#infosec 搜索结果
Technical breakdown of how Espressif’s flash encryption can be bypassed through key derivation and boot process flaws courk.cc/breaking-flash… #infosec #espressif


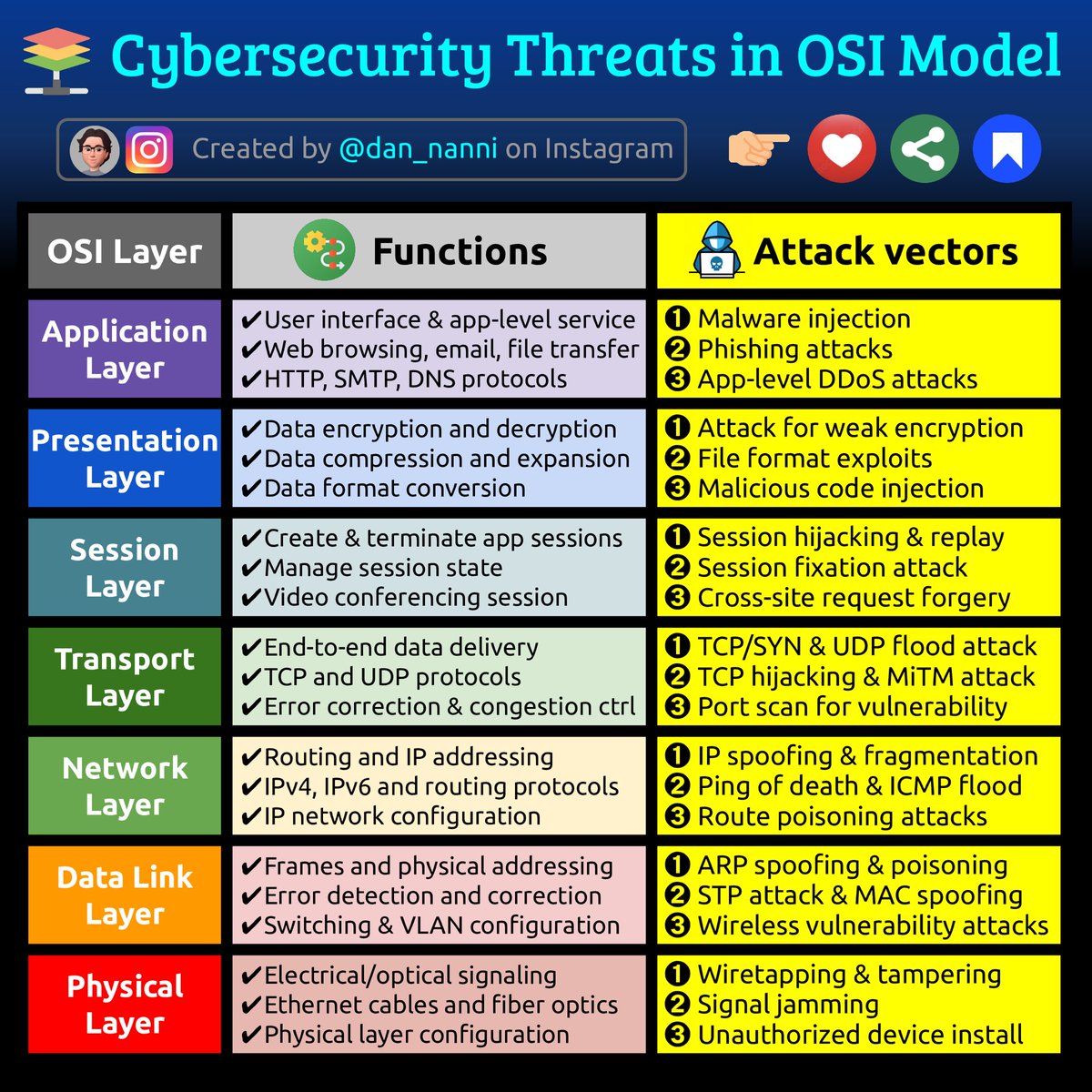
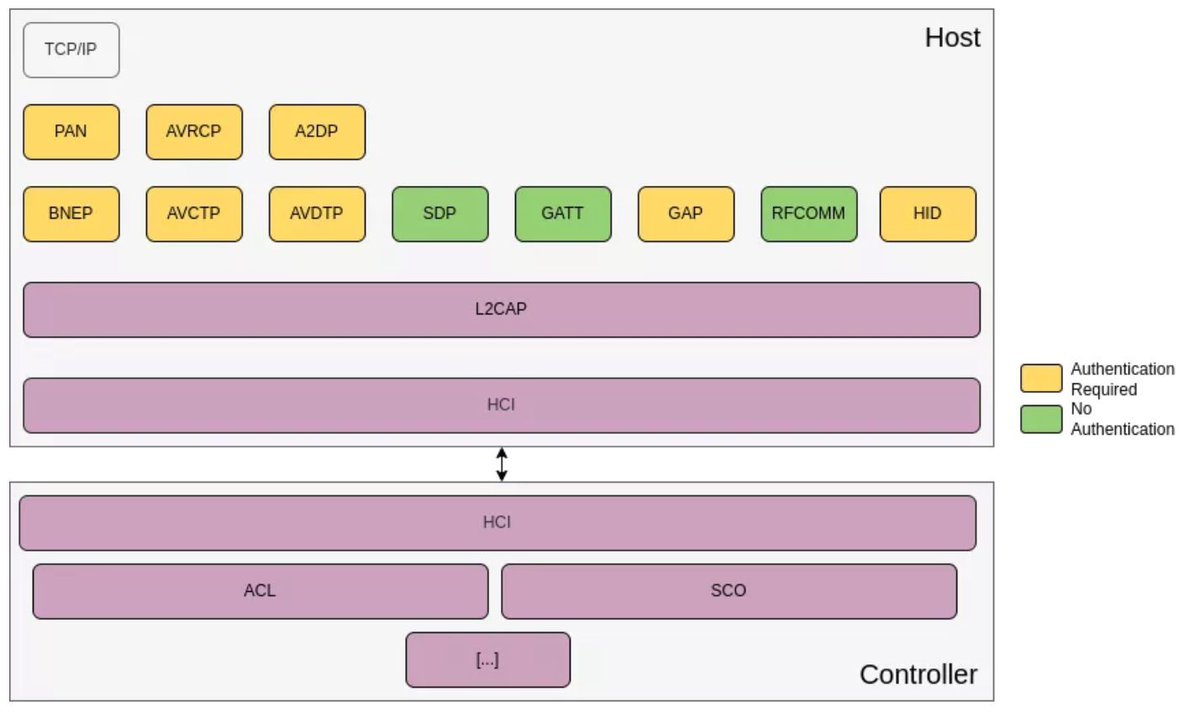
Cybersecurity Threats in OSI Model Credit @xmodulo 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP…
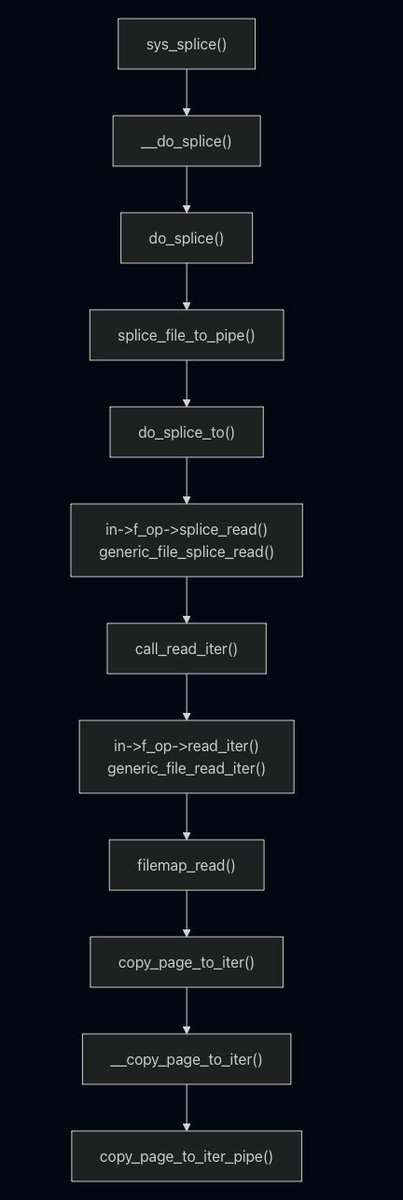
Learning how to exploit DirtyPipe vulnerability in Linux kernel (@0xnull007 and @stdnoerr) 0xnull007.github.io/posts/dirtypip… stdnoerr.blog/blog/DirtyPipe… #infosec #Linux
Offensive Linux Security Tools Credit @xmodulo 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting

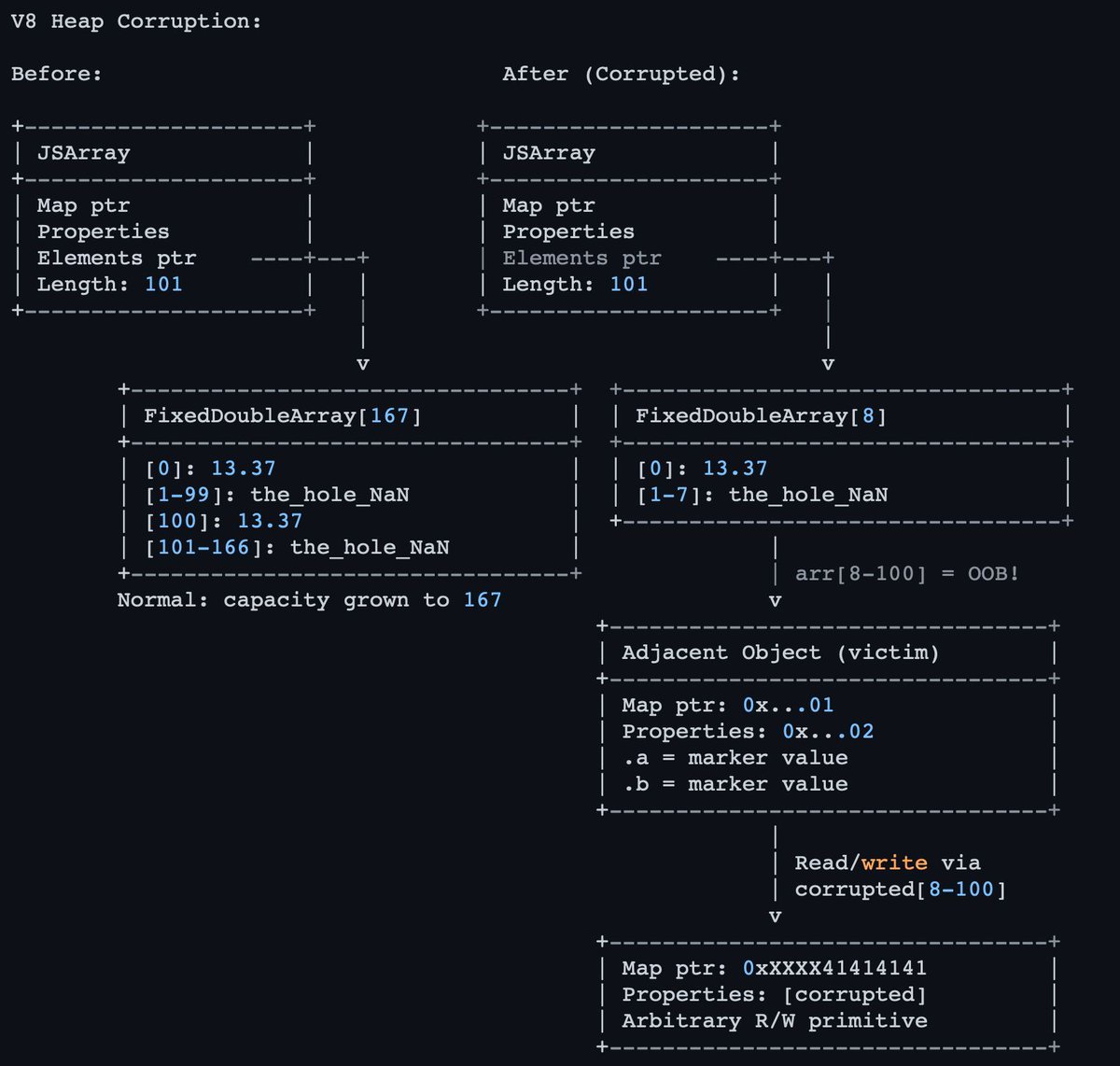
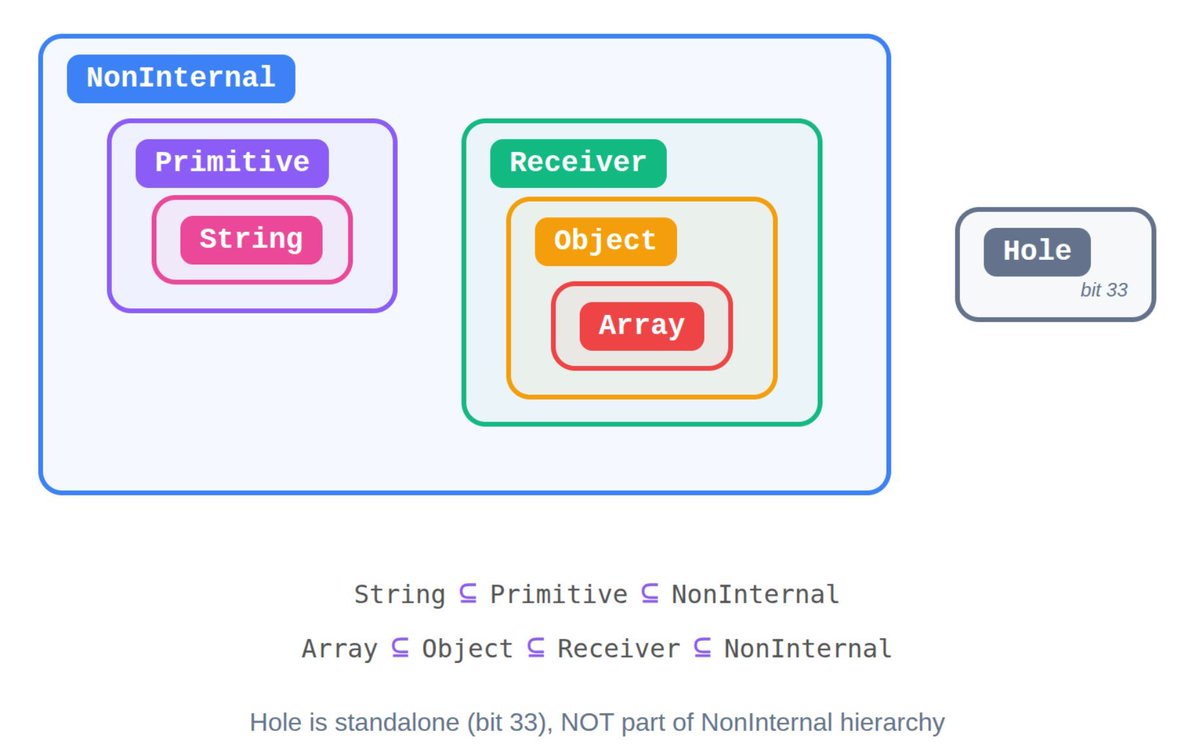
🚨 CVE-2025-55182 #ReactJS/Next.js RCE Surface Scanner Most current PoC exploits fail on production builds due to minified IDs I wrote this Python tool to detect RSC exposure reliably, safe, avoiding these False Negatives👍🏻 👇 github.com/fatguru/CVE-20… #InfoSec #bugbountytips
Analysis and exploitation of a Use-After-Free vulnerability in the Linux network packet schedule (CVE-2025-38001) syst3mfailure.io/rbtree-family-… #infosec #Linux

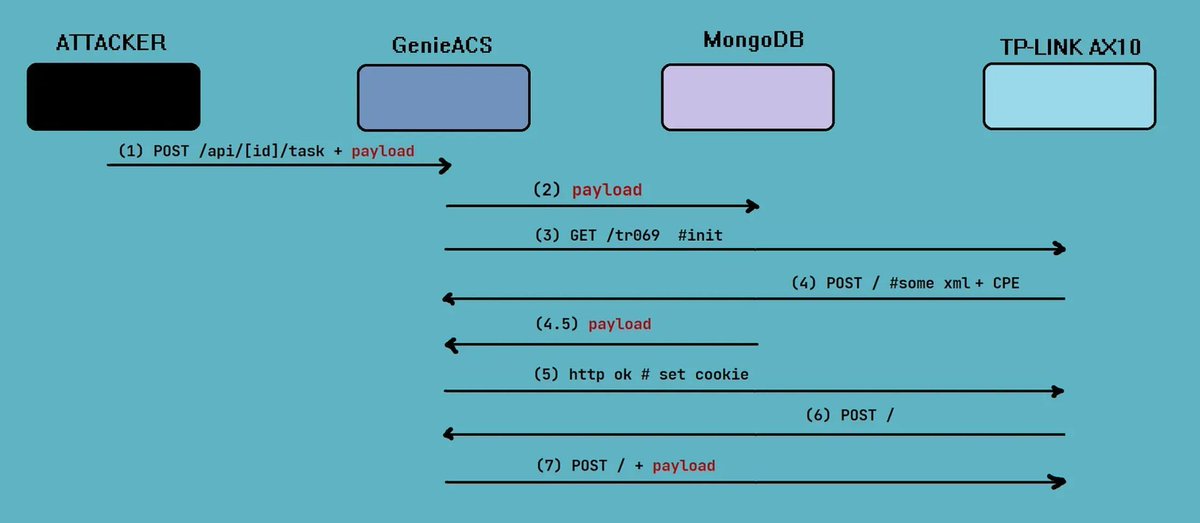
Authenticated remote code execution via the CWMP binary on TP-Link AX10 and AX1500 (CVE-2025–9961) blog.byteray.co.uk/exploiting-zer… #infosec

🛡️ We added Android framework vulnerabilities CVE-2025-48572 & CVE-2025-48633 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #Cybersecurity #InfoSec

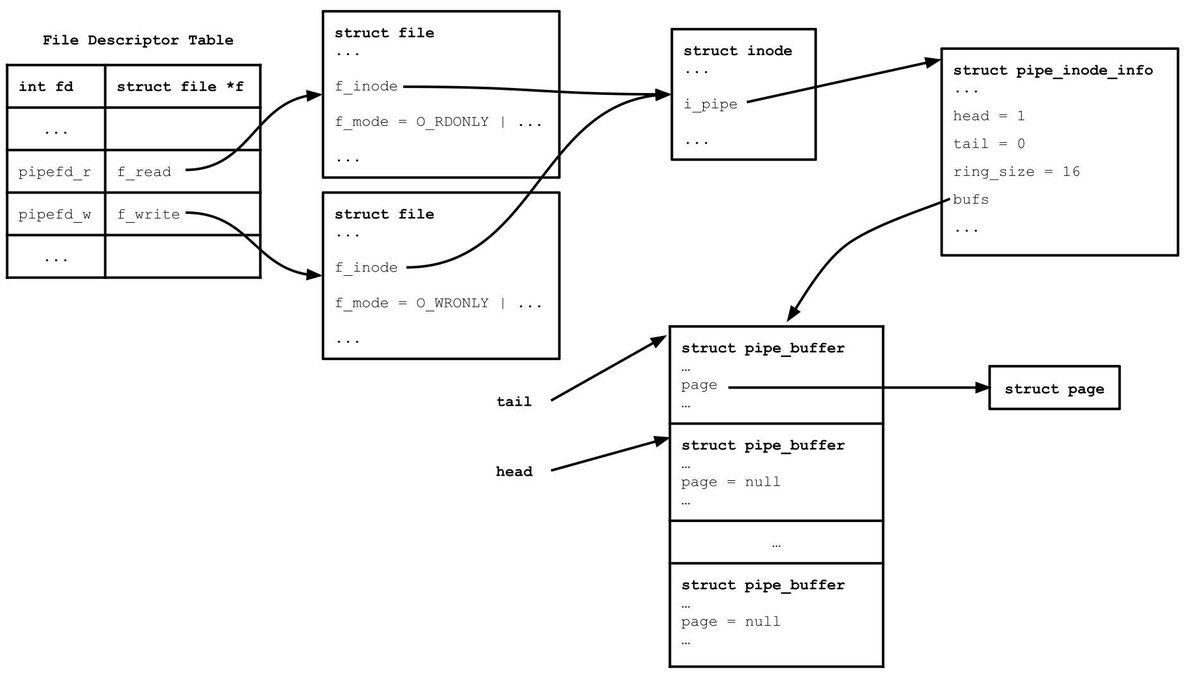
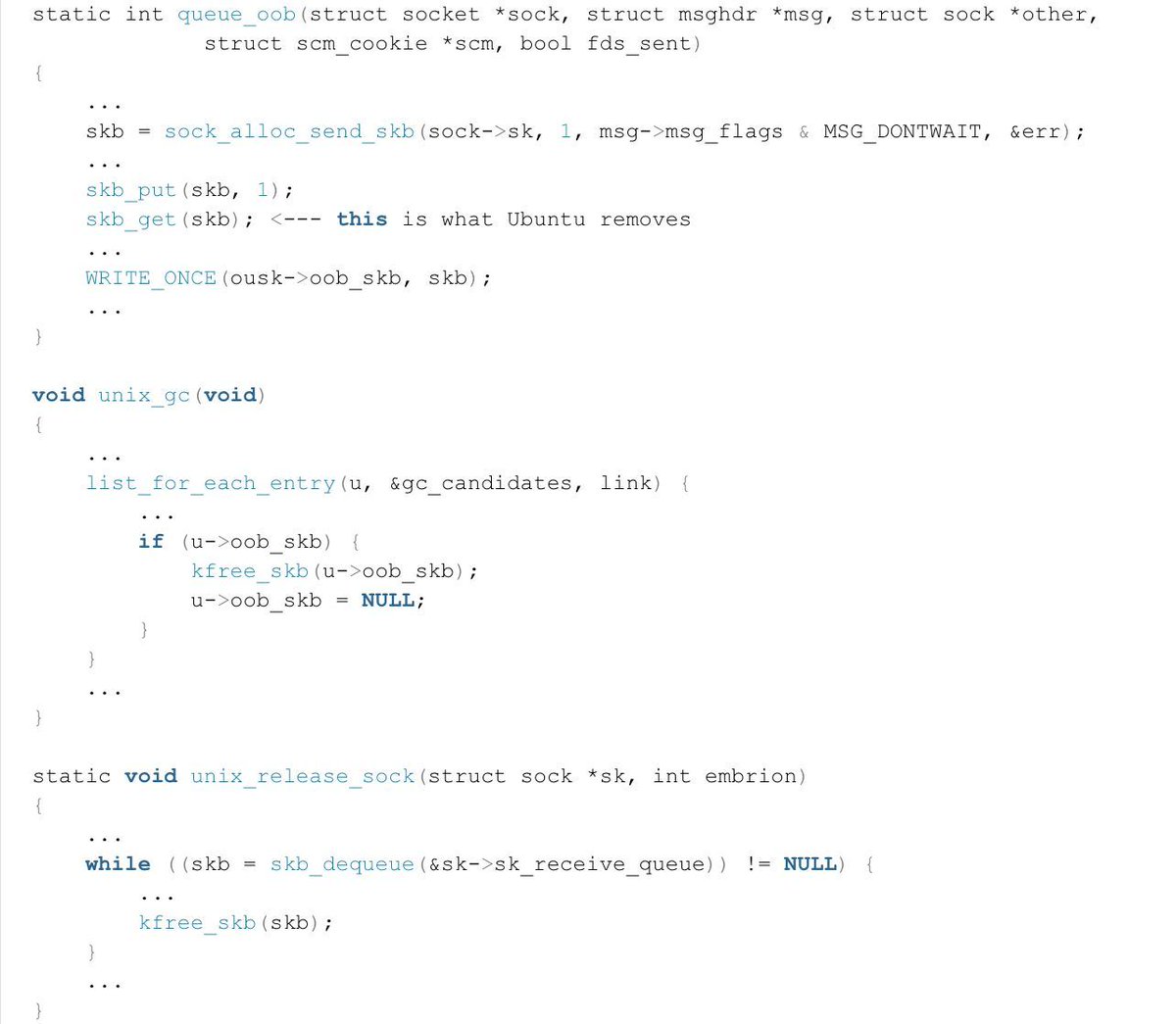
LPE by exploiting a refcount imbalance issue in the af_unix subsystem of Ubuntu’s kernel. ssd-disclosure.com/lpe-via-refcou… #infosec #Linux
6 months into cyber security. Still hunting for my first bug bounty. Got 2 informational reports so far. It's tough but I'm not giving up. Leaving this here to remember: keep going. @Bugcrowd #bugbounty #infosec #cybersecurity #nevergiveup
Testing and Scanning template injection vulnerabilities 📓 - github.com/Hackmanit/TInjA #infosec #cybersec #bugbountytips
🚨 Just found NEW XSS On Salesforce the “component” allow to bypass the CSP and Firewall. The path appears like that: /apex/CommVisualforce?params=eyJjb21wb25lbnQiOiJjb21tQWxyZWFkeUN1c3RvbWVyIn0= {"component":"commAlreadyCustomer"} #BugBounty #Bugbountytips #infosec

this Secure Code Explain page is a goldmine. Super easy breakdowns of common vulns with vulnerable code: securitycipher.com/docs/security/… #bugbountytips #InfoSec
Analysis and exploitation of an integer underflow in the Bluetooth GATT protocol (CVE-2023-40129) synacktiv.com/en/publication… Credits Mehdi Talbi and Etienne Helluy-Lafont (@Synacktiv) #infosec #Android
Here’s what it looks like when someone falls for a phishing email. Stay vigilant, everyone, we’re all in this together! #Cybersecurity #InfoSec #TechHumor

How To Get Your First Job In #Cybersecurity: a blog post of all the steps you need to transition into #InfoSec! twp.ai/ImsxdP

Here's how @nmatt0 used his AI hackbot (github.com/BrownFineSecur…) to bypass authentication in an IP camera and control it 🔥 It utilises Claude skills for embedded and IoT security testing. #cybersecurity #infosec #iotnbo
Hackers turned the Marquis breach into a bank heist blockbuster—over 74 US institutions caught off guard! Time to lock down your accounts like a vault. What's your best defense? 😏🔒 #CyberSec #InfoSec #DataBreach bleepingcomputer.com/news/security/…
"Comprehensive Crisis Management Plans: Develop and maintain robust crisis management plans that are regularly updated and tested through tabletop exercises and simulations." lttr.ai/AluGd #Security #Infosec #Compliance
A massive breach of South Korea online retailer Coupang reportedly compromised 33.7 million customer accounts, potentially affecting 65% of the country’s population of 51.7 million. #cybersecurity #infosec #ITsecurity #CISO bit.ly/3XZxhyD
An update that solves one vulnerability and has one errata is now available. openSUSE Security Update: Security update for icinga2 ____________________________________________... #OpenSUSE #Linux #infosec #opensource #linuxsecurity tinyurl.com/26swmra6

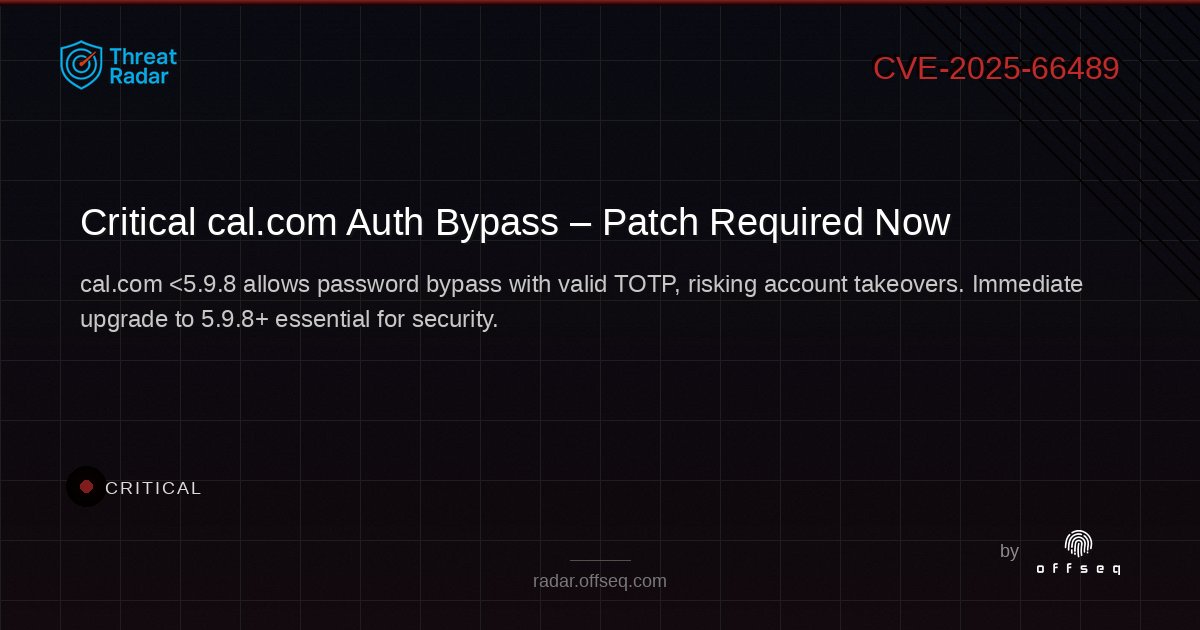
🚨 CRITICAL flaw in cal.com (<5.9.8): attackers can bypass passwords with valid TOTP, risking account takeovers! Patch ASAP to protect your data. Details: radar.offseq.com/threat/cve-202… #OffSeq #calcom #infosec
Maximum-severity Vulnerability Threatens 6% Of All Websites - mwyr.es/dju3EE5J #arstechnica #infosec
ASX Outage Caused By Security Software Upgrade - mwyr.es/i0y8vKs #itnews #infosec
Critical King Addons Vulnerability Exploited To Hack WordPress Sites - mwyr.es/c89wD2S #securityweek #infosec
Microsoft Silently Mitigated Exploited LNK Vulnerability - mwyr.es/I6bKef6G #securityweek #infosec
Chrome 143 Patches High-Severity Vulnerabilities - mwyr.es/ZUF13Fg7 #securityweek #infosec
Australian Telco Fined $2.5m Over Breaches Of Anti-scam Laws - mwyr.es/lGXjaXqi #cyberdaily #infosec
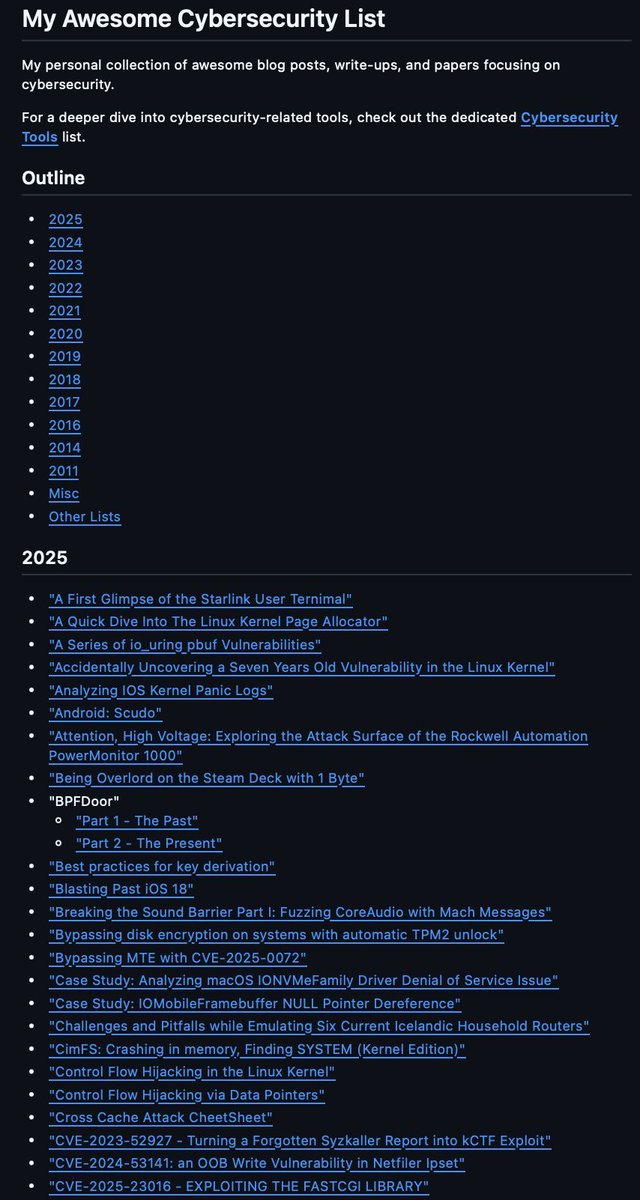
Collection of blog posts, write-ups, papers and tools related to cybersecurity, reverse engineering and exploitation github.com/0xor0ne/awesom… #cybersecurity #infosec
Technical breakdown of how Espressif’s flash encryption can be bypassed through key derivation and boot process flaws courk.cc/breaking-flash… #infosec #espressif


Cybersecurity Threats in OSI Model Credit @xmodulo 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP…

Learning how to exploit DirtyPipe vulnerability in Linux kernel (@0xnull007 and @stdnoerr) 0xnull007.github.io/posts/dirtypip… stdnoerr.blog/blog/DirtyPipe… #infosec #Linux


6 months into cyber security. Still hunting for my first bug bounty. Got 2 informational reports so far. It's tough but I'm not giving up. Leaving this here to remember: keep going. @Bugcrowd #bugbounty #infosec #cybersecurity #nevergiveup

How To Get Your First Job In #Cybersecurity: a blog post of all the steps you need to transition into #InfoSec! twp.ai/ImsxdP

"Troll Fortifications and Report Notifications" Why its important to keep reporting abusive accounts. tacticalstrikemedia.com/post/troll-for… #NAFOworks #infosec #InformationWarfare

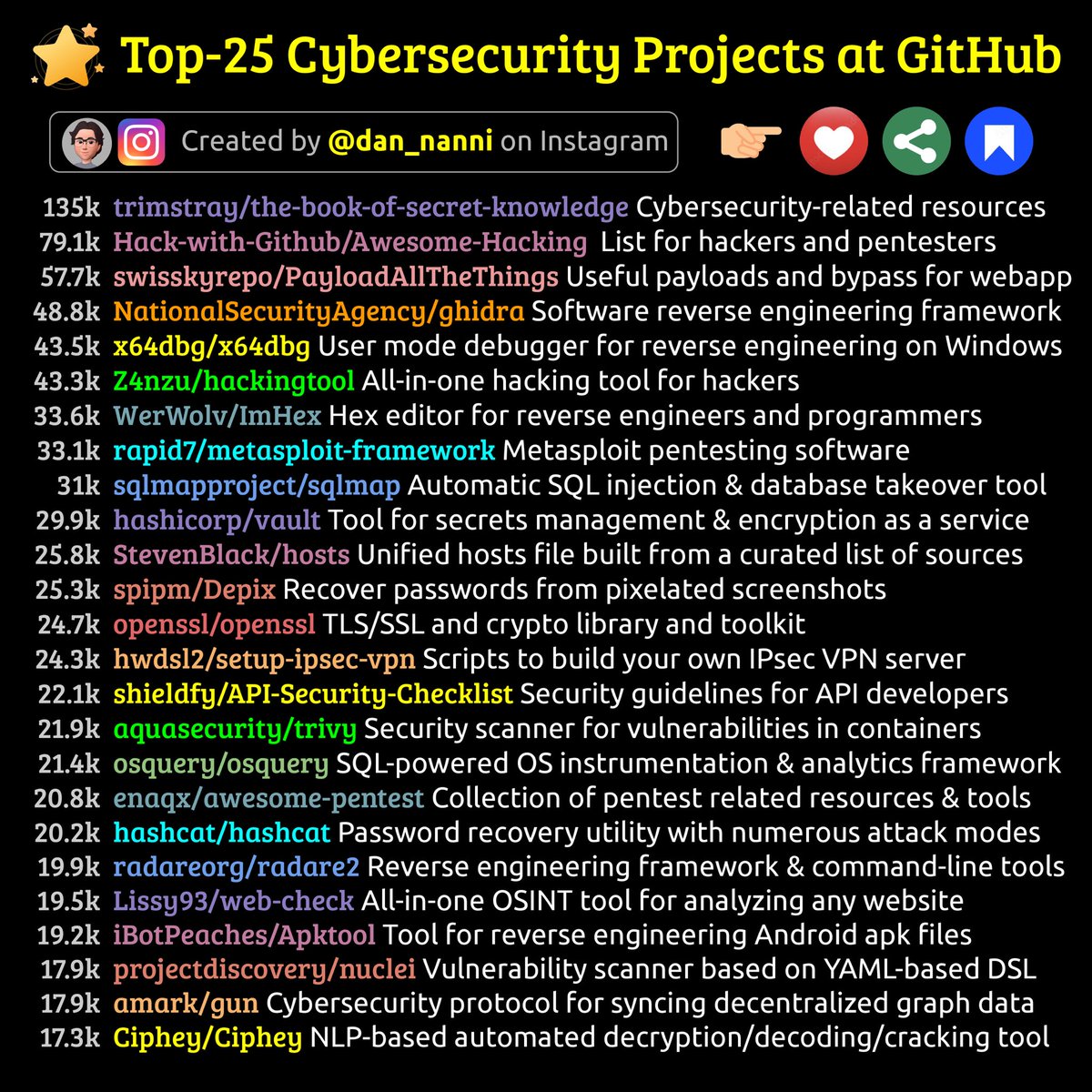
Top-25 Github Cybersec Projects 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting
Testing and Scanning template injection vulnerabilities 📓 - github.com/Hackmanit/TInjA #infosec #cybersec #bugbountytips

Analysis and exploitation of an integer underflow in the Bluetooth GATT protocol (CVE-2023-40129) synacktiv.com/en/publication… Credits Mehdi Talbi and Etienne Helluy-Lafont (@Synacktiv) #infosec #Android


Here’s what it looks like when someone falls for a phishing email. Stay vigilant, everyone, we’re all in this together! #Cybersecurity #InfoSec #TechHumor

Exploiting LPE vulnerabilities in NVIDIA Linux Open GPU Kernel Modules by Robin Bastide (@quarkslab) blog.quarkslab.com/nvidia_gpu_ker… #infosec
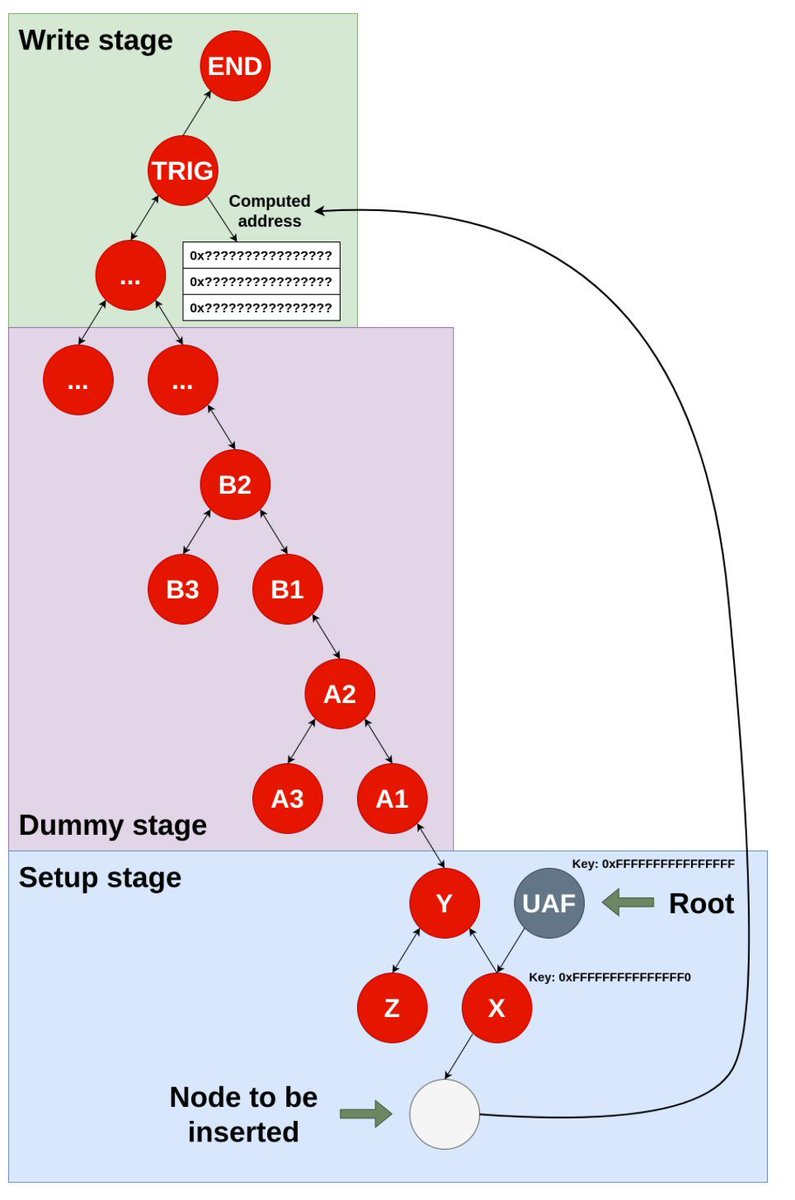
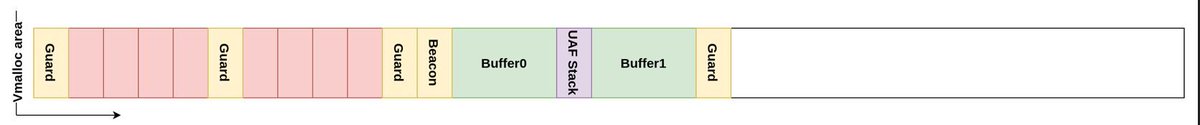
Pic of the Day 🔥 Telegram: t.me/hackinarticles #infosec #cybersecurity #informationsecurity #pentesting #ITSecurity #OSCP #PenTesting

Great deep-dive on AMD Zen microcode hacking and a signature-validation flaw bughunters.google.com/blog/542484235… #infosec
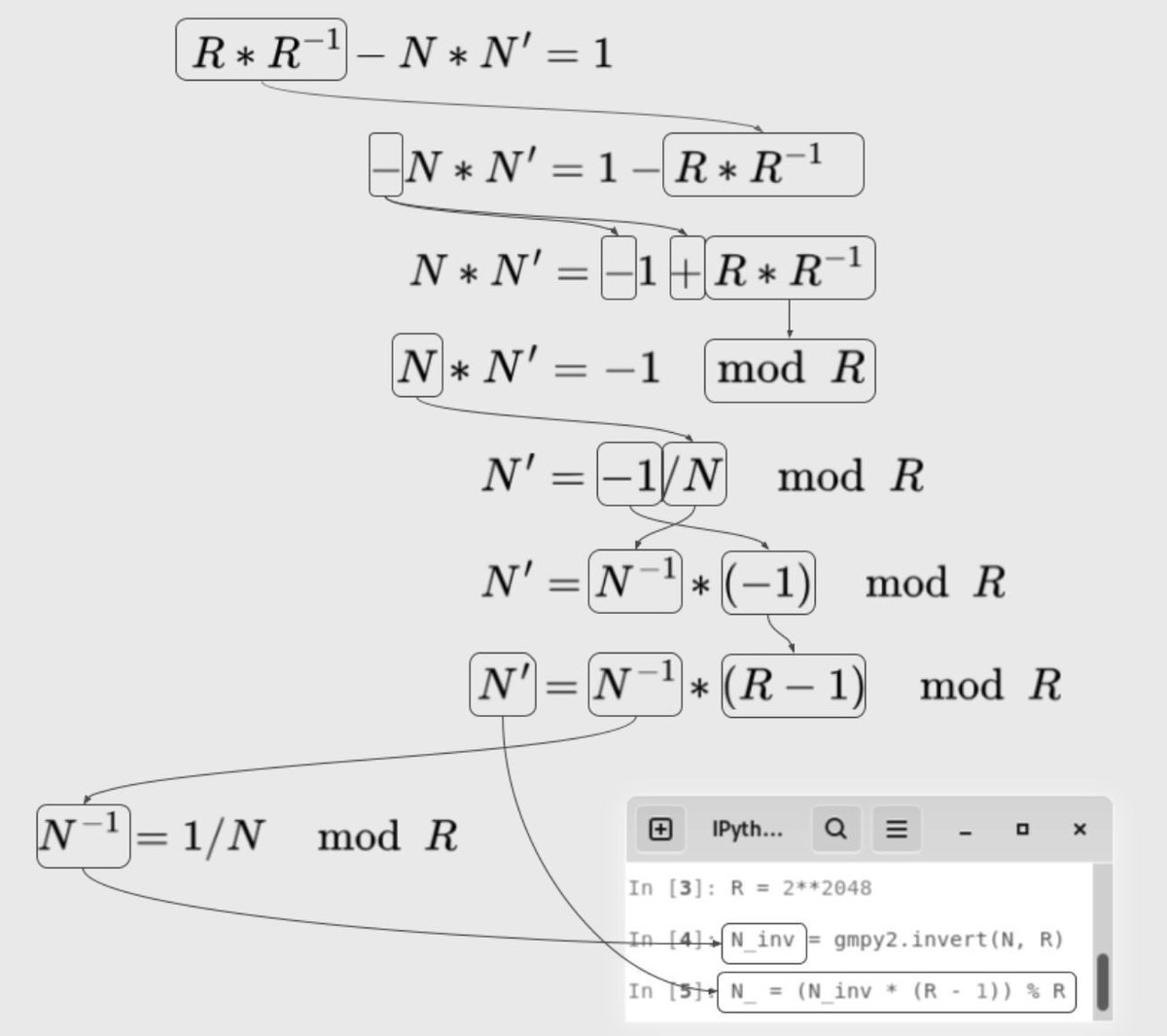
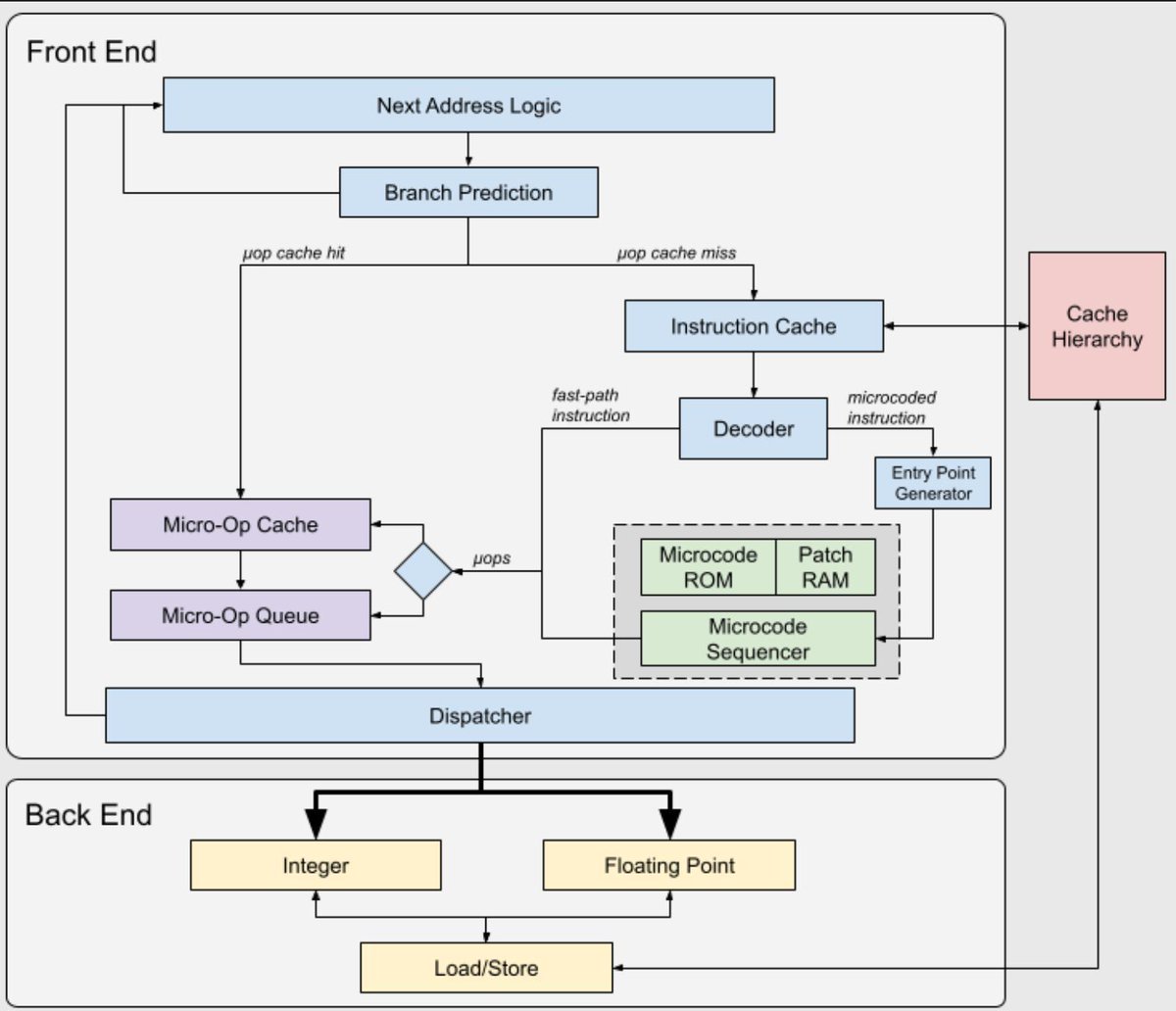
Tools and Techniques for Blue Team / Incident Response Collection of over 65 tools for blue teaming activities 📓 #infosec #cybersec #BugBountytips

Windows ARM64 Pointer Authentication (PAC) internals preludesecurity.com/blog/windows-a… Credits @preludeorg #infosec

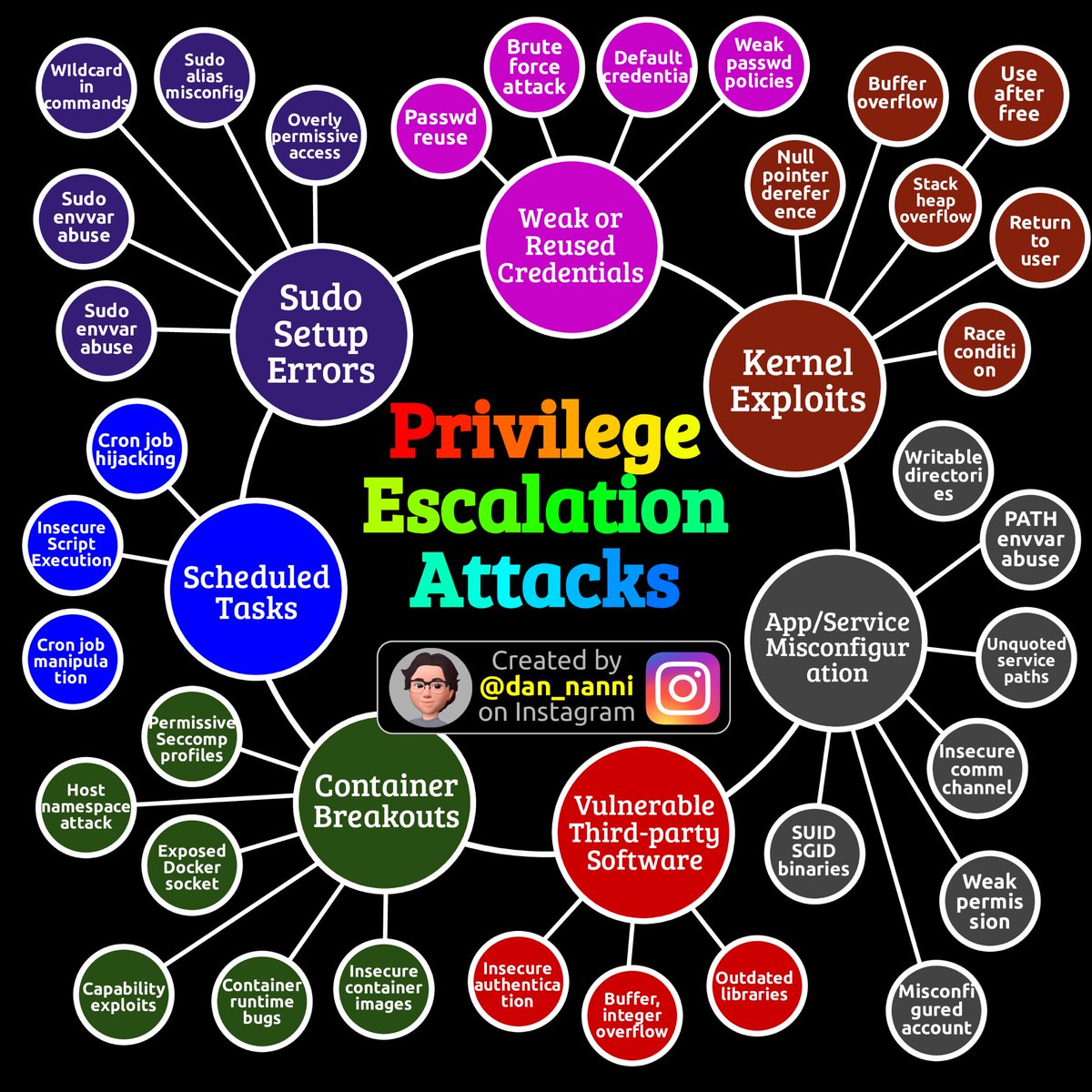
Privilege Escalation Attacks Credit @xmodulo 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting
Something went wrong.
Something went wrong.
United States Trends
- 1. #AEWDynamite 13.2K posts
- 2. Giannis 71.5K posts
- 3. #Survivor49 1,940 posts
- 4. #iubb 1,023 posts
- 5. Jamal Murray 1,793 posts
- 6. #TheChallenge41 1,074 posts
- 7. Kevin Knight 1,422 posts
- 8. Dark Order 1,296 posts
- 9. Achilles 4,839 posts
- 10. #SistasOnBET 1,074 posts
- 11. Spotify 1.92M posts
- 12. Bucks 44.8K posts
- 13. Steve Cropper 2,744 posts
- 14. Spurs 28.6K posts
- 15. Yeremi N/A
- 16. Lonzo N/A
- 17. Mikel 34K posts
- 18. LUKE KORNET N/A
- 19. Rizo N/A
- 20. Brazile N/A