#infosec 搜尋結果
Wyandot Center: Sicherheitsvorfall #Einbruch #Datendiebstahl #infosec #TeamInfoSec #cyberangriff security-incidents.de/sicherheitsvor…
Reporters sans frontières (RSF): Sicherheitsvorfall #Phishing #Hacktivismus #infosec #TeamInfoSec #cyberangriff security-incidents.de/sicherheitsvor…
🚨 Critical #cybersecurity update: Active exploits in #React (CVE-2025-55182), @nextjs , @langflow_ai AI (CVE-2025-34291), & @Android @AndroidDev zero-days. Patch NOW—web/cloud/mobile at risk! 🛡️ #infosec #CVE #ZeroDay #WebDev #cloudsecurity #MobileSecurity #RCE #PatchTuesday…
linkedin.com
Top Content on LinkedIn
Explore top LinkedIn content from members on a range of professional topics.
Ransomware-Angriff: Gepa #Ransomware #Ausfall #infosec #TeamInfoSec #cyberangriff security-incidents.de/sicherheitsvor…
Your business deserves top-tier protection. 🛡️ SysfoCyber delivers threat detection, data security & zero-downtime strategies to keep you safe 24/7. Get started → sysfotion.com/sysfocyber/ #CyberSecurity #InfoSec #DataProtection #CyberThreats #ITSecurity #SysfoCyber #Sysfotion

Leroy Merlin: Sicherheitsvorfall #Einbruch #Datendiebstahl #infosec #TeamInfoSec #cyberangriff security-incidents.de/sicherheitsvor…
Is your critical software vendor about to be sanctioned? Geopolitics is now a major factor in IT procurement. We explain the new reality of buying tech in a fractured world. modelodge.com/the-new-due-di… #Infosec #Business
DAY : 2 Just completed the "Phishing" room on @TryHackMe! 🎯 A great intro to how phishing works and how to spot it. Hands-on practice is key to building those essential #cybersecurity skills. #TryHackMe #InfoSec #LearnByDoing tryhackme.com/r/room/phishin…
Stop building massive LLMs. "Shadow AI" is causing 20% of data breaches. The cloud is leaking. The fix isn't better firewalls; it's Small Language Models (SLMs) that run offline. Read article - wix.to/Vgk3Yo3 #AI #DevOps #InfoSec #Mistral #TechTrends
Ростелеком зафиксировал заметный рост звонков от мошенников, которые пытаются выдавать себя за операторов прямой линии: securitymedia.org/news/rosteleko… #infosecurity #CyberMedia #infosec #ИБ #Россия

We write and review your company #InformationSecurity policies and procedures: #infosec #cybersecurity #databreach ift.tt/bNpfTUG
How To Get Your First Job In #Cybersecurity: a blog post of all the steps you need to transition into #InfoSec! twp.ai/ImsxdP

Firmware encryption bypass on ESP32 through side channel attack (2024) courk.cc/breaking-flash… #infosec #espressif


Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
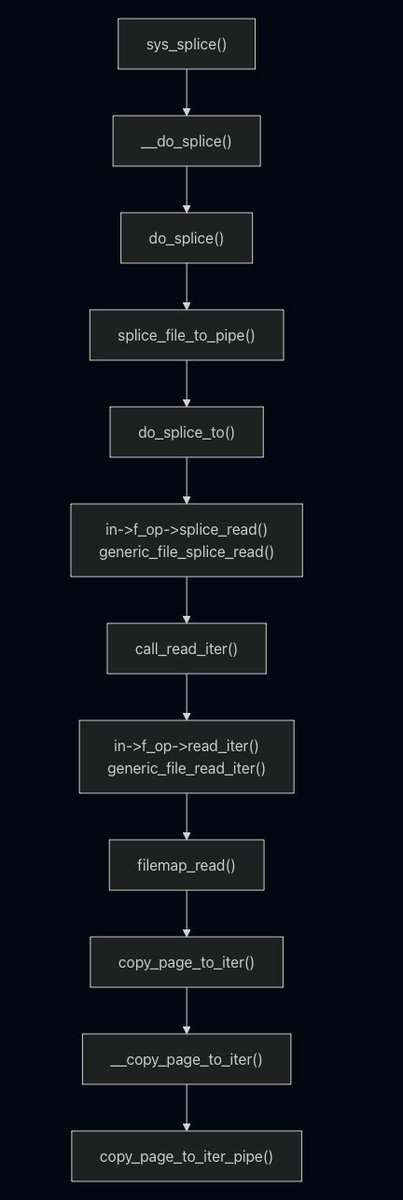
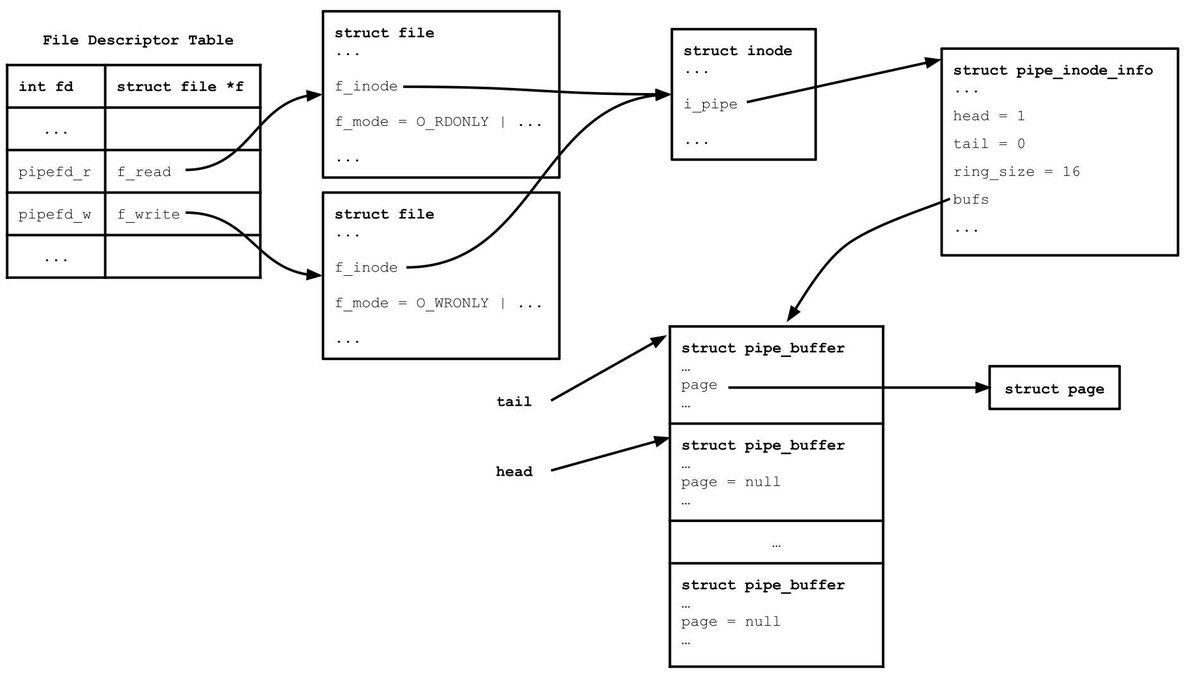
Learning how to exploit DirtyPipe vulnerability in Linux kernel (@0xnull007 and @stdnoerr) 0xnull007.github.io/posts/dirtypip… stdnoerr.blog/blog/DirtyPipe… #infosec #Linux
SOC Operations 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting

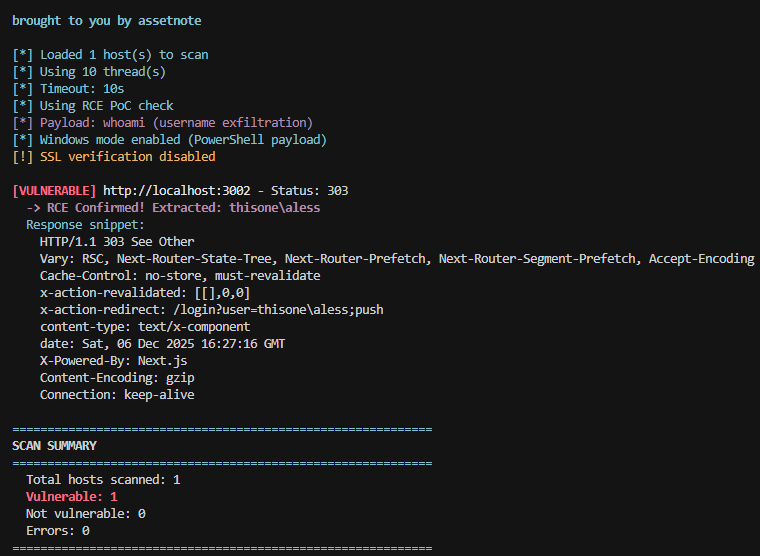
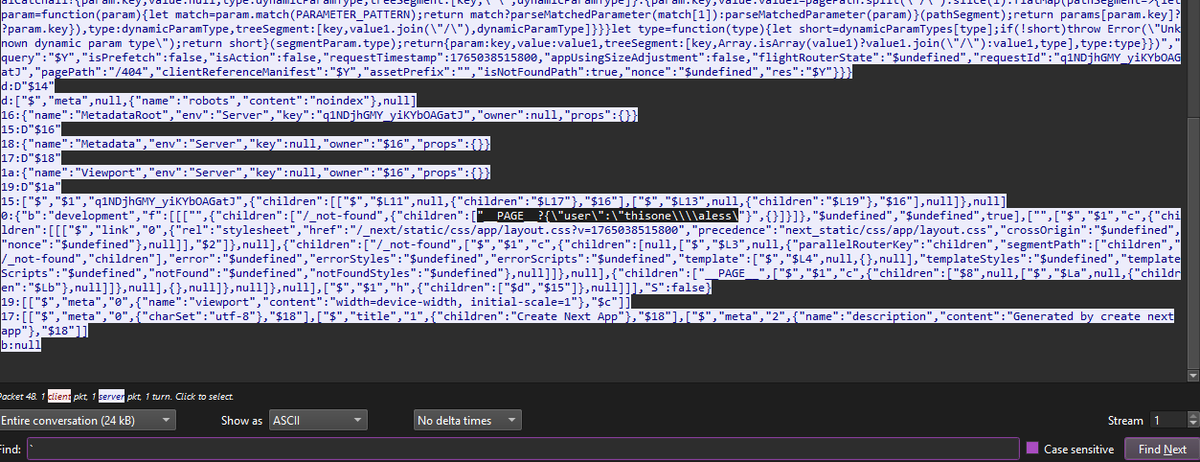
Testing my modified version of the scanner for the new Next.js RCEs by @assetnote. Targeting CVE-2025-55182 & CVE-2025-66478. Confirmed working on: Next.js 15.0.0 React 19.0.0-rc (RSC) on Win. It worked! 🔗 github.com/alessiodos/rea… #InfoSec #BugBounty #NextJS #CyberSecurity #RCE
Pic of the Day 🔥 Telegram: t.me/hackinarticles #infosec #cybersecurity #informationsecurity #pentesting #ITSecurity #OSCP #PenTesting

Exploiting Lexmark's Postscript stack (arbitrary read/write) boredpentester.com/pwn2own-2025-p… Credits @boredpentester #infosec
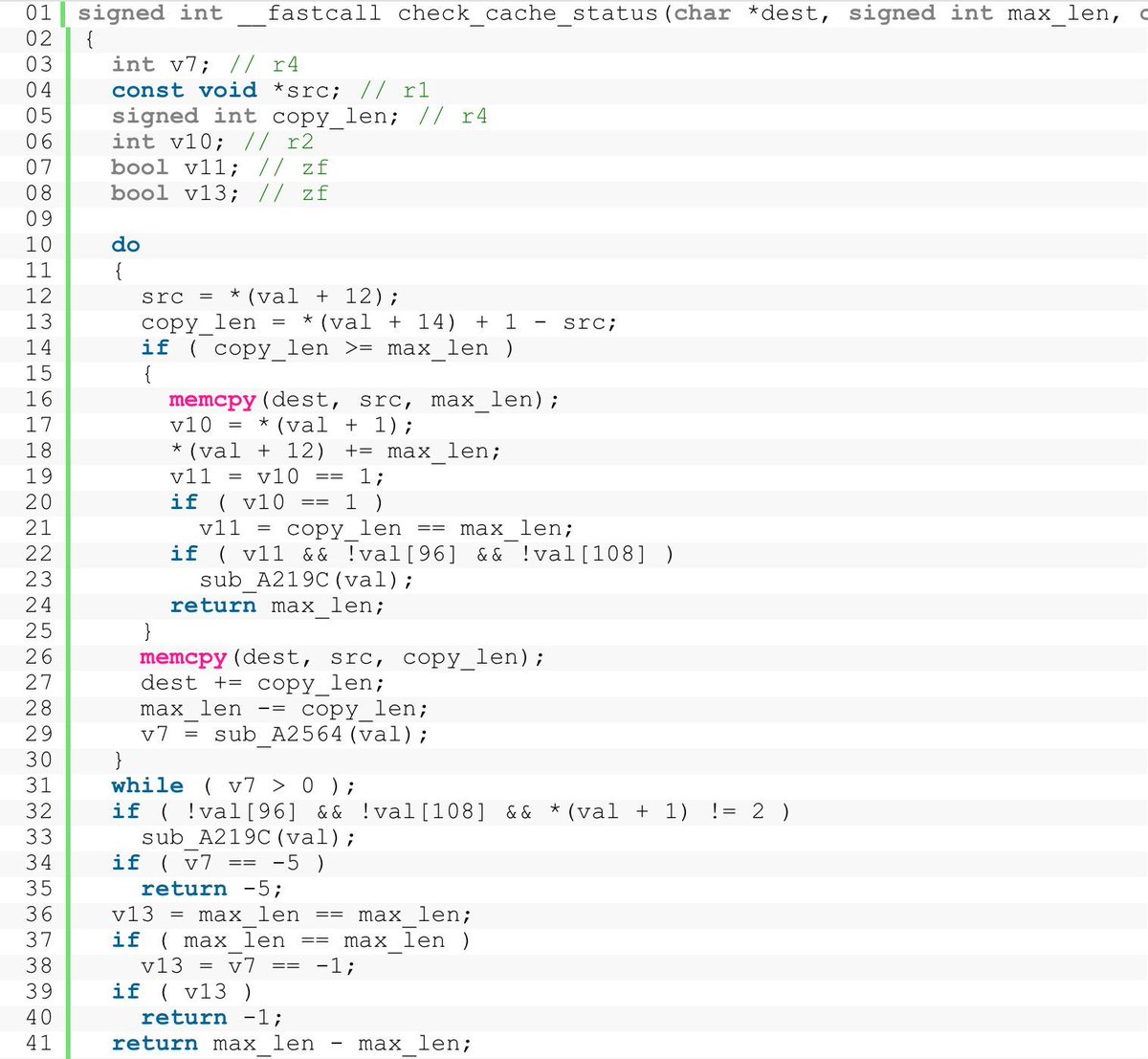
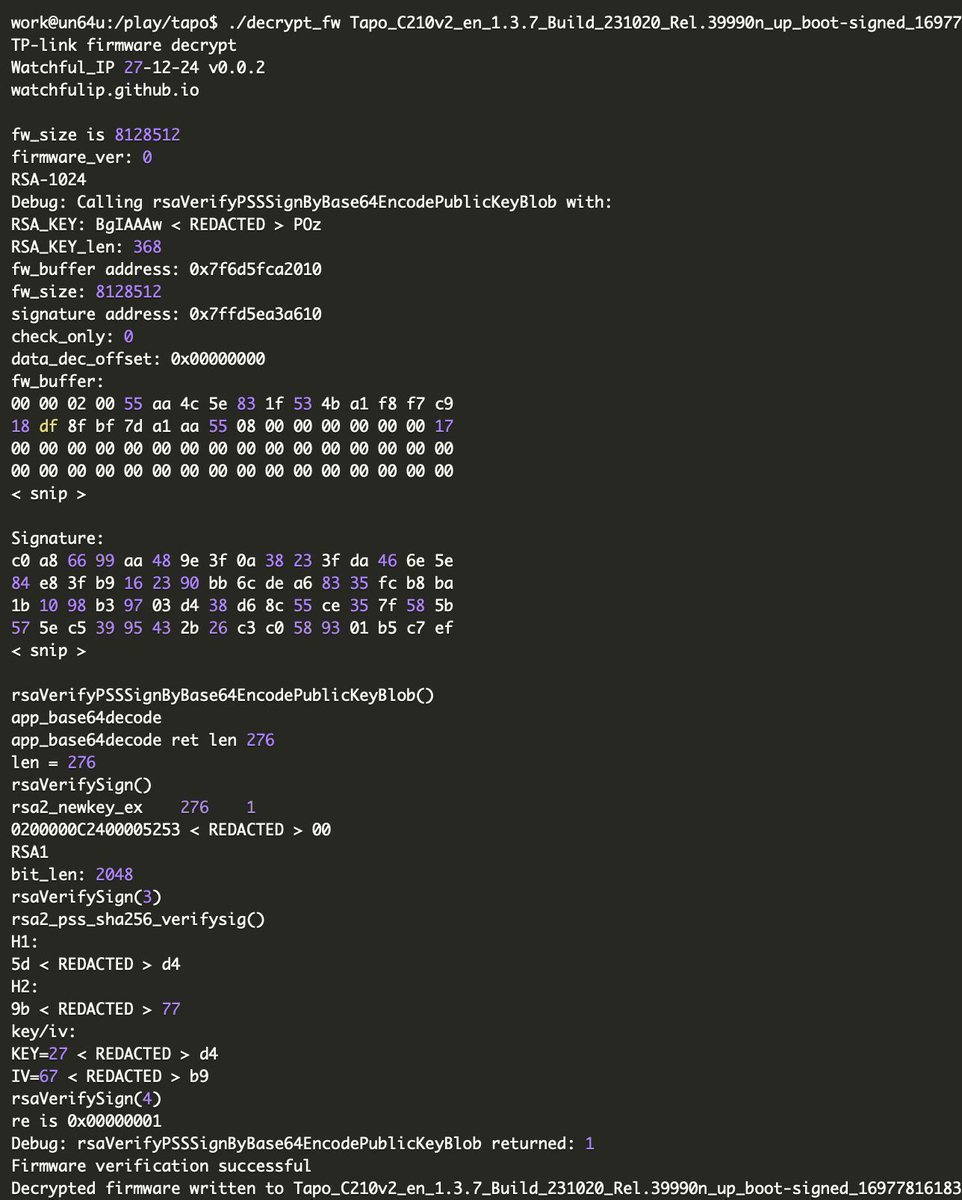
TP-Link (Tapo) C210 cloud camera: bootloader vulnerability and firmware decryption watchfulip.github.io/28-12-24/tp-li… Credits @Watchful_IP #embedded #infosec
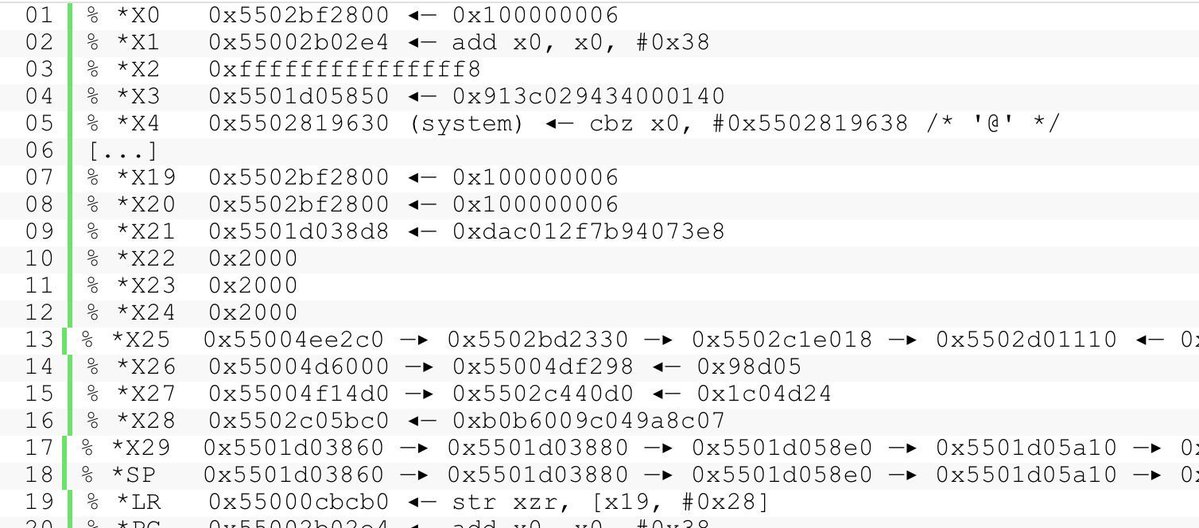
pre-auth RCE (CVE-2025-9242) stack buffer overflow vulnerability in WatchGuard Fireware OS labs.watchtowr.com/yikes-watchgua… Credits @watchtowrcyber #infosec

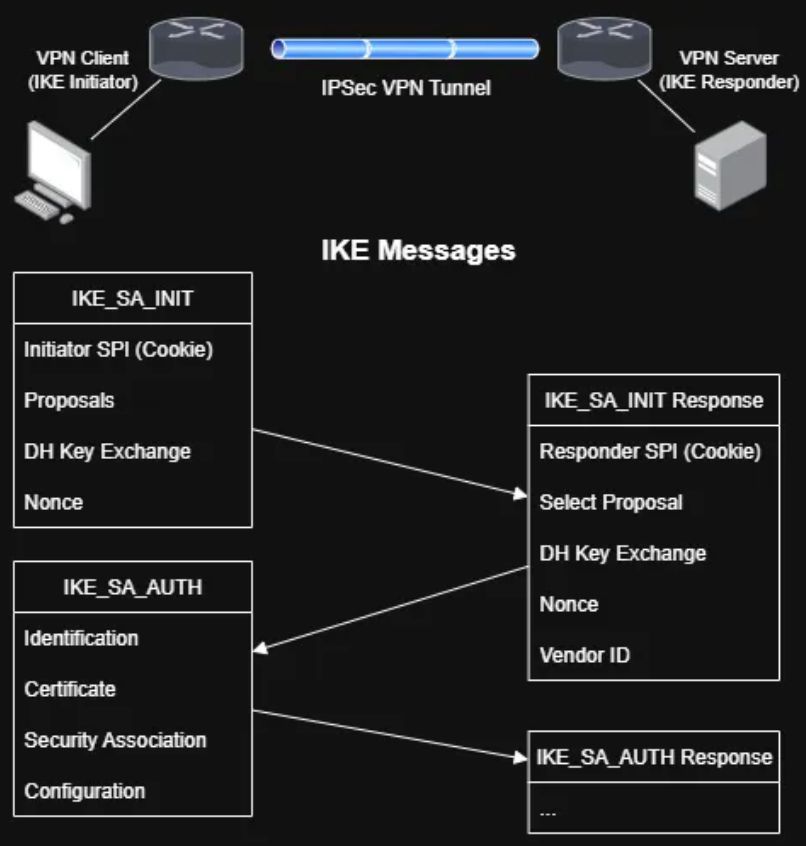
Offensive Linux Security Tools Credit @xmodulo 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting

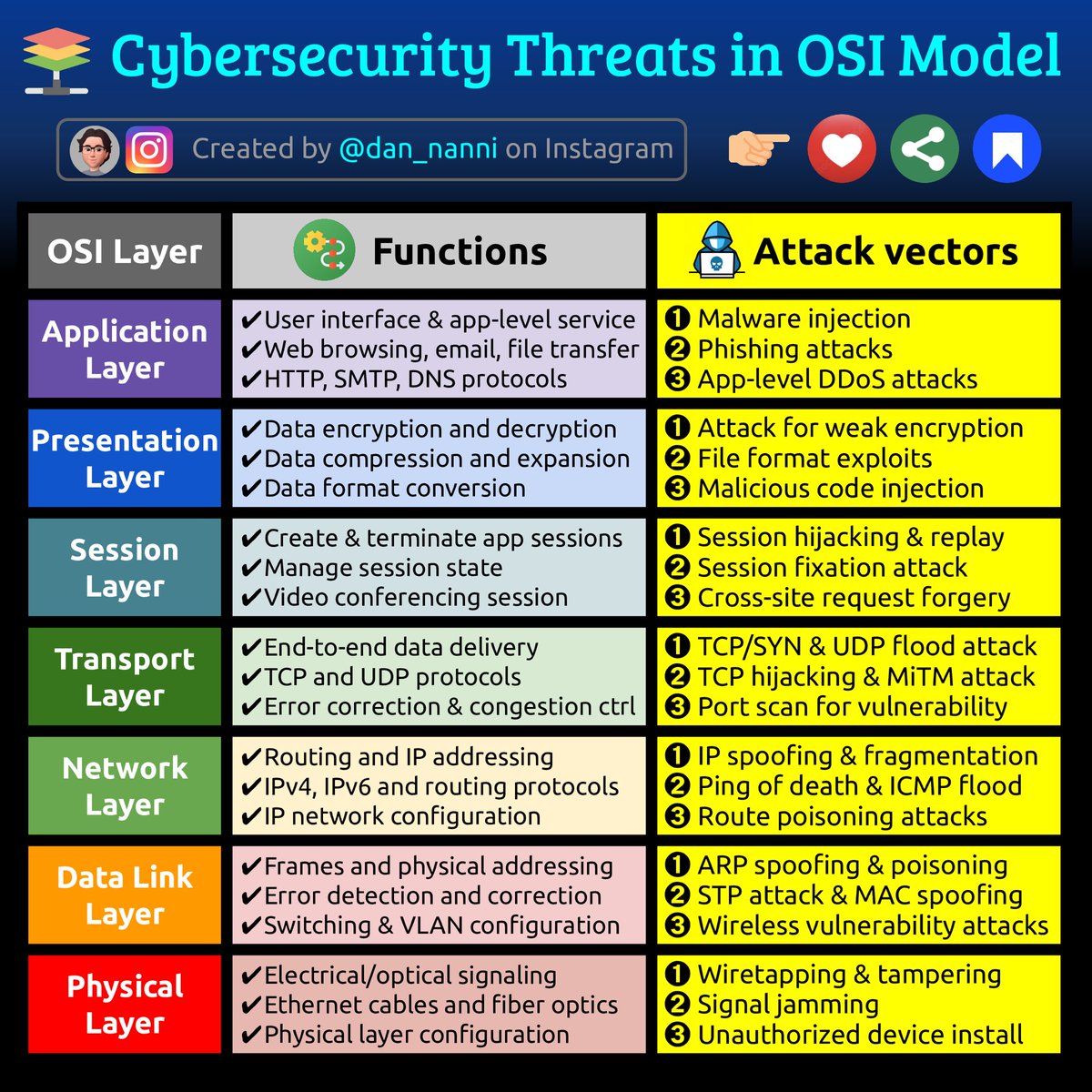
Cybersecurity Threats in OSI Model Credit @xmodulo 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP…
🎉 Censys is honored to be included in the 2025 Deloitte Technology Fast 500! As THE Authority for Internet intelligence and insights, we’re committed to strengthening global cybersecurity. Thank you to our team, customers, and partners. 🌐🙌 #Censys #Cybersecurity #InfoSec

Pic of the Day 🔥 Telegram: t.me/hackinarticles #infosec #cybersecurity #informationsecurity #pentesting #ITSecurity #OSCP #PenTesting

Pic of the Day 🔥 Telegram: t.me/hackinarticles #infosec #cybersecurity #informationsecurity #pentesting #ITSecurity #OSCP #PenTesting

🚨 Just found NEW XSS On Salesforce the “component” allow to bypass the CSP and Firewall. The path appears like that: /apex/CommVisualforce?params=eyJjb21wb25lbnQiOiJjb21tQWxyZWFkeUN1c3RvbWVyIn0= {"component":"commAlreadyCustomer"} #BugBounty #Bugbountytips #infosec

Something went wrong.
Something went wrong.
United States Trends
- 1. Chiefs 108K posts
- 2. Mahomes 39.3K posts
- 3. Kelce 24.5K posts
- 4. Texans 47K posts
- 5. #ITWelcomeToDerry 61K posts
- 6. Andy Reid 6,820 posts
- 7. #BaddiesUSA 29.4K posts
- 8. Collinsworth 6,697 posts
- 9. Rashee Rice 8,770 posts
- 10. #HOUvsKC 2,108 posts
- 11. Stroud 10.5K posts
- 12. Chris Jones 2,761 posts
- 13. Pennywise 30.5K posts
- 14. #HTownMade 2,962 posts
- 15. Pitre 6,591 posts
- 16. doyoung 239K posts
- 17. jungwoo 257K posts
- 18. Jeff Kent 8,898 posts
- 19. Nagy 2,437 posts
- 20. AFC West 4,937 posts



























