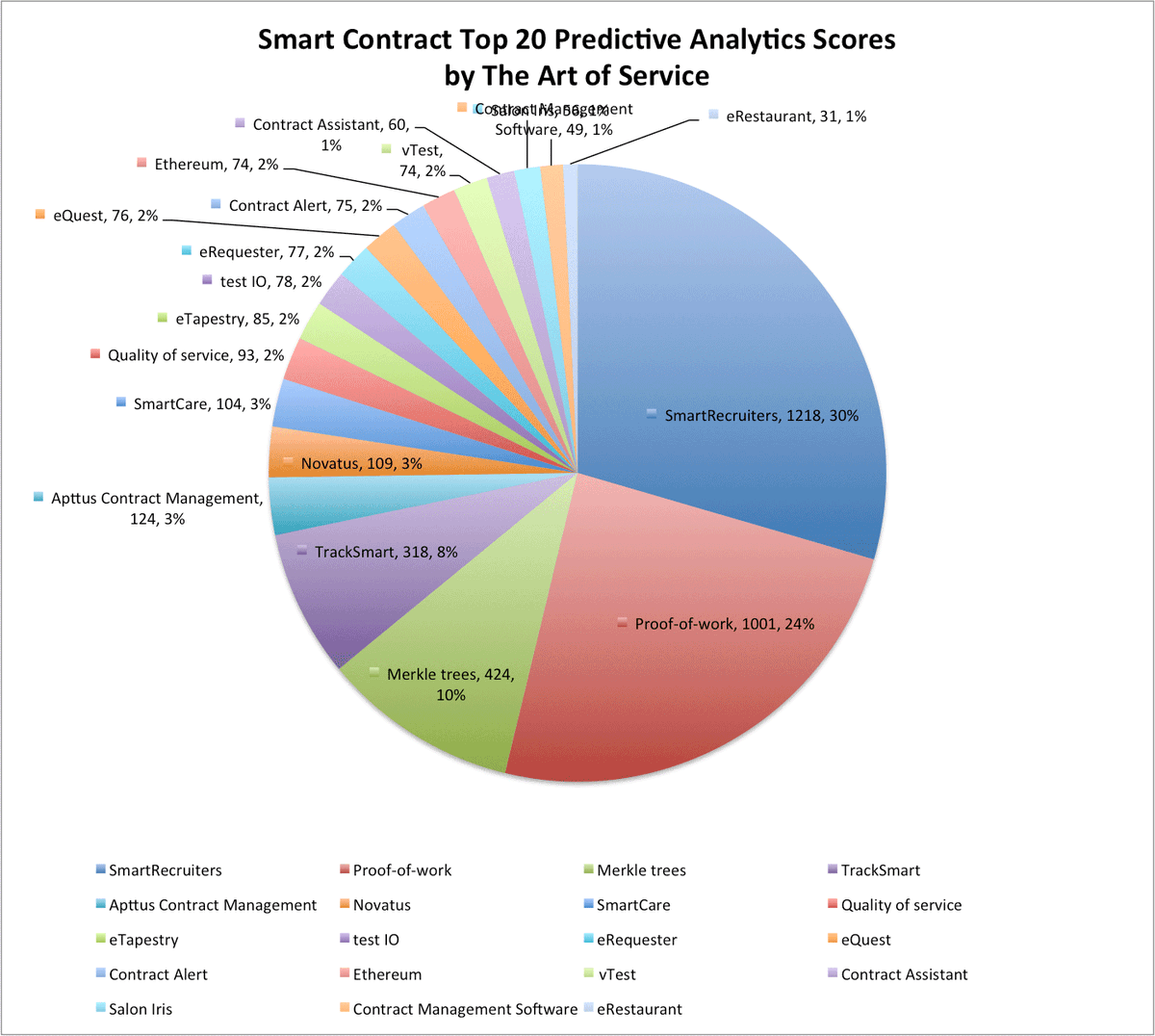
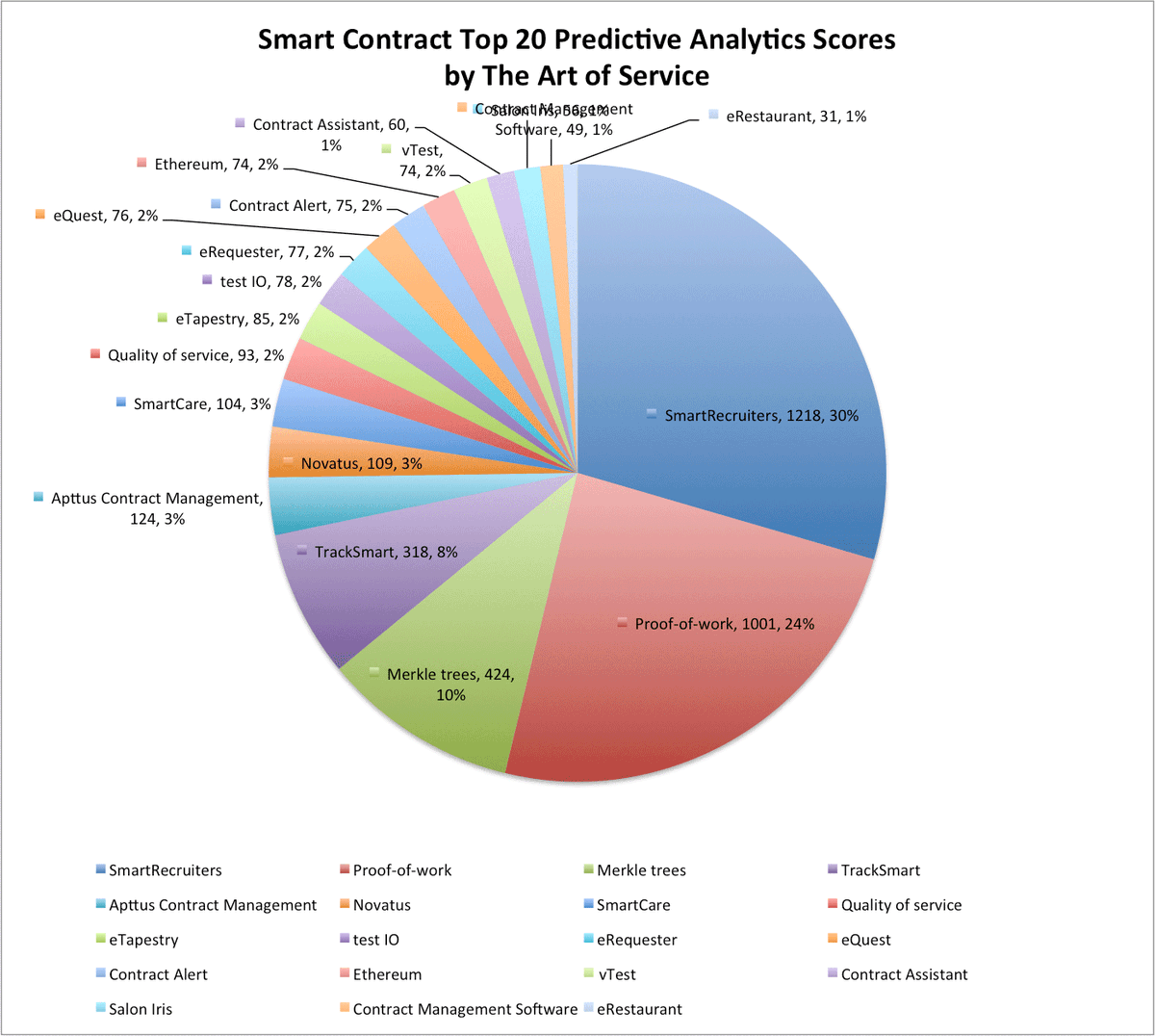
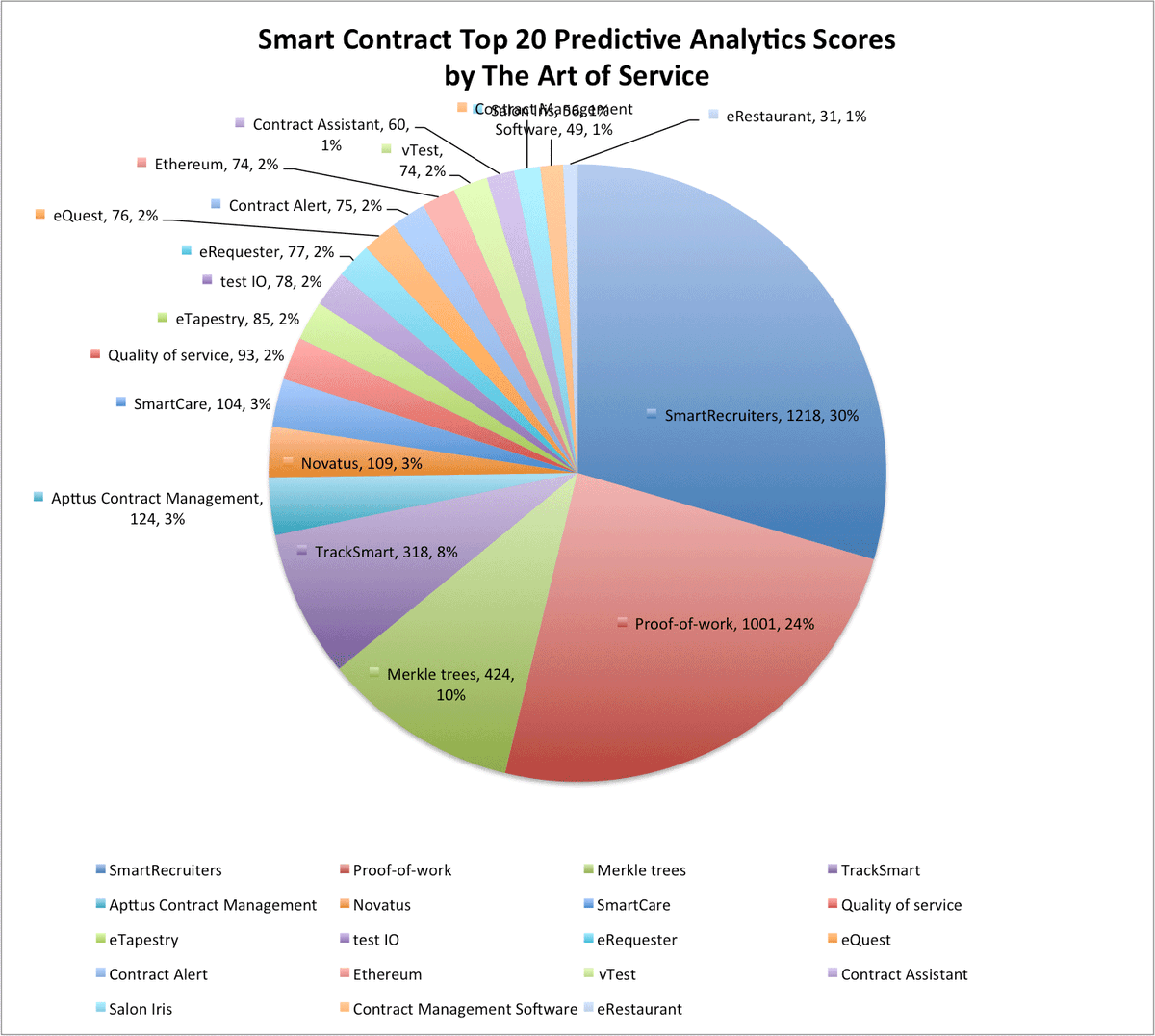
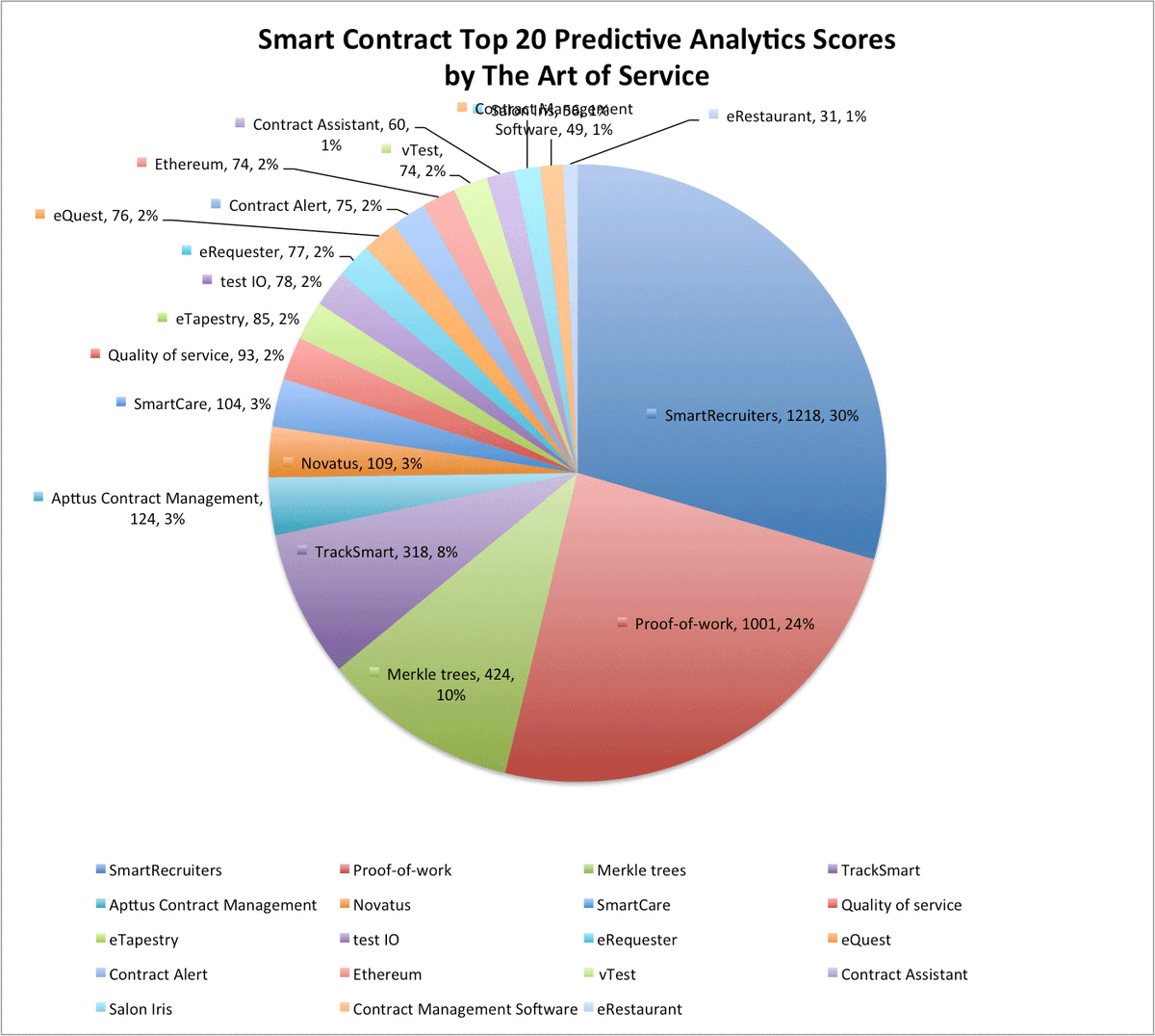
#securemultipartycomputation نتائج البحث


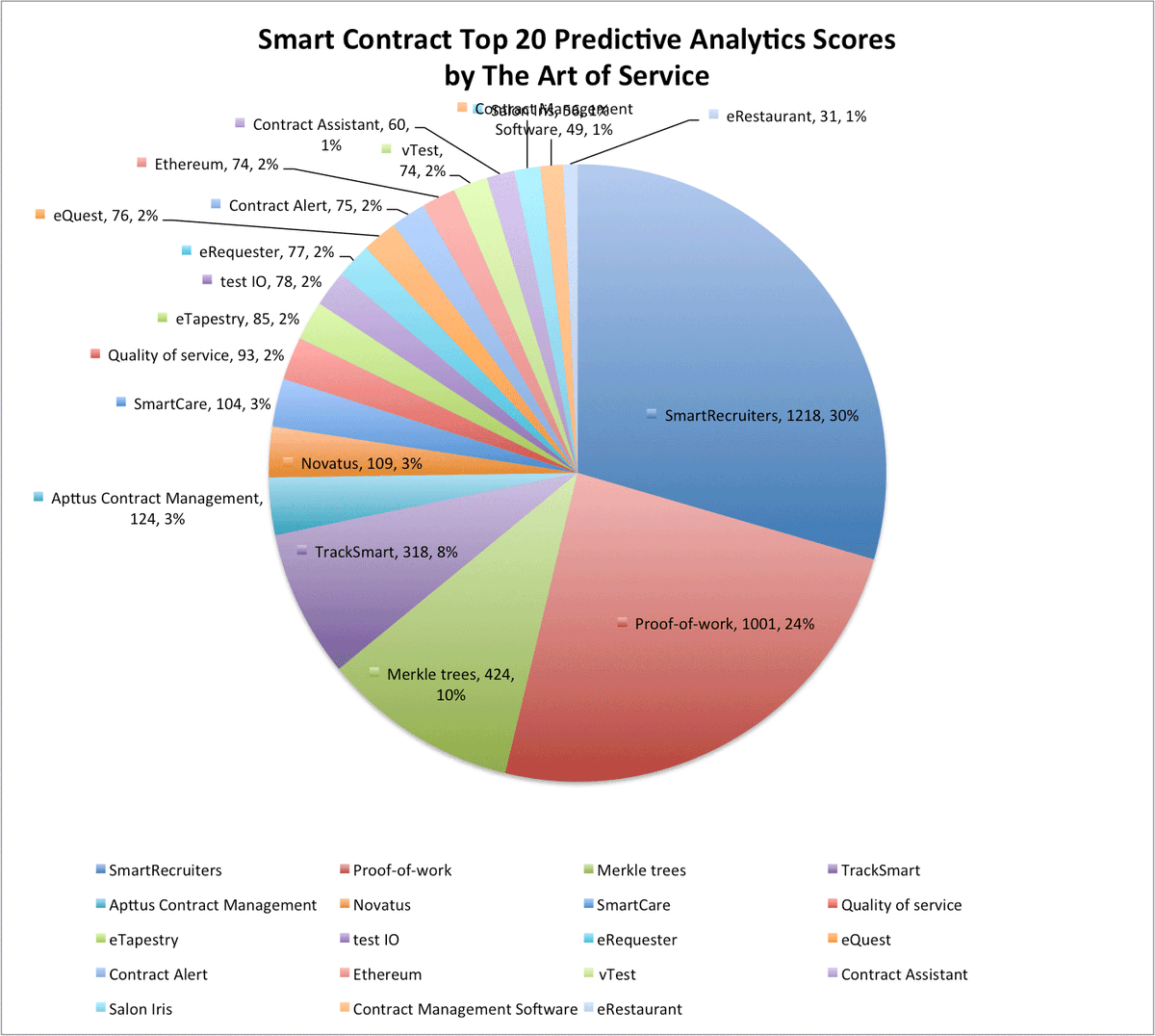
buff.ly/2bR87ek #SmartContract #Securemultipartycomputation #BestRead #RT #Unsurpassed #ContinuousIntegrati…

buff.ly/2csc1dc #SmartContract #Securemultipartycomputation #Compelling #Yes #ProjectPhase #Sizable #Neurom…

In case you are around, visit us at @FrankfurtSchool #SecureMultiPartyComputation #cloud #blockchain



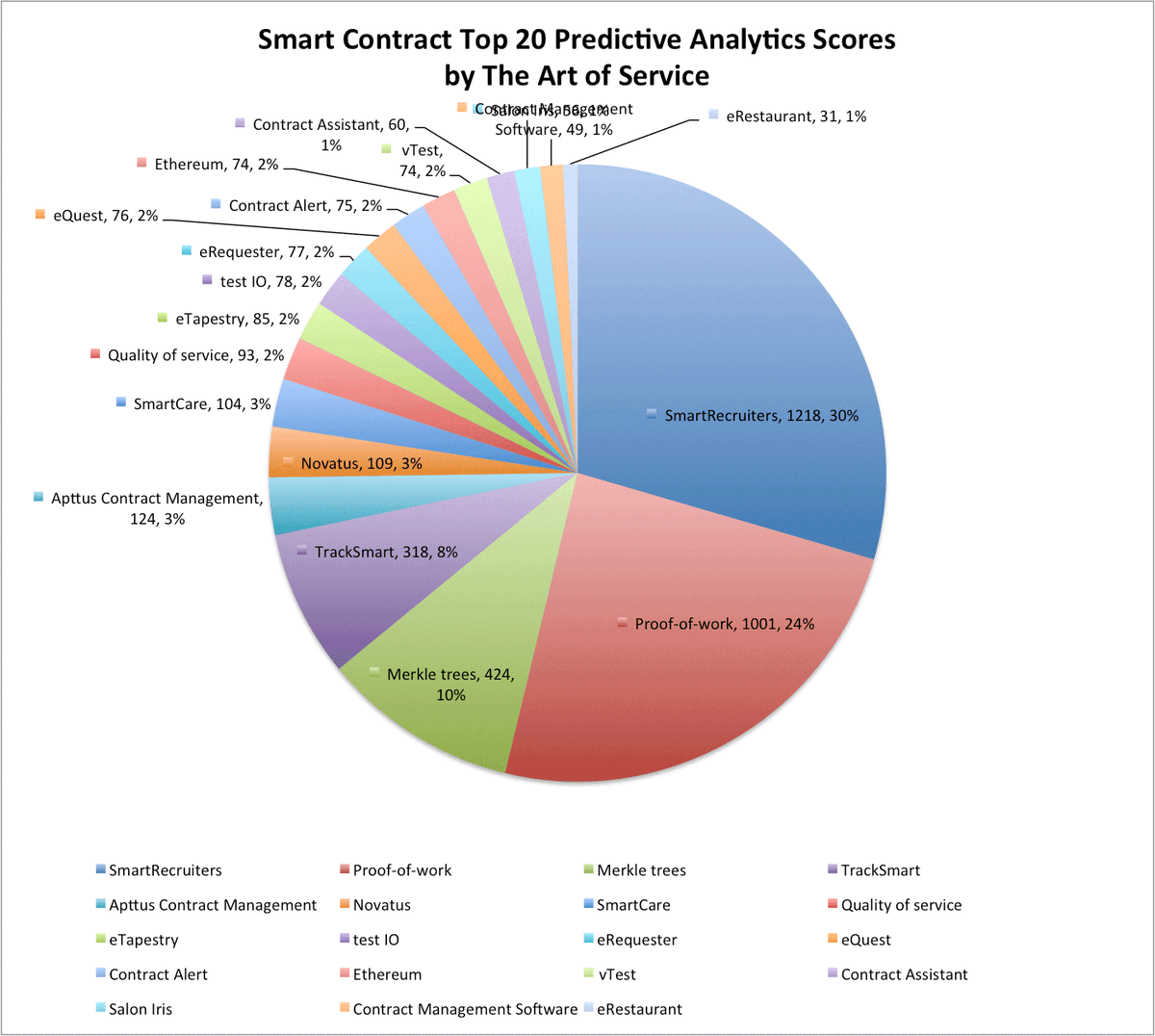



Secure Multi‑Party Computation: Privacy‑Preserving Collaboration #securemultipartycomputation #confidentialcomputing #cryptography #dataethics #dataprivacy #dataprotection #federatedlearning #espincorp e-spincorp.com/secure-multi%e…

@soon_svm #SOONISTHEREDPILL The secure multi-party computation on Soon-SVM allows for collaborative data analysis without sharing raw data. #SoonSVM #SecureMultiPartyComputation
. @soon_svm #SOONISTHEREDPILL Secure Multi-Party Computation: "Enabling secure multi-party computation with blockchain! Soon_SVM's solution protects sensitive data #SecureMultiPartyComputation"
The journey towards a truly decentralized future is an ongoing collaborative effort, requiring continuous innovation and refinement across the entire ecosystem. #Web3Development #DecentralizedGovernance #SecureMultiPartyComputation
The innovative solutions being developed at ChainMotion are vital for fostering trust and user autonomy in the decentralized space. I look forward to seeing the impact of your work! #Web3Privacy #ZKProofs #SecureMultiPartyComputation
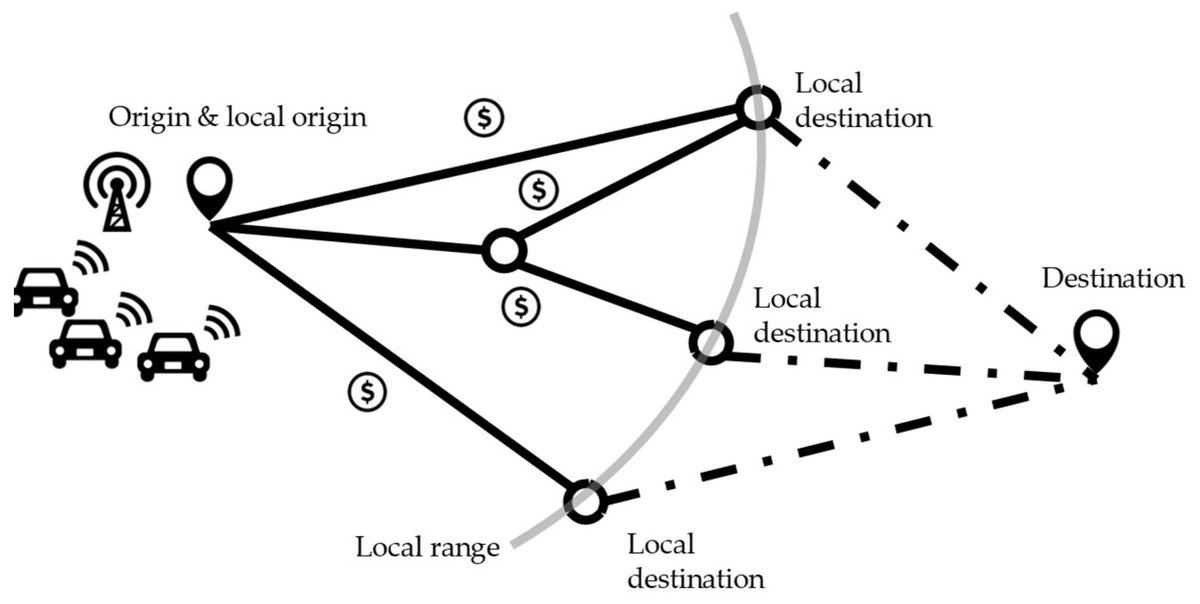
Incentive Mechanism for Privacy-Preserving Collaborative Routing Using Secure Multi-Party Computation and Blockchain mdpi.com/1424-8220/24/2… @GeorgiaTech #incentivemechanism; #securemultipartycomputation; #blockchain
Fireblocks Uncovers Vulnerabilities Present in Major Wallet Providers #Fireblocks #BitForge #SecureMultiPartyComputation mpost.io/fireblocks-unc…
mpost.io
Fireblocks Uncovers Vulnerabilities Present in Major Wallet Providers
Enterprise crypto management platform Fireblocks has announced that it has uncovered the so-called “BitForge," a series of zero-day vulnerabilities
In lecture 7 I showed the basics of #SecureMultipartyComputation, covering #ObliviousTransfer, #GarbledCircuits and #SecretSharing. I then sketched how these cryptographic protocols are used to obtain privacy-preserving #MachineLearning youtube.com/watch?v=u2qHj4…

youtube.com
YouTube
Lecture 7a - Secure Multiparty Computation, Oblivious Transfer and...
ZMET utilizes advances in #PrivacyEnhancingTechnologies (PETs), namely #SecureMultipartyComputation (#SMPC), to expand data utility for #ML use cases by eliminating risk factors that frequently prove to be gating functions.
🔒 Secure Bits 💡 𝗬𝗼𝘂𝗿 𝗥𝗗𝗣 𝘀𝗲𝘀𝘀𝗶𝗼𝗻 𝗺𝗶𝗴𝗵𝘁 𝗹𝗲𝗮𝘃𝗲 𝗮 𝘃𝗶𝘀𝘂𝗮𝗹 𝘁𝗿𝗮𝗶𝗹… Did you know that Remote Desktop Protocol (RDP) 𝗰𝗮𝗰𝗵𝗲𝘀 𝗳𝗿𝗮𝗴𝗺𝗲𝗻𝘁𝘀 of your screen on the client? 🖼️ These bitmap caches are stored locally to improve performance —…

Old Cloudflare XSS bypass but still works . . <img alt="<x" title="/><img src=x onerror=alert(6)>">

Don't automatically assume that any profile that has a uniformed picture can be trusted. Be careful, stay safe! #AkanchaSrivastavaFoundation #India #CyberSafety

In the age of AI and deepfakes, a ‘safe word’ is your strongest protection! AI tools can now clone your face and voice with shocking accuracy. Fraudsters misuse these deepfakes to trick people — pretending to be your friend, colleague, or even an official. 👉 Defend yourself…

vhoy.cloud/e/o8vuevk41bov vihoy.pro/e/kahKqgb2HqPU vhoy.cloud/e/cv6g2olsmarw vihoy.pro/e/kaguzhqpm6lb0 vhoy.cloud/e/k5cgdaerio3b vihoy.pro/e/jahwjqhf5BNmv vhoy.cloud/e/n1wchpfkrnhv vhoy.cloud/e/gtfbkud8wuji

🛠️ Protege tus sistemas con actualizaciones regulares y parches de seguridad. No dejes huecos para el ransomware. 🔧💻 #infosecurity #cloudsecurity

A picture I did for your study journal: The ICT Suspension Block - Algorithmic Signature by @I_Am_The_ICT Like, RT, Bookmark💾

Every login is a security decision. With Zero Trust & Identity Access Management, we ensure only the right people access the right data—securely. Want to know how? Let’s talk. #SepiaSolutions #CyberSecurity #ZeroTrust #SecureLogin #DataProtection
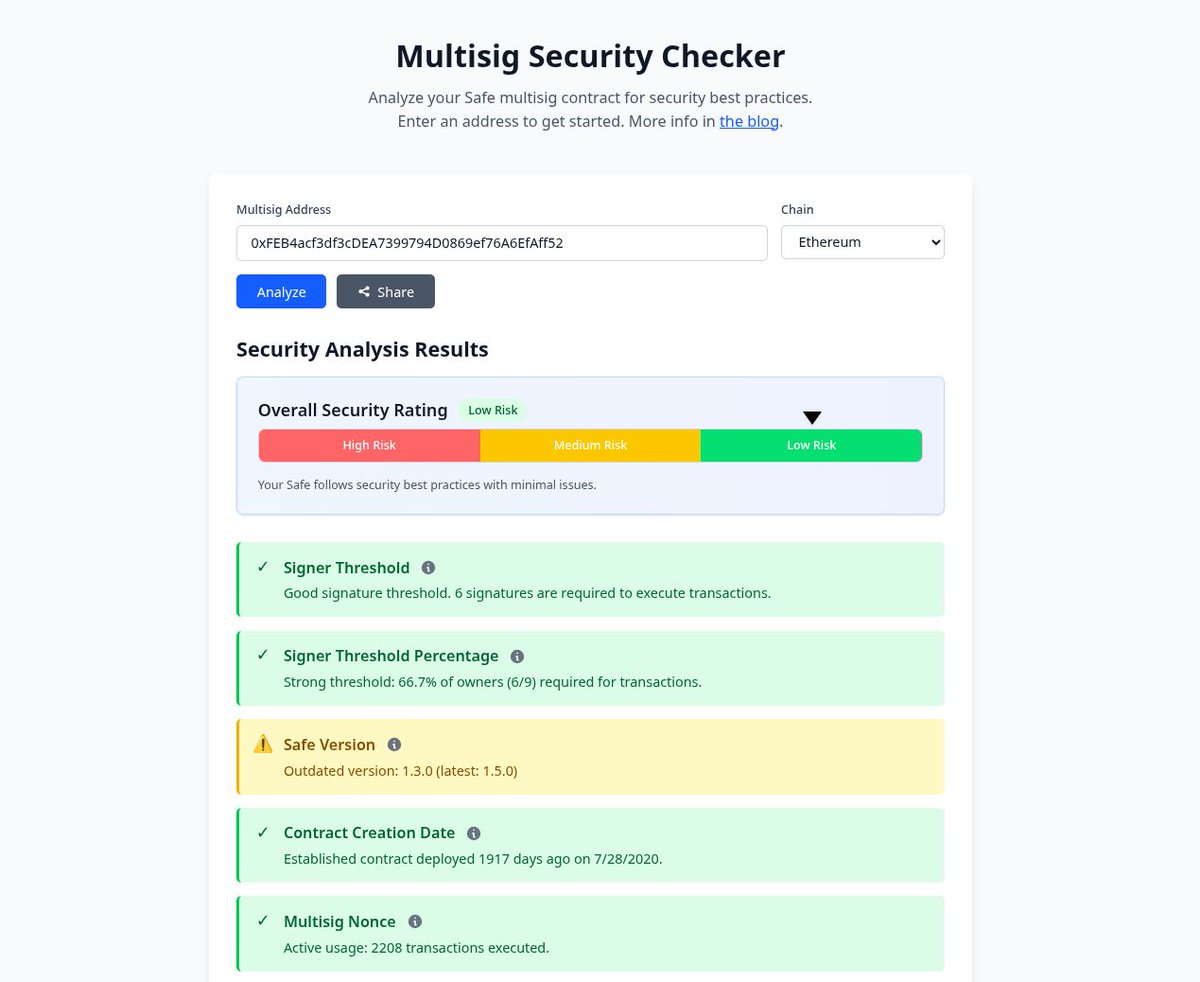
In honor of multisig security month, I'm happy to present a new tool that analyzes the security of a Safe multisig's configuration. 🛠️ Not every Safe is safe! Test it out on the example multisig addresses 👇
Pic of the Day #cybersecurity #infosec #ethicalhacking #vulnerability #cybersecurity #cyber #security

🟦 Multi-Factor Authentication (MFA) Exploitation . . . ⤵️ Techniques Below⤵️

Seed phrases are Web3 Achilles’ heel. One typo, one phish poof, gone. @idOS_network fixes it with MPC (Multi-Party Computation): Shard keys. Sign without exposing. Passwordless, sovereign, hack-proof. The tech rarely spoken about but powers everything.

🔒 Trust starts with protection. 🌐 At Metaspear, security is built-in. 🛡 Encrypted trades. Private protocols. ✔️ No leaks. No compromise. 📈 Your edge is only as safe as your infrastructure, ours runs on zero-trust. #DataSecurity #Metaspear #SecureQuant #ZeroLeakage

Red Team & Blue Team Tools 🔴⚫️Full HD Image: github.com/Ignitetechnolo… #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #AI #cybersecurityawareness #bugbounty #bugbountytips
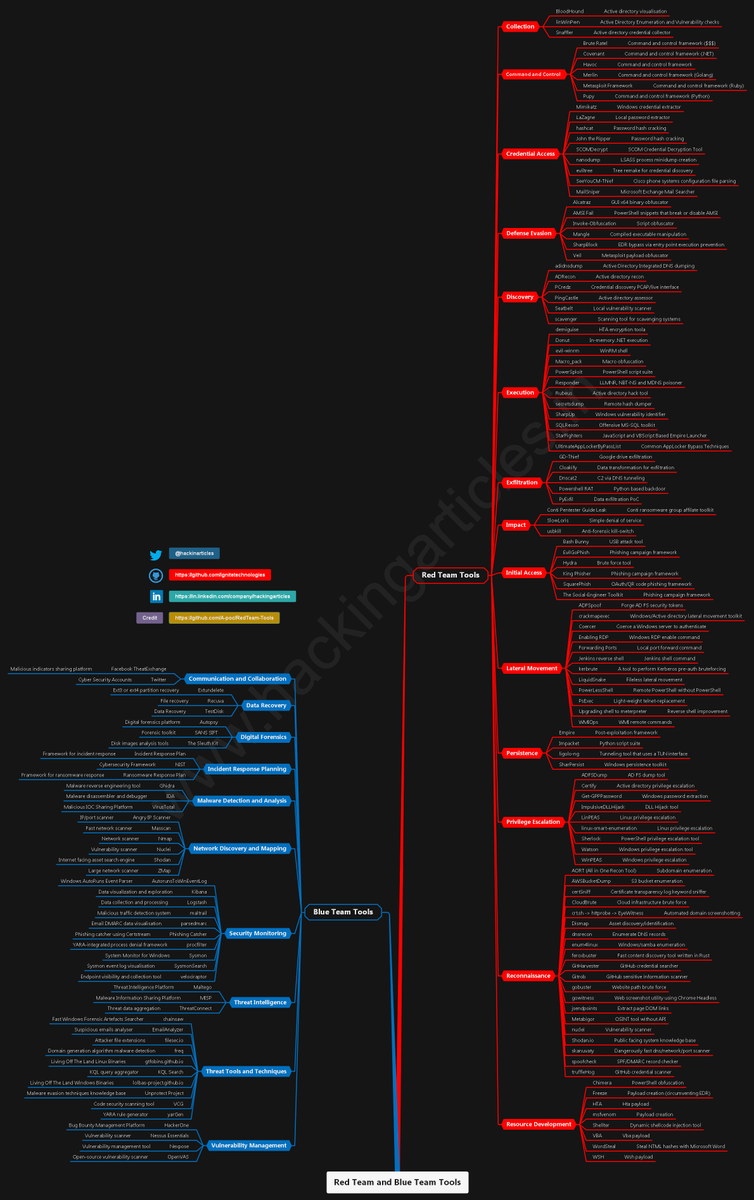
Photo taken in our lab 20 years ago. The two desktop computers on top left are locked and have tamper-proof seals. They were used for signing updates to our detection database. This room was behind 4 locked doors.

Something went wrong.
Something went wrong.
United States Trends
- 1. #WorldSeries 212K posts
- 2. Dodgers 264K posts
- 3. Freddie 99.1K posts
- 4. Klein 210K posts
- 5. Ohtani 139K posts
- 6. Good Tuesday 21K posts
- 7. Kershaw 20.1K posts
- 8. Mookie 15.5K posts
- 9. #Worlds2025 10.3K posts
- 10. 2-12% River Pts N/A
- 11. Yamamoto 29.9K posts
- 12. USS George Washington 16.6K posts
- 13. Wikipedia 62.5K posts
- 14. Victory 156K posts
- 15. Lauer 5,255 posts
- 16. WHAT A GAME 42.6K posts
- 17. Grokipedia 79K posts
- 18. Dave Roberts 6,363 posts
- 19. Joe Davis 2,335 posts
- 20. 18 INNINGS 15.5K posts