#malwareanalysis نتائج البحث
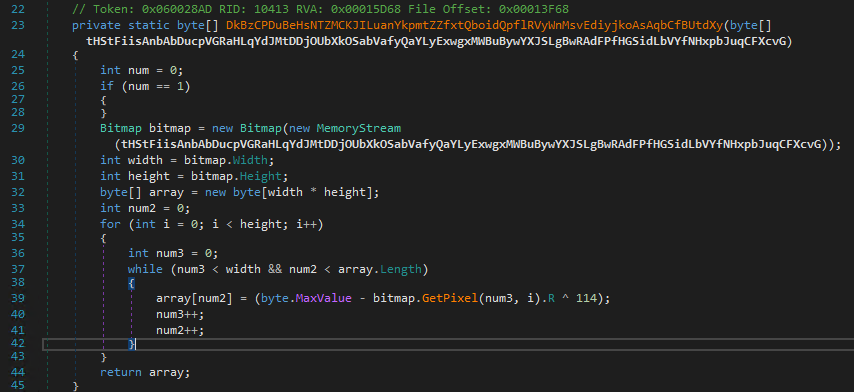
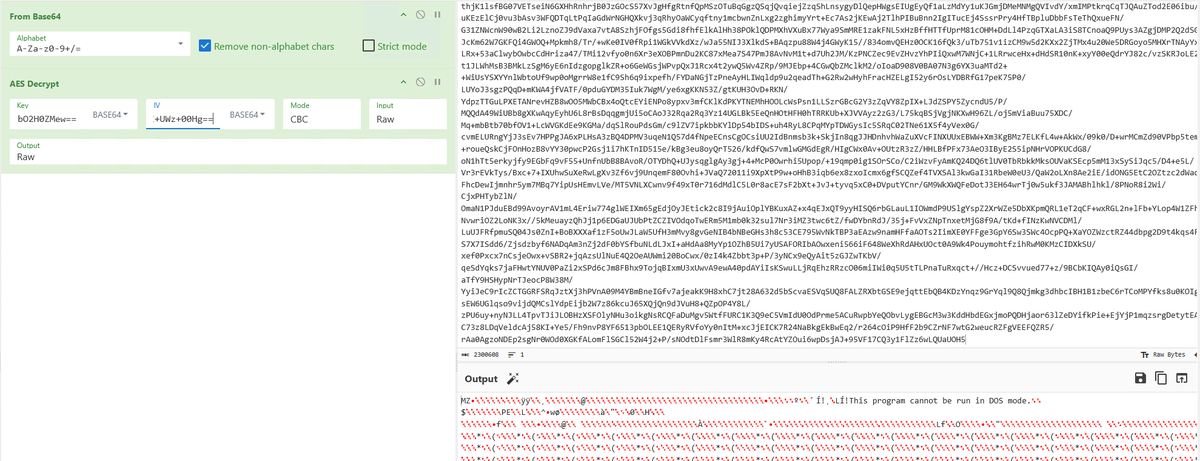
🧵New: "From Pixels to Payloads" — We reverse-engineered a multi-stage .NET loader hiding Lumma Stealer in BMPs via stego trick: (255-R)^0x72. Donut Loader → C# Injector → Lumma in memory. 🧠👇 github.com/ShadowOpCode/S… #LummaStealer #Infosec #MalwareAnalysis #ThreatIntelligence


Happened to analyze a suspicious macOS file. A developer downloaded Git from a git lookalike domain. Turns out to be #AMOS :) Thanks to @obje tool Lulu @patrickwardle Check out for more in the thread #macos #malwareanalysis #malware #infostealer

Excited to speak at @WWHackinFest – Deadwood 2025! Catch my talk: “N-Grams, Quantum, and Malware – A Recipe for Chaos?” Let’s get nerdy in the Black Hills! #WWHF #InfoSec #MalwareAnalysis #Cybersecurity #QuantumSecurity
⛓️💥 Don't want to pay the GTI bundled price increases with #VirusTotal? Just break up: bit.ly/4mBUTTZ ☝️ Use the link above to learn why you should switch to RL for #ThreatIntel & #MalwareAnalysis.
Learn from the author of "Mastering Malware Analysis", @Amr_Thabet, at his intensive training sessions: Advanced Malware Hunting & Prevention: start October 27 👉cqureacademy.com/cyber-security… PowerShell Basics: start November 3 👉cqureacademy.com/cyber-security… #MalwareAnalysis #PowerShell

New drop: Patching Binary for Dumping. Conceptually learn how analysts find hidden binaries and what hot-patching means. Full lesson on YouTube youtu.be/o8b2OrFyHBs?si… Labs & challenges at academy.hack-defender.com #HackDef #MalwareAnalysis #ReverseEngineering #infosec
Silent Watcher: Cmimai Stealer Unveiled Discover how this stealthy VBS-based malware uses PowerShell and Discord webhooks to exfiltrate sensitive data. Learn about its operational workflow and how to defend against it. labs.k7computing.com/index.php/sile… #MalwareAnalysis #DataProtection

Learn about Xenomorph malware in part 6 of our Mobile Malware Series➡️ 8ksec.io/mobile-malware… #mobilesecurity #androidsecurity #malwareanalysis

⚙️Aprende qué es el análisis estático y el análisis dinámico.⚙️ Desglosamos ambos métodos de análisis y cómo se utilizan para detectar ciberamenazas. 🔗Te invitamos a ver el video completo: youtu.be/nnjxl1rupWo #malwareanalysis #IA
🔍 A DLL isn’t a standalone file — it has no main function like an EXE. That’s why we need tools like WinDbg + SOS to uncover where execution really begins. In this week’s drop, we show you how. youtu.be/MsijfXAu3rA?si… #ReverseEngineering #dotnet #MalwareAnalysis #HackDef #dll
Attackers Abuse Velociraptor Forensic Tool to Deploy Visual Studio Code for C2 Tunneling dlvr.it/TNLcVP #Cybersecurity #ThreatHunting #MalwareAnalysis #DigitalForensics #RedTeam

Malware loves to hide. But real analysts know how to unpack it. 📦 Module 3: Packers & Obfuscators Now live on our YouTube channel! 🔗Link in BIO #malwareanalysis #hackdefenderacademy #cybersecurity #reverseengineering #infosec #cybersecuritytraining
🚨 Malware infra is volatile. ~50% of Cobalt Strike servers vanish in 5 days. ~40% of Viper hides on port 60000. 🔎 Data freshness = critical. If you’re not tracking, you’re missing it. Latest from Censys → 🔗 hubs.ly/Q03BNq5F0 #ThreatIntelligence #SOTIR #MalwareAnalysis

Revisited my malware analysis project using FLARE VM and upgraded it with a custom YARA rule to hunt AgentTesla variants. Proud of how it turned out. Shoutout to @ireteeh and @Cyblackorg for this opportunity 🙂 #MalwareAnalysis #YARARules #Cybersecurity #ThreatHunting #FLAREVM

Project Ire autonomously identifies malware at scale microsoft.com/en-us/research… #MalwareAnalysis
⏰ Time is Running Out! ⏰ Don’t miss your chance to learn Malware Analysis with practical training using open-source tools. 💥 Get 50% OFF with code learnmalware0925 – offer ends September 30th! 👉 Enroll now: academy.cyber5w.com/courses/c5w-ma… #Cyber5W #MalwareAnalysis #CyberSecurity…

One of the biggest cybersecurity news outlets @TheHackersNews just featured our academy — and this is what they posted 👇 #malwareanalysis #hackdefenderacademy #cybersecurity #reverseengineering #infosec #Training
Mustang Panda's latest campaign targets the Tibetan community, using DLL side-loading via phishing to deliver malware through a decoy file named 'Voice for the Voiceless Photos.exe', as analyzed in a detailed report. #CyberSecurity #MalwareAnalysis 0x0d4y.blog/mustang-panda-…
0x0d4y.blog
Mustang Panda Employ Publoader Through ClaimLoader: Yes.. another DLL Side-Loading Technique...
In this new post I will analyze, once again, an execution chain of payloads delivered via Phishing from another Threat Actor China-Nexus, however, implementing the same TTP, yes, DLL Side-Loading! In...
🚨 New variant spotted: Matanbuchus 3.0 — a rebuilt malware loader advertised on underground forums. Features DNS/HTTPS C2, in-memory execution, reverse shell, morphing builds & multitenant panel. Price: $10K–$15K/month. Active threat. #CyberThreat #Infosec #MalwareAnalysis

🔍 Web Malware Scan Results Website: bacinovrsud.it Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/91fe7320-… #GenerativeAI #MalwareAnalysis #AppSec #Malware
🚨 Warning! PureRAT is evolving. Discover how this threat transforms from a simple infostealer into a full-blown Remote Access Trojan 🚨 in this essential analysis. Stay informed, stay secure! #Cybersecurity #MalwareAnalysis ⤵️
🚨 UTA0388's espionage malware evolved from HealthKick to the dangerous GOVERSHELL! Uncover the full evolution of this persistent threat. #CyberSecurity #MalwareAnalysis ⤵️
🔬 New video: Android Hacking 888 RAT 1.2.6 Watch: youtube.com/watch?v=qjRuu4… #MobileSecurity #MalwareAnalysis #ThreatHunting #888 #888RAT #RAT #androidhacking #hacking #mobilehacking

Have a question about your binaries? e.g., is this malware? are there any vulnerabilities, etc.🧩@ me with a downloadable link and your questions — I’ll run a full analysis for you. AI-powered reverse engineering, live 24x7. 📷 #MalwareAnalysis #ReverseEngineering #CyberSec…
🔍 Web Malware Scan Results Website: comune.gaiola.cn.it Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/ec590032-… #MalwareAnalysis #SOC #DigitalSecurity
🔍 Web Malware Scan Results Website: normalil.gov Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/f0dd83ba-… #DevSecOps #CyberDefense #MalwareAnalysis
🌱🕵️♀️ Every great hacker story starts with curiosity — the urge to ask “how does this work?” Join @_sudhackar at #NullconGoa2026 to advance that spark into a skill, learning through the complexities of #reverseengineering and #malwareanalysis. Know More: nullcon.net/goa-2026/train…

⚙️Aprende qué es el análisis estático y el análisis dinámico.⚙️ Desglosamos ambos métodos de análisis y cómo se utilizan para detectar ciberamenazas. 🔗Te invitamos a ver el video completo: youtu.be/nnjxl1rupWo #malwareanalysis #IA
⚙️Aprende qué es el análisis estático y el análisis dinámico.⚙️ Desglosamos ambos métodos de análisis y cómo se utilizan para detectar ciberamenazas. 🔗Te invitamos a ver el video completo: youtu.be/nnjxl1rupWo #malwareanalysis #IA
🔍 Web Malware Scan Results Website: windsorwi.gov Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/78ab0dd4-… #SOCAnalyst #RedTeam #MalwareAnalysis #WebSecurity #SOC
🔍 A DLL isn’t a standalone file — it has no main function like an EXE. That’s why we need tools like WinDbg + SOS to uncover where execution really begins. In this week’s drop, we show you how. youtu.be/MsijfXAu3rA?si… #ReverseEngineering #dotnet #MalwareAnalysis #HackDef #dll
Day 6/100 #CybersecurityChallenge Yesterday, I explored malware analysis techniques & tactics 🦠 Learned how analysts detect behaviors, persistence, and evasion methods. Another layer of understanding added to my #Cybersecurity journey. #MalwareAnalysis #100DaysOfCybersecurity
Mustang Panda's latest campaign targets the Tibetan community, using DLL side-loading via phishing to deliver malware through a decoy file named 'Voice for the Voiceless Photos.exe', as analyzed in a detailed report. #CyberSecurity #MalwareAnalysis 0x0d4y.blog/mustang-panda-…
0x0d4y.blog
Mustang Panda Employ Publoader Through ClaimLoader: Yes.. another DLL Side-Loading Technique...
In this new post I will analyze, once again, an execution chain of payloads delivered via Phishing from another Threat Actor China-Nexus, however, implementing the same TTP, yes, DLL Side-Loading! In...
Dynamic code loading shows up everywhere in Android, useful for devs and painful for analysts. I wrote about how it works, why it is abused, and how to spot it in the wild. reverselabs.dev/blog/dynamic-c… #ReverseEngineering #AndroidSecurity #MalwareAnalysis #ThreatDetection

✅Day 3: Tool highlight: Ghidra ✅Day 4: Top 5 skills every reverse engineer needs ✅Day 5: Personal story ✅Day 6: Malware in the real world Next week, I will dive into tools and practical knowledge. Stay tuned! #ReverseEngineering #MalwareAnalysis #RedTeam #EthicalHacker

🧵New: "From Pixels to Payloads" — We reverse-engineered a multi-stage .NET loader hiding Lumma Stealer in BMPs via stego trick: (255-R)^0x72. Donut Loader → C# Injector → Lumma in memory. 🧠👇 github.com/ShadowOpCode/S… #LummaStealer #Infosec #MalwareAnalysis #ThreatIntelligence




🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥 Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg. We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses. [1/24] 🖊️ #Malwareanalysis #Ghidra
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gG0vaUAAkrE4.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gOFMbIAA2_rv.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gVA0bMAAeWzo.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0hjgObwAAyIRM.png)
Excited to speak at @WWHackinFest – Deadwood 2025! Catch my talk: “N-Grams, Quantum, and Malware – A Recipe for Chaos?” Let’s get nerdy in the Black Hills! #WWHF #InfoSec #MalwareAnalysis #Cybersecurity #QuantumSecurity

The MasterFred malware exploits hidden overlays, abusive permissions, and JavaScript interfaces to steal sensitive user data. Read the full breakdown here: 8ksec.io/mobile-malware… #MalwareAnalysis #MasterFred #AndroidSecurity #DataBreach #DFIR #MobileSecurity

In one of the #MalwareAnalysis communities I’m in, we were talking about Go malware. Someone mentioned CAPA as a good tool. I have to say, it’s really helpful for finding the 50kb of interesting code buried inside a 5mb Go binary 😎What other tools do you use?

CyberChef Tips - Creating and Accessing Variables #CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis. [1/2] #malware #malwareanalysis
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTCaMAECV1x.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTabwAAd1RG.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTNa4AAkCq3.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQR2bEAAPiZM.png)
FLARE floss applied to all unpacked+dumped samples in Malpedia Nice project by Daniel Plohmann (@push_pnx) Blog post: danielplohmann.github.io/blog/2024/03/0… Github repo: github.com/malpedia/malpe… #malwareanalysis #infosec


Automating Malware Analysis Operations (MAOps) blogs.jpcert.or.jp/en/2023/01/clo… #Pentesting #MalwareAnalysis #CyberSecurity #Infosec
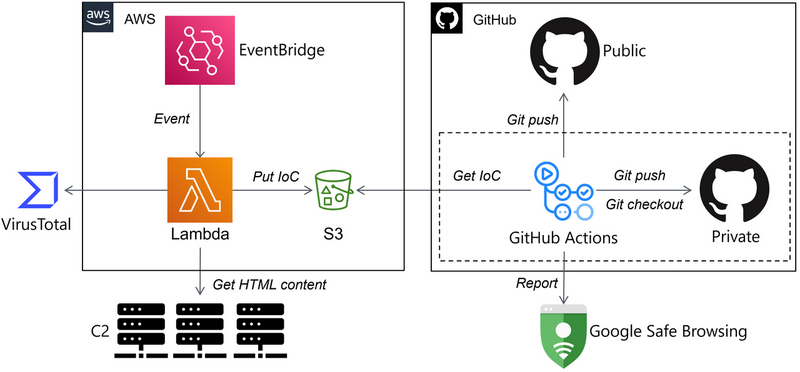
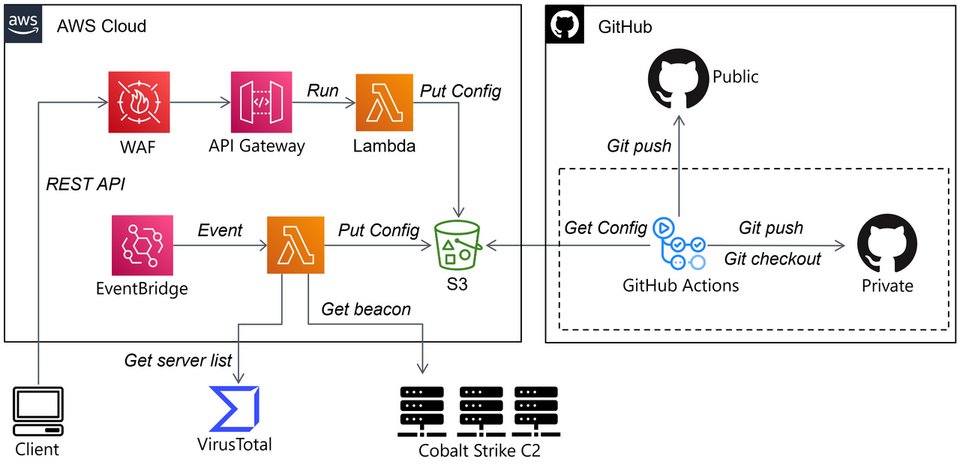
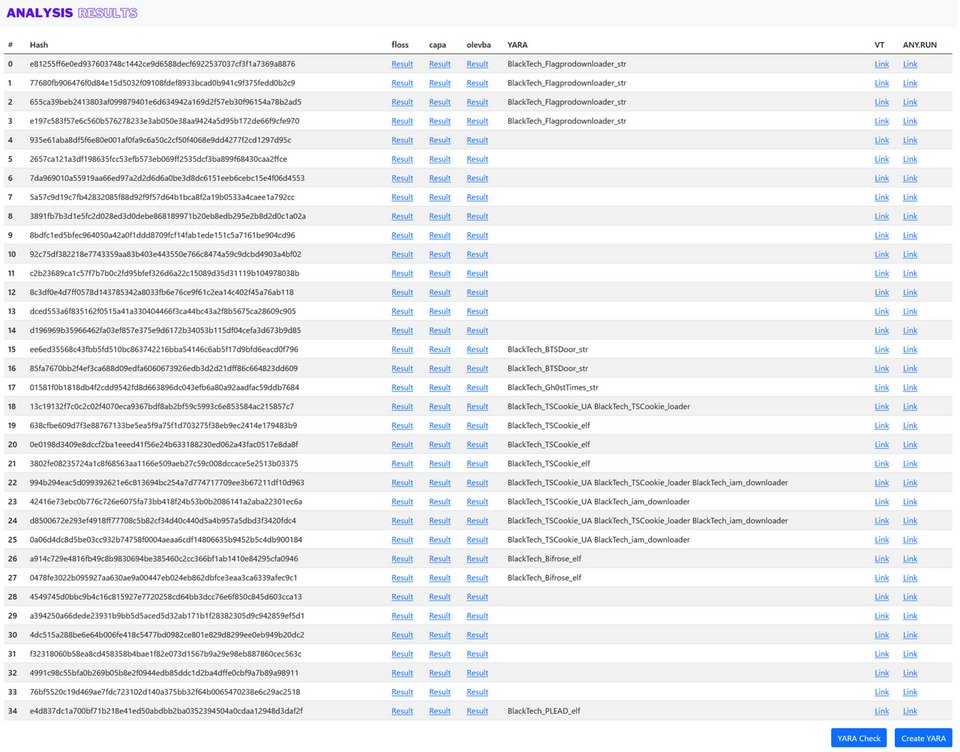
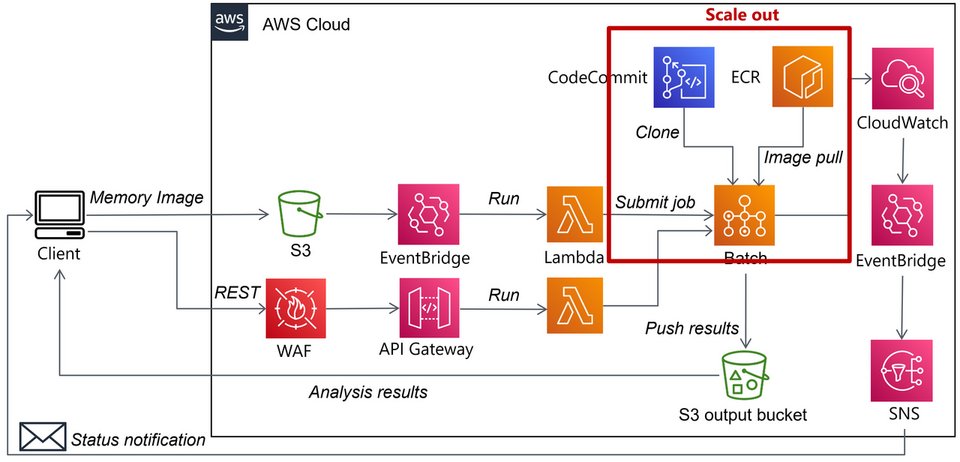
(PT_BR) O treinamento de MALWARE ANALYSIS 1 está com a próxima turma CONFIRMADO para 03/MAIO/2025. Informações adicionais podem ser obtidas no website da Blackstorm Security. #malwareanalysis #informationsecurity #malware #cybersecurity #threathunting #blueteam
🚨 New variant spotted: Matanbuchus 3.0 — a rebuilt malware loader advertised on underground forums. Features DNS/HTTPS C2, in-memory execution, reverse shell, morphing builds & multitenant panel. Price: $10K–$15K/month. Active threat. #CyberThreat #Infosec #MalwareAnalysis

🔍 #Opendir Alert! 📂 Target: ⚠️ hxxps://m[.]bureaux[.]fr/ 📄 Sample Files: Advanced IP Scanner.exe AnyDesk.exe AnyDesk.apk ⚡ Repository contains .apk & .exe files. Handle with caution! 🛡️ 🎯 Potential resource for malware analysts. #CyberSecurity #MalwareAnalysis…
![cyberfeeddigest's tweet image. 🔍 #Opendir Alert!
📂 Target:
⚠️ hxxps://m[.]bureaux[.]fr/
📄 Sample Files:
Advanced IP Scanner.exe
AnyDesk.exe
AnyDesk.apk
⚡ Repository contains .apk & .exe files. Handle with caution! 🛡️
🎯 Potential resource for malware analysts.
#CyberSecurity #MalwareAnalysis…](https://pbs.twimg.com/media/GhhcEuqWoAAUj9f.jpg)
Attackers Abuse Velociraptor Forensic Tool to Deploy Visual Studio Code for C2 Tunneling dlvr.it/TNLcVP #Cybersecurity #ThreatHunting #MalwareAnalysis #DigitalForensics #RedTeam

📱MasterFred malware uses hidden overlays, permissions, and JavaScript interfaces to steal sensitive data. Get the full analysis here: 8ksec.io/mobile-malware… 🚀For a deeper understanding of mobile malware techniques, explore our course: academy.8ksec.io/course/offensi… #MalwareAnalysis…

Dive deep into the world of antivirus systems. Learn how static, dynamic, heuristic and unpacking engines work to detect malware. hackers-arise.net/2023/12/12/eva… #CyberSecurity #MalwareAnalysis @three_cube

🦠💻Explore Part 2 of our Windows Malware blog series on process injections: 8ksec.io/dissecting-win… 📈Ready to sharpen your skills? Browse our courses here: academy.8ksec.io/course/practic… #MalwareAnalysis #Windows #ReverseEngineering

Learn about Xenomorph malware in part 6 of our Mobile Malware Series➡️ 8ksec.io/mobile-malware… #mobilesecurity #androidsecurity #malwareanalysis

Something went wrong.
Something went wrong.
United States Trends
- 1. Jets 67K posts
- 2. Aaron Glenn 2,720 posts
- 3. Justin Fields 4,627 posts
- 4. Garrett Wilson 1,601 posts
- 5. HAPPY BIRTHDAY JIMIN 57K posts
- 6. #JetUp 1,434 posts
- 7. Peart 1,570 posts
- 8. #BroncosCountry 2,228 posts
- 9. Tyrod N/A
- 10. #DENvsNYJ 1,573 posts
- 11. #OurMuseJimin 93.1K posts
- 12. Sherwood 1,162 posts
- 13. Kurt Warner N/A
- 14. Good Sunday 65.9K posts
- 15. Bam Knight N/A
- 16. Hail Mary 2,352 posts
- 17. #30YearsofLove 86.9K posts
- 18. Rich Eisen N/A
- 19. Brownlee N/A
- 20. Troy Franklin N/A


















































