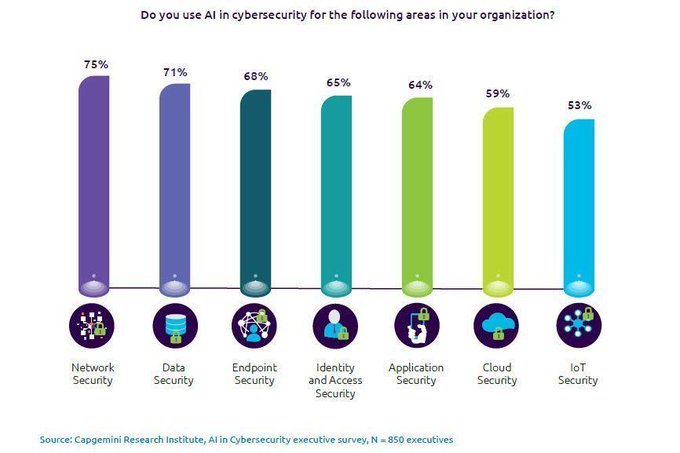
73% of enterprises are testing use cases for AI for cybersecurity across their organizations today with network security leading all categories. @capgemini @Irregulars bit.ly/3e3MLsH rt @antgrasso #AI #CyberSecurity #NetworkSecurity
🎛️ Monitorizamos tu sistema 24/7. Si pasa algo, lo sabemos antes que tú. #consultoriainformaticamadrid #networksecurity #cloudsecurity

We’re honored to be named a Network Security Market Leader in Cyber Defense Magazine's Top InfoSec Innovator Awards for 2025! 🔗 Read the press release: ow.ly/gXxj50XiZX0 #FireMon #NetworkSecurity

AI cybersecurity detects threats 1000x faster than humans! Trust Procal Technologies to secure your future. #Cybersecurity #AI #NetworkSecurity #TechTrends @bsindia

Network Security today it’s the Core of new network deployments. Watch these Tech tips to discover it #networksecurity #CyberSecurity #ransomwareattack #ransomwaredefense
🚀 Could vibe coding redefine the future of programming? Its rapid integration has echoes of potential security pitfalls. Understand the shift: #hacking #python #NetworkSecurity bit.ly/3IKx3HV

Your home router is often the weakest link in your network security. Change the default password immediately and update the firmware regularly. Protect your perimeter 🏠 #NetworkSecurity #Router

📧 Are your Microsoft 365 users unknowingly compromised in the Gmail 183M breach? Attackers could exploit weak credentials shared across platforms. Investigate & secure your network. Details: #microsoft365 #CyberThreats #NetworkSecurity bit.ly/4hy4n1G

🧠 Best Tools for Port Scanning & Network Analysis 🔍 #NetworkSecurity #PortScanning #CyberSecurity #Nmap #Masscan #Netcat #EthicalUse #NetworkAnalysis #InfoSec #EducationOnly
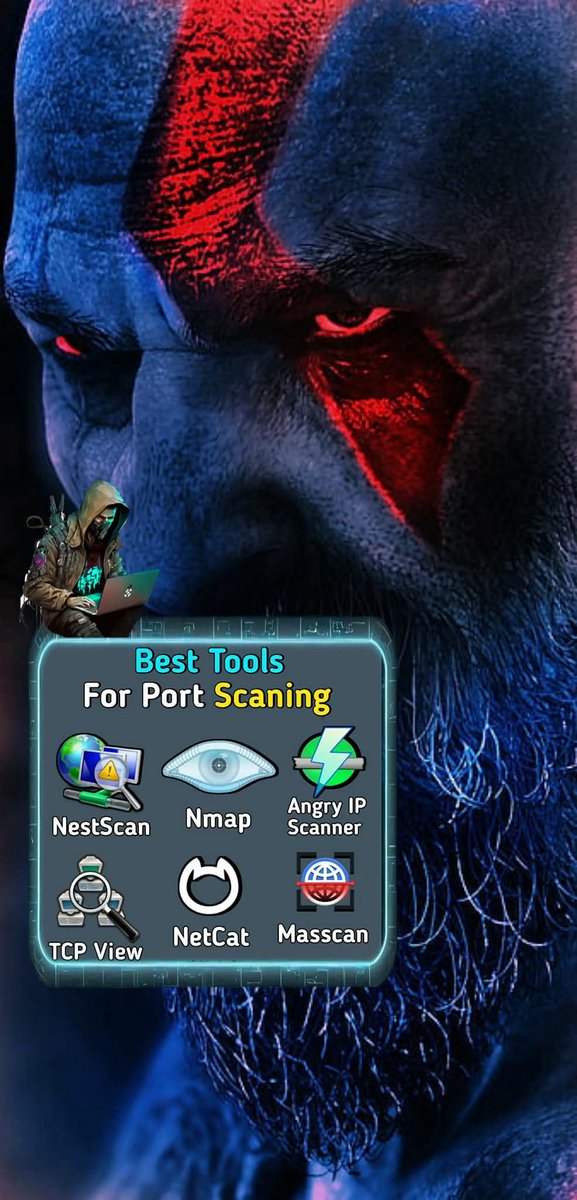
#CyberSec #KaliLinux #NetworkSecurity #WebSecurity #HackingTools #CyberAwareness #RedTeam #SecureCoding #Pentester

Anyone else feel like they’re not telling us what’s really going on? Either AI is writing all their code or these services are under attack. Second outage in one week fox4news.com/news/att-amazo… #CyberSecurity #NetworkSecurity @awscloud @ATT
Unlike other chains that prune history, @AutonomysNet embraces #Data as power. More storage means higher participation and deeper #NetworkSecurity. Every block written makes the #Web3 foundation stronger.
Most blockchains treat data bloat as a liability. Autonomys treats it as an asset. More data on the network → more farmers join → more decentralization → more security. Instead of pruning or archiving history like other chains, Autonomys is built to scale. Every new piece of…
🔐 How does AI compliance impact Linux system security for startups? It’s all about accountability in model explainability, data traceability & hardened servers. Find out why this is critical knowledge for IT admins. #hacking #cybersec #NetworkSecurity bit.ly/4oJSgAZ

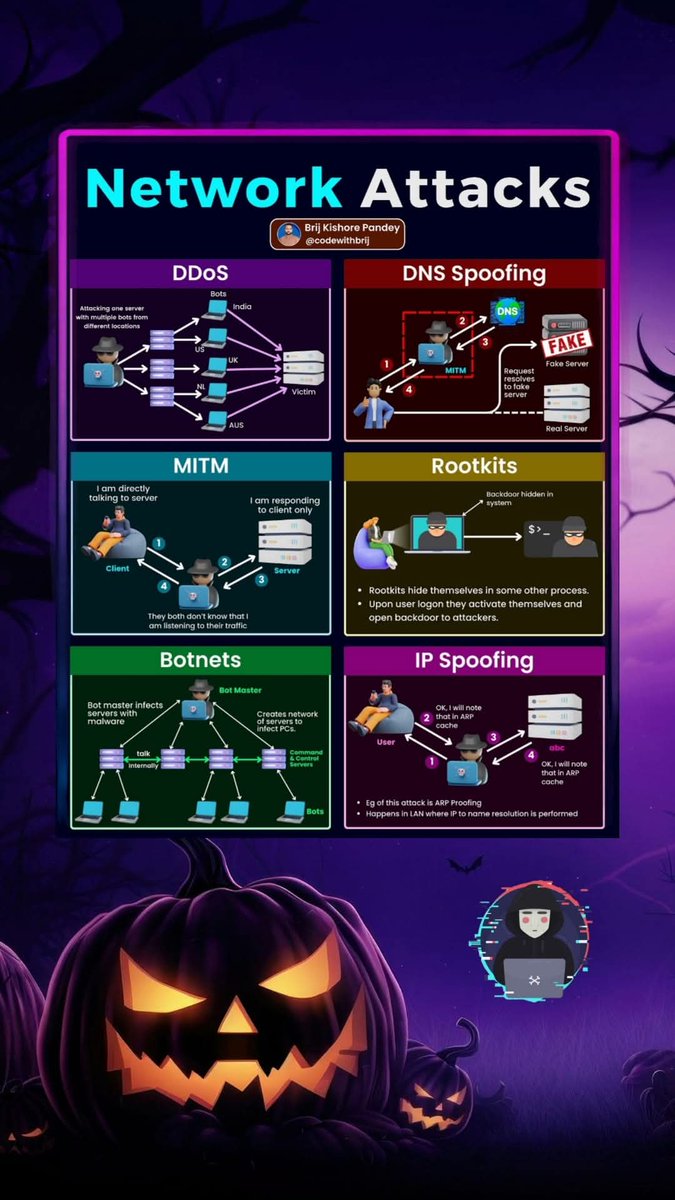
⚔️ Network Threat Scenarios — What Defenders Should Know Brief overview of common network threat scenarios, detection signals, and mitigation priorities to help defenders anticipate and respond effectively. For educational use only. #NetworkSecurity #ThreatHunting
AI identifies suspicious network activities for businesses. #ThreatDetection #NetworkSecurity AI helps in password security by analyzing breach patterns. #AIPrivacy #CyberProtection
Varonis Threat Labs revealed a flaw where CloudTrail Network Activity events paired with a VPC endpoint deny policy can expose AWS Account IDs for S3 buckets. AWS has issued a redaction fix. #AWSCloud #NetworkSecurity #USA ift.tt/nyqD9WG
🛑 Let’s talk token deprecation: GitHub is saying goodbye to time-based tokens to prevent package hijacking. Start transitioning your workflows now—don’t wait for the next worm attack. #cybersec #programming #NetworkSecurity bit.ly/3IFuYgg
Learn how UniFi's CyberSecure service, integrated with their new WiFi 7 access points, can protect your business without the enterprise price tag. #Cybersecurity #NetworkSecurity #SMB Read more 👉 lttr.ai/AkHmj #iFeelTech

🎛️ Monitorizamos tu sistema 24/7. Si pasa algo, lo sabemos antes que tú. #consultoriainformaticamadrid #networksecurity #cloudsecurity

Portnox and CrowdStrike have partnered to provide real-time, risk-based network access control combining continuous device telemetry with Zero Trust scoring. #CyberSecurity #ZeroTrust #NetworkSecurity #TechPartnership techdayca.com/story/portnox-…
Streamline your network with Sophos Switch! Enjoy secure, cloud-managed access that integrates with your Sophos ecosystem. Learn more >> cloudware.africa/sophos/sophos-…. #NetworkSecurity #CloudManagement #Sophos #ITInfrastructure #BusinessContinuity

🔮 Identifying harmful content is more challenging as unmoderated AI image generation grows. Read all 7 cyber predictions from our experts #cybersecurity #informationsecurity #networksecurity #ai #msp #cyberthreats #ransomware #phishing #DNSFilter dnsfilter.com/newsroom/2026-…
Your daily sip of security, brewed fresh by Mocha Samich Software ☕🛡️ Tip: Secure your home Wi-Fi. Change default passwords on routers. #NetworkSecurity

We love hearing from our users - one customer highlighted how rate-based monitoring and automatic Flow Spec routing made it easier to detect and stop DDoS traffic, without needing constant input from engineers. Read more: eu1.hubs.ly/H0pdWN50 #NetworkSecurity #DDosDetection

Your home router is often the weakest link in your network security. Change the default password immediately and update the firmware regularly. Protect your perimeter 🏠 #NetworkSecurity #Router

#NetworkSecurity Submit your Research Article..!!! 17th International Conference on Wireless, Mobile Network & Applications (WiMoA 2025) November 22 ~ 23, 2025, London, United Kingdom Webpage URL; iccsea2025.org/wimoa/index Contact Us : [email protected]

👥 Validator Set — The consensus committee! Group of validators actively participating in block production and network security. The chosen ones keeping blockchain alive! 🛡️✨ 🔗 chainterms.com/glossary.html#… #ValidatorSet #ConsensusCommittee #NetworkSecurity #BlockProducers
🛠️ Bettercap — Network Recon & MITM Framework Powerful toolkit for network monitoring, protocol inspection, and authorized MITM-style testing — ideal for defenders to validate detections and for learning how attackers operate. #Bettercap #NetworkSecurity #MITMDetection





73% of enterprises are testing use cases for AI for cybersecurity across their organizations today with network security leading all categories. @capgemini @Irregulars bit.ly/3e3MLsH rt @antgrasso #AI #CyberSecurity #NetworkSecurity

New Mexico invests $315M in #QuantumComputing infrastructure spanning fabrication facilities venture capital funds & a state-wide quantum #network fostering public-private partnerships & research commercialization. #networksecurity #VentureCapital #nextgentech #NewMexico #news

#CyberSec #KaliLinux #NetworkSecurity #WebSecurity #HackingTools #CyberAwareness #RedTeam #SecureCoding #Pentester

AI cybersecurity detects threats 1000x faster than humans! Trust Procal Technologies to secure your future. #Cybersecurity #AI #NetworkSecurity #TechTrends @bsindia

🕵️ What’s hiding on your network? Untracked devices and unknown software = serious risk. If you can’t see it, you can’t secure it. Start with a full network audit. 👉 Book your free IT Strategy Session: parried.com/get-started #CybersecurityMonth #NetworkSecurity #ITSecurity…



🎛️ Monitorizamos tu sistema 24/7. Si pasa algo, lo sabemos antes que tú. #consultoriainformaticamadrid #networksecurity #cloudsecurity

Can I DIY SSL on Debian without a chaos monkey throwing bananas at my server? 🐒🍌 Source: devhubby.com/thread/how-to-… #ITSecurity #NetworkSecurity #Encryption #TechTutorial #webserver #web

Legal & General establishes digital infrastructure investment fund, targeting #datacenters, fiber #networksecurity & #Cloud assets to drive connectivity, digital economy growth & institutional investor returns. #DataCenter #CloudComputing #SmartInvesting #DigitalTransformation

Firewalls aren’t enough alone. USB Security Locking Devices for Business and Network Module Locks for Corporate Networks add essential physical protection. #USBLocks #NetworkSecurity #CyberSecurity #DataProtection #CorporateSecurity #ConnectivityCenter

Your home router is often the weakest link in your network security. Change the default password immediately and update the firmware regularly. Protect your perimeter 🏠 #NetworkSecurity #Router

Smith has named Mike Mercado Chief Information Officer! In this role, Mike will lead our #IT department in enhancing our advanced #NetworkSecurity and developing cutting-edge technology initiatives. Read more: smth.bz/rwj #IntelligentDistribution

SpaceX launches 51 @Starlink satellites from Vandenberg expanding low Earth orbit broadband improving global connectivity scaling next-generation internet #networksecurity for commercial & strategic applications. #SpaceX #Starlink #Internetheld #LEO #SpaceExploration #aerodrome

🎙️ Meet your security dream team: Ahmed Abeer, making complex networks simple for 15+ years, and Chris Noon, 1 of ~300 VCDXs, driving 4000% growth at Alkira. Real experts. Real results. Register in comment. #CloudSecurity #NetworkSecurity #NetworkInfrastructure #asaservice

📧 Are your Microsoft 365 users unknowingly compromised in the Gmail 183M breach? Attackers could exploit weak credentials shared across platforms. Investigate & secure your network. Details: #microsoft365 #CyberThreats #NetworkSecurity bit.ly/4hy4n1G

Dr. Shereen Ismail, Research Scientist: Networking & Cybersecurity at Merit Network, will present two research papers at the @IEEEorg UEMCON 2025 Conference! linkedin.com/feed/update/ur… #Cybersecurity #Research #NetworkSecurity #Innovation #IEEEConference #TexasAM

Mix of UDP attack types with a total capacity of 35.45 Gbps and 5.37 Mpps, including heavy DNS amplification, were smoothly filtered by our PYRUS DDoS protection appliance. Customer stayed online and unaffected ✅ #DDoS #CyberSecurity #NetworkSecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Halloween 86.4K posts
- 2. Prince Andrew 45.6K posts
- 3. Ryan Clark 4,195 posts
- 4. Georgetown 2,128 posts
- 5. Henry 48.2K posts
- 6. #TNFonPrime 1,336 posts
- 7. #RavensFlock 2,983 posts
- 8. Jaire N/A
- 9. Heritage 54.8K posts
- 10. Sydney Sweeney 114K posts
- 11. Morgan Geekie N/A
- 12. Thursday Night Football 4,446 posts
- 13. Usha 38.3K posts
- 14. Mike Reilly N/A
- 15. UTSA 1,715 posts
- 16. #LightningStrikes N/A
- 17. $AMZN 51.7K posts
- 18. King Charles 14.7K posts
- 19. Go to TikTok 5,030 posts
- 20. Giannis 19.6K posts


































































