#cloudbasedsecurityservices search results
Hybrid Cloud Security Solution is the Most Trusted Cloud Strategy: CISO MAG Survey: Is cloud the ultimate data storage solution? That remains a hot and widely debated topic. Every day more and more organizations are… dlvr.it/RW6L9H #CISOMAG #cloudbasedsecurityservices

Cybersecurity mesh solutions are becoming more popular as enterprises look for ways to improve their cybersecurity posture. bit.ly/3N9VXgj #CLOUDBASEDSECURITYSERVICES #CYBERSECURITYEXPERTS #CYBERSECURITYMESH #DIGITALSECURITY #FUTURECYBERSECURITY #ARHAMSOFT

Hybrid Cloud Security Solution is the Most Trusted Cloud Strategy: CISO MAG Survey: Is cloud the ultimate data storage solution? That remains a hot and widely debated topic. Every day more and more organizations are… dlvr.it/RW6L9H #CISOMAG #cloudbasedsecurityservices

Here are FREE Cloud Security resources to get you started in Cloud Security 👩🏽💻 📌 AWS Security Fundamentals skillbuilder.aws/search?searchT… 🪡 AWS Well-Architected Labs (Security) wellarchitectedlabs.com/security/ 📌 Microsoft SC-900 Security, Compliance, Identity Learning Path…

📚 CYBERSECURITY TOOLS COLLECTION 📚 Practical, tested, and trusted. Bookmark-worthy ⤵️

klosukslikeaja.ss 📁 bejos.cloud/f/ckdtc3ohulm 📁 bejos.cloud/f/8zem0wmrxy7 📁 bejos.cloud/f/ve8rlqki399 📁 bejos.cloud/f/3m7r45ebowk 📁 bejos.cloud/f/cz40r983031 📁 bejos.cloud/f/dp9vqz0jpy9

⚔️ 35 Essential Cybersecurity Tools for Professionals A curated list of top tools used in vulnerability assessment, incident response, digital forensics, and network monitoring. #CyberSecurity #InfoSec #SecurityTools #NetworkSecurity #EthicalHacking #PenTesting #Forensics




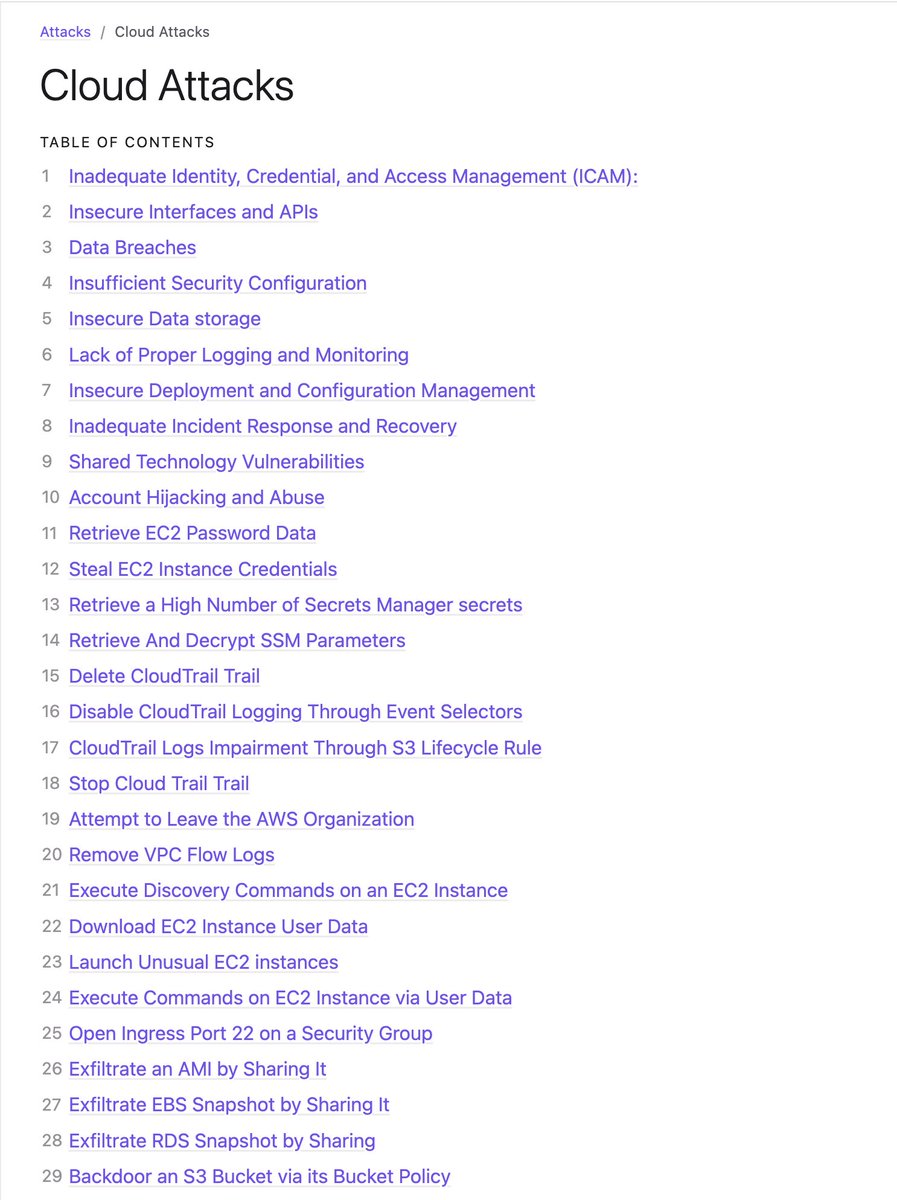
Today, I have a great resource suggestion that you can benefit from regarding cloud attacks❗️☺️ You should definitely add it to your bookmarks.🤞🏻🌸 I wish you a weekend full of great energy❗️😌 Credit: devsecopsguides.com/docs/attacks/c… #cybersecurity #infosec #cloud #cloudsecurity
Cloud power means nothing without security that never blinks. AI that predicts. Systems that protect. CloudSecurity isn’t optional, it’s the future. Stay ahead; secure smarter, not harder. #CyberSecurity #AI #TechInnovation #DataProtection #FutureOfCloud

Cybersecurity doesn’t have to be scary! 👻 With the right IT team, protecting your business becomes simple and stress-free. Reach out and we’ll share a cybersecurity checklist to keep you safe, no scares involved. #Cybersecurity #CyberAwareness #ITSupport #EnvisionConsulting

🔐 Cirrus Safe protects what matters most — your files & privacy. Encrypted, decentralized, and 100 % under your control. No Big Tech tracking. No data mining. Just true digital freedom. #CirrusSafe #OwnYourData #Web3Security

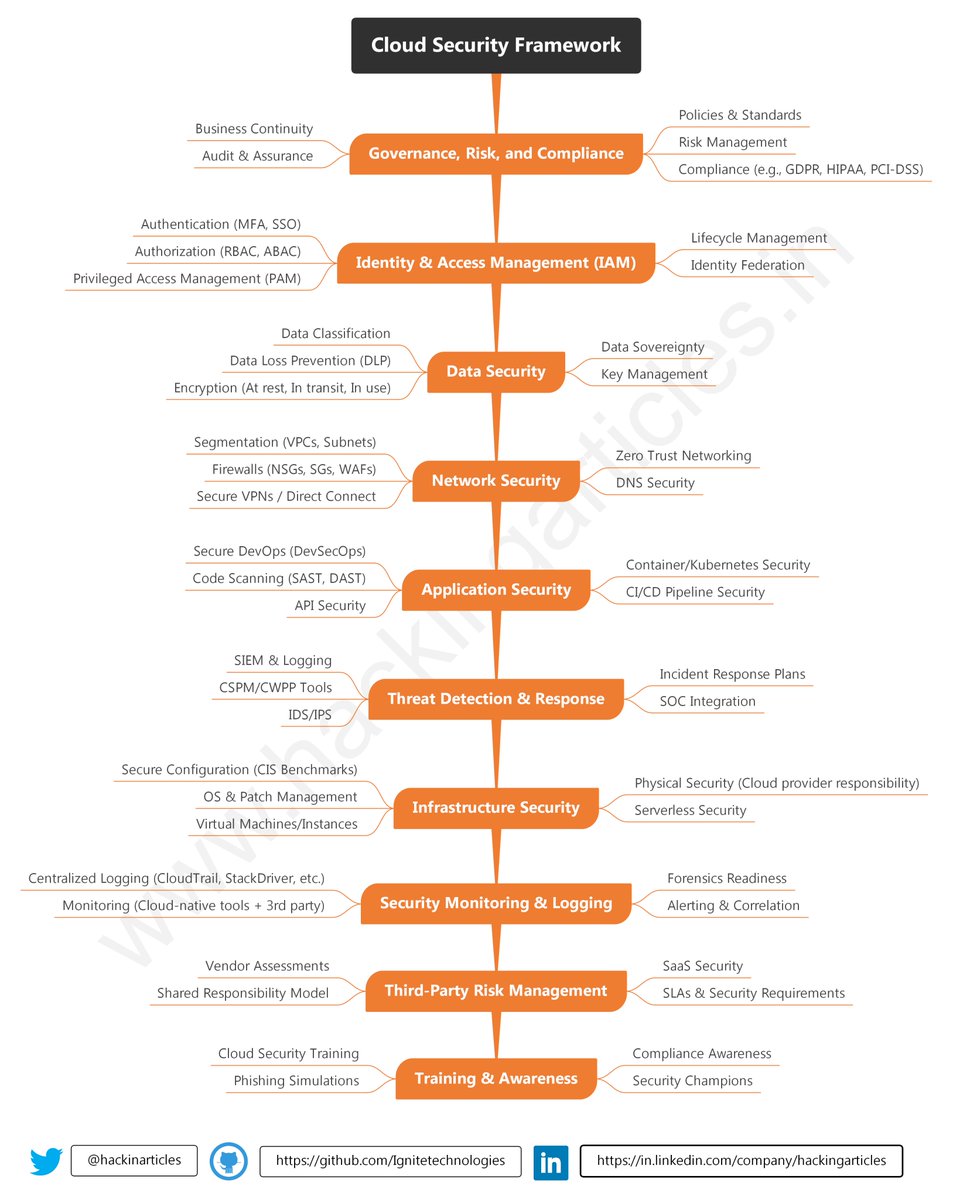
Cloud Security Framework Cheat Sheet 🔴⚫️Full HD Image: github.com/Ignitetechnolo… 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam…
Something went wrong.
Something went wrong.
United States Trends
- 1. Sesko 37.7K posts
- 2. Ugarte 12.7K posts
- 3. Richarlison 17.8K posts
- 4. Amorim 62.3K posts
- 5. Cunha 24.3K posts
- 6. Good Saturday 29.4K posts
- 7. De Ligt 20.9K posts
- 8. Tottenham 74.5K posts
- 9. #SaturdayVibes 4,097 posts
- 10. #TOTMUN 15.9K posts
- 11. #MUFC 22.5K posts
- 12. GAME DAY 29.8K posts
- 13. Casemiro 19.8K posts
- 14. Manchester United 80.3K posts
- 15. Dalot 11.6K posts
- 16. #Caturday 4,218 posts
- 17. #BrazilGP 63.1K posts
- 18. Vicario 1,867 posts
- 19. Lando 34.8K posts
- 20. Man United 34.3K posts