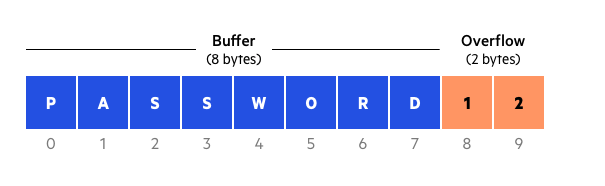
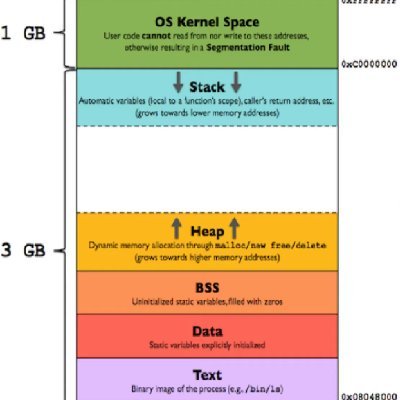
#bufferoverflow hasil pencarian
It starts with basic #bufferoverflow attacks and builds into learning the skills needed to crack the critical security mitigations protecting enterprises.

Lmfao. #chatgpt can be such a push over sometimes. I barely had to bully it into make a #bufferoverflow example for me lmfao. #CyberSec #exploits #aisecurity #chatgptsec #z0ds3c

Algunas fotos de mi Conferencia en la X Edición de @Fu_Turismo , Foro Nacional para Empresarios del Turismo. En la primera fui cazado explicando de manera sencilla a los asistentes conceptos complejos como el de #bufferoverflow . Muchas gracias por contar conmigo 🙏🔥💪🏻❤️




A High-severity flaw (CVE-2025-13654) in the Duc disk usage tool risks DoS and information leaks. An integer underflow in buffer.c allows out-of-bounds memory read. Update to v1.4.6 immediately. #Duc #LinuxSecurity #BufferOverflow #Cybersecurity securityonline.info/high-severity-…
Poniendo lavadora tras regresar de la #sh3llcon2025 y al ver su fallo se me ha ocurrido este ejemplo de “Buffer Overflow” como analogía en comparación al mundo real físico #WashingMachine #BufferOverflow #PlannedObsolescence #BeGoodBeHackers
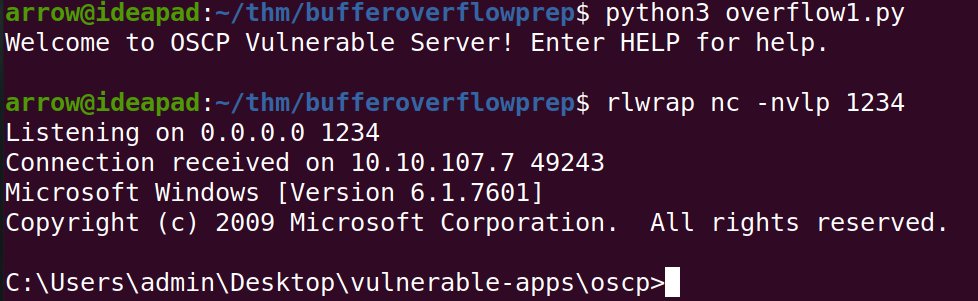
Mastering buffer overflows in Vulnserver is essential for exploit development. WinDBG aids in debugging vulnerabilities by controlling EIP and generating shellcode. A must-learn for secure environments! 🔍⚙️ #ExploitDev #BufferOverflow link: ift.tt/fFk6AGK

Buffer Overflow: Belleğin Sessiz Zafiyeti 🎯 Buffer Overflow, bellek bloklarının sınırlarını aşarak bilgisayar programlarında meydana gelen bir güvenlik açığıdır. 🔍 Tanım: Buffer, veriyi geçici olarak saklamak için ayrılan bir bellek alanıdır. #BufferOverflow bu alana izin…

#EthicalHacking #BufferOverflow Cominciamo a organizzare lo studio di uno degli argomenti piu importanti per la certificazione eCPPT.

Kudos to the creator of Day 6 in the @RealTryHackMe Advent of Cyber lab! The explanation was spot-on and made the learning experience enjoyable. 👏 Just incase you missed it youtu.be/D_tVQ49SizY?si… #AdventOfCyber #CyberSecurity #BufferOverflow

CVE-2025-21333 exposes a heap-based buffer overflow in Windows 11’s vkrnlintvsp.sys, risking privilege escalation. Microsoft issued patch KB5050021 on January 14, 2024. 🔒🔧 #WindowsSecurity #BufferOverflow #USA link: ift.tt/W6MUJqX

Want to exploit a buffer overflow? You must watch this video by Andrew Bellini (@d1gitalandrew)! Follow along as he walks through a #bufferoverflow vulnerability using his tool, Overflowme (which you can find on his #GitHub in the YouTube video description). This video also…

🔍 ¿Qué es un Buffer Overflow? Explicación clara y rápida para profesionales de la ciberseguridad linkedin.com/posts/the-hack… 🔐 #Ciberseguridad #BufferOverflow #HackingÉtico #Infosec #ExploitDevelopment #SeguridadInformática #CyberSecurity #DevSecOps #MemoryManagement #SecureCodin




What is a Buffer Overflow | Attack Types and Prevention Methods | Imperva #bufferoverflow imperva.com/learn/applicat…
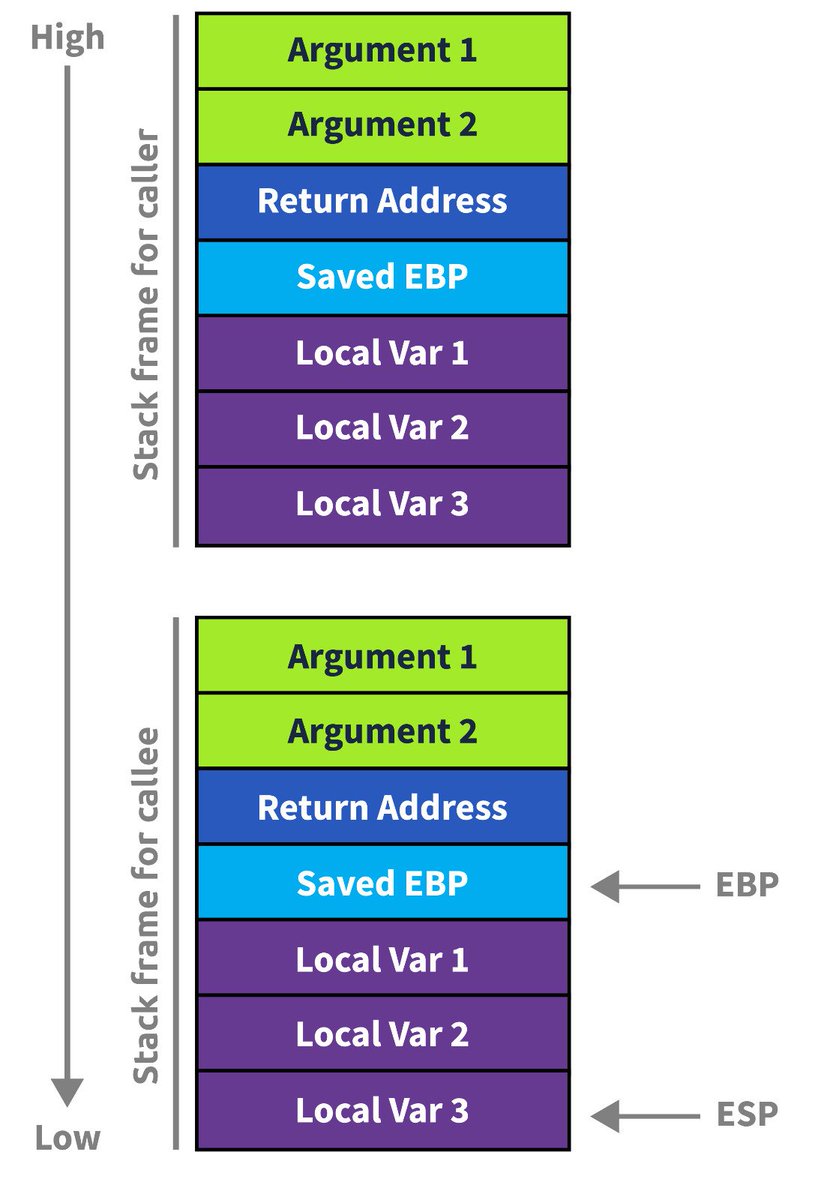
جمعة مباركة ♥️ ده شرح بسيط لترتيب ال Stack frame و الاتاكس الي ممكن تحصل عليه linkedin.com/posts/mx0o14_c… #CyberSecurity #BufferOverflow #StackFrame #ROP #StackSmashing #MemoryProtection #PenetrationTesting #Security
Die Programmiersprache C ist in Wirklichkeit eine groß angelegte Psy-Op der NSA gewesen, um sichere Software zu verhindern. #BufferOverflow
🚨Vulnerability Tuesday🚨 A buffer overflow occurs when excess data overwrites memory, potentially crashing apps or letting attackers run malicious code. Proper buffer size is key for security. 💻 #BufferOverflow #CyberSecurity #SecurityBoat

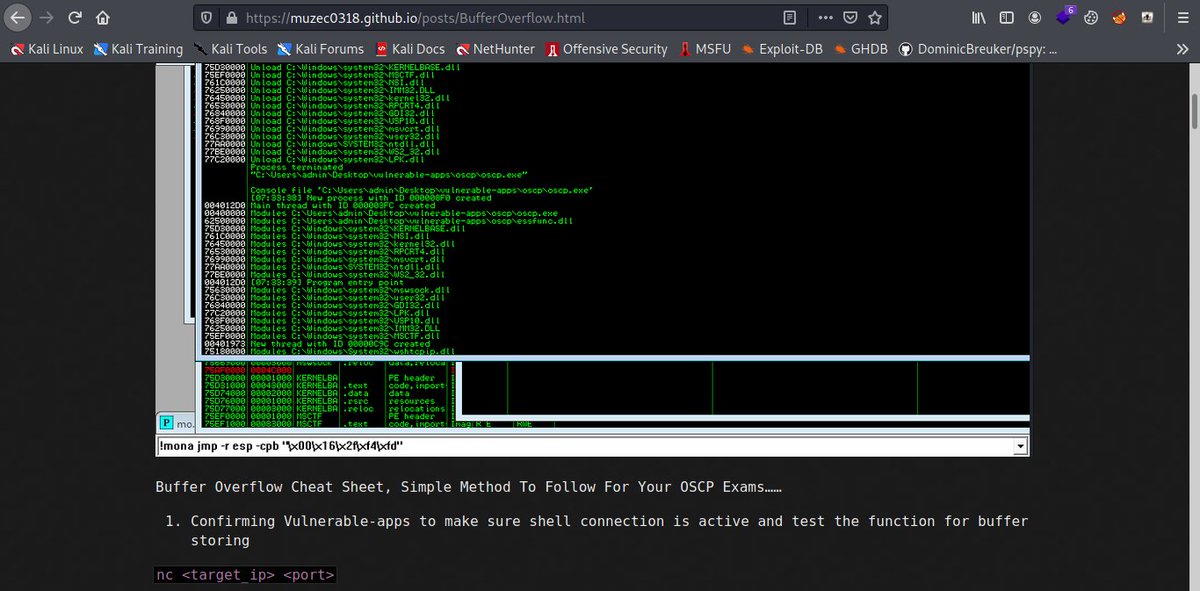
Yes Finally 😄😄😄😄 My Cheat Sheet For Buffer Overflow Buffer Overflow Cheat Sheet;- muzec0318.github.io/posts/BufferOv… #BufferOverflow #Pentesting #Hacking
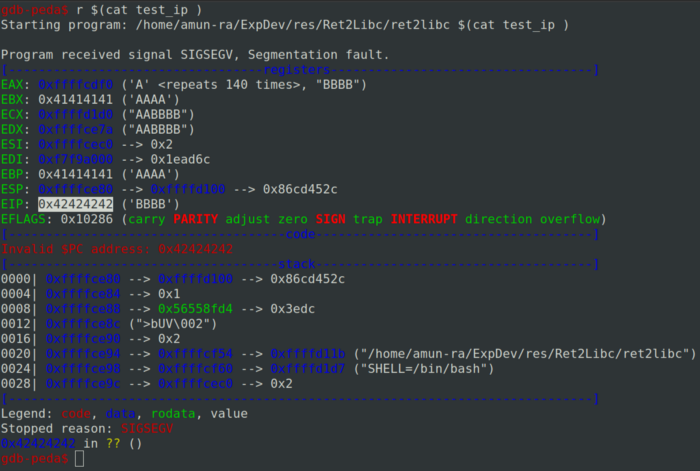
Return To LIBC Attack (ret2libc) aidenpearce369.github.io/exploit%20deve… #Pentesting #BufferOverflow #ExploitDev #CyberSecurity #Infosec



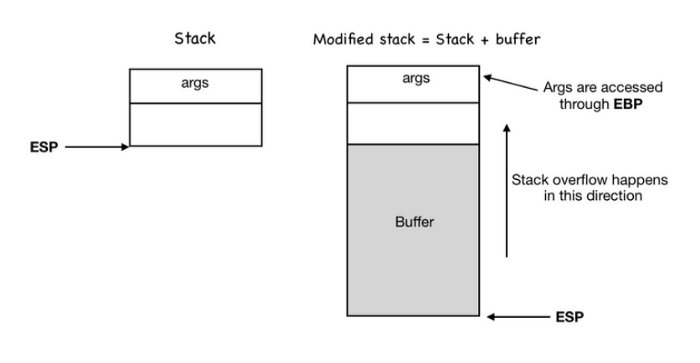
Exploit Development, Part 1: Anatomy of a Buffer Overflow #bof #bufferoverflow #exploitdevelopment #whatsapp #cybersecurity bit.ly/2rphf46

WAScan - Web Application Scanner goo.gl/QEWmCC #BufferOverflow #CommandInjection #Cookie #Firewall #LDAP #Linux #Python #SQLi
Buffer Overflows for Dummies sans.org/reading-room/w… #Pentesting #BufferOverflow #CyberSecurity #Infosec



Buffer Overflow (ret2func) aidenpearce369.github.io/exploit%20deve… #Pentesting #BufferOverflow #Exploit #CyberSecurity #Infosec

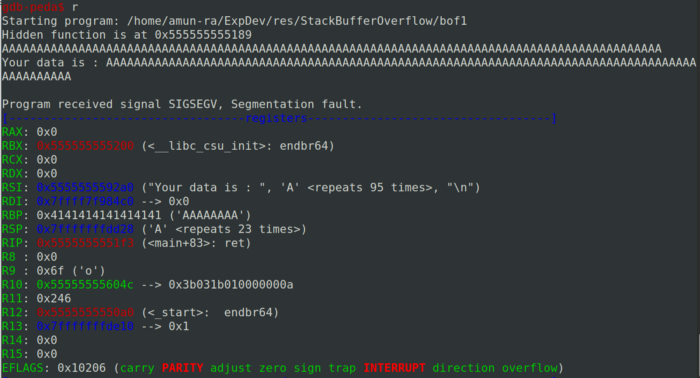
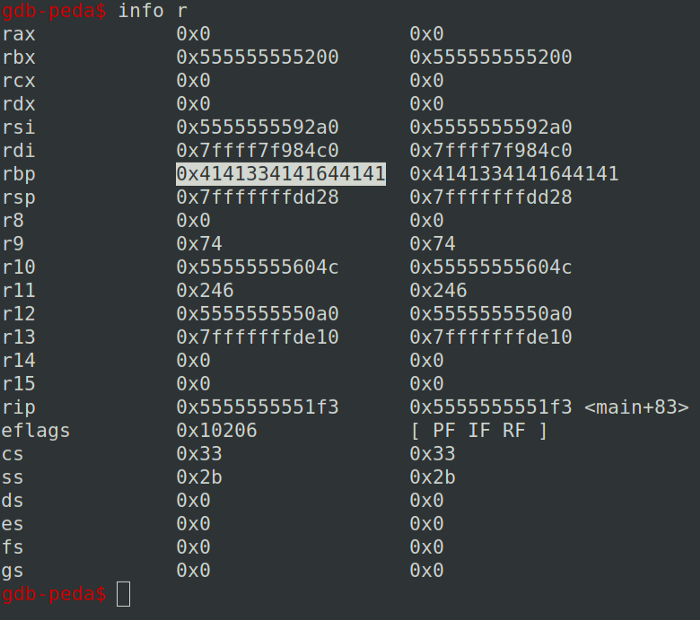
Exploiting a Windows-Based Buffer Overflow infosecwriteups.com/exploiting-a-w… #BufferOverflow #Windows10 #Hacking #Cybersecurity #Infosec




Amazing CD Ripper 1.2 Buffer Overflow #0day #BufferOverflow #0day_Hejap packetstormsecurity.com/files/166380/A…

Got Overwrite infosecwriteups.com/got-overwrite-… #Exploitation #Stackoverflow #BufferOverflow #ExploitDev #Cybersecurity



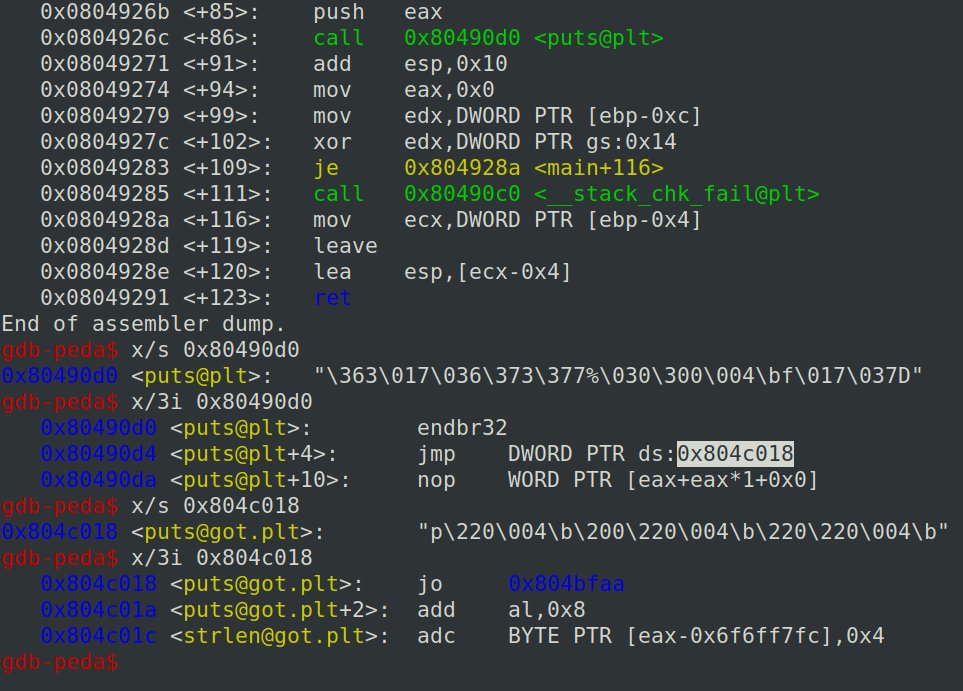
Muzec's Cyber Security Blog muzec0318.github.io/posts/BufferOv… #Pentesting #BufferOverflow #Hacking #Infosec


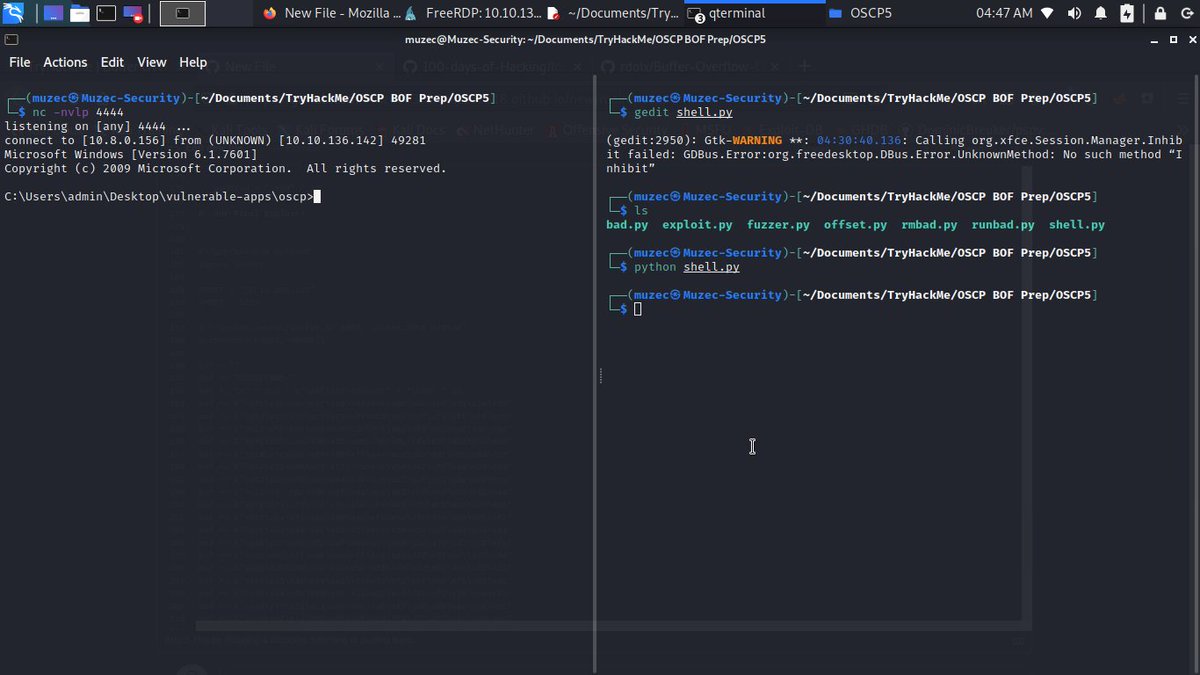
Live de Overview do treinamento de Desenvolvimento de Exploits, quer saber mais sobre o treinamento? Público alvo, módulos, conteúdo? Então não vai perder a Live né? Te encontro na quarta (27/05) à 21h07. #m4v3r1ck #helviojunior #bufferoverflow #exploit #dica

Exploit Development, Part 1: Anatomy of a Buffer Overflow #exploitdevelopment #bufferoverflow #cybersecurity #cyberwarrior hackers-arise.com/single-post/20…

I worked all day on WarFTP exploit development following the book and I finally got it. I could understand all the steps from the #bufferoverflow and got a reverse #shell. What a feeling! #hacking #pentesting @georgiaweidman

Something went wrong.
Something went wrong.
United States Trends
- 1. Chiefs 114K posts
- 2. Harada 6,645 posts
- 3. Mahomes 41.4K posts
- 4. Good Monday 33K posts
- 5. Tekken 16.1K posts
- 6. ORM HAUS NOWHERE GOP 86.1K posts
- 7. #OrmxHausNowhereBKK 85.1K posts
- 8. Kelce 25.4K posts
- 9. #ITWelcomeToDerry 72.4K posts
- 10. Texans 49.2K posts
- 11. rUSD N/A
- 12. Andy Reid 7,051 posts
- 13. #MondayMotivation 5,932 posts
- 14. #BaddiesUSA 33.3K posts
- 15. #Ormkornnaphat 86.5K posts
- 16. Proverbs 4,847 posts
- 17. Pennywise 36.2K posts
- 18. Rashee Rice 10.8K posts
- 19. Cambodia 47K posts
- 20. Stroud 10.9K posts