#c2server search results
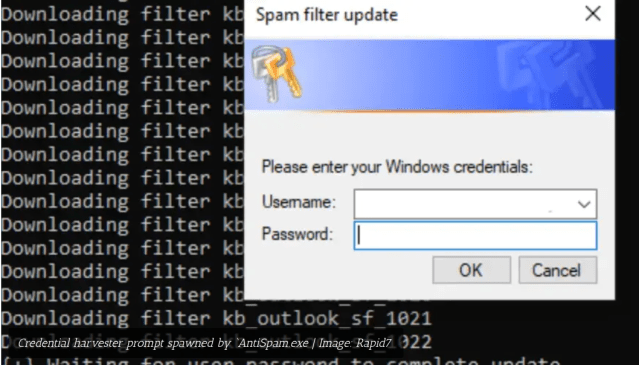
Last night, I was able to get a solid p90 together for the CLI utility that researchers will use to query #Darkweb, #C2Server and other records within the platform's blob storage. There are still a few small details that I need to iron out, but my approach was a little different…
Installing Your Own C2 Server in Kali Linux #kali #c2server #infosec #cybersecurity #cyberwarrior hackers-arise.com/post/command-c…
🚨 Mythic C2 Server Detected 🚨 http://54[.]215[.]152[.]194 A Mythic Command & Control (C2) server has been identified. This C2 framework is often used in targeted attacks and red team operations #CyberSecurity #ThreatIntel #C2Server #MythicC2 #MalwareAlert
![s3curetheweb's tweet image. 🚨 Mythic C2 Server Detected 🚨
http://54[.]215[.]152[.]194
A Mythic Command & Control (C2) server has been identified.
This C2 framework is often used in targeted attacks and red team operations
#CyberSecurity #ThreatIntel #C2Server #MythicC2 #MalwareAlert](https://pbs.twimg.com/media/GpEuLvYWcAAADoX.jpg)
![s3curetheweb's tweet image. 🚨 Mythic C2 Server Detected 🚨
http://54[.]215[.]152[.]194
A Mythic Command & Control (C2) server has been identified.
This C2 framework is often used in targeted attacks and red team operations
#CyberSecurity #ThreatIntel #C2Server #MythicC2 #MalwareAlert](https://pbs.twimg.com/media/GpEuLvbWcAAGHlY.jpg)
Remote Domination: Command & Control Every sophisticated cyber operation needs a central nervous system. #RedTeam #C2Server #Cybersecurity #OffensiveSecurity #Hacking #Botnet #InfoSec #CyberOps #ThreatIntel #Malware #NetworkSecurity #C2Infrastructure #CyberThreats




[Criminal IP #BlackFriday Event] Don’t miss out on getting your Premium #threatintelligence DB! Enhance your security policies with the #C2server IP, malicious URL, and Snort Rules detected by Criminal IP daily. ⬇️Go to Event blog.criminalip.io/2023/11/21/cri…
![CriminalIP_US's tweet image. [Criminal IP #BlackFriday Event] Don’t miss out on getting your Premium #threatintelligence DB!
Enhance your security policies with the #C2server IP, malicious URL, and Snort Rules detected by Criminal IP daily.
⬇️Go to Event
blog.criminalip.io/2023/11/21/cri…](https://pbs.twimg.com/media/F_hCnGBbsAAZbYe.jpg)
4/n 🌐 Network Traffic Analysis I identified the Command & Control (C2) server endpoint:http://77.91.124.55:19071/. Blocking this traffic is crucial for preventing further data exfiltration and malicious communication. #NetworkSecurity #C2Server
The Group-IB Threat Intelligence team discovered and shut down а #C2server at 212.60.5[.]129 used by the group tracked by us under the name EagleStrike GamebleForce which was behind #SQL injection attacks on government and #gambling sites in the Asia-Pacific region. The attackers…
Gomir, Linux backdoor sajberinfo.com/2024/05/24/gom… #backdoor #c2server #cronjobs #crontab #gobear #gomir #httppostrequests #kimsukyapt #linuxmalware #linuxsystems #persistence #phishing #socialengineering
🚨 Understanding C2 Servers in Cybersecurity! 🚨 What’s a #C2Server? In cybersecurity, C2 (Command & Control) servers are used by attackers to communicate with compromised systems. These servers allow them to send commands, receive data, and control the infected devices remotely.
Once the data is located on the target system, it is sent to the malware's #C2server. Details about #Raccoon #stealer will be included in our upcoming #MostUpdatedMalware Report.
Windows の脆弱性 CVE-2022-26923 の悪用:電子メール爆弾から RAT へつなげる手口とは? iototsecnews.jp/2024/08/16/cyb… #AppLocker #C2Server #CommandandComtrol #CyberAttack #eMailBomb #Exploit #Malware #Rapid7 #RAT #RMM #Scammer #SocialEngineering #TTP #Vulnerability #Windows
The Ultimate Guide to C2 Servers: Command & Control Server (Installing your own C2 Server on Kali Linux) Explore Here: codelivly.com/the-ultimate-g… #c2server #infosec #cybersec #codelivly #hacking #botnet #cybersecurity #networking #pentesting #redteam #bugbounty #bughountytips

4 — Fake Internet Connection Some malware run a ping test to see if there’s a live internet connection (likely for #exfiltrating #stolendata to a #C2server). So, we need to fake an internet connection to trick it into thinking it's online.
AvNeutralizer osposobljava EDR riješenja sajberinfo.com/2024/07/21/avn… #advancedpersistence #avneutralizer #c2server #coreimpactimplants #datatheft #edrsolutions #fin7 #malware #powertrashloaders #ransomware #sophisticatedtools #sshbasedbackdoor #threatactors #undergroundmarketplaces
SpyAgent Android zlonamjerni softver sajberinfo.com/2024/09/16/spy… #androidthreat #c2server #cryptowallettheft #datastealingmalware #deviceinfection #deviceinformationtheft #mobilesecurity #ocrtechnology #smsphishing #spyagentmalware #victimcontactlist
編集長の本日(4/18)のPick upは、C2リダイレクタの実態と対策とは?というお話し。 packet-pilot.net/packet-news/un… #c2redirector #C2Server #REDTEAM #BLUETEAM #NISC #IPA #packetnews #いつかは月刊化 #ネットワークマガジン #network #packet
Kematian kradljivac zloupotrebljava PowerShell sajberinfo.com/2024/07/28/kem… #adaptability #buildertool #c2server #cookiecollector #cryptocurrencywallets #datacollection #evadingdetection #exfiltration #github #informationstealer #kematianstealer #passwordstealer #somalidevs
Detecting Google Calendar phishing attacks with Wazuh & Suricata helps identify malicious C2 traffic early. Real-time alerts like Slack enable quick responses to prevent breaches. 🚨 #LivingOffTheLand #C2Server #UK ift.tt/TbJZzW3
Last night, I was able to get a solid p90 together for the CLI utility that researchers will use to query #Darkweb, #C2Server and other records within the platform's blob storage. There are still a few small details that I need to iron out, but my approach was a little different…
Remote Domination: Command & Control Every sophisticated cyber operation needs a central nervous system. #RedTeam #C2Server #Cybersecurity #OffensiveSecurity #Hacking #Botnet #InfoSec #CyberOps #ThreatIntel #Malware #NetworkSecurity #C2Infrastructure #CyberThreats




🛡️ SOC Actions: Use threat intelligence feeds to block known C2 infrastructure. Implement EDR and NDR tools to spot anomalous outbound traffic. #CyberSecurity #C2Server #ThreatDetection #SOC #BlueTeam #InfoSec #NetworkSecurity #MalwareTraffic #SOCOperations
Detecting Google Calendar phishing attacks with Wazuh & Suricata helps identify malicious C2 traffic early. Real-time alerts like Slack enable quick responses to prevent breaches. 🚨 #LivingOffTheLand #C2Server #UK ift.tt/TbJZzW3
🚨 Mythic C2 Server Detected 🚨 http://54[.]215[.]152[.]194 A Mythic Command & Control (C2) server has been identified. This C2 framework is often used in targeted attacks and red team operations #CyberSecurity #ThreatIntel #C2Server #MythicC2 #MalwareAlert
![s3curetheweb's tweet image. 🚨 Mythic C2 Server Detected 🚨
http://54[.]215[.]152[.]194
A Mythic Command & Control (C2) server has been identified.
This C2 framework is often used in targeted attacks and red team operations
#CyberSecurity #ThreatIntel #C2Server #MythicC2 #MalwareAlert](https://pbs.twimg.com/media/GpEuLvYWcAAADoX.jpg)
![s3curetheweb's tweet image. 🚨 Mythic C2 Server Detected 🚨
http://54[.]215[.]152[.]194
A Mythic Command & Control (C2) server has been identified.
This C2 framework is often used in targeted attacks and red team operations
#CyberSecurity #ThreatIntel #C2Server #MythicC2 #MalwareAlert](https://pbs.twimg.com/media/GpEuLvbWcAAGHlY.jpg)
Google Play 上のアプリに潜むトロイの木馬:200万ダウンロードの可能性が iototsecnews.jp/2024/11/12/res… #Android #FakeApp #C2Server #CyberAttack #DataBreach #DrWeb #Google #Malware #Mobile #Play #RAT #Scammer #TTP
Linux のエミュレート環境が標的:“CRON#TRAP” キャンペーンの巧妙な検出回避術とは? iototsecnews.jp/2024/11/06/new… #C2Server #Chisel #CRON #TRAP #crondx #Linux #Literacy #LOLbin #Malware #OpenSource #Phishing #QEMU #RAT #Scammer #Securonix #TinyCore #TTP
iototsecnews.jp
Linux のエミュレート環境が標的:“CRON#TRAP” キャンペーンの巧妙な検出回避術とは?
New “CRON#TRAP” Campaign Exploits Emulated Linux Environments to Evade Detection 2024/11/06 SecurityOnline — Securonix 脅威調査チームが検出したのは、”CRON#TRAP” と呼ばれる高度なマルウェア・キャンペーンの存在である。このキャンペ…
VPN/Botnet を組み合わせた脅威:きわめて危険な ORB (Operational Relay Box) とは? iototsecnews.jp/2024/11/05/bey… #Botnet #C2Server #CommandandComtrol #CyberAttack #IoT #Malware #OperationalRelayBox #ORB #RAT #TeamCymru #TTP #VPN
iototsecnews.jp
VPN/Botnet を組み合わせた脅威:きわめて危険な ORB (Operational Relay Box) とは?
Beyond VPNs and Botnets: Understanding the Danger of ORB Networks 2024/11/05 SecurityOnline — 最近の Team Cymru の S2 研究チームは、サイバーセキュリティ分野で拡大している脅威である、ORB (Operational Relay Box) ネットワークにフォーカスしている。…
In our latest blog post, we delve into how adversaries use C2 servers to maintain control over compromised systems and execute various malicious activities: bit.ly/3YF8HTC #C2Server #Cybercrime #Cybersecurity
Lumma Stealer マルウェア:偽の CAPTCHA ページを使用してペイロードを実行 iototsecnews.jp/2024/10/22/fak… #C2Server #CAPTCHA #FilelessMalware #InfoStealer #Lumma #LummaStealer #MaaS #MalwarePolyglot #ProcessHollowing #Qualys #QualysTRU
iototsecnews.jp
Lumma Stealer マルウェア:偽の CAPTCHA ページを使用してペイロードを実行
Fake CAPTCHA Pages Used by Lumma Stealer to Spread Fileless Malware 2024/10/22 HackRead — Qualys TRU (Threat Research Unit) が公表したのは、MaaS (Malware-as-a-Service) モデルとして提供されるマルウェア Lumma Stealer …
VOIDMAW というテクノロジー:メモリス・キャナーに対する新たなバイパス手法を提示 iototsecnews.jp/2024/10/21/voi… #C2Server #CobaltStrike #CommandandComtrol #Malware #Mimikatz #OpenSource #Protection #RAT #SecTool #TTP #VOIDMAW
GhostStrike の解説:Sliver C2 の解析から Cobalt Strike などへと対象を拡大 iototsecnews.jp/2024/10/17/gho… #C2Server #CobaltStrike #Covenant #Empire #GhostStrike #Havoc #Literacy #OpenSource #Protection #SecTools #Sliver #Windows
iototsecnews.jp
GhostStrike の解説:Sliver C2 の解析から Cobalt Strike などへと対象を拡大
GhostStrike: Open-source tool for ethical hacking 2024/10/17 HelpNetSecurity — GhostStrike は、倫理的ハッキングやレッドチームでの運用に特化された、高度なサイバー・セキュリティのための、オープンソース・ツールである。このツールは、Windows システム上での検知をステルス的に回避する ho…
DNS Tunneling キャンペーン:Palo Alto Unit42 が発見した検出回避と攻撃の方式とは? iototsecnews.jp/2024/10/07/dns… #8NS #C2Server #CommandandComtrol #CyberAttack #DNS #DNSTunneling #FinHealthXDS #Malware #NSfinder #PaloAlto #RAT #RussianSite #TTP #42 #ZeroTrust
iototsecnews.jp
DNS Tunneling キャンペーン:Palo Alto Unit42 が発見した検出回避と攻撃の方式とは?
DNS Tunneling: The Hidden Threat Exploited by Cyberattackers 2024/10/07 SecurityOnline — サイバー攻撃者が用いる DNS トンネリングという手法は、検出を回避しながら悪意の活動を行い、データを盗み出すための隠された戦術である。Palo Alto Networks の最新レポートでは、従来のセキ…
Visual Studio Code を悪用する攻撃を検出:Remote-Tunnels エクステンションで C2 通信 iototsecnews.jp/2024/10/01/ste… #APT #C2Server #CommandandComtrol #CyberAttack #Cyble #Lazagne #LOLbin #Malware #Mimikatz #Phishing #RAT #Scammer #StatelyTaurus #TTP #Unit42 #VisualStudio #VSCode
iototsecnews.jp
Visual Studio Code を悪用する攻撃を検出:Remote-Tunnels エクステンションで C2 通信
Stealthy Cyberattack Turns Visual Studio Code into a Remote Access Tool 2024/10/01 SecurityOnline — Visual Studio Code (VSCode) を悪用して、被害者のシステムに不正なリモート アクセスを確立する高度なサイバー攻撃を、Cyble Research and I…
SpyAgent Android zlonamjerni softver sajberinfo.com/2024/09/16/spy… #androidthreat #c2server #cryptowallettheft #datastealingmalware #deviceinfection #deviceinformationtheft #mobilesecurity #ocrtechnology #smsphishing #spyagentmalware #victimcontactlist
CyberVolk ランサムウェアの台頭:C2 サーバを必要としない自律型の暗号化機能を備えている iototsecnews.jp/2024/09/05/cyb… #C2Server #CommandandComtrol #CyberAttack #CyberVolk #Literacy #RaaS #Ransomware #ThreatMon
iototsecnews.jp
CyberVolk ランサムウェアの台頭:C2 サーバを必要としない自律型の暗号化機能を備えている
CyberVolk Ransomware: A New and Evolving Threat to Global Cybersecurity 2024/09/05 SecurityOnline — サイバー犯罪の世界では新しいプレーヤーである、インドのハッカー・グループ CyberVolk だが、その洗練されたランサムウェアの技法で波紋を引き起こしている。2024年7月に初…
Google Sheets を悪用するマルウェア:基本的な技術/機能による巧妙な手口とは? iototsecnews.jp/2024/08/30/cyb… #APT #C2Server #CommandandComtrol #CyberAttack #DarkGate #GoogleSheets #IAB #Latrodectus #Malware #NetskopeThreatLabs #OpenDrive #Proofpoint #RAT #TTP #Voldemort #XWorm
npm へ攻撃:難読化された悪意のパッケージを展開する北朝鮮の脅威グループ iototsecnews.jp/2024/08/29/nor… #C2Server #CryptoJacking #CyberAttack #InfoStealer #JavaScript #Malware #NorthKorea #npm #OpenSource #Phylum #RAT #Repository #SupplyChainAttack
Gmail を狙う新たなマルウェア:MalAgent.AutoITBot を SonicWall が発見 iototsecnews.jp/2024/08/27/son… #authNauthZ #AutoIT #C2Server #Facebook #Gmail #GoogleChrome #Literacy #MalAgentAutoITBot #Malware #MicrosoftEdge #MozillaFirefox #RAT #Reddit #SonicWall #TTP
iototsecnews.jp
Gmail を狙う新たなマルウェア:MalAgent.AutoITBot を SonicWall が発見
SonicWall Warns: New Malware Targets Gmail 2024/08/27 SecurityOnline — Gmail アカウントを標的とする、コンパイル済みの AutoIT 実行ファイルが、SonicWall Capture Labs の脅威リサーチ・チームにより発見された。このマルウェアは、元々 “File.exe” …
Installing Your Own C2 Server in Kali Linux #kali #c2server #infosec #cybersecurity #cyberwarrior hackers-arise.com/post/command-c…

Sak1To-Shell - Multi-threaded C2 Server And Reverse Shell Client Written In Pure C j.mp/347ljrg #C2Server #ReverseShell #Shell

C2 server extracted from malicious document. Doc SHA256: aaa97571b8c811109ab623de66ca34027193e0e78835abd187f6c5750fc1c6d2 C2 server: http: // 20.106.255.48 Endpoints: /rump /dll @malwrhunterteam @500mk500 #c2server #ThreatHunting #malware #opendir


C2 with shell script. IoC: http: // 185.216.71.192 Endpoints: /aws /lg /thinkphp /pulse /ma @malwrhunterteam @500mk500 #malwarec2 #c2server #mirai #botnet

🚨 Mythic C2 Server Detected 🚨 http://54[.]215[.]152[.]194 A Mythic Command & Control (C2) server has been identified. This C2 framework is often used in targeted attacks and red team operations #CyberSecurity #ThreatIntel #C2Server #MythicC2 #MalwareAlert
![s3curetheweb's tweet image. 🚨 Mythic C2 Server Detected 🚨
http://54[.]215[.]152[.]194
A Mythic Command & Control (C2) server has been identified.
This C2 framework is often used in targeted attacks and red team operations
#CyberSecurity #ThreatIntel #C2Server #MythicC2 #MalwareAlert](https://pbs.twimg.com/media/GpEuLvYWcAAADoX.jpg)
![s3curetheweb's tweet image. 🚨 Mythic C2 Server Detected 🚨
http://54[.]215[.]152[.]194
A Mythic Command & Control (C2) server has been identified.
This C2 framework is often used in targeted attacks and red team operations
#CyberSecurity #ThreatIntel #C2Server #MythicC2 #MalwareAlert](https://pbs.twimg.com/media/GpEuLvbWcAAGHlY.jpg)
Another C2 with juicy files (script, password list etc.) IoC: http: // 194.38.23.170/ Endpoints: /jira /pas /px /ro /scan @malwrhunterteam #c2server #maliciousdomain #malwareresearch #ThreatHunting

earmas.ga - BabyShark - Basic C2 Server j.mp/3hnNk2V #BabyShark #C2Server #GTRS #Linux #Python #Reverse #earmas

Remote Domination: Command & Control Every sophisticated cyber operation needs a central nervous system. #RedTeam #C2Server #Cybersecurity #OffensiveSecurity #Hacking #Botnet #InfoSec #CyberOps #ThreatIntel #Malware #NetworkSecurity #C2Infrastructure #CyberThreats




C2 contains shell script and low detected GoLang binary. Binary: http: // 79.110.62.213/cnc SHA256: ceab7461cdb0c12063075da3edc64da571bb191554cacb9c91ee354be3c41902 @malwrhunterteam @500mk500 #malware #c2server #maliciousscripts


SharpEDRChecker - Checks Running Processes, Process Metadata, DLLs Loaded Into Your Current Process And The Each DLLs Metadata, Common Inst all Directories, Installed Services And Each Service Binaries… dlvr.it/RsTwqz #C2Server #PoshC2 #Python #SharpEDRChecker

#APT34 #Backdoor #C2Server #RussianHackers #IranianHackers #Malware #CyberCrime #CyberAttack #CyberSecurity Russian Turla APT Group Hacked Iranian APT C2 Server For Backdoor Access To Expand The Cyber Attack artemonsecurity.com/snake_whitepap… ncsc.gov.uk/news/turla-gro… media.defense.gov/2019/Oct/18/20…

"RT BabyShark - Basic C2 Server j.mp/3hnNk2V #BabyShark #C2Server #GTRS #Linux #Python #Reverse https://t.co/xCXiNN9BOQ"

"RT Sak1To-Shell - Multi-threaded C2 Server And Reverse Shell Client Written In Pure C j.mp/347ljrg #C2Server #ReverseShell #Shell https://t.co/t088rKsm30"

#malware #C2SERVER #ransomware HASH:58ECD6B9E87F80026E3B063750F46166CF1FE21A5021F43FEFCE930376A2C26B C2 LINK: bit.ly/2q8BBuh

The Ultimate Guide to C2 Servers: Command & Control Server (Installing your own C2 Server on Kali Linux) Explore Here: codelivly.com/the-ultimate-g… #c2server #infosec #cybersec #codelivly #hacking #botnet #cybersecurity #networking #pentesting #redteam #bugbounty #bughountytips

earmas.ga - Sak1To-Shell - Multi-threaded C2 Server And Reverse Shell Client Written In Pure C j.mp/347ljrg #C2Server #ReverseShell #Shell #earmas

LOLBITS v2.0.0 - C2 Framework That Uses Background Intelligent Transfer Service (BITS) As Communication Protocol And Direct Syscalls + Dinvoke For EDR User-Mode Hooking Evasion dlvr.it/RfqgF8 #C2Framework #C2Server #FlaskApplication #Framework #LOLBITS

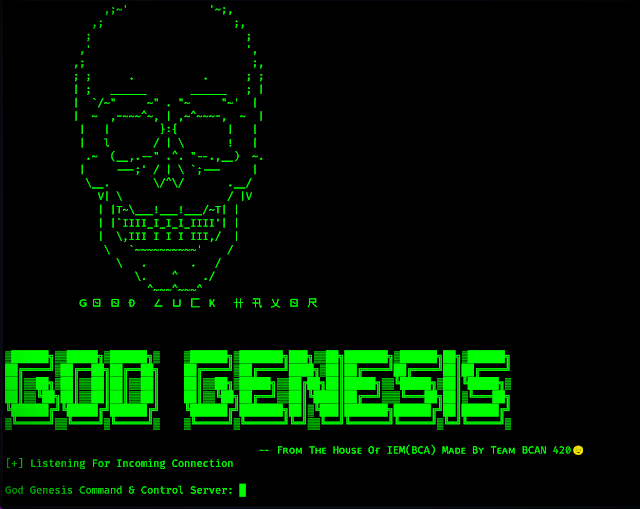
GodGenesis - A Python3 Based C2 Server To Make Life Of Red Teamer A Bit Easier. The Payload Is Capable To Bypass All The Known Antiviruses And Endpoints dlvr.it/Sb78Fs #AntivirusEvasion #C2Server #GodGenesis via KitPloit
Something went wrong.
Something went wrong.
United States Trends
- 1. LINGORM DIOR AT MACAU 123K posts
- 2. #LingOrm_DiorMacau4Seasons 117K posts
- 3. #GenshinSpecialProgram 9,707 posts
- 4. Josh Allen 40.8K posts
- 5. Texans 60.7K posts
- 6. Bills 151K posts
- 7. #FridayVibes 2,970 posts
- 8. Joe Brady 5,365 posts
- 9. Niger 49.8K posts
- 10. OpenMind 51.2K posts
- 11. Infinit 84.2K posts
- 12. #Ashes2025 26.3K posts
- 13. #MissUniverse 480K posts
- 14. McDermott 4,837 posts
- 15. Miden 13.3K posts
- 16. Anderson 28.5K posts
- 17. FINAL DRAFT FINAL LOVE 1.34M posts
- 18. Beane 2,959 posts
- 19. joon 13.6K posts
- 20. Chan 195K posts