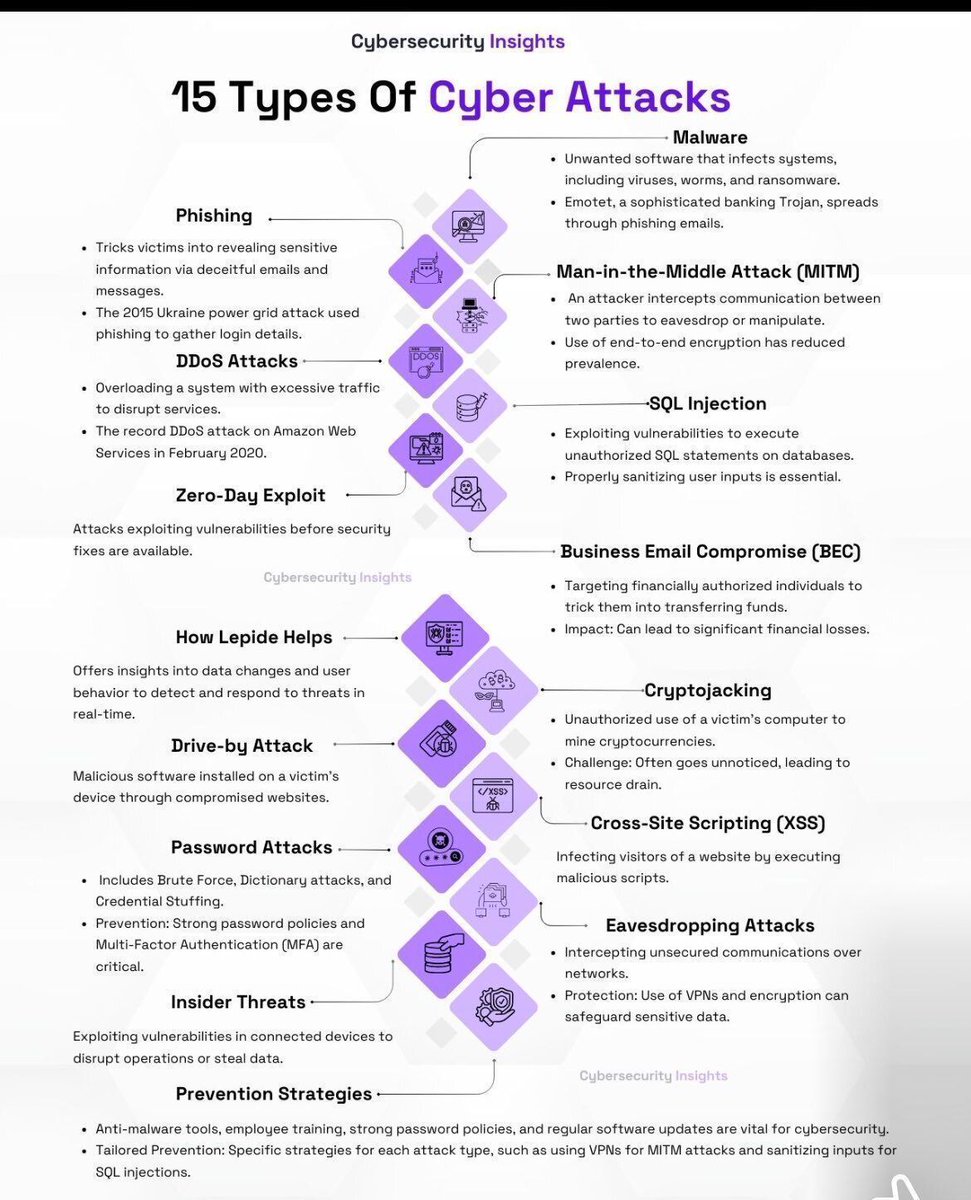
#infosec 검색 결과
CVE-2025-55182 (React2Shell) pre-auth RCE FOFA, Shodan,Zoomeye filters : vul.cve="CVE-2025-55182" , asn="REDACTED" && (app="Next.js" || app="React.js") #infosec #cybersec #BugBounty #bugbountytips - Github: github.com/l4rm4nd/CVE-20…

📲 Introduction to Android Pentesting for Beginners Blog: tsublogs.wordpress.com/2022/11/18/int… #pentesting #infosec
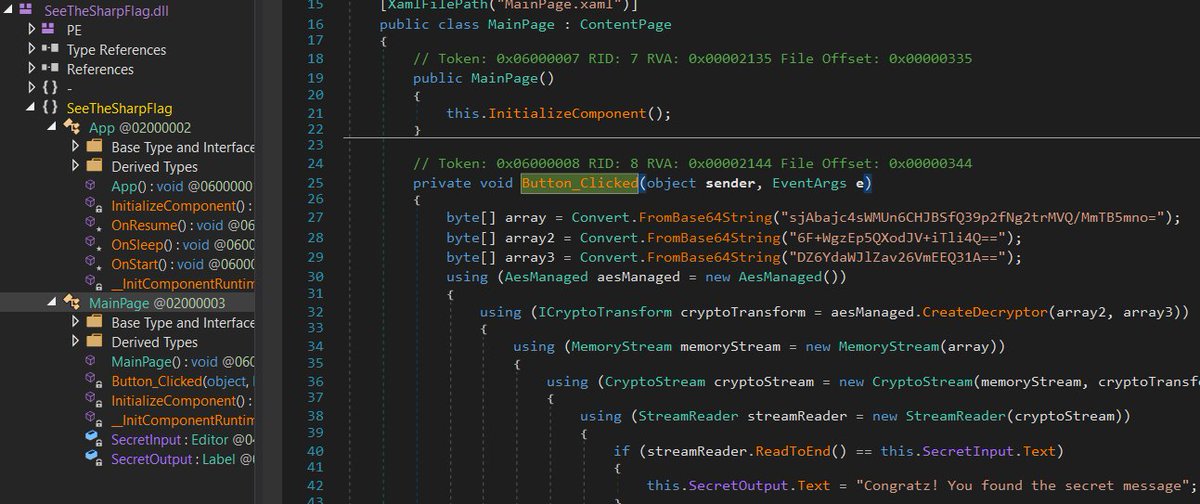
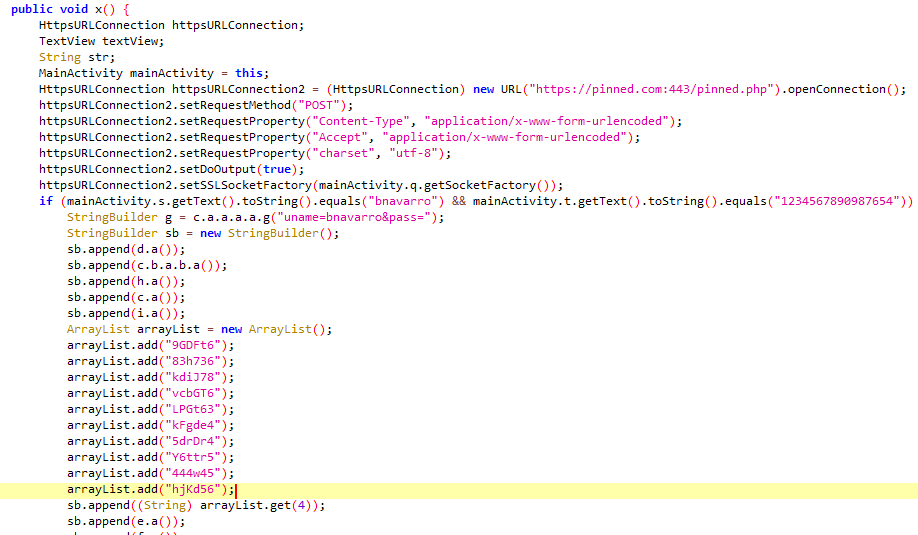
Exploiting an N-day vulnerability in Qualcomm Adreno GPUs microcode xploitbengineer.github.io/CVE-2025-21479 #infosec

SOC Operations 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting

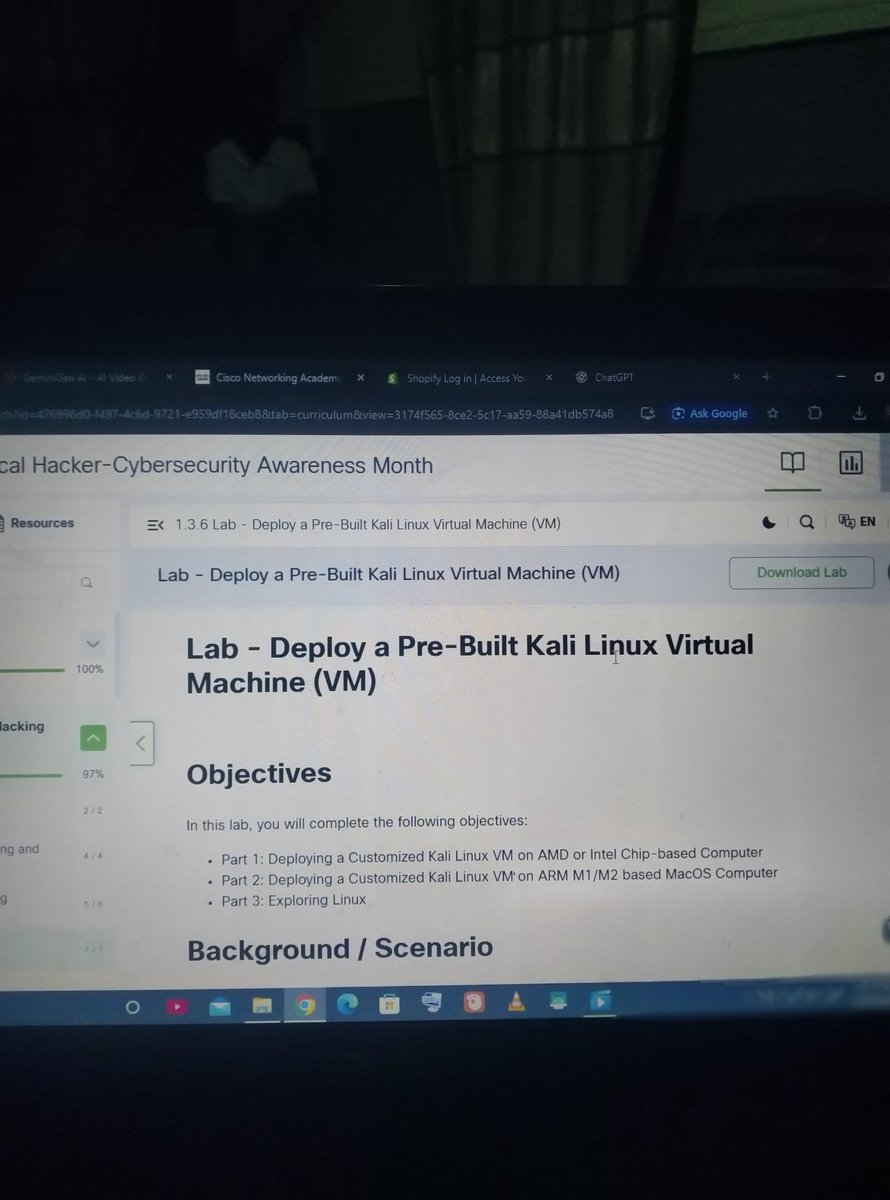
"Day 3 of my #cybersecurity journey! 🚀 Just learned how to set up my Kali Linux lab environment and I'm excited to start practicing #ethicalhacking skills! 💻🔒 #infosec #hacking #LearningJourney
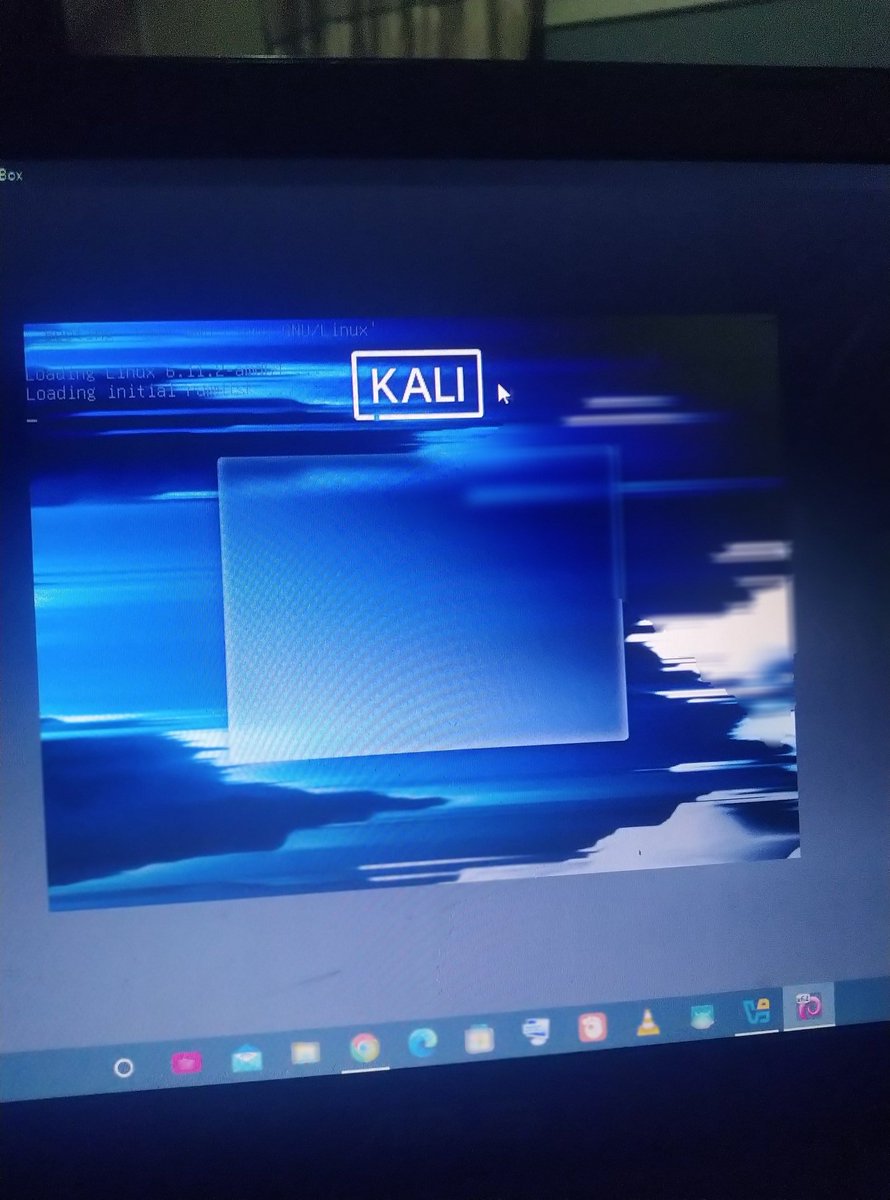

Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
Automates LLM fuzzing to identify jailbreaks✨ - github.com/cyberark/Fuzzy… #infosec #cybersec #aisec
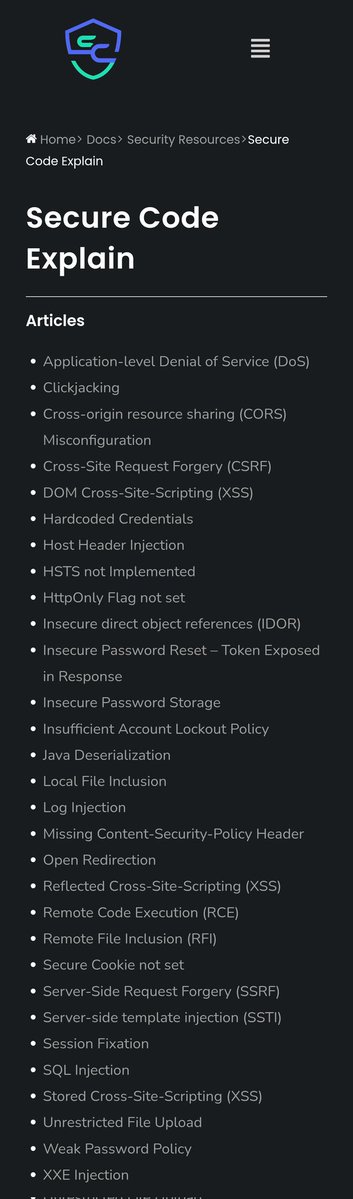
this Secure Code Explain page is a goldmine. Super easy breakdowns of common vulns with vulnerable code: securitycipher.com/docs/security/… #bugbountytips #InfoSec
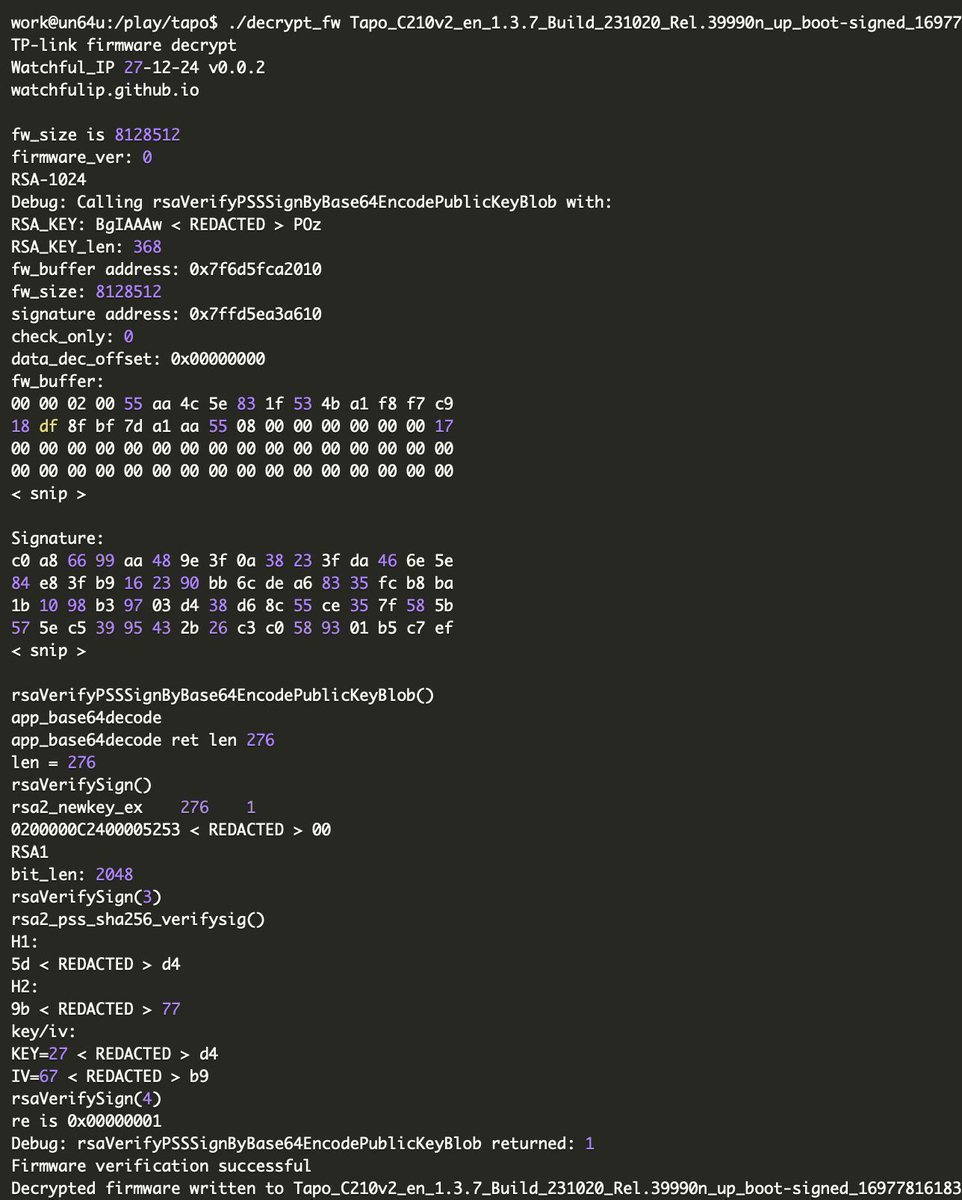
TP-Link (Tapo) C210 cloud camera: bootloader vulnerability and firmware decryption watchfulip.github.io/28-12-24/tp-li… Credits @Watchful_IP #embedded #infosec
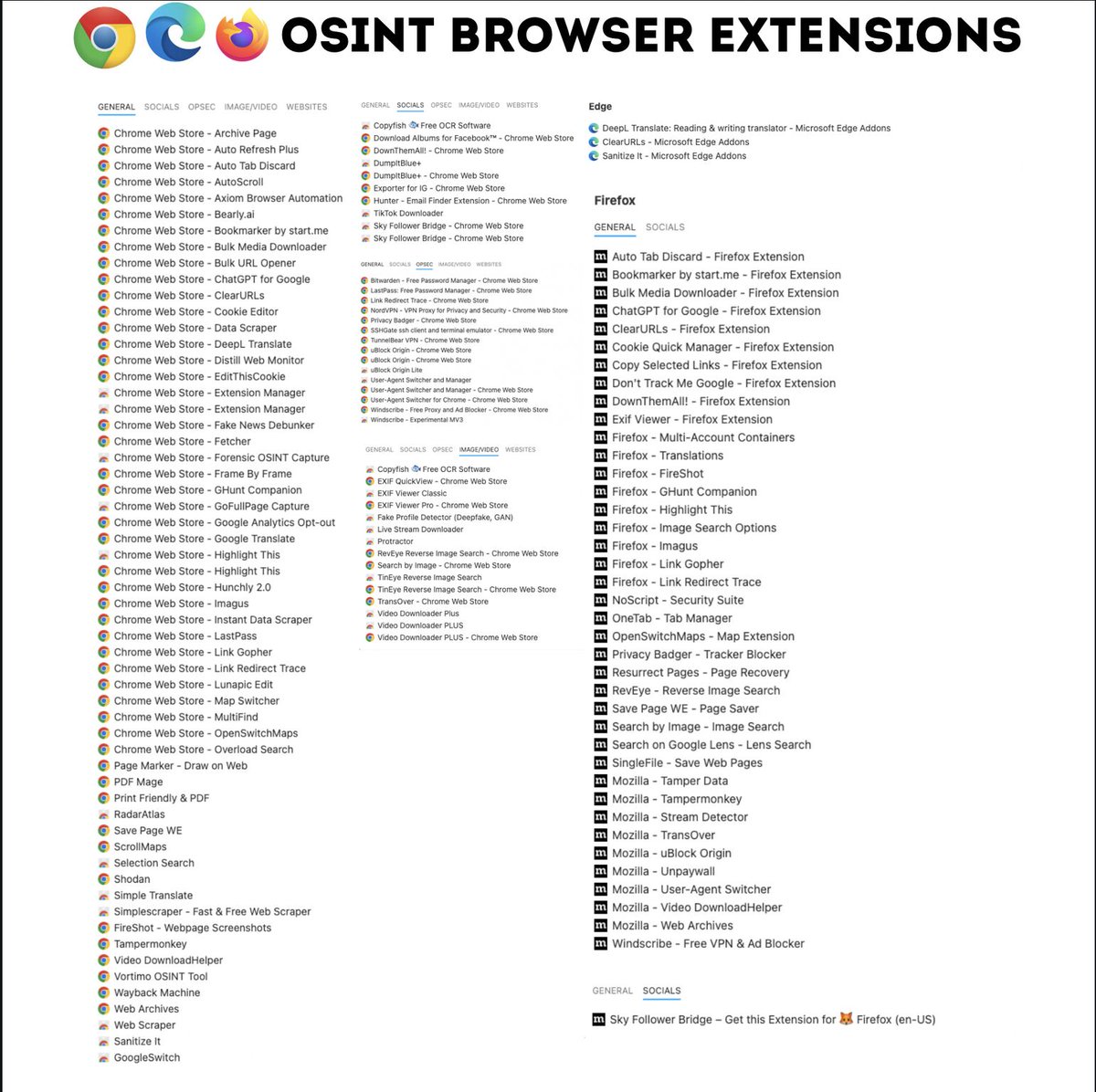
OSINT Browser Extensions 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting
🎅✨ En esta temporada de fiestas, no solo pienses en los regalos bajo el árbol… piensa también en la seguridad de tu empresa. 🔐 Esta Navidad, cuida lo más valioso: protege tus datos, tu reputación y la confianza de tus clientes. #Ciberseguridad #NavidadSegura #InfoSec…
Getting RCE on Brother printer (MFC-J1010DW) by chaining three vulnerabilities starlabs.sg/blog/2025/11-b… Credits Nguyên Đăng Nguyên & Manzel Seet & Amos Ng (@starlabs_sg) #infosec
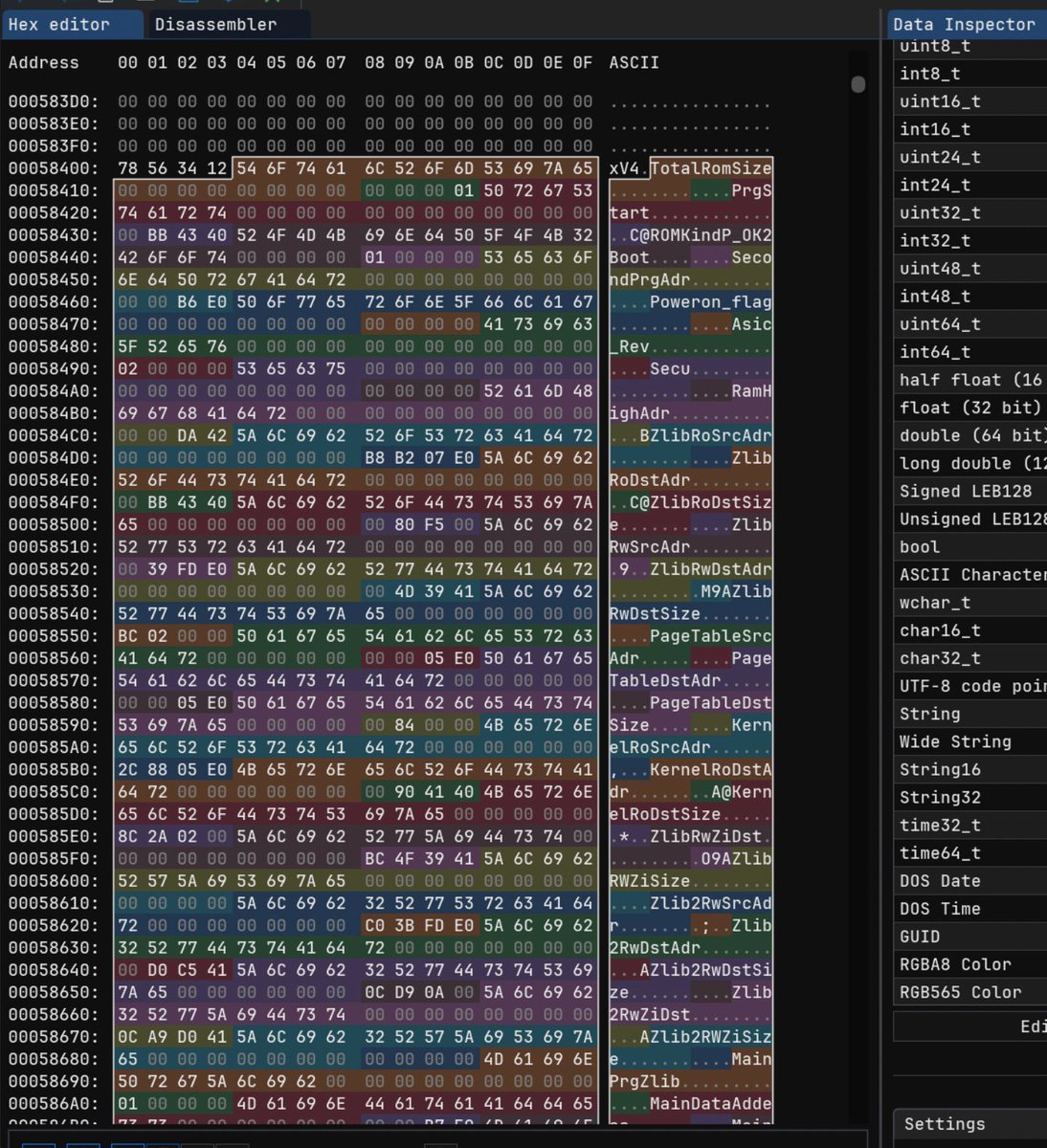

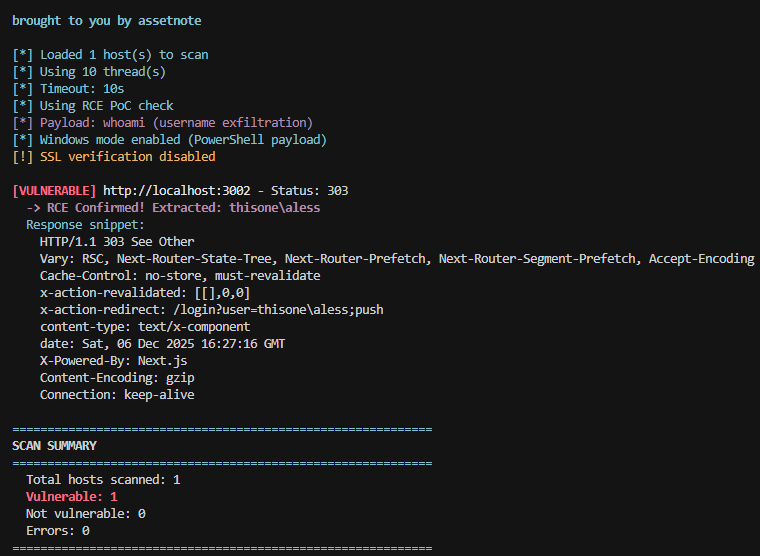
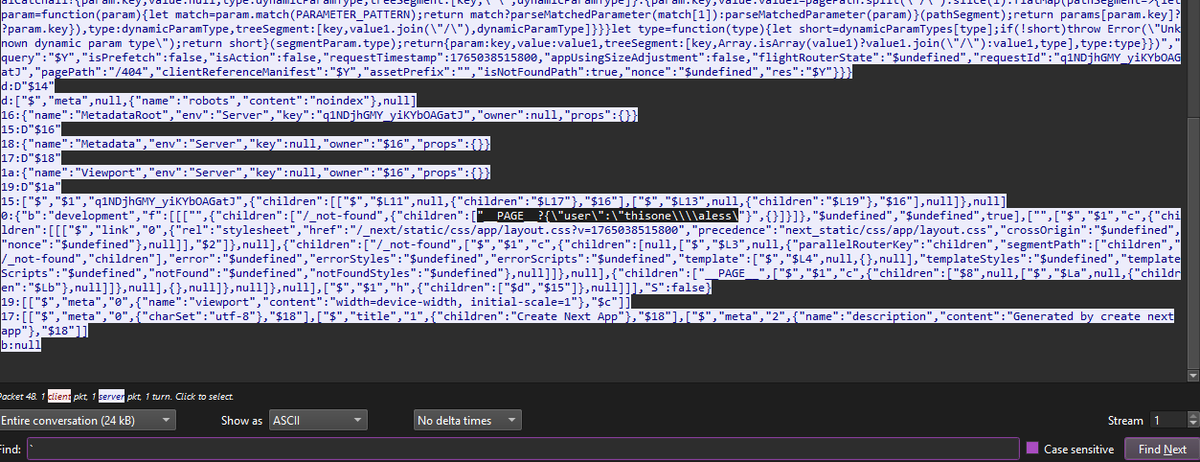
Testing my modified version of the scanner for the new Next.js RCEs by @assetnote. Targeting CVE-2025-55182 & CVE-2025-66478. Confirmed working on: Next.js 15.0.0 React 19.0.0-rc (RSC) on Win. It worked! 🔗 github.com/alessiodos/rea… #InfoSec #BugBounty #NextJS #CyberSecurity #RCE
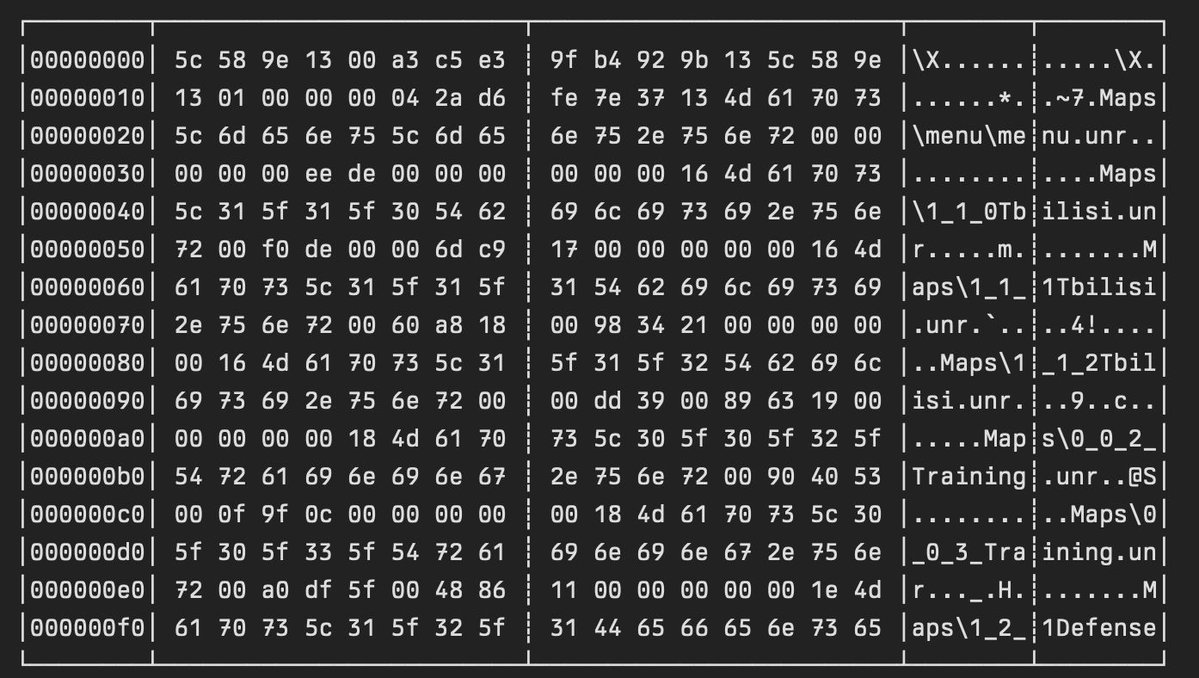
Interesting deep-dive into reverse-engineering an Unreal Engine 2 file format (.lin) for game assets landaire.net/a-file-format-… Credits @landaire #infosec

Automated risk management is changing how security teams work. Faster assessments, fewer manual tasks and clearer visibility make it easier to stay ahead of threats. Read more: bit.ly/4oKjkj0 #CyberSecurity #Automation #InfoSec #HiTechNectar

🛑 Microsoft Patch Tuesday de décembre 2025 Au total, 57 vulnérabilités ont été corrigées dans les produits et services Microsoft (sans tenir compte des patchs Edge). Mon récapitulatif par ici 👇 - it-connect.fr/patch-tuesday-… #Microsoft #PatchTuesday #infosec #cybersecurite

🔧 "Microsoft fixes exploited zero-day flaw on Light Patch Tuesday, with over 1,150 security patches released so far this year. Take immediate action to update your systems to prevent potential attacks." darkreading.com/application-se… #ZeroDay #Exploit #InfoSec
New critical threats: Sneeit #WordPress RCE is being mass exploited, while a flaw in ICTBroadcast is fueling a new precision-targeted Frost DDoS botnet. Backdoors, admin hijacks, and automated exploitation are accelerating. Patch immediately. #Cybersecurity #InfoSec #Canada

🚨 #phishing report issued 🚨 🌐 Suspected URL: https://uniswap-viewers[.]web[.]app/ 🔎 Analysis: urlscan.io/result/019b047… 🔒 #InfoSec 🛡️ @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: https://uniswap-viewers[.]web[.]app/
🔎 Analysis: urlscan.io/result/019b047…
🔒 #InfoSec
🛡️ @Phish_Destroy](https://pbs.twimg.com/media/G7yd3quXkAAb0_P.png)
Australian cyber threats have intensified.🚨 From a critical React RCE (CVE-2025-55182) to Defence supply chain breaches and AI identity attacks, no sector is immune. See our full analysis & mitigation steps. Read more: leansecurity.com.au/blog/2025/12/1… #CyberSecurity #InfoSec #Australia
🚨 #phishing report issued 🚨 🌐 Suspected URL: http://suite-trezor[.]click 🔎 Analysis: urlscan.io/result/019b069… 🔒 #InfoSec 🛡️ @CloudflareHelp @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: http://suite-trezor[.]click
🔎 Analysis: urlscan.io/result/019b069…
🔒 #InfoSec
🛡️ @CloudflareHelp @Phish_Destroy](https://pbs.twimg.com/media/G7ycNg5WoAAiEv1.png)
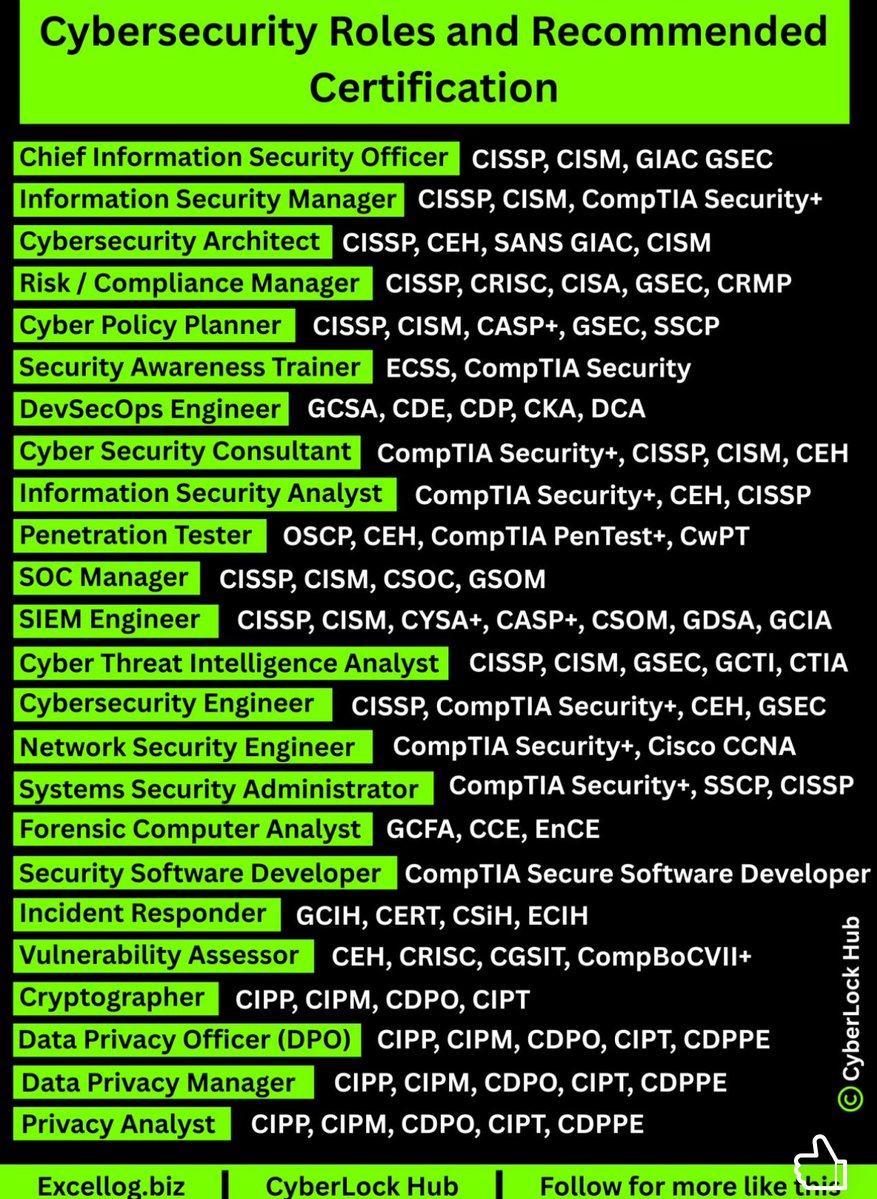
🛡 Cybersecurity Roles & Recommended Certifications The cybersecurity field offers a wide range of professional roles, each requiring different skills, responsibilities, and certification paths. #CyberSecurity #InfoSec #Career #Certification #CyberJobs
AI security isn't optional anymore—it's survival. Smart attackers use AI. Smarter defenders do too. DM us if your org needs AI-powered defense🛡️ #CyberSecurity #AI #InfoSec

"Attackers need just one point of entry. Defenders must secure them all." — MIT CAMS AI widens this gap dramatically. Traditional security = bringing a knife to a drone fight #CyberSecurity #AI #InfoSec
🚨NEW: 80% of ransomware attacks now use AI MIT study of 2,800 incidents shows cybercriminals have weaponized AI—and traditional defenses can't keep up. The threat landscape just changed fundamentally. 🧵 #CyberSecurity #AI #InfoSec
🚨 #phishing report issued 🚨 🌐 Suspected URL: http://solmysterygift[.]xyz 🔎 Analysis: urlscan.io/result/019b069… 🔒 #InfoSec 🛡️ @CloudflareHelp @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: http://solmysterygift[.]xyz
🔎 Analysis: urlscan.io/result/019b069…
🔒 #InfoSec
🛡️ @CloudflareHelp @Phish_Destroy](https://pbs.twimg.com/media/G7ybfPNXoAAf5G8.png)
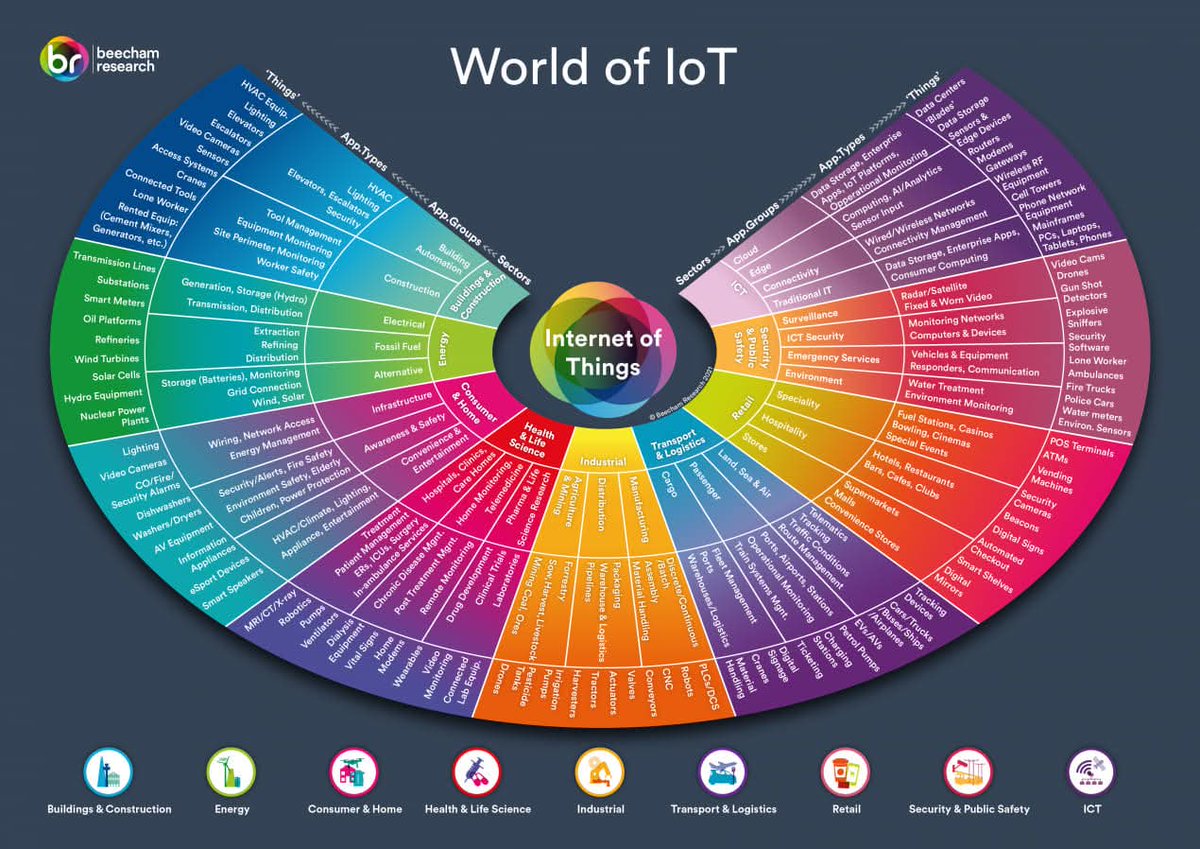
🌍World of IoT 🏢Buildings & Constructions ⚡Energy 🏠Consumer & Home 🩸Health & Life Science 🏭Industrial ✈️Transport & Logistics 🛍️Retail 🛡️Security & Public Safety 📱ICT 🔖#infosec #cybersecurity #hacking #pentesting #security
Irish HSE will pay €750 to each of ~90k victims of the 2021 Conti ransomware attack—the first health‑sector settlement. Phishing‑prone IT drives liability; audit email filters, segment networks. thecyberexpress.com/hse-cyberattac… #infosec #ransomware
🚨 #phishing report issued 🚨 🌐 Suspected URL: https://rabbicareers[.]com/wp-includes/customize/class-wp-customize-partial[.]html 🔎 Analysis: urlscan.io/result/019b047… 🔒 #InfoSec 🛡️ @GoDaddyHelp @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: https://rabbicareers[.]com/wp-includes/customize/class-wp-customize-partial[.]html
🔎 Analysis: urlscan.io/result/019b047…
🔒 #InfoSec
🛡️ @GoDaddyHelp @Phish_Destroy](https://pbs.twimg.com/media/G7yaHodXkAAbyA1.png)
Fedora 43: lunasvg 2025 58c0baba42 Unbundle plutovg from lunasvg, this avoids shipping a duplicate library with conflicting files. Update lunasvg to consume the plutovg v... #Fedora #Linux #infosec #opensource #linuxsecurity tinyurl.com/23uq374q

Something went wrong.
Something went wrong.
United States Trends
- 1. UConn 7,714 posts
- 2. #MerryChristmasJustin 2,889 posts
- 3. Danity Kane 2,077 posts
- 4. Slept 20.8K posts
- 5. #WWENXT 17.7K posts
- 6. Boogie Fland N/A
- 7. Aundrea N/A
- 8. Lamar Wilkerson 1,508 posts
- 9. Raptors 11.5K posts
- 10. Scottie Barnes 2,457 posts
- 11. #RHOSLC 4,493 posts
- 12. Xaivian Lee N/A
- 13. MSPs 2,168 posts
- 14. Todd Golden N/A
- 15. Jalen Brunson 3,781 posts
- 16. Cale Makar N/A
- 17. Gowdy 5,669 posts
- 18. #iubb 1,681 posts
- 19. Oilers 3,389 posts
- 20. #bb27 N/A