#bufferoverflow search results
Successfully completed the TryHackMe "Buffer Overflows" lab, gaining practical experience in vulnerability exploitation and understanding process memory layouts. #TryHackMe #BufferOverflow #Cybersecurity #EthicalHacking #LearningByDoing @CyberMindSpace @RohitVishw54326
Code spills over bounds, Memory chaos unleashed, Errors creep within. #Haiku #Bufferoverflow #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
Memory spills out, Data leaks, chaos unfolds, Code's silent peril. #Haiku #Bufferoverflow #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
Memory spills wide, Code's limits breached, chaos reigns, Bug's dance in the dark. #Haiku #Bufferoverflow #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
Libelf 0.8.12’s gmo2msg faces a stack-based buffer overflow via unbounded sprintf on long filename args (~1200 bytes). Exploits may cause crashes or code execution in privileged contexts. #BufferOverflow #CodeExecution #USA ift.tt/f0A1Phk
Memory spills forth, Data leaks, chaos unfolds, Code's silent danger. #Haiku #Bufferoverflow #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
Learn what buffer overflow is in plain language. Discover how it happens, why hackers exploit it, and how you can protect systems from this classic vulnerability. redsecuretech.co.uk/blog/post/what… #BufferOverflow #CyberSecurity #WebSecurity #AppSec #EthicalHacking #InfoSec #Vulnerability

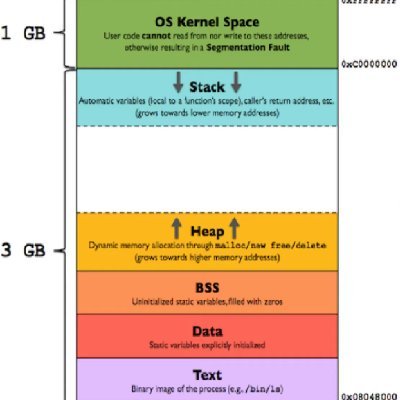
Buffer Overflow 101 When a program writes more data than a buffer can hold, attackers can overwrite memory, hijack execution, and run malicious code. Prevention: safe functions, ASLR, Stack Canaries. #BufferOverflow #CyberSecurity #InfoSec #AzefoxInnovations




Memory spills out, Data leaks in silent rows, Chaos from the code. #Haiku #Bufferoverflow #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
#VulnerabilityReport #bufferoverflow CVE-2025-31700 & CVE-2025-31701: Buffer Overflow Flaws in Dahua IP Cameras Expose Devices to RCE securityonline.info/cve-2025-31700…
#VulnerabilityReport #bufferoverflow Buffer Overflows & XSS in SonicWall SMA 100 Expose Devices to RCE – Patch Immediately! securityonline.info/buffer-overflo…
lets gooo first official #bufferOverflow in the bag labs.hackthebox.com/achievement/ma…
Bytes spill over stack, Chaos in a coded world, Errors take their toll. #Haiku #Bufferoverflow #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
Memory spills out, Code's edge pushed beyond its bounds, Chaos in silence. #Haiku #Bufferoverflow #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
What is a #BufferOverflow? Buffer overflows occur when programs write more data than allocated space, allowing attackers to overwrite adjacent memory with malicious code. 🔎 Read more: techtarget.com/searchsecurity…
🚀 Yeni Blog Yazısı: Buffer Overflow Gereksinimler Vmware yada Virtualbox (Tercihim Vmware) Kali Linux, Parrot OS İşletim sistemleriden biri (Tercihim Kali... #BufferOverflow erengozaydin.com/article/buffer…
🔍 ¿Qué es un Buffer Overflow? Explicación clara y rápida para profesionales de la ciberseguridad linkedin.com/posts/the-hack… 🔐 #Ciberseguridad #BufferOverflow #HackingÉtico #Infosec #ExploitDevelopment #SeguridadInformática #CyberSecurity #DevSecOps #MemoryManagement #SecureCodin




Memory spills out, Code's edge breached, chaos unleashed, Silent error waits. #Haiku #Bufferoverflow #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
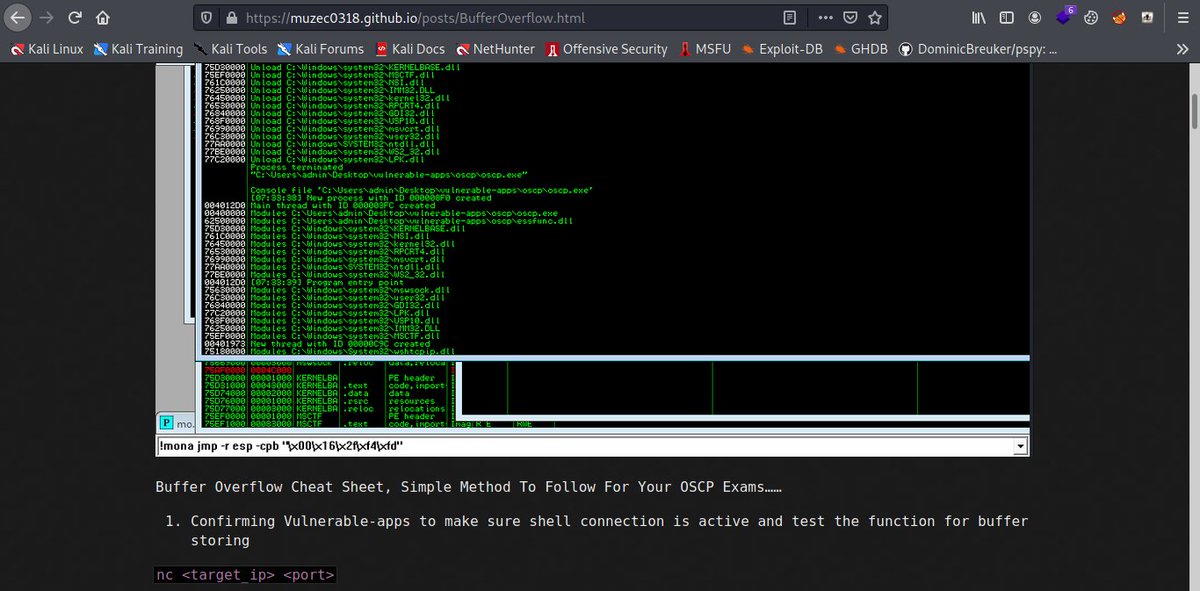
Yes Finally 😄😄😄😄 My Cheat Sheet For Buffer Overflow Buffer Overflow Cheat Sheet;- muzec0318.github.io/posts/BufferOv… #BufferOverflow #Pentesting #Hacking
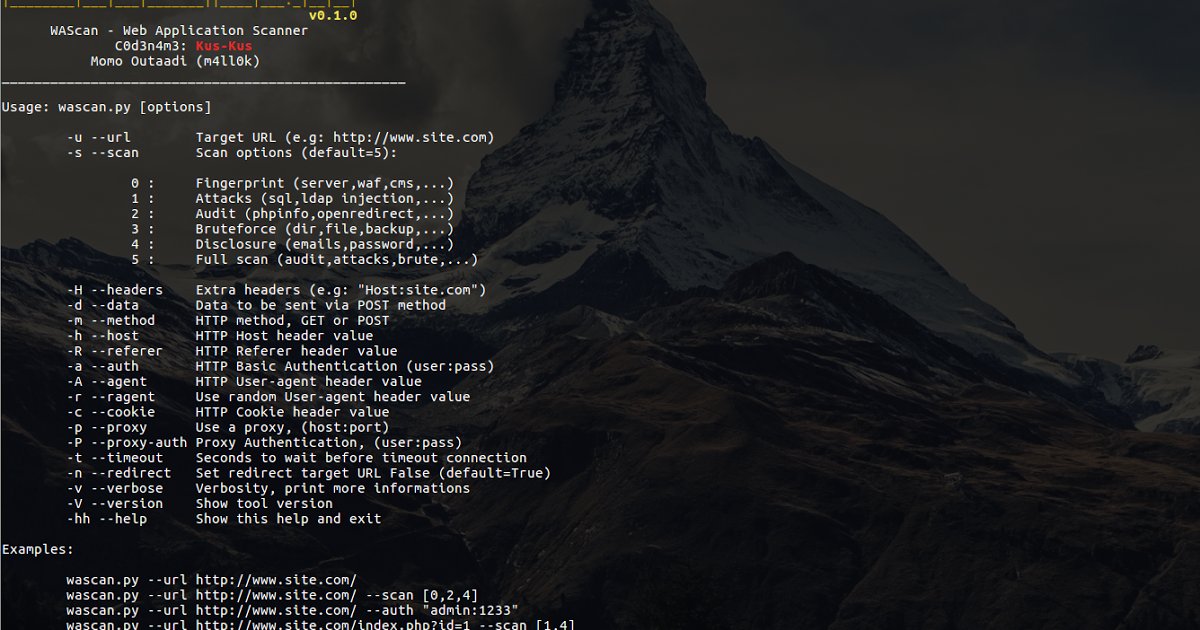
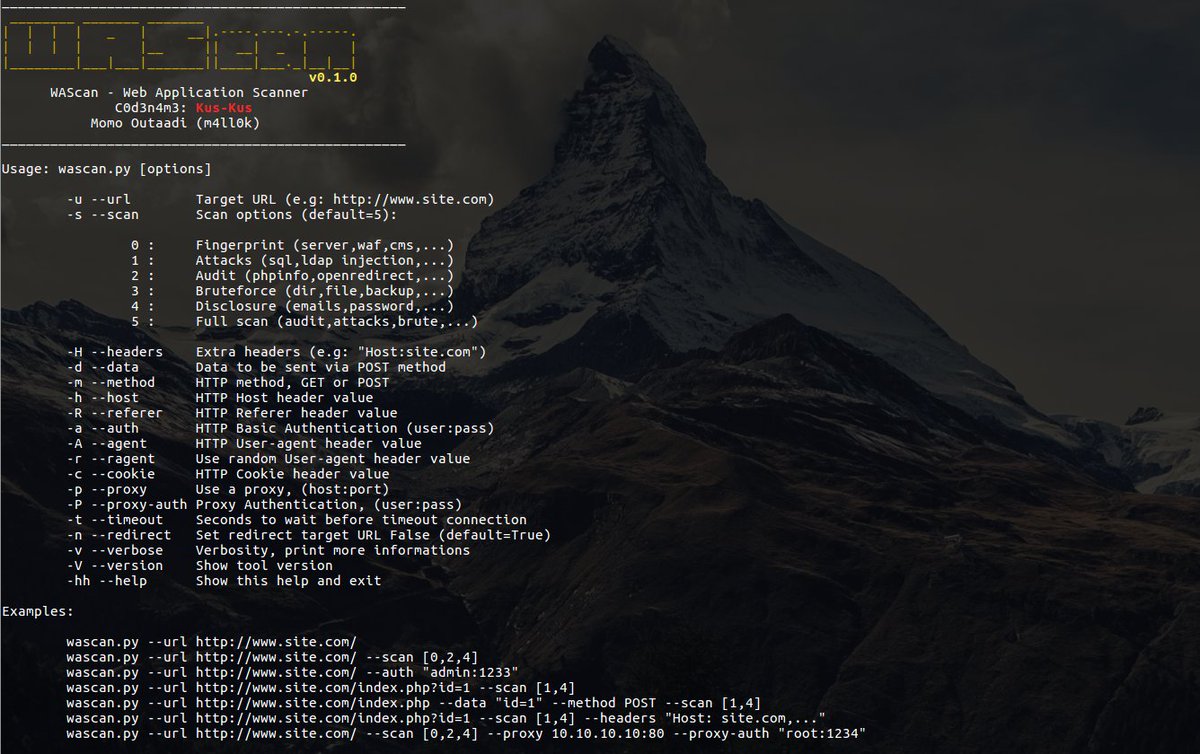
WAScan - Web Application Scanner goo.gl/QEWmCC #BufferOverflow #CommandInjection #Cookie #Firewall #LDAP #Linux #Python #SQLi
Buffer Overflows for Dummies sans.org/reading-room/w… #Pentesting #BufferOverflow #CyberSecurity #Infosec



Buffer Overflow (ret2func) aidenpearce369.github.io/exploit%20deve… #Pentesting #BufferOverflow #Exploit #CyberSecurity #Infosec
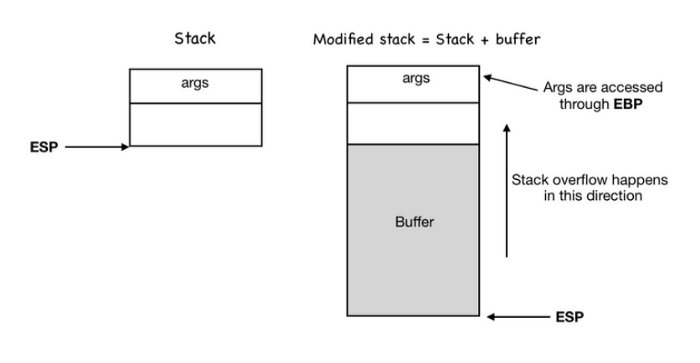

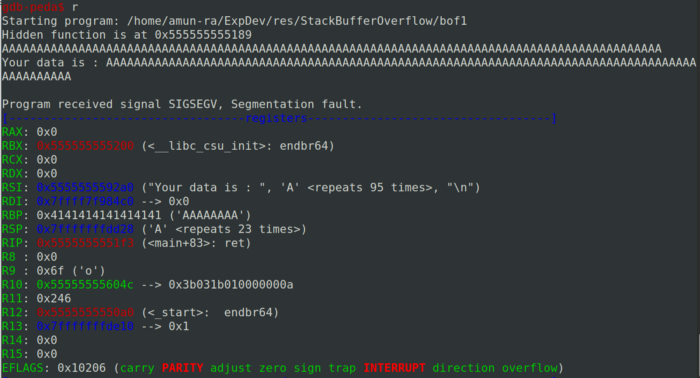
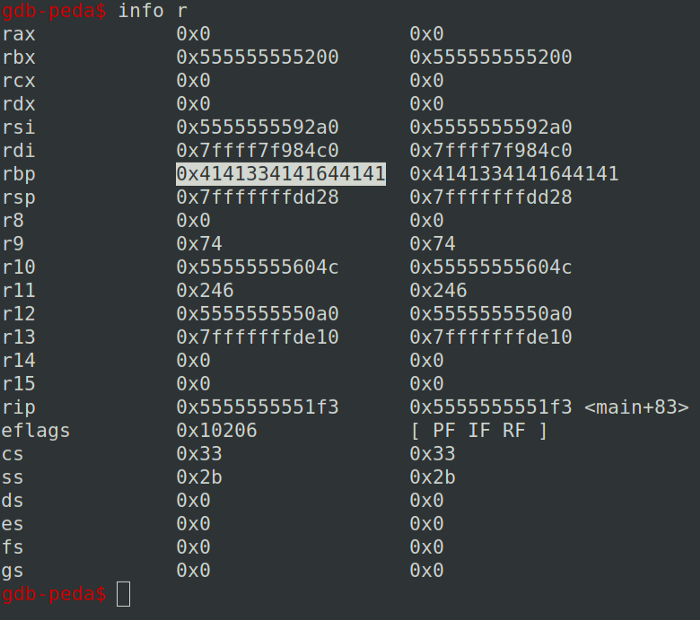
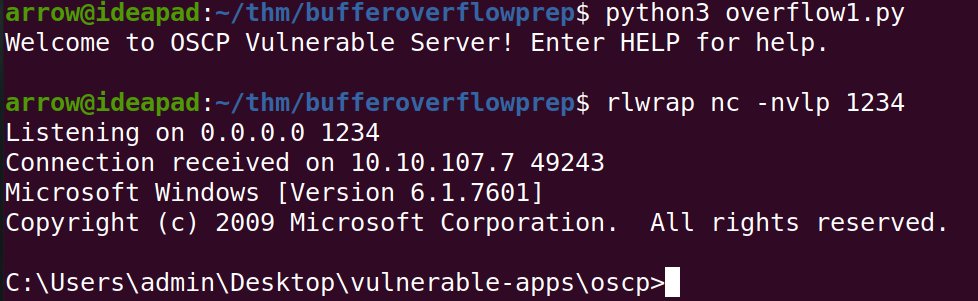
Exploiting a Windows-Based Buffer Overflow infosecwriteups.com/exploiting-a-w… #BufferOverflow #Windows10 #Hacking #Cybersecurity #Infosec




Exploit Development, Part 1: Anatomy of a Buffer Overflow #bof #bufferoverflow #exploitdevelopment #whatsapp #cybersecurity bit.ly/2rphf46

Exploit Development, Part 1: Anatomy of a Buffer Overflow #exploitdevelopment #bufferoverflow #cybersecurity #cyberwarrior hackers-arise.com/single-post/20…

Got Overwrite infosecwriteups.com/got-overwrite-… #Exploitation #Stackoverflow #BufferOverflow #ExploitDev #Cybersecurity



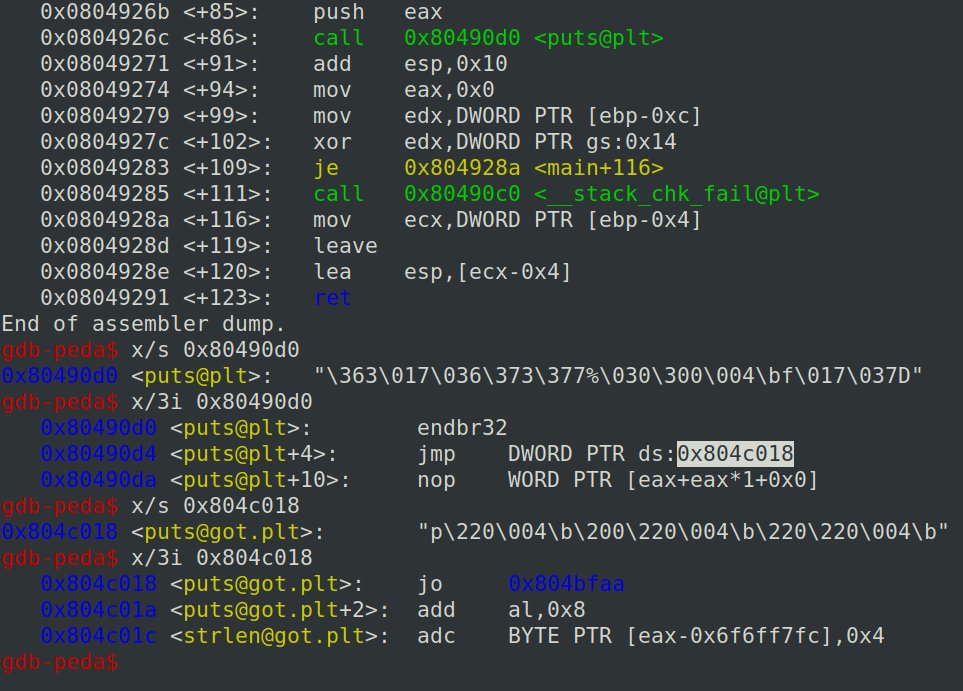
Amazing CD Ripper 1.2 Buffer Overflow #0day #BufferOverflow #0day_Hejap packetstormsecurity.com/files/166380/A…

Muzec's Cyber Security Blog muzec0318.github.io/posts/BufferOv… #Pentesting #BufferOverflow #Hacking #Infosec


Is your data safe? 👨💻 Cybercriminals have a lot of opportunities to exploit your system. #BufferOverflow is one of them. Find out more about it in our #CybersecurityDictionary. #ESET #ProgressProtected

Live de Overview do treinamento de Desenvolvimento de Exploits, quer saber mais sobre o treinamento? Público alvo, módulos, conteúdo? Então não vai perder a Live né? Te encontro na quarta (27/05) à 21h07. #m4v3r1ck #helviojunior #bufferoverflow #exploit #dica

Return To LIBC Attack (ret2libc) aidenpearce369.github.io/exploit%20deve… #Pentesting #BufferOverflow #ExploitDev #CyberSecurity #Infosec



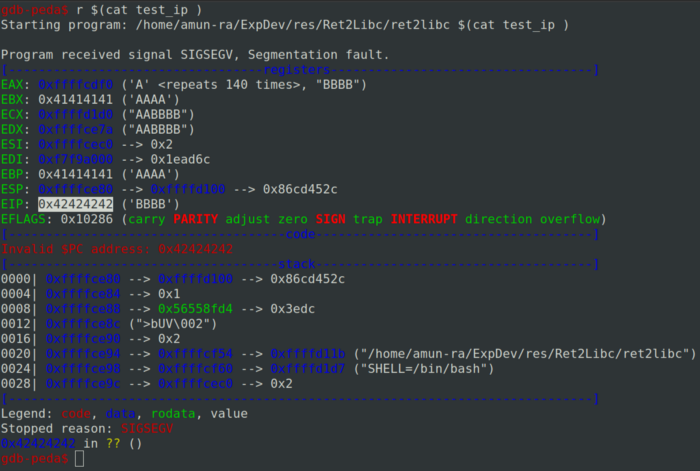
🔍 ¿Qué es un Buffer Overflow? Explicación clara y rápida para profesionales de la ciberseguridad linkedin.com/posts/the-hack… 🔐 #Ciberseguridad #BufferOverflow #HackingÉtico #Infosec #ExploitDevelopment #SeguridadInformática #CyberSecurity #DevSecOps #MemoryManagement #SecureCodin




I worked all day on WarFTP exploit development following the book and I finally got it. I could understand all the steps from the #bufferoverflow and got a reverse #shell. What a feeling! #hacking #pentesting @georgiaweidman

Treinamento “Advanced Exploitation” 100% on-line com o conteúdo: introdução a linguagem assembly para criação de exploits, criação de shellcode, exploit zero day, egg hunting, e muito mais. Segue o link de inscrição: eventbrite.com.br/e/treinamento-… #m4v3r1ck #bufferoverflow #exploit

Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Birthday Charlie 36.9K posts
- 2. Good Tuesday 27.6K posts
- 3. #tuesdayvibe 2,870 posts
- 4. #Worlds2025 39.9K posts
- 5. #PutThatInYourPipe N/A
- 6. #T1WIN 17.5K posts
- 7. Pentagon 71.7K posts
- 8. Janet Mills 1,289 posts
- 9. #Wordle1578 N/A
- 10. Dissidia 5,541 posts
- 11. Romans 10.9K posts
- 12. Martin Sheen 6,108 posts
- 13. Blinken 24.9K posts
- 14. JPMorgan 3,090 posts
- 15. Medal of Freedom 48.7K posts
- 16. Gaia 9,612 posts
- 17. No American 64.4K posts
- 18. Time Magazine 16K posts
- 19. Alec Baldwin 7,444 posts
- 20. Jake Moody 14.9K posts