#webapplicationsecurity результаты поиска
Web Application Penetration Testing Checklist👾 Credits: @e11i0t_4lders0n 🔗alike-lantern-72d.notion.site/Web-Applicatio…

🚨 Big news for AppSec teams! The new OWASP Top 10 2025 has dropped — and it’s a game-changer for anyone building or securing web apps. 🔐 Guess which risk continues to dominate? It’s Broken Access Control (BAC), again. According to OWASP, when authorization fails, serious harm…

Este repositorio es una joya. Te da todos los pasos e instrucciones para proteger y asegurar tu servidor Linux. Perfecto por si tienes un servidor propio o VPS: github.com/imthenachoman/…

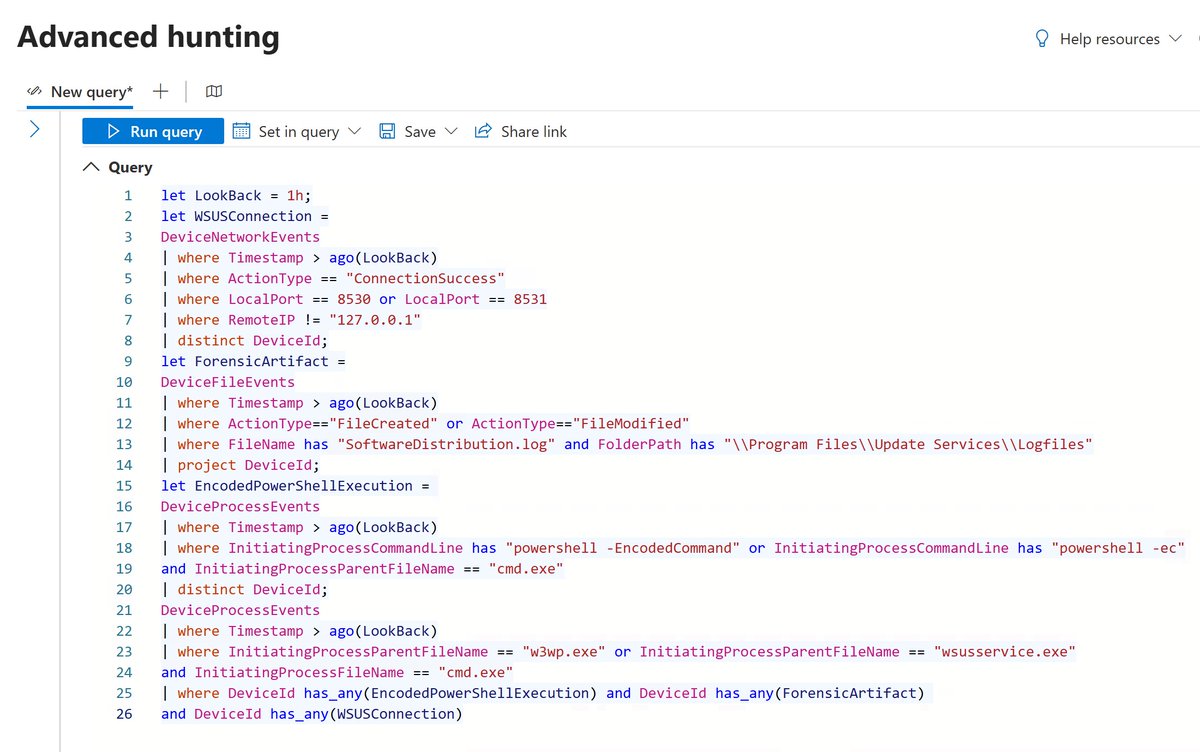
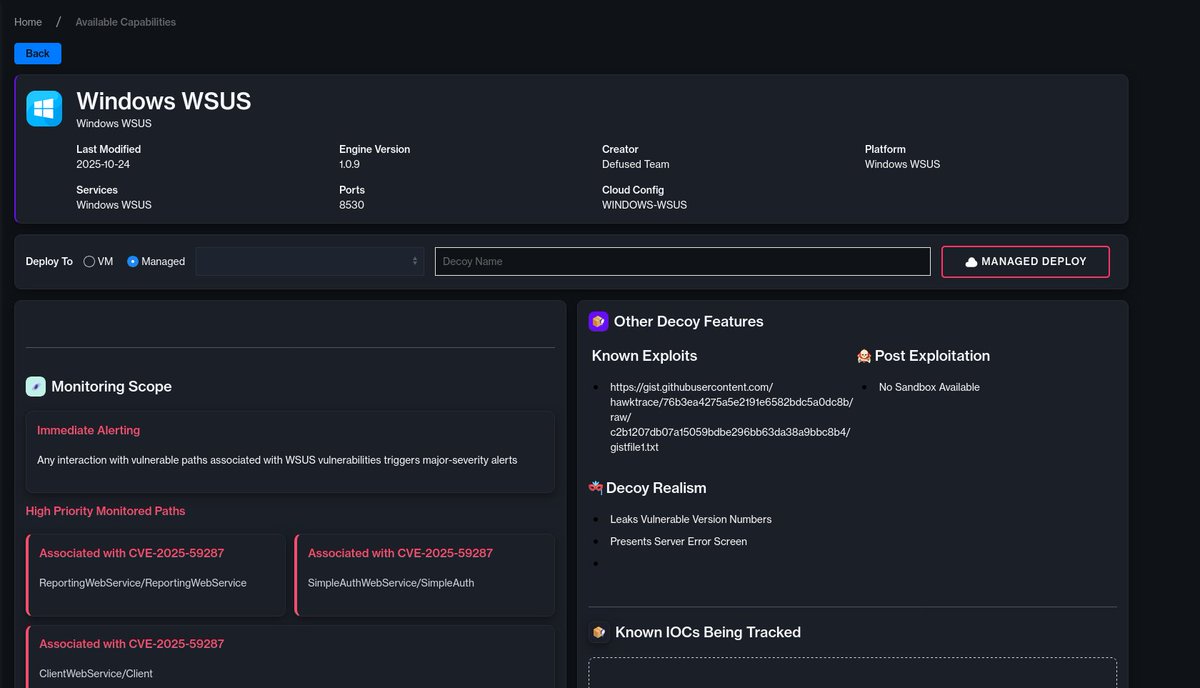
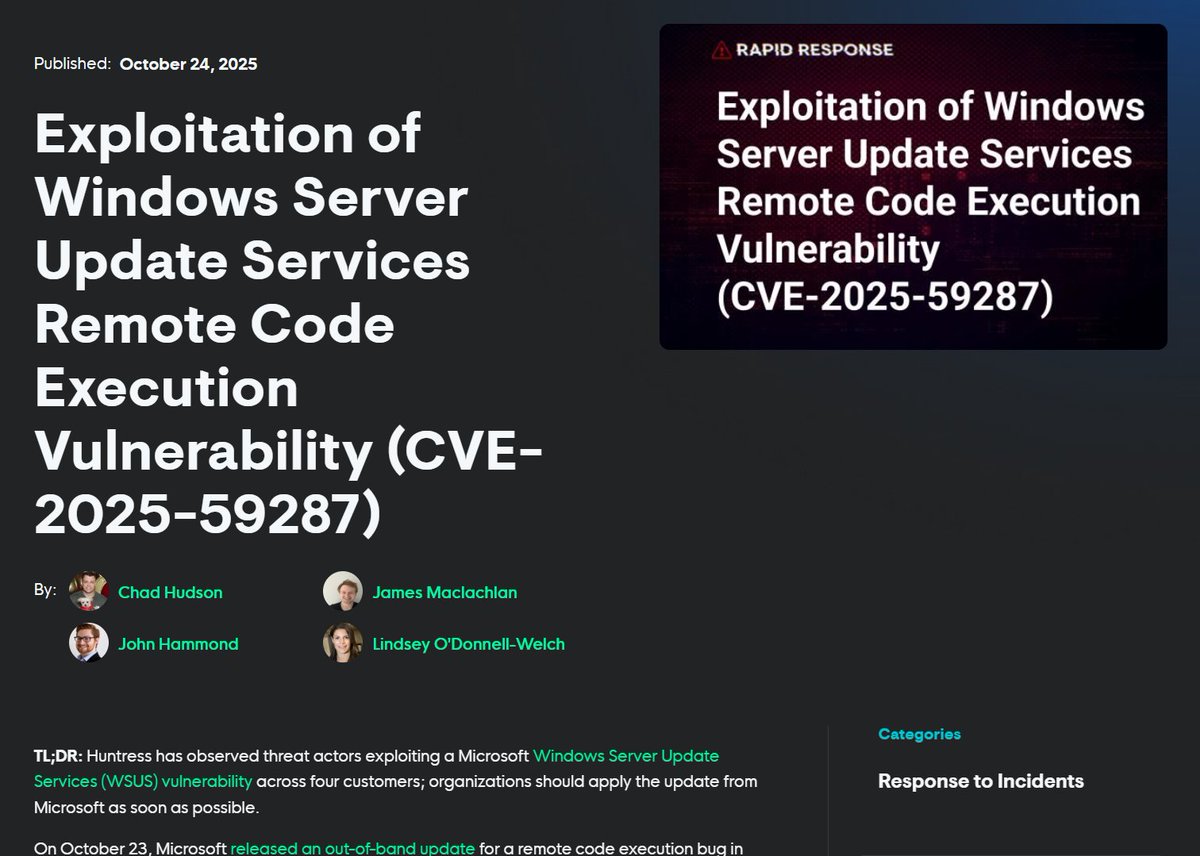
🔥 𝗛𝗶𝗴𝗵-𝗙𝗶𝗱𝗲𝗹𝗶𝘁𝘆 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗳𝗼𝗿 𝗪𝗦𝗨𝗦 𝗥𝗲𝗺𝗼𝘁𝗲 𝗖𝗼𝗱𝗲 𝗘𝘅𝗲𝗰𝘂𝘁𝗶𝗼𝗻 A critical deserialization flaw (CVSS 9.8) in Windows Server Update Services (WSUS) — CVE-2025-59287 — enables unauthenticated remote code execution over the network. This…
Top 3 Mistakes That Cost Web3 $3.1B in 2025 2025 proved that the biggest threats to Web3 weren’t always new; they were repeated. 🧵 A quick breakdown from CredShields’ State of Web3 Security 2025 Report:

OWASP TOP 10 2025 UPDATE! Open Web Application Security Project has released a new update for applications security vulnerabilities It has 2 new categories, 1 merger, 3 dropped in rank and there are 248 CWEs spread across the listed vulnerabilities. What are your thoughts?

Securing Your ASP .NET Core App with Authorization Fallback Policy by Bart Wullems bartwullems.blogspot.com/2025/10/securi… #aspnetcore

Critical RCE Vulnerability in Windows Server WSUS 🚨 The vulnerability CVE-2025-59287 has just been added to CISA Known Exploited Vulnerabilities. Attacks are underway and a POC is available. We have added an WSUS honeypot for Defused Free users for a limited time - take…
web app security auditing toolkit for testing and intercepting requests

Good Morning Listen 👂 Most hacks in Web3 happen on bridges. @OneAnalog eliminates the need for those fragile connectors with native interoperability that’s verifiable and secure at the protocol level.

Smart Audit now includes embeddable proof-of-audit badges. Scan your contract and embed your security score directly on your website. The badge links to your full audit report - showing vulnerabilities found, severity levels, and remediation solutions. Auto-updates every time…
There's a special type of firewall built just for websites called a web application firewall, or WAF. And in this guide, Manish goes through some of the best options to help you choose one. You'll learn about their features, cost, pros and cons, and how they can help you…
The field of Cybersecurity is growing - and no wonder with the ever-present threat of attacks these days. So if you want to show potential employers you know your stuff, there are some certifications you should consider. Here, Manish shares his top cert picks and why they're…

hey hi hello we've been seeing summa dat WSUS sussy baka CVE-2025-59287 remote code execution exploitation windows servers with WSUS ports 8530 & 8531 exposed ( -- why?) getting point-and-shoot popped from a POC already public huntress.com/blog/exploitat… prolly limited ITW…
⚠️ You copy an address, check the first and last characters — everything looks right. You hit send → Your crypto disappears. That’s address poisoning: one of the most effective and underestimated phishing methods in Web3. 🧵 Here’s how it works and how to avoid it.

building apps is easy; securing them is the hard part. > this is the field guide for devs who want to defend against real-world attacks. > a must-read if you ship code to the web

CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
Finding web application vulnerabilities with Burp AI and it's also fun? Yes, please! Watch the full video here ⬇️ bit.ly/4nDeELk
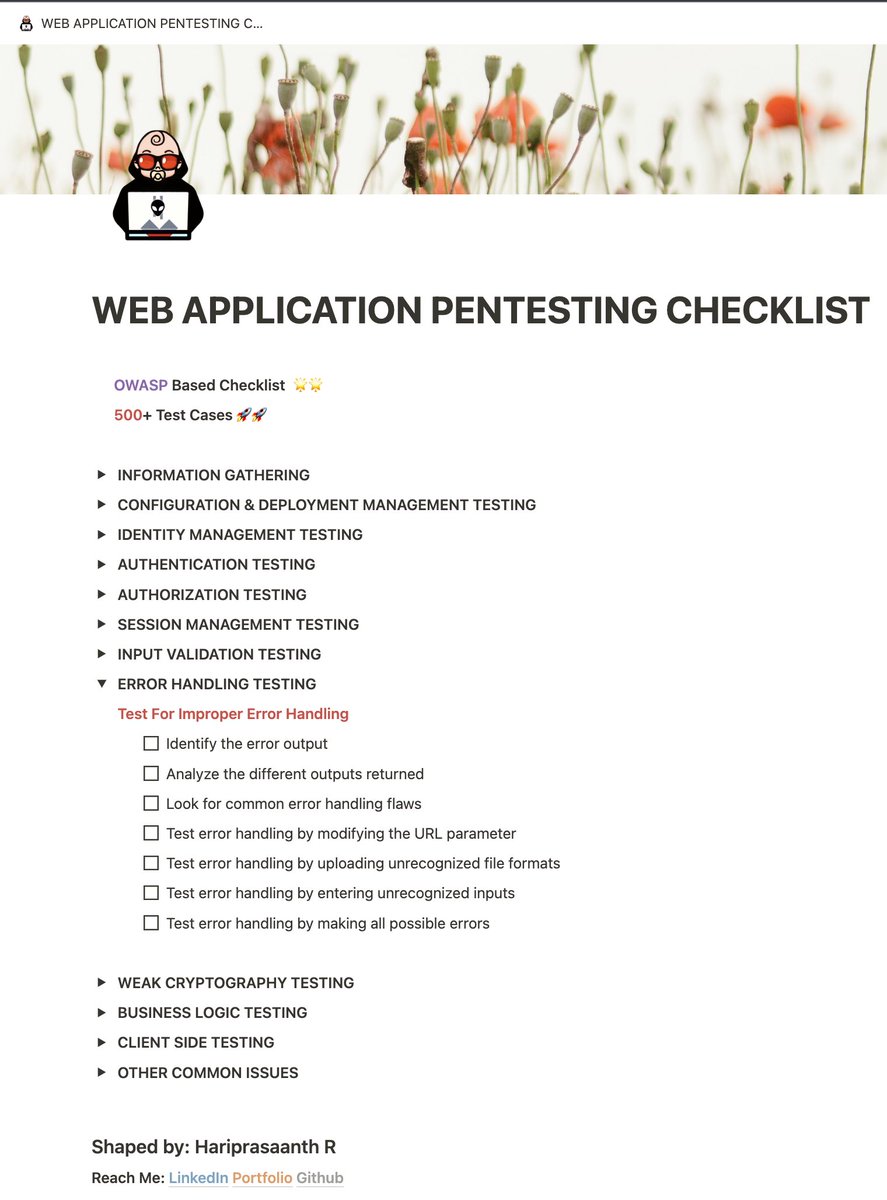
Today I have a very comprehensive checklist suggestion for you on Web Application Penetration Testing❗️📝 I definitely suggest adding it to your bookmarks❗️🎃 Credit: hariprasaanth.blogspot.com 🌟🙌🏻 Notion Link: hariprasaanth.notion.site/hariprasaanth/… #appsec #PenTest #bugbounty #CyberSecurity
I've noticed not many are aware of it but I published a full guide on how to get started in web app security (& bug bounty) Instead of buying someone's course that just started out yesterday, you can use this for free It's sometimes much better, just take a look 👇
Top Web Application Penetration Testing Tools #WebApplicationSecurity #PenetrationTesting #VulnerabilityAssessment #AppSec #CyberSecurity #EthicalHacking #BugBounty #RedTeam #InfoSec #WebSecurity

Top Web Application Penetration Testing Tools Registe here for AWAPT Course - infosectrain.com/courses/web-ap… #WebApplicationSecurity #PenetrationTesting #VulnerabilityAssessment #AppSec #CyberSecurity #EthicalHacking

An enterprise-strength WAF solution at a price small and midsize businesses can afford. #webapplicationsecurity #webapplicationfirewall Read more. atomicorp.com/web-applicatio…
we will delve into the OWASP Top 10 Web Application Security Vulnerabilities, exploring each security risk in detail read more : reconbee.com/owasp-top-10-w… #owasp #owasptop10 #webapplicationsecurity #webapplication #websecurity #cybersecurity #CyberSecurityAwareness
💻 Secure Your Web App Before Hackers Do! 🔐 Detect, analyze, and fix vulnerabilities with Web Application Penetration Testing (WAPT) by Nightingale Data Solution. #WebApplicationSecurity #PenetrationTesting #WAPT #CyberSecurity #EthicalHacking #DataProtection #AppSecurity
🏆 We’re honored! Fortinet #WebApplicationSecurity has been named a 2025 @Gartner_inc Peer Insights™ Customers’ Choice for #CloudWAAP, earning a 4.8/5 rating and 99% willingness to recommend score! 👉 See why we believe organizations choose Fortinet: ftnt.net/6015AsnPb
#WebApplicationSecurity #Cybersecurity #VulnerabilityManagement #APIsecurity #SecureCode #CyberResilience #DigitalTrust #ThreatPrevention #BotAttack #DDoSProtection #CredentialStuffing #FraudPrevention #CyberDefense #AttackSolutions

🔐 Protect your business from hidden online threats with Web Application Penetration Testing (WAPT)! 🚀 #WAPT #WebApplicationSecurity #CyberSecurity #PenetrationTesting #VulnerabilityTesting #DataProtection #AppSecurity #InfoSec #HackerProof #SecurityFirst #BusinessSecurity
Understanding OWASP Top 10: A Comprehensive Guide to Web Application Security read more :reconbee.com/owasp-top-10-w… #OWASPtop10 #webapplicationsecurity #webappsecurity #webapplication #websecurity #vulnerability #vulnerabilities
This practical exposure helped students understand the real-world challenges and techniques involved in securing web platforms. #KAHECyberSecurity #WebApplicationSecurity #SkillTraining #CyberAwareness #EthicalHacking #HandsOnLearning #SecureTheWeb #CyberSkills #TevelCorp
For our Devs out there, Are you building apps, or are you building secure apps? Are you using secure libraries? #webapplicationsecurity #Security #developers
73% of successful corporate breaches begin with exploitable vulnerabilities in web applications. Book your free scoping session today to prioritise remediation🛡️ow.ly/hKbE50Wu31Y #WebApplicationSecurity #PenetrationTesting (Source: Kaspersky Lab)

73% of successful corporate breaches begin with exploitable vulnerabilities in web applications. Book your free scoping session to prioritise remediation 🛡️ow.ly/7iZx50Wu2Kh #WebApplicationSecurity #PenetrationTesting (Source: Kaspersky Lab)

Did you know that 73% of successful corporate breaches start with vulnerabilities in web applications ? Book a free scoping session today to uncover your weaknesses, before a hacker does 🛡️itgovernance.co.uk/pen-testing-th… #WebApplicationSecurity #PenetrationTesting

In this blog post we will delve into the OWASP Top 10 Web Application Security Vulnerabilities, exploring each security risk in detail read more: reconbee.com/owasp-top-10-w… #OWASP #OWASPtop10 #webapplicationsecurity #webapplication #vulnerabilities #vulnerability #websecurity

Web Application Exploit Cheat sheet #intelligence #cyber #webapplicationsecurity #webappdevelopment #webapp #webapplications #informationtechnology #informationsecurity #cybersecurity


Ensure the security of your web applications with comprehensive penetration testing. Learn everything you need to know in our all-encompassing guide. #PenetrationTesting #WebApplicationSecurity #Cybersecurity #WebAppTesting #Infosec okt.to/rdYzAq

🥳 Woohoo! Just cleared the @eLearnSecurity's Web Application Penetration Testing eXtreme (eWPTXv2) certification exam! 🎉 It was an awesome learning experience that I truly enjoyed! #eWPTXv2 #eLearnSecurity #WebApplicationSecurity

Preventing Web Application Access Control Abuse: cisa.gov/sites/default/… #webapplicationsecurity #cybersecurity #informationsecurity #infosec #threatintelligence #hacking #blueteam

🔒 Strengthen your web applications with robust security testing! At QO-BOX, we identify vulnerabilities early with SAST, DAST, IAST, and advanced techniques like Black Box and Fuzz Testing. 🛡️ Stay secure. Stay smart. 🌐✨ #WebApplicationSecurity #CyberSecurity #SecurityTesting…

Discover how #PenTesting helps identify complex #WebApplicationSecurity #Vulnerabilities like gateway and logic errors in our April 27th #Webinar with Milton Araújo. Register now: bit.ly/3KuX4ZD #Cybersecurity #ApplicationSecurity #WebApplications #ECCouncil #WAHS

#بدرد_بخور #Udemy این دوره ی خوبی هستش تا برداشته نشده به صورت رایگان به اکانت یودمی تون اضافه کنید موضوع : Uncle Rat's Web Application Hacking And Bug Bounty Guide لینک : udemy.com/course/uncle-r… #WebApplicationSecurity #BugBounty #HackingTutorial #CyberSecurity



An amazing meetup was organized by the @OWASPIndore team, featuring an insightful session by @_p4nk4j on Business Logic Vulnerabilities. It was great experience to connect with all of you in person. #webapplicationsecurity #bugbounty #owasp #owaspindore


👉 Just 2 days to go! Join this CISO panel discussion (link in threads) #webapplicationsecurity #topthreats #insuranceindustry #insurancesector #cybersecurity #cyberthreats #webapplications #appsec #apiprotection #apptrana #indusface

🚀 Elevate your #webapplicationsecurity with our #penetrationtestingchecklist! 💼💻 It can be your toolkit for uncovering and fixing critical security gaps: (link in thread)

Get insights on how #PenTesting helps to proactively detect and mitigate potential #WebApplicationSecurity risks in our April 27 #Webinar by Milton Araújo. Register now: bit.ly/3KuX4ZD #Cybersecurity #WebApplications #PenetrationTesting #ECCouncil #CybersecurityExpert

Something went wrong.
Something went wrong.
United States Trends
- 1. #BUNCHITA 1,344 posts
- 2. #SmackDown 42.4K posts
- 3. Tulane 3,560 posts
- 4. Aaron Gordon 2,232 posts
- 5. Giulia 13.9K posts
- 6. Supreme Court 179K posts
- 7. Russ 12.8K posts
- 8. #OPLive 2,214 posts
- 9. Connor Bedard 2,149 posts
- 10. #TheLastDriveIn 3,129 posts
- 11. #BostonBlue 4,180 posts
- 12. Caleb Wilson 5,374 posts
- 13. Podz 2,511 posts
- 14. Northwestern 4,800 posts
- 15. Scott Frost N/A
- 16. Rockets 20K posts
- 17. Frankenstein 72.2K posts
- 18. Memphis 15.5K posts
- 19. Zach Lavine N/A
- 20. Isaiah Hartenstein N/A