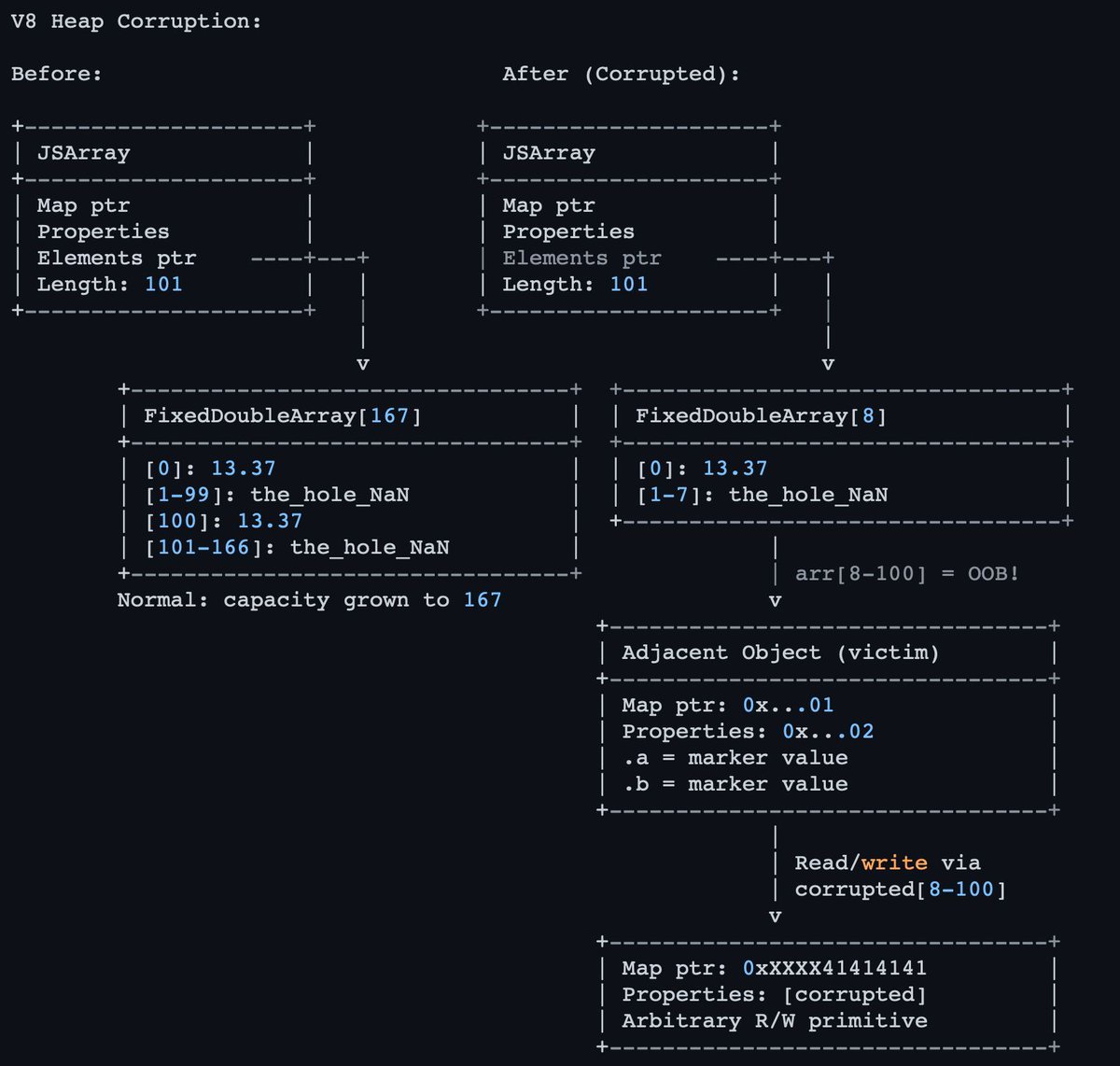
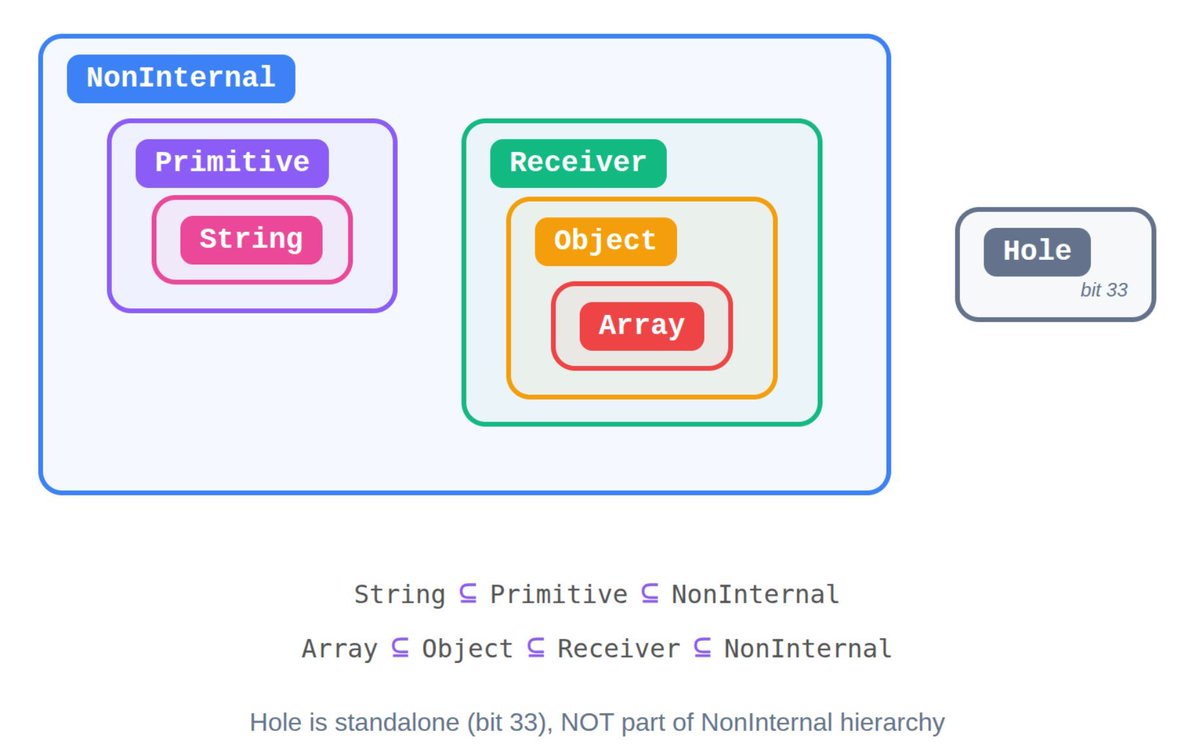
#infosec ผลการค้นหา
Interesting short blog post on how electronic passports cryptography works blog.trailofbits.com/2025/10/31/the… Credits Joop van de Pol (@trailofbits) #infosec #embedded


No vibes, just coded, Opus 4.5 still goated. There's no better feeling than when you have finally built your own full scale investigative platform. Artificial Intelligence is the game changer. #AI #OSINT #InfoSec
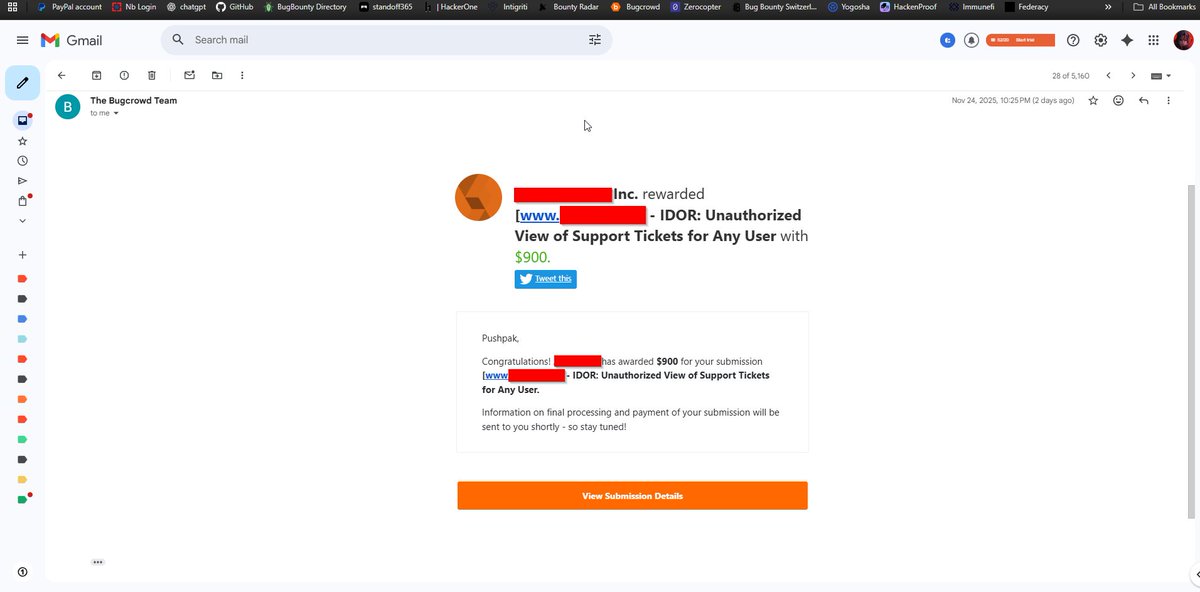
6 months into cyber security. Still hunting for my first bug bounty. Got 2 informational reports so far. It's tough but I'm not giving up. Leaving this here to remember: keep going. @Bugcrowd #bugbounty #infosec #cybersecurity #nevergiveup
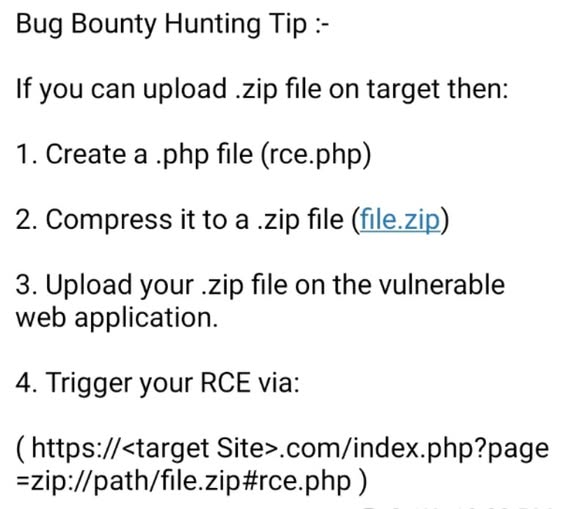
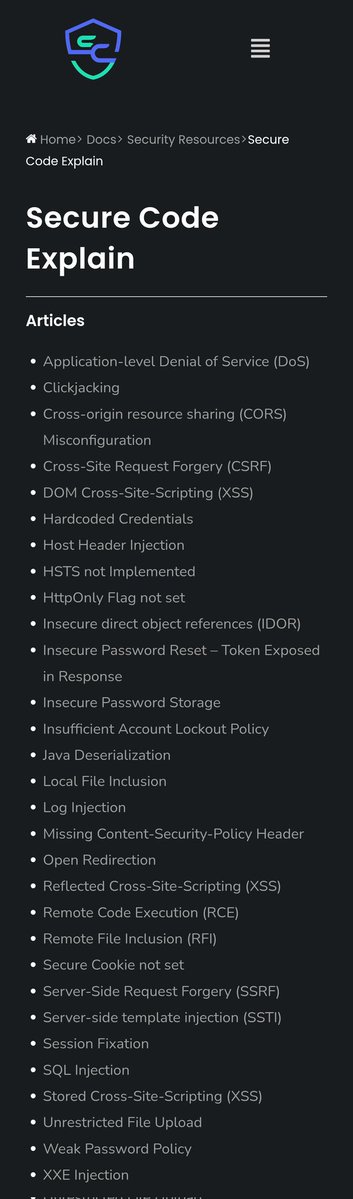
this Secure Code Explain page is a goldmine. Super easy breakdowns of common vulns with vulnerable code: securitycipher.com/docs/security/… #bugbountytips #InfoSec
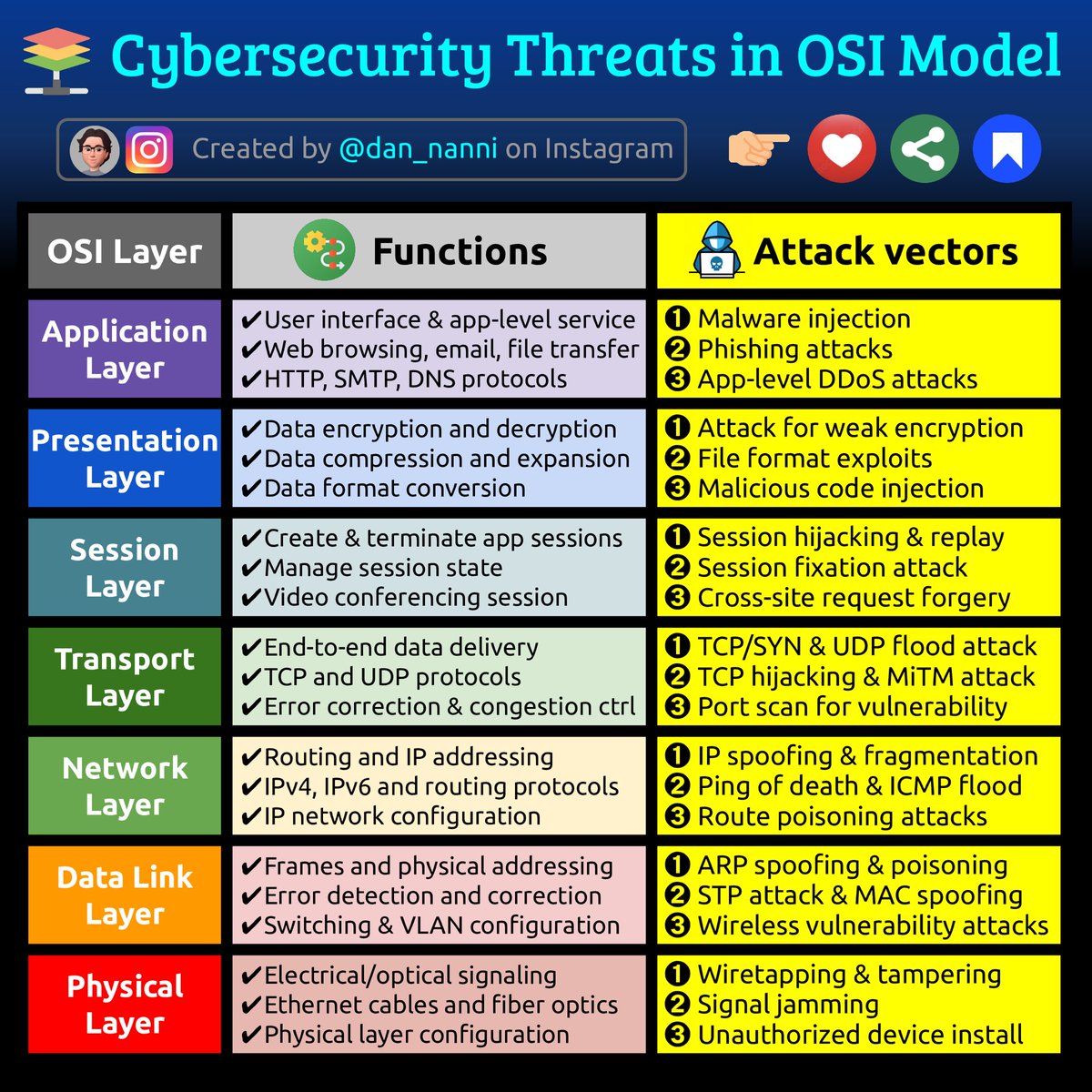
Cybersecurity Threats in OSI Model Credit @xmodulo 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP…
🚨 Just found NEW XSS On Salesforce the “component” allow to bypass the CSP and Firewall. The path appears like that: /apex/CommVisualforce?params=eyJjb21wb25lbnQiOiJjb21tQWxyZWFkeUN1c3RvbWVyIn0= {"component":"commAlreadyCustomer"} #BugBounty #Bugbountytips #infosec

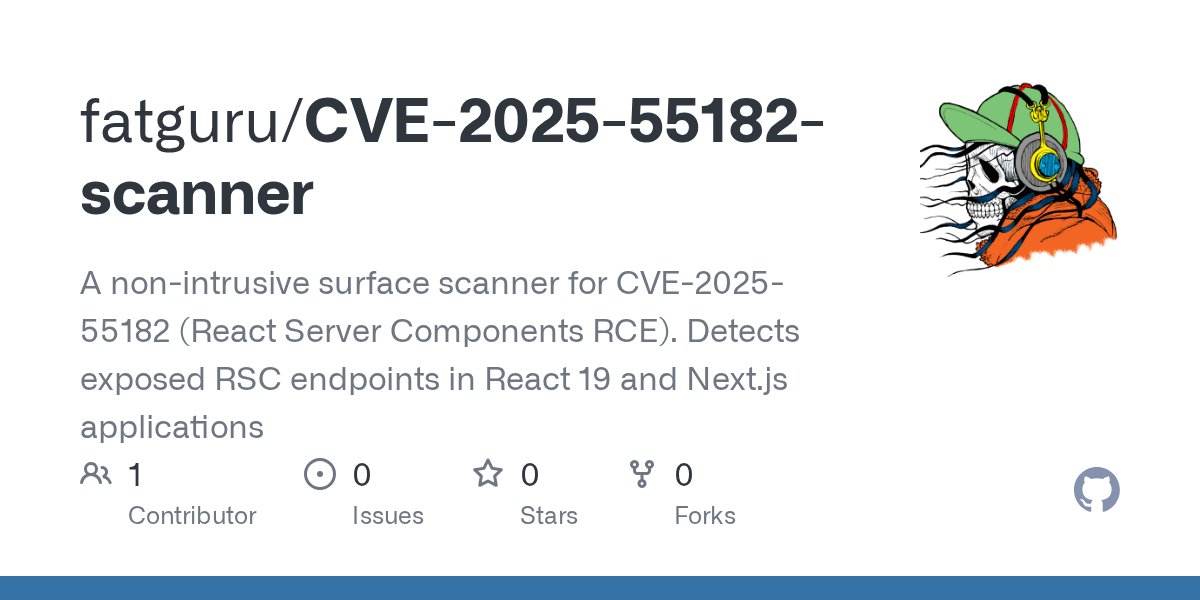
🚨 CVE-2025-55182 #ReactJS/Next.js RCE Surface Scanner Most current PoC exploits fail on production builds due to minified IDs I wrote this Python tool to detect RSC exposure reliably, safe, avoiding these False Negatives👍🏻 👇 github.com/fatguru/CVE-20… #InfoSec #bugbountytips
Pic of the Day 🔥 Telegram: t.me/hackinarticles #infosec #cybersecurity #informationsecurity #pentesting #ITSecurity #OSCP #PenTesting

Four years ago in December 2021, we had Log4shell. Now in December 2025, we have React2shell. It's as widespread and bad, as in unauthenticated and RCE. A coincidence? 😂 #infosec #cybersecurity #bugbounty

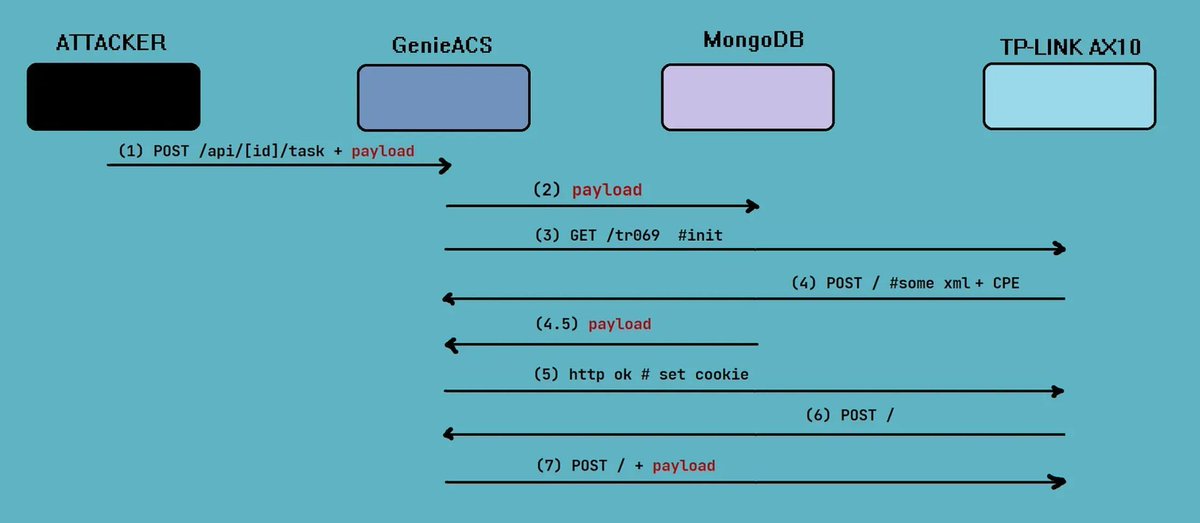
Authenticated remote code execution via the CWMP binary on TP-Link AX10 and AX1500 (CVE-2025–9961) blog.byteray.co.uk/exploiting-zer… #infosec

OT Vulnerability Management Checklist 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting

Here’s what it looks like when someone falls for a phishing email. Stay vigilant, everyone, we’re all in this together! #Cybersecurity #InfoSec #TechHumor

🛡️ We added Android framework vulnerabilities CVE-2025-48572 & CVE-2025-48633 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #Cybersecurity #InfoSec

📢 Stay informed on the latest vulnerabilities with @CISAgov's Vulnerability Bulletin & gain valuable insights into emerging threats. 💡Check out the latest updates: go.dhs.gov/i7H #Cybersecurity #InfoSec #VulnerabilityManagement

Cyber Security Six Pack(TM) - Tip of the Day! #cybersecurity #infosec #multifactorauthentication #TwoFactorAuthentication #cybersecuritysixpack #passkey
Cyber Security Six Pack(TM) - Tip of the Day! #cybersecurity #infosec #multifactorauthentication #TwoFactorAuthentication #cybersecuritysixpack #passkey
The Moonlight Maze (1999) – A still-classified Russian intrusion quietly siphoned gigabytes of U.S. military and NASA data for over a year, becoming one of the first nation-state cyber-espionage campaigns ever uncovered. #Infosec
Deepfakes can copy your face. AI can mimic your voice. Your inbox still falls for “Hello sir I am from IT.” Modern threats are wild — but 90% of breaches still start with someone clicking a bad link. Paranoid? No. Prepared. #CyberAwareness #Infosec #AIThreats
🔐 "Agentic security firm 7AI raises $130 million, increasing its total funding to $166 million. This significant investment matters as it fuels the development of innovative threat detection solutions that ca... securityweek.com/agentic-securi… #Cybersecurity #InfoSec
Chicago Tribune sues Perplexity: ift.tt/TPNYSOZ by TechCrunch #infosec #cybersecurity #technology #news
Ambient and autonomous security for the agentic era : ift.tt/Ul7Db1L by Microsoft Security Blog #infosec #cybersecurity #technology #news
🚨 CRITICAL XXE flaw in Apache Tika core (1.13–3.2.1) risks data leaks & DoS via crafted PDFs. All platforms affected — upgrade to 3.2.2+ now! 🛡️ Details: radar.offseq.com/threat/cve-202… #OffSeq #ApacheTika #Infosec

Interesting short blog post on how electronic passports cryptography works blog.trailofbits.com/2025/10/31/the… Credits Joop van de Pol (@trailofbits) #infosec #embedded


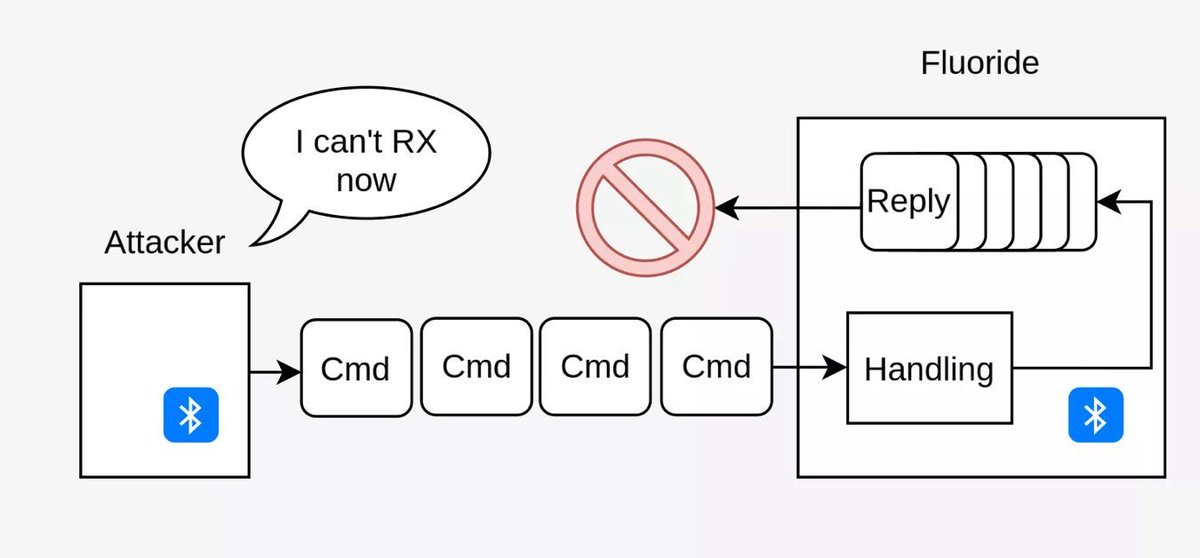
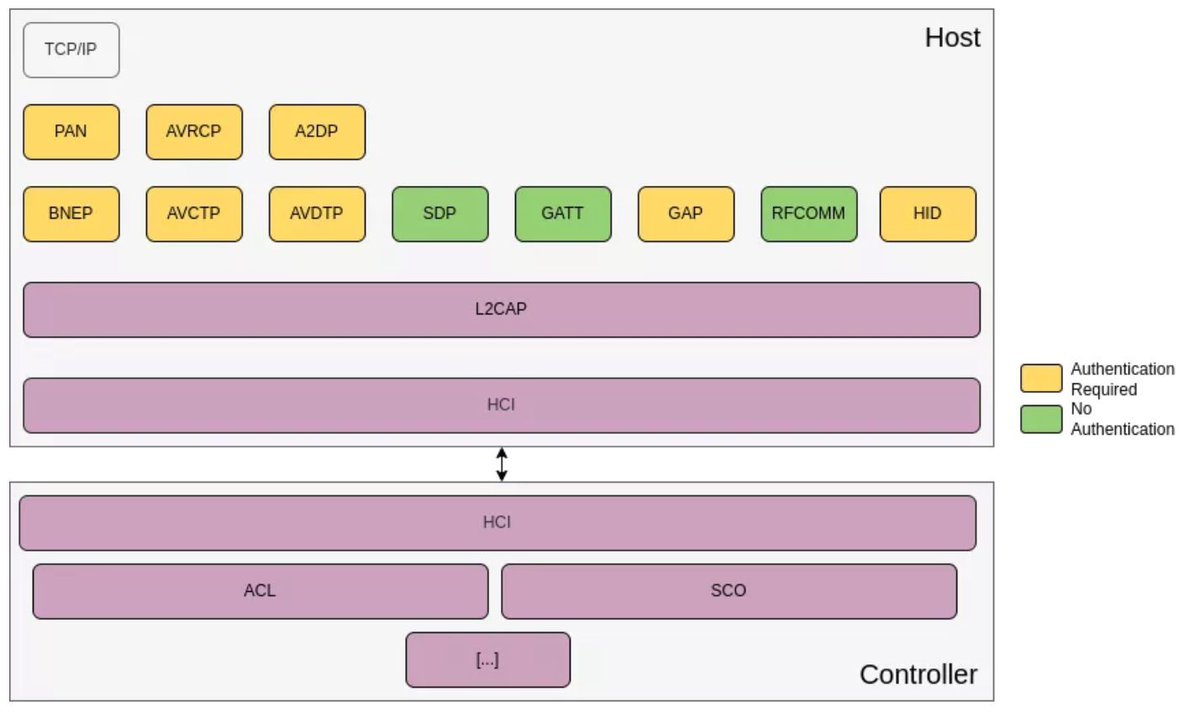
Analysis and exploitation of an integer underflow in the Bluetooth GATT protocol (CVE-2023-40129) synacktiv.com/en/publication… Credits Mehdi Talbi and Etienne Helluy-Lafont (@Synacktiv) #infosec #Android
6 months into cyber security. Still hunting for my first bug bounty. Got 2 informational reports so far. It's tough but I'm not giving up. Leaving this here to remember: keep going. @Bugcrowd #bugbounty #infosec #cybersecurity #nevergiveup

Cybersecurity Threats in OSI Model Credit @xmodulo 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP…

Tools and Techniques for Blue Team / Incident Response Collection of over 65 tools for blue teaming activities 📓 #infosec #cybersec #BugBountytips

Pic of the Day 🔥 Telegram: t.me/hackinarticles #infosec #cybersecurity #informationsecurity #pentesting #ITSecurity #OSCP #PenTesting

CISSP Domain Topics 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting

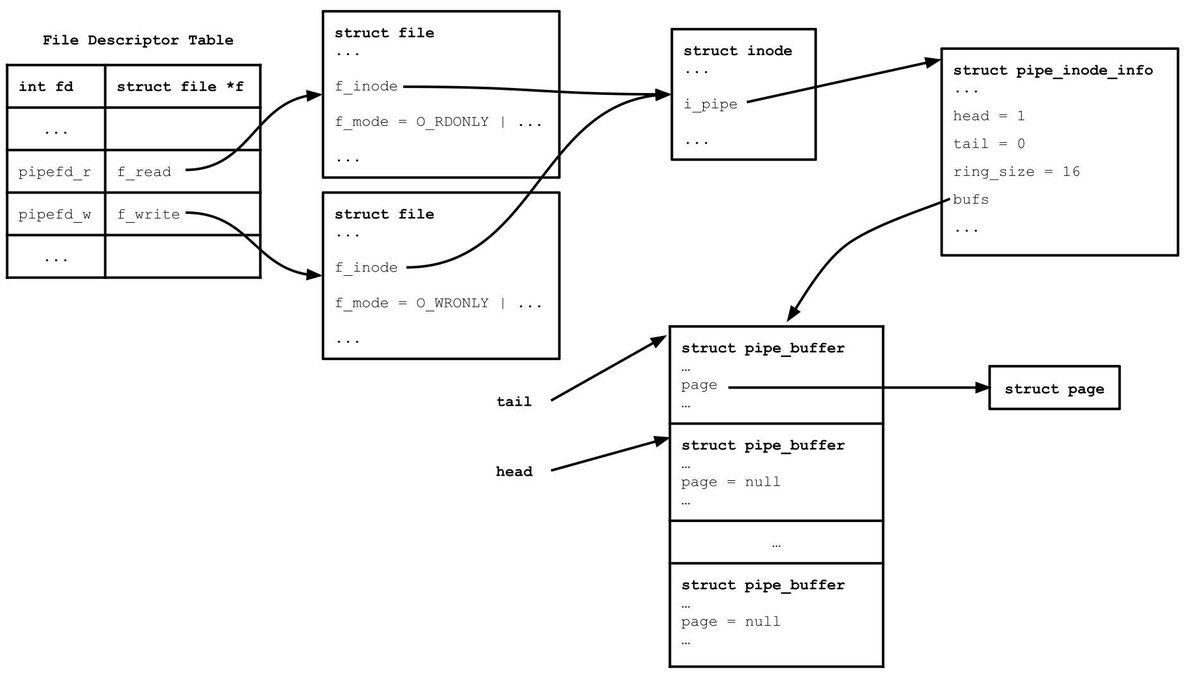
Learning how to exploit DirtyPipe vulnerability in Linux kernel (@0xnull007 and @stdnoerr) 0xnull007.github.io/posts/dirtypip… stdnoerr.blog/blog/DirtyPipe… #infosec #Linux
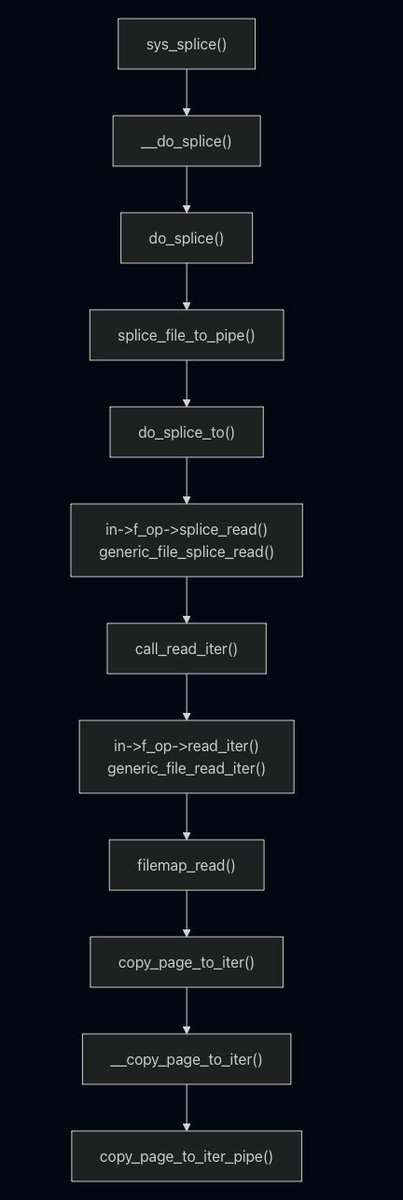
Just earned my Certified Cybersecurity Educator Professional (CCEP) certification! 🎓🔐 Proud of this milestone and excited to keep growing in the cybersecurity field. #CyberSecurity #InfoSec #CareerGrowth #CyberEducation #CCEP #RedTeamLeaders


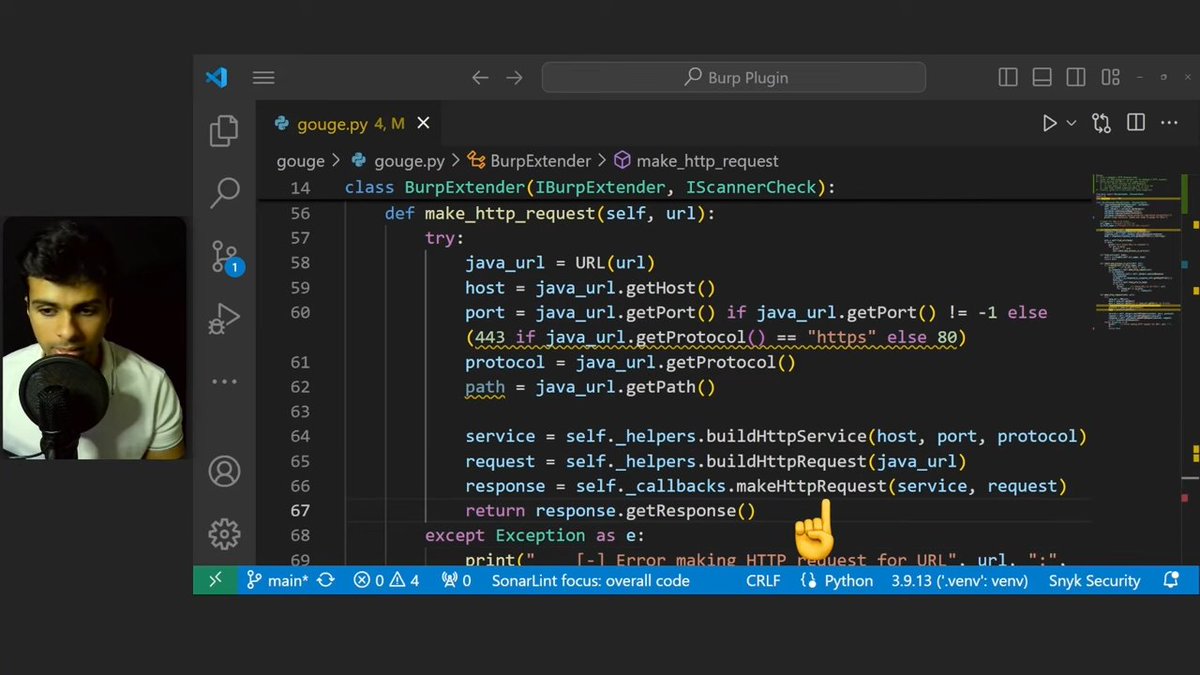
🔨 If you’ve never built a Burp Suite Extension from scratch before, this video is for you. Tutorial: youtube.com/watch?v=9yXQ2U… #infosec
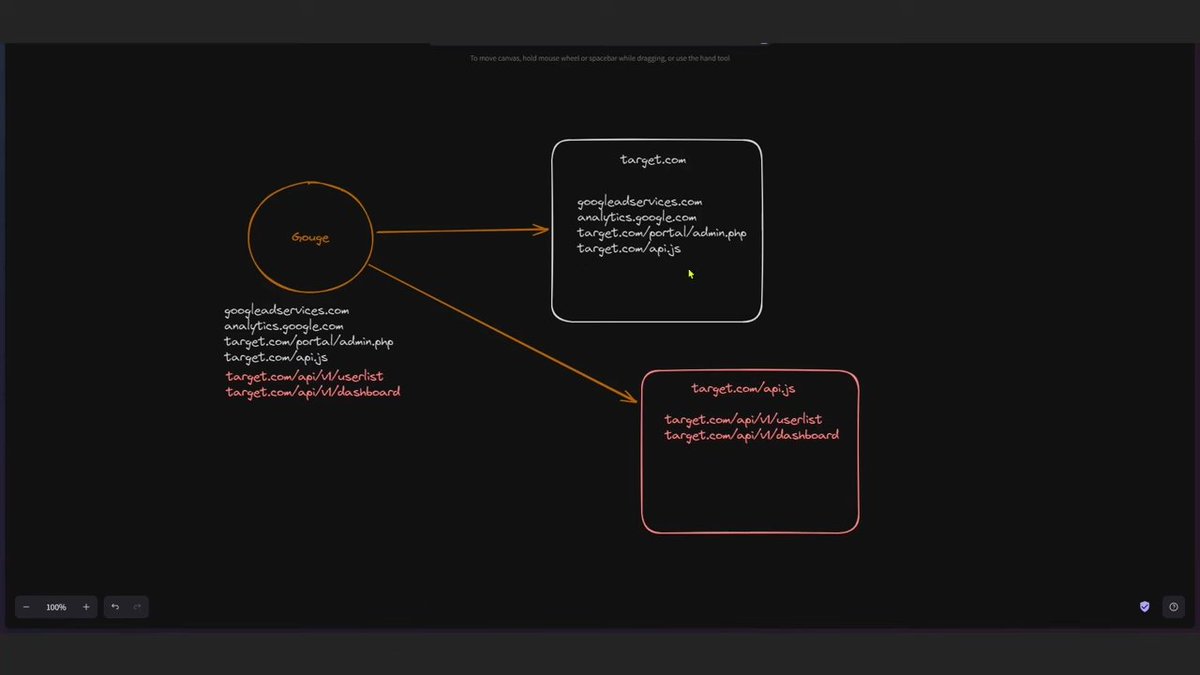
Here’s what it looks like when someone falls for a phishing email. Stay vigilant, everyone, we’re all in this together! #Cybersecurity #InfoSec #TechHumor

OT Vulnerability Management Checklist 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting

Technical breakdown of how Espressif’s flash encryption can be bypassed through key derivation and boot process flaws courk.cc/breaking-flash… #infosec #espressif


Something went wrong.
Something went wrong.
United States Trends
- 1. Lions 57.9K posts
- 2. Gibbs 8,873 posts
- 3. #OnePride 4,729 posts
- 4. Turpin 1,445 posts
- 5. #DALvsDET 2,778 posts
- 6. James Houston 1,764 posts
- 7. Nate Thomas N/A
- 8. #RHOBH 2,414 posts
- 9. #TNFonPrime 1,982 posts
- 10. Pat Spencer 1,682 posts
- 11. #MissVenezuela2025 5,149 posts
- 12. Sixers 4,421 posts
- 13. Brandon Aubrey 2,832 posts
- 14. Matt Campbell 2,805 posts
- 15. TPUSA 94.6K posts
- 16. Kenneth Murray N/A
- 17. Fame 56.6K posts
- 18. Oviedo 6,361 posts
- 19. Jamo 2,800 posts
- 20. Dan Skipper N/A