#malwareanalysis search results
It’s finally here! 📦 Just received my own printed copies of MAoS – Malware Analysis on Steroids 🔥 There’s nothing like holding your work after months of writing, research, and late-night debugging. Get your copy here👉amazon.com/dp/B0FQDGZGZW #CyberSecurity #MalwareAnalysis…


Example: IDA + DIE — Decode XOR data directly in DIE’s data convertor. A fast workflow for efficient malware analysis. #MalwareAnalysis #XOR #ReverseEngineering #DIE #IDA
A new approach to static analysis with AI that turns days of research into hours. No MCP or live IDA required. Using GPT-5, we completely cracked XLoader v8, one of the most challenging malware families to analyze. #XLoader #MalwareAnalysis #AI research.checkpoint.com/2025/generativ…
Binary Reverse Engineering vs Binary exploitation #reverseengineering #binaryexploitation #malwareanalysis #vulnerabilityresearch #espincorp e-spincorp.com/reverse-engine…

A technical analysis reveals that the Kimsuky threat group utilizes a JavaScript dropper to exfiltrate data from compromised systems, utilizing network IOCs and establishing persistence via Windows scheduled tasks. #CyberSecurity #MalwareAnalysis blog.pulsedive.com/dissecting-the…
🚀 Two months ago, we uncovered the operation behind the malware loader known as #TinyLoader, which was found distributing crypto-theft tools across a global infrastructure. hunt.io/blog/tinyloade… #MalwareAnalysis #SecurityResearch
Black Friday sales have started! Link: training.dfirdiva.com/current-discou… Having a sale? Submit it here: training.dfirdiva.com/submit-a-sale-… or tag me in a post about the sale. #DFIR #IncidentResponse #MalwareAnalysis #OSINT #Cybersecurity

Diving into ‘MAOS - Malware Analysis on Steroids’ by Uriel Kosayev! @MalFuzzer #CyberSecurity #MalwareAnalysis #ThreatIntel #DFIR

Malware hides behind layers of obfuscation. Most analysts slow down there. We don’t. 👊⚡️ #NeZa reveals runtime behavior, API activity, and memory artifacts fast — and you learn to do it hands-on. Train like a real defender, not a spectator. #MalwareAnalysis #DFIR #BlueTeam
RL ❤️ #YARArules! We've been writing them for years. Watch below to see how RL Spectra Analyze makes YARA seamless & powerful for the #SOC. #MalwareAnalysis
Revisited my malware analysis project using FLARE VM and upgraded it with a custom YARA rule to hunt AgentTesla variants. Proud of how it turned out. Shoutout to @ireteeh and @Cyblackorg for this opportunity 🙂 #MalwareAnalysis #YARARules #Cybersecurity #ThreatHunting #FLAREVM

🔥 A week after release and thank God, MAoS – Malware Analysis on Steroids is officially a #1 Best Seller on Amazon! Get your copy today: amazon.com/gp/aw/d/B0FQDL… #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware


🚨 New variant spotted: Matanbuchus 3.0 — a rebuilt malware loader advertised on underground forums. Features DNS/HTTPS C2, in-memory execution, reverse shell, morphing builds & multitenant panel. Price: $10K–$15K/month. Active threat. #CyberThreat #Infosec #MalwareAnalysis

🔍 A DLL isn’t a standalone file — it has no main function like an EXE. That’s why we need tools like WinDbg + SOS to uncover where execution really begins. In this week’s drop, we show you how. youtu.be/MsijfXAu3rA?si… #ReverseEngineering #dotnet #MalwareAnalysis #HackDef #dll
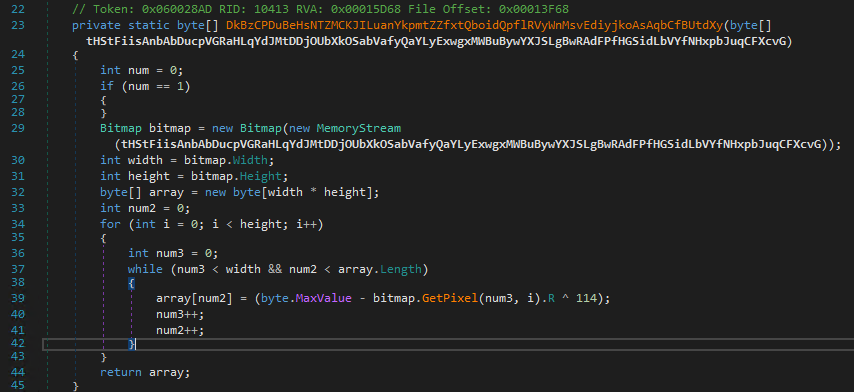
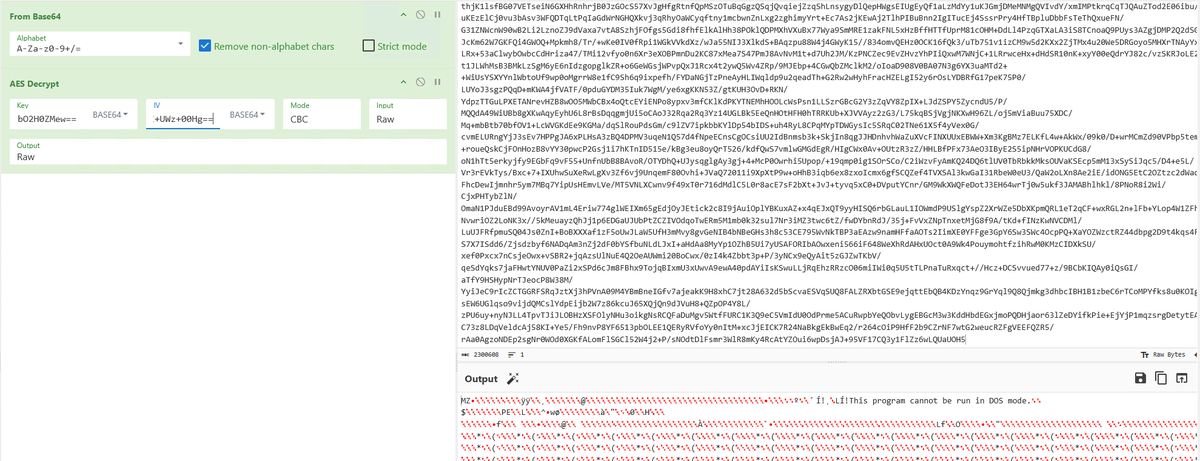
🧵New: "From Pixels to Payloads" — We reverse-engineered a multi-stage .NET loader hiding Lumma Stealer in BMPs via stego trick: (255-R)^0x72. Donut Loader → C# Injector → Lumma in memory. 🧠👇 github.com/ShadowOpCode/S… #LummaStealer #Infosec #MalwareAnalysis #ThreatIntelligence


BAT & PowerShell: powerful admin tools — but attackers can abuse them. Follow for Part 2: how to detect & defend. Drop of the week youtu.be/j5PTyL9TFZA?si… #MalwareAnalysis #Cybersecurity #HackDef #script #training
Fixing an APT sample so it can work on Modern Windows versions - An Exercise in Reverse Engineering gist.github.com/ahm3dgg/b2041f… #malware #malwareanalysis #reverseengineering
We’re excited to welcome Anmol Maurya, Staff Malware Reverse Engineer @ Palo Alto Networks, as he reveals how attackers leverage Go’s portability to target Mac & Linux—and why multi-OS defenses matter. #CyberSecurity #MalwareAnalysis #Infosec #ThreatResearch

Binary Reverse Engineering vs Binary exploitation #reverseengineering #binaryexploitation #malwareanalysis #vulnerabilityresearch #espincorp e-spincorp.com/reverse-engine…

Enhance your malware analysis skills with Mandiant Academy's Basic Static and Dynamic Analysis course! 🛠️🔍 #MalwareAnalysis #ThreatHunting #DigitalForensics #Cybersecurity cloud.google.com/blog/products/…
cloud.google.com
Mandiant Academy: Basic Static and Dynamic Analysis course now available | Google Cloud Blog
To help you get started in pursuing malware analysis as a primary specialty, we’re introducing Mandiant Academy’s new "Basic Static and Dynamic Analysis" course.
Example: IDA + DIE — Decode XOR data directly in DIE’s data convertor. A fast workflow for efficient malware analysis. #MalwareAnalysis #XOR #ReverseEngineering #DIE #IDA
Black Friday sales have started! Link: training.dfirdiva.com/current-discou… Having a sale? Submit it here: training.dfirdiva.com/submit-a-sale-… or tag me in a post about the sale. #DFIR #IncidentResponse #MalwareAnalysis #OSINT #Cybersecurity

If this has piqued your interest, head over to our article to read more ➡️ hunt.io/blog/tinyloade… #ThreatHunting #TinyLoader #MalwareAnalysis #SecurityResearch
🚀 Two months ago, we uncovered the operation behind the malware loader known as #TinyLoader, which was found distributing crypto-theft tools across a global infrastructure. hunt.io/blog/tinyloade… #MalwareAnalysis #SecurityResearch
Malware hides behind layers of obfuscation. Most analysts slow down there. We don’t. 👊⚡️ #NeZa reveals runtime behavior, API activity, and memory artifacts fast — and you learn to do it hands-on. Train like a real defender, not a spectator. #MalwareAnalysis #DFIR #BlueTeam
A new approach to static analysis with AI that turns days of research into hours. No MCP or live IDA required. Using GPT-5, we completely cracked XLoader v8, one of the most challenging malware families to analyze. #XLoader #MalwareAnalysis #AI my.sociabble.com/gL7TxRh9dk8C
Unpacking MedusaLocker / BabyLockerKZ — another day, another ransomware. cyderes.com/howler-cell/me… #MalwareAnalysis #Ransomware #ReverseEngineering
A new approach to static analysis with AI that turns days of research into hours. No MCP or live IDA required. Using GPT-5, we completely cracked XLoader v8, one of the most challenging malware families to analyze. #XLoader #MalwareAnalysis #AI research.checkpoint.com/2025/generativ…
It also copied itself into shared folders and startup directories. It copied itself to all addresses in the Windows Address Book used by Microsoft Outlook allowing it spread much faster than any previous worm #SocialEngineering #cyberhistory #Malwareanalysis #threatintelligence
🔍 Web Malware Scan Results Website: guides.vote Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/e05dbc46-… #Pentesting #WebSecurity #MalwareAnalysis #ZeroTrust #AIResearch
🔍 Web Malware Scan Results Website: adams.gov Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/52c4f47c-… #MalwareAnalysis #CyberDefense #AIResearch
Targeting Windows systems, CABINETRAT uses stealthy techniques like XLL file exploitation and credential harvesting. Learn how Picus Security simulates these attacks to help you stay ahead of evolving threats. 🔍 Read the full analysis: hubs.li/Q03Q1SMj0 #MalwareAnalysis…
Just whipped up a Python script that extracts hidden threats from AES-encrypted ZIPs in-memory (no disk drops!) & repacks 'em into standard ZIP with "infected" password suitable for most AVs & sandboxes for analysis. #MalwareAnalysis #RedTeam #CyberSec Pls DM for the script

Threat actors use malicious SVG image attachments in phishing emails to gain remote access, steal data, and deploy malware. FortiGuard Labs found 26 IoCs including domains and IPs. #SVGPhishing #DNSAnalysis #MalwareAnalysis ift.tt/WyUti8P
🔍 Web Malware Scan Results Website: healthcare.gov Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/9d9aba3f-… #MalwareAnalysis #WebSecurity #Pentesting #EthicalHacking
🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥 Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg. We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses. [1/24] 🖊️ #Malwareanalysis #Ghidra
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gG0vaUAAkrE4.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gOFMbIAA2_rv.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gVA0bMAAeWzo.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0hjgObwAAyIRM.png)
It’s finally here! 📦 Just received my own printed copies of MAoS – Malware Analysis on Steroids 🔥 There’s nothing like holding your work after months of writing, research, and late-night debugging. Get your copy here👉amazon.com/dp/B0FQDGZGZW #CyberSecurity #MalwareAnalysis…


CyberChef Tips - Creating and Accessing Variables #CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis. [1/2] #malware #malwareanalysis
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTCaMAECV1x.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTabwAAd1RG.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTNa4AAkCq3.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQR2bEAAPiZM.png)
In one of the #MalwareAnalysis communities I’m in, we were talking about Go malware. Someone mentioned CAPA as a good tool. I have to say, it’s really helpful for finding the 50kb of interesting code buried inside a 5mb Go binary 😎What other tools do you use?

Diving into ‘MAOS - Malware Analysis on Steroids’ by Uriel Kosayev! @MalFuzzer #CyberSecurity #MalwareAnalysis #ThreatIntel #DFIR

🚨 New variant spotted: Matanbuchus 3.0 — a rebuilt malware loader advertised on underground forums. Features DNS/HTTPS C2, in-memory execution, reverse shell, morphing builds & multitenant panel. Price: $10K–$15K/month. Active threat. #CyberThreat #Infosec #MalwareAnalysis

🧵New: "From Pixels to Payloads" — We reverse-engineered a multi-stage .NET loader hiding Lumma Stealer in BMPs via stego trick: (255-R)^0x72. Donut Loader → C# Injector → Lumma in memory. 🧠👇 github.com/ShadowOpCode/S… #LummaStealer #Infosec #MalwareAnalysis #ThreatIntelligence




Revisited my malware analysis project using FLARE VM and upgraded it with a custom YARA rule to hunt AgentTesla variants. Proud of how it turned out. Shoutout to @ireteeh and @Cyblackorg for this opportunity 🙂 #MalwareAnalysis #YARARules #Cybersecurity #ThreatHunting #FLAREVM

Binary Reverse Engineering vs Binary exploitation #reverseengineering #binaryexploitation #malwareanalysis #vulnerabilityresearch #espincorp e-spincorp.com/reverse-engine…

Automating Malware Analysis Operations (MAOps) blogs.jpcert.or.jp/en/2023/01/clo… #Pentesting #MalwareAnalysis #CyberSecurity #Infosec
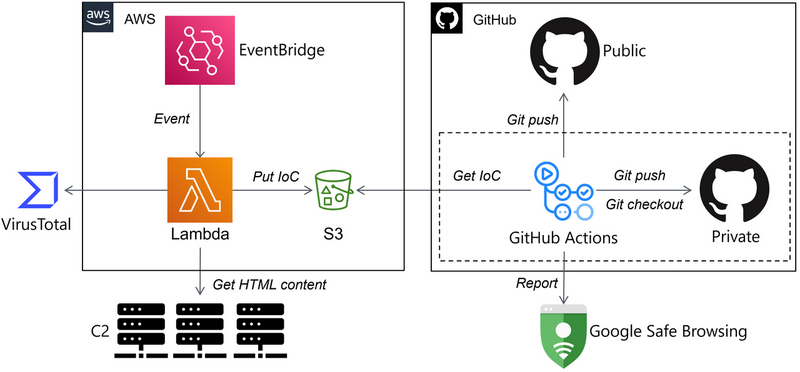
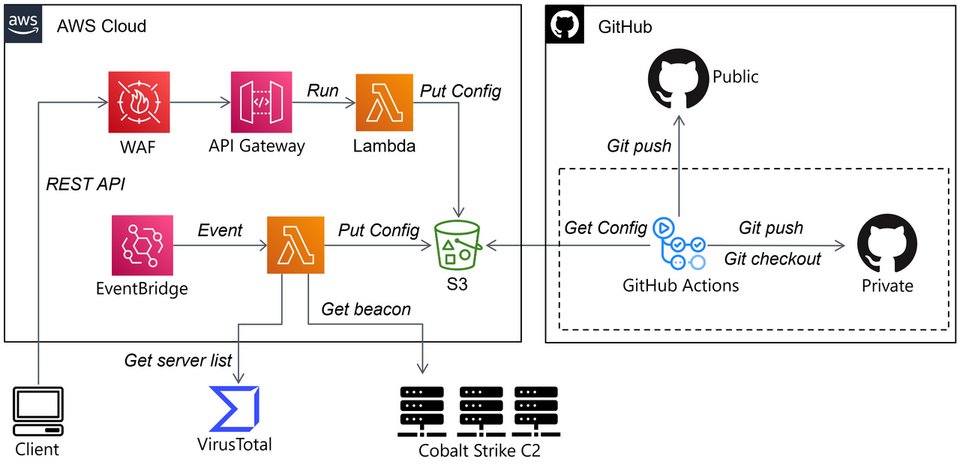
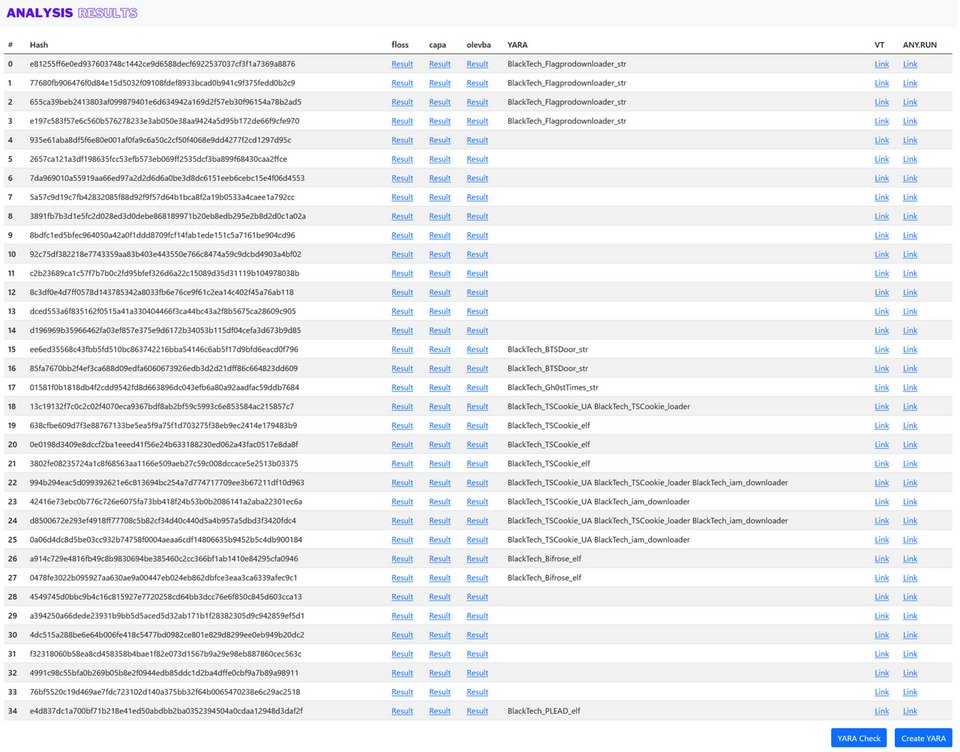
FLARE floss applied to all unpacked+dumped samples in Malpedia Nice project by Daniel Plohmann (@push_pnx) Blog post: danielplohmann.github.io/blog/2024/03/0… Github repo: github.com/malpedia/malpe… #malwareanalysis #infosec


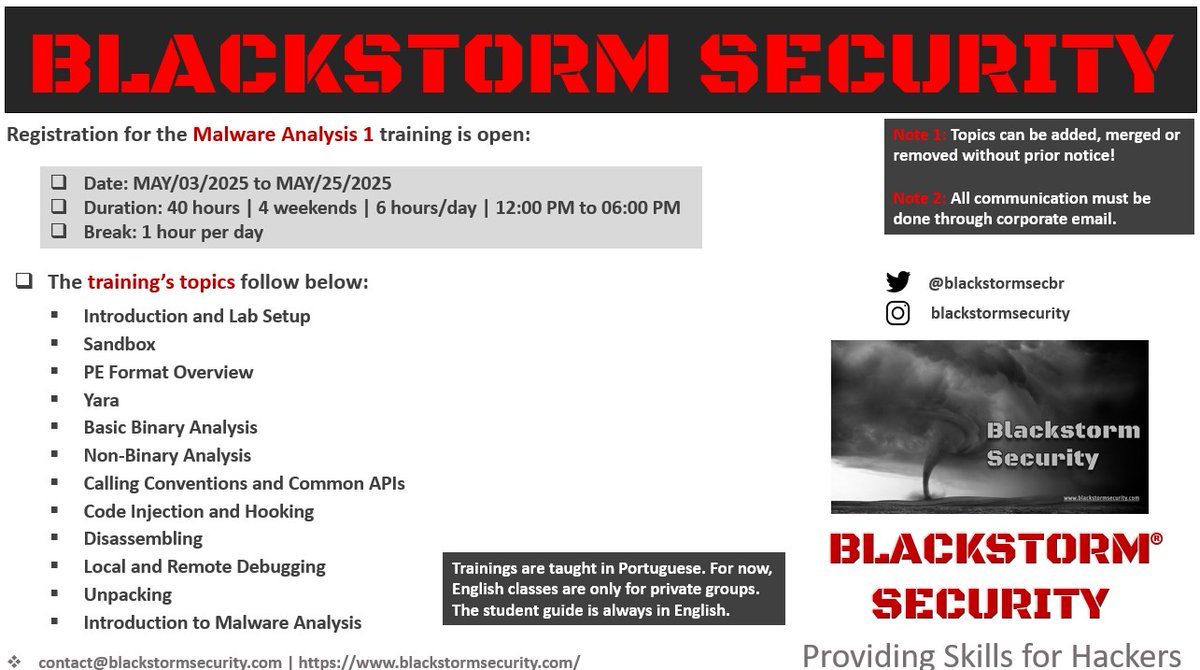
(PT_BR) O treinamento de MALWARE ANALYSIS 1 está com a próxima turma CONFIRMADO para 03/MAIO/2025. Informações adicionais podem ser obtidas no website da Blackstorm Security. #malwareanalysis #informationsecurity #malware #cybersecurity #threathunting #blueteam
🔍 #Opendir Alert! 📂 Target: ⚠️ hxxps://m[.]bureaux[.]fr/ 📄 Sample Files: Advanced IP Scanner.exe AnyDesk.exe AnyDesk.apk ⚡ Repository contains .apk & .exe files. Handle with caution! 🛡️ 🎯 Potential resource for malware analysts. #CyberSecurity #MalwareAnalysis…
![cyberfeeddigest's tweet image. 🔍 #Opendir Alert!
📂 Target:
⚠️ hxxps://m[.]bureaux[.]fr/
📄 Sample Files:
Advanced IP Scanner.exe
AnyDesk.exe
AnyDesk.apk
⚡ Repository contains .apk & .exe files. Handle with caution! 🛡️
🎯 Potential resource for malware analysts.
#CyberSecurity #MalwareAnalysis…](https://pbs.twimg.com/media/GhhcEuqWoAAUj9f.jpg)
📱MasterFred malware uses hidden overlays, permissions, and JavaScript interfaces to steal sensitive data. Get the full analysis here: 8ksec.io/mobile-malware… 🚀For a deeper understanding of mobile malware techniques, explore our course: academy.8ksec.io/course/offensi… #MalwareAnalysis…

Happened to analyze a suspicious macOS file. A developer downloaded Git from a git lookalike domain. Turns out to be #AMOS :) Thanks to @obje tool Lulu @patrickwardle Check out for more in the thread #macos #malwareanalysis #malware #infostealer

Dive deep into the world of antivirus systems. Learn how static, dynamic, heuristic and unpacking engines work to detect malware. hackers-arise.net/2023/12/12/eva… #CyberSecurity #MalwareAnalysis @three_cube

Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 69.5K posts
- 2. Luka 65.6K posts
- 3. Wemby 25.3K posts
- 4. Marcus Smart 5,551 posts
- 5. #LakeShow 5,402 posts
- 6. Blazers 7,954 posts
- 7. Russ 9,947 posts
- 8. Ayton 14.8K posts
- 9. Will Richard 6,129 posts
- 10. Horford 1,885 posts
- 11. #AmphoreusStamp 5,835 posts
- 12. #RipCity N/A
- 13. Podz 2,358 posts
- 14. Champagnie 1,200 posts
- 15. #dispatch 61.4K posts
- 16. Kuminga 3,302 posts
- 17. Thunder 33.3K posts
- 18. Godzilla 32.5K posts
- 19. #AEWDynamite 20.2K posts
- 20. Nico Harrison 1,660 posts























































