#bufferoverflow arama sonuçları
Memory spills out, Code's boundaries blurred and broken, Chaos in the stack. #Haiku #Bufferoverflow #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
It starts with basic #bufferoverflow attacks and builds into learning the skills needed to crack the critical security mitigations protecting enterprises.

Lmfao. #chatgpt can be such a push over sometimes. I barely had to bully it into make a #bufferoverflow example for me lmfao. #CyberSec #exploits #aisecurity #chatgptsec #z0ds3c

Algunas fotos de mi Conferencia en la X Edición de @Fu_Turismo , Foro Nacional para Empresarios del Turismo. En la primera fui cazado explicando de manera sencilla a los asistentes conceptos complejos como el de #bufferoverflow . Muchas gracias por contar conmigo 🙏🔥💪🏻❤️




Mastering buffer overflows in Vulnserver is essential for exploit development. WinDBG aids in debugging vulnerabilities by controlling EIP and generating shellcode. A must-learn for secure environments! 🔍⚙️ #ExploitDev #BufferOverflow link: ift.tt/fFk6AGK

Poniendo lavadora tras regresar de la #sh3llcon2025 y al ver su fallo se me ha ocurrido este ejemplo de “Buffer Overflow” como analogía en comparación al mundo real físico #WashingMachine #BufferOverflow #PlannedObsolescence #BeGoodBeHackers
Kudos to the creator of Day 6 in the @RealTryHackMe Advent of Cyber lab! The explanation was spot-on and made the learning experience enjoyable. 👏 Just incase you missed it youtu.be/D_tVQ49SizY?si… #AdventOfCyber #CyberSecurity #BufferOverflow

Buffer Overflow: Belleğin Sessiz Zafiyeti 🎯 Buffer Overflow, bellek bloklarının sınırlarını aşarak bilgisayar programlarında meydana gelen bir güvenlik açığıdır. 🔍 Tanım: Buffer, veriyi geçici olarak saklamak için ayrılan bir bellek alanıdır. #BufferOverflow bu alana izin…

Want to exploit a buffer overflow? You must watch this video by Andrew Bellini (@d1gitalandrew)! Follow along as he walks through a #bufferoverflow vulnerability using his tool, Overflowme (which you can find on his #GitHub in the YouTube video description). This video also…

#EthicalHacking #BufferOverflow Cominciamo a organizzare lo studio di uno degli argomenti piu importanti per la certificazione eCPPT.

CVE-2025-21333 exposes a heap-based buffer overflow in Windows 11’s vkrnlintvsp.sys, risking privilege escalation. Microsoft issued patch KB5050021 on January 14, 2024. 🔒🔧 #WindowsSecurity #BufferOverflow #USA link: ift.tt/W6MUJqX

🔍 ¿Qué es un Buffer Overflow? Explicación clara y rápida para profesionales de la ciberseguridad linkedin.com/posts/the-hack… 🔐 #Ciberseguridad #BufferOverflow #HackingÉtico #Infosec #ExploitDevelopment #SeguridadInformática #CyberSecurity #DevSecOps #MemoryManagement #SecureCodin




🚨Vulnerability Tuesday🚨 A buffer overflow occurs when excess data overwrites memory, potentially crashing apps or letting attackers run malicious code. Proper buffer size is key for security. 💻 #BufferOverflow #CyberSecurity #SecurityBoat

جمعة مباركة ♥️ ده شرح بسيط لترتيب ال Stack frame و الاتاكس الي ممكن تحصل عليه linkedin.com/posts/mx0o14_c… #CyberSecurity #BufferOverflow #StackFrame #ROP #StackSmashing #MemoryProtection #PenetrationTesting #Security
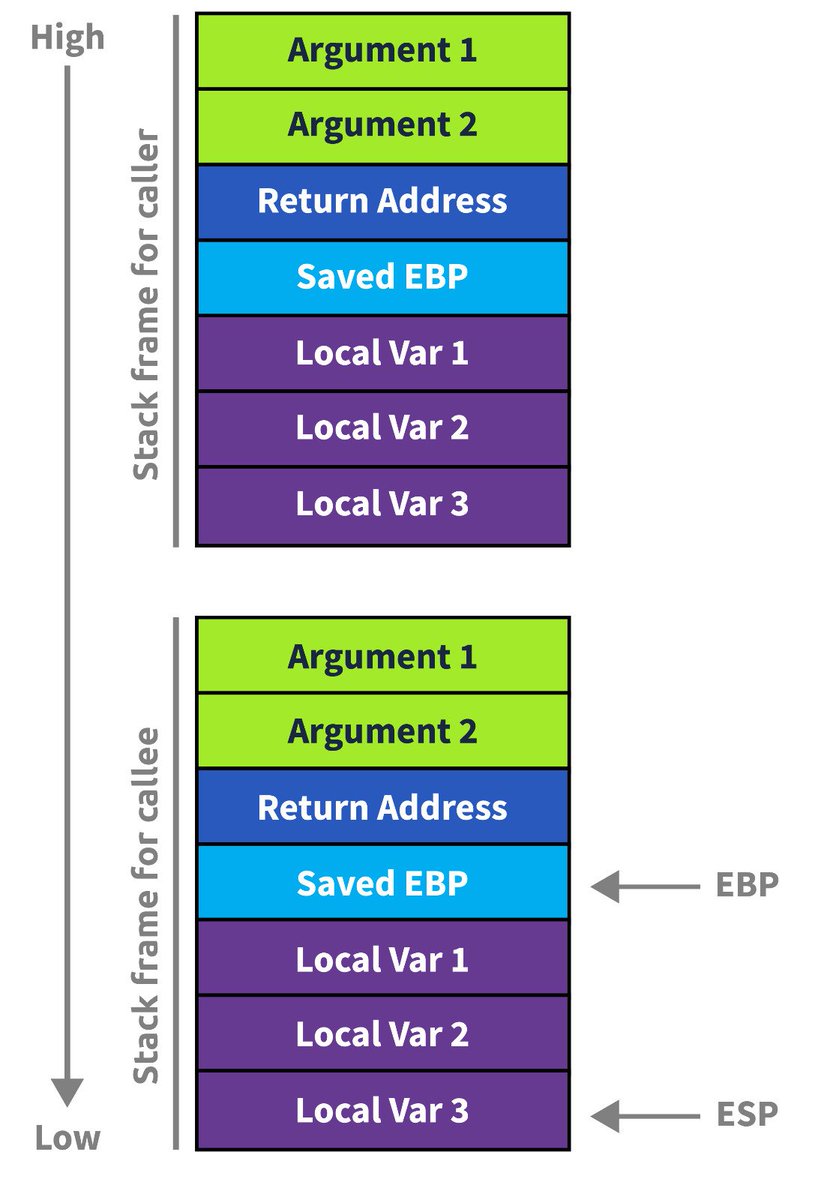
I published my WriteUp of MagicGardens box from @hackthebox_eu 👇👇👇 v0lk3n.github.io/writeup/HackTh… I hope that you will like it :) #HTB #BufferOverflow #CSRF #XSS #DevTools #Missconfiguration #docker #django #Pentest #CyberSecurity #HackTheBox

In security we're never always safe #bufferoverflow
What is a Buffer Overflow | Attack Types and Prevention Methods | Imperva #bufferoverflow imperva.com/learn/applicat…
Something went wrong.
Something went wrong.
United States Trends
- 1. The BONK 83.5K posts
- 2. FINALLY DID IT 351K posts
- 3. $TONO N/A
- 4. JUNGKOOK FOR CHANEL BEAUTY 90.3K posts
- 5. Good Thursday 22.8K posts
- 6. Lakers 46.2K posts
- 7. Godzilla 22.3K posts
- 8. Spurs 36.9K posts
- 9. Doug Dimmadome 11.8K posts
- 10. Dolly Parton 3,552 posts
- 11. Zane 5,576 posts
- 12. PETA 31.8K posts
- 13. TOP CALL 10.5K posts
- 14. Jim Ward 12.1K posts
- 15. Usher 3,829 posts
- 16. Sherrone Moore 65.4K posts
- 17. Wemby 5,637 posts
- 18. Erika 184K posts
- 19. Marcus Smart 2,279 posts
- 20. Sheen 54.6K posts